(Fedora: Lesson 19)
{ Testing denyhosts and brutessh.py }
| Section 0. Background Information |
- What is denyhosts
- DenyHosts is a log-based intrusion prevention security tool for SSH servers written in Python. It is intended to prevent brute force attacks on SSH servers by monitoring invalid login attempts in the authentication log and blocking the originating IP addresses.
- http://denyhosts.sourceforge.net/
- What is brutessh.py
- Brutessh is a program that uses the paramiko ssh library, to launch bruteforce passwords attacks to the sshd service. The tools is multithreading and uses a dictionary for the passwords.
- Prerequisite
- Fedora: Lesson 1: Installing Fedora 14
- Fedora: Lesson 18: Installing and Configuring denyhosts
- BackTrack: Lesson 1: Installing BackTrack 5 R1
-
Lab Notes
- In this lab we will how to do the following:
- We will install brutessh.py on BackTrack.
- We will use brutessh on BackTrack to attack Fedora.
- Fedora will block BackTrack
- We will unblock BackTrack
- In this lab we will how to do the following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- You are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2013 No content replication of any kind is allowed without express written permission.
| Section 1: Edit the Fedora14 Virtual Machine |
- Open Your VMware Player
- Instructions:
- On Your Host Computer, Go To
- Start --> All Program --> VMWare --> VMWare Player
- Instructions:
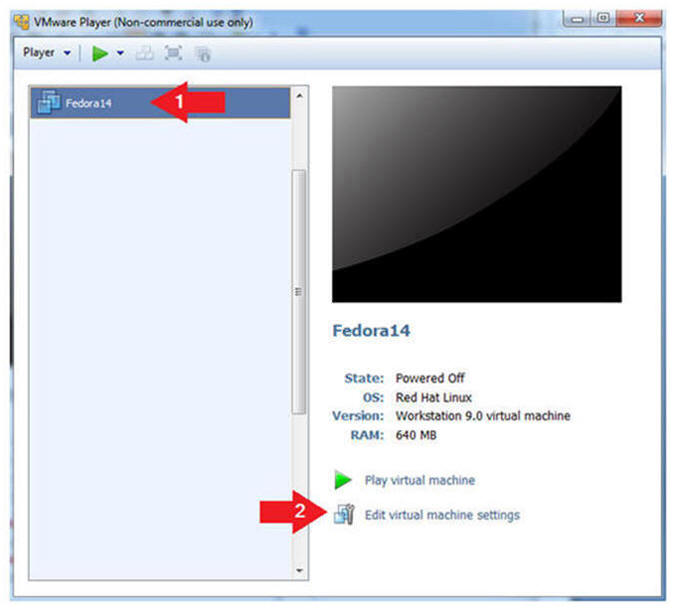
- Edit Fedora 14 Virtual Machine Settings
- Instructions:
- Highlight Fedora14
- Click Edit virtual machine settings
- Instructions:
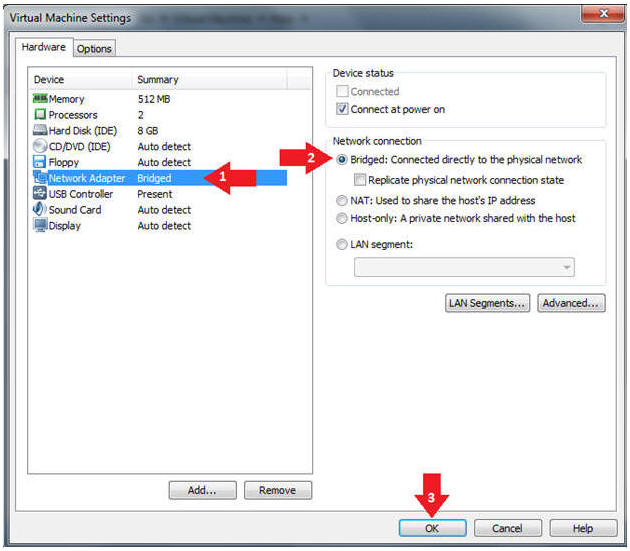
- Edit Network Adapter
- Instructions:
- Highlight Network Adapter
- Select Bridged
- Click the OK Button
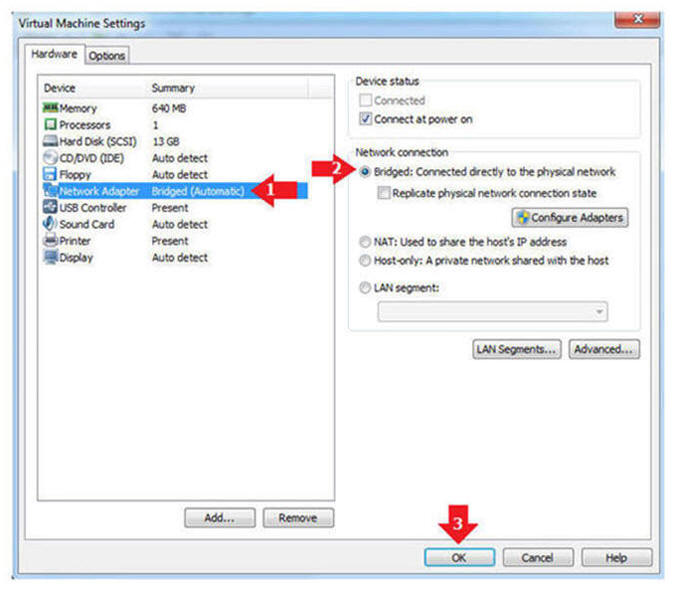
- Instructions:
| Section 2: Play the Fedora14 Virtual Machine |
- Start the Fedora14 VM
- Instructions:
- Click on the Fedora14 VM
- Click on Play virtual machine
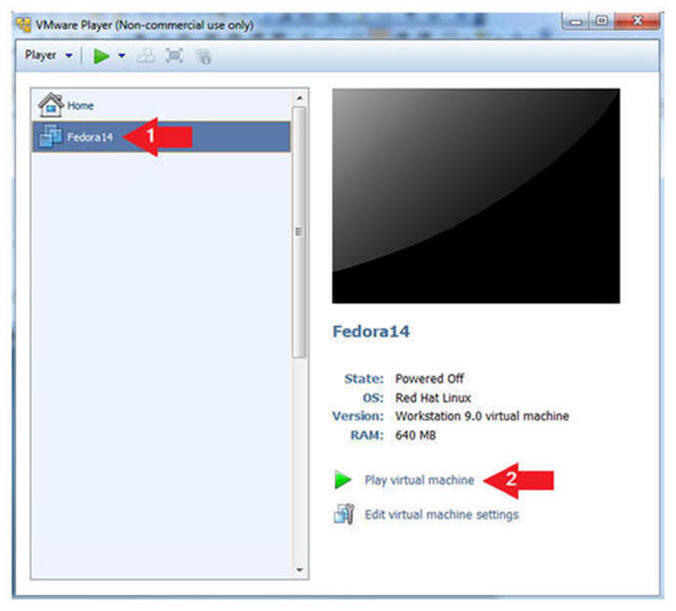
- Instructions:
| Section 3: Login to your Fedora14 server: |
- Login As student
- Instructions:
- Click on student
- Provide student password
- Click the Login Button
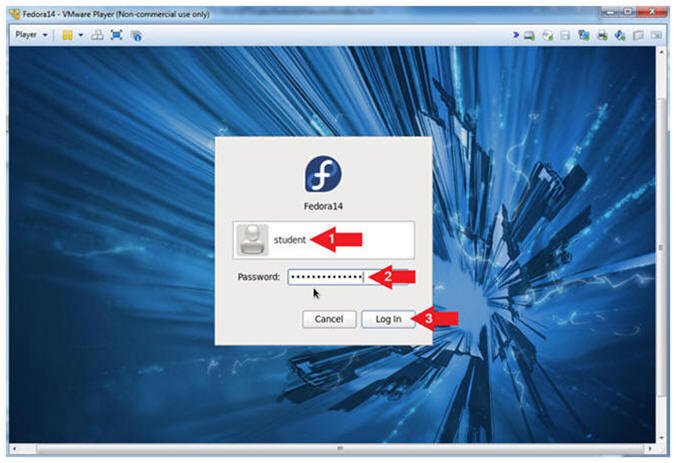
- Instructions:
- Start Up A Terminal.
- Applications --> System Tools --> Terminal
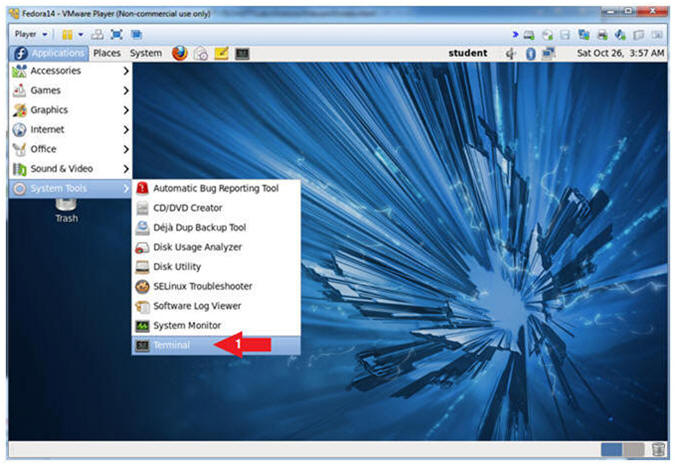
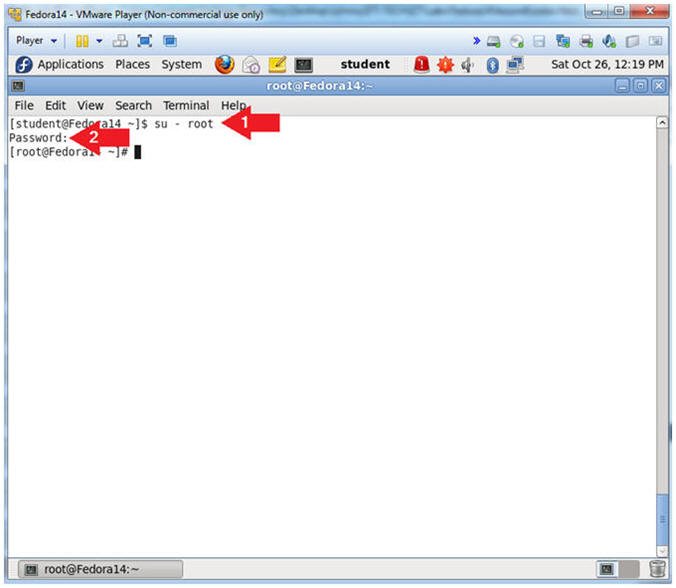
- Switch User to root
- Instruction:
- su - root
- Supply the Root Password
- Instruction:
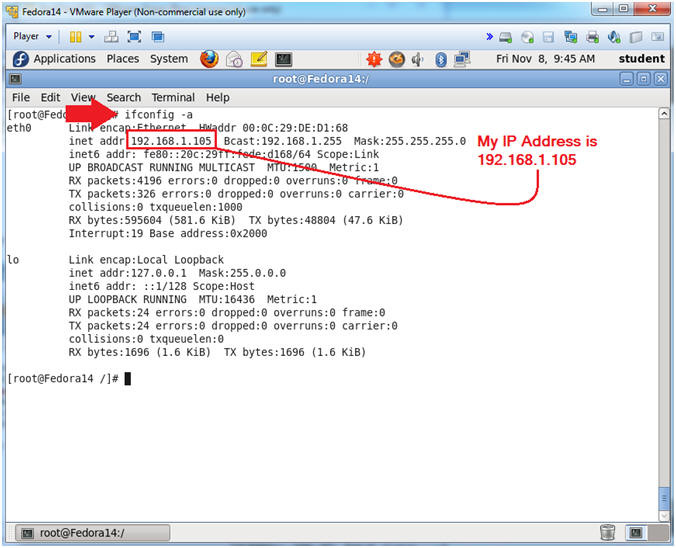
- Get IP Address
- Instructions:
- ifconfig -a
- Notes (FYI):
- As indicated below, my IP address is 192.168.1.105.
- Please record your IP address.
- Instructions:
| Section 4: Configure BackTrack Virtual Machine Settings |
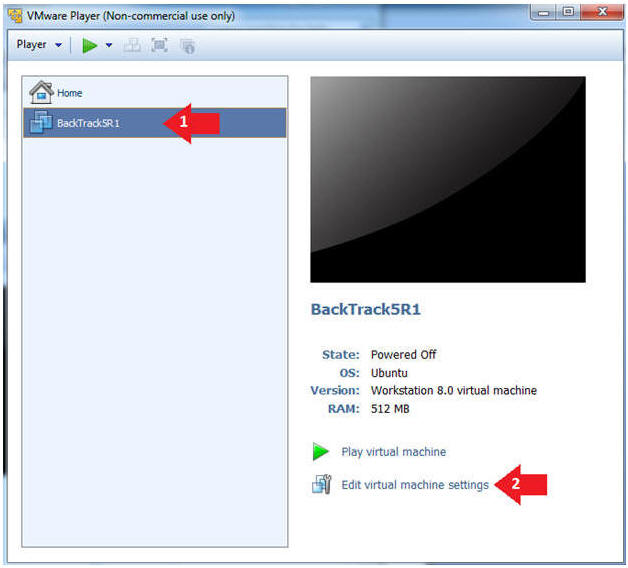
- Edit the BackTrack5R1 VM
- Instructions:
- Select BackTrack5R1 VM
- Click Edit virtual machine settings
- Instructions:
- Edit Virtual Machine Settings
- Instructions:
- Click on Network Adapter
- Click on the Bridged Radio button
- Click on the OK Button
- Instructions:
| Section 5: Play and Login to BackTrack |
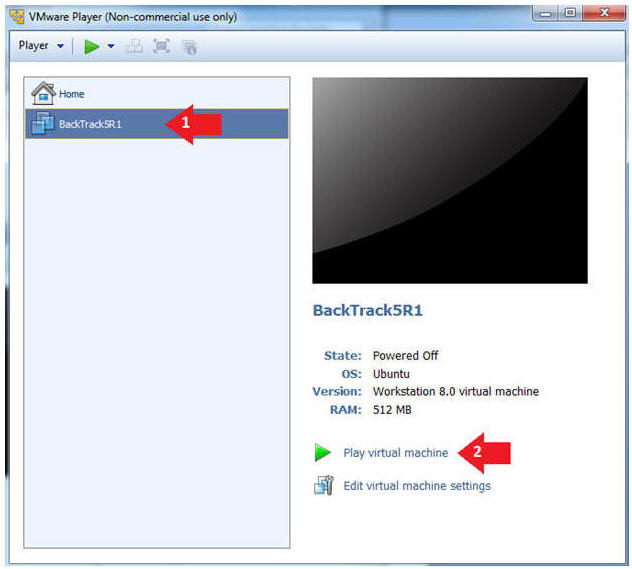
- Play the BackTrack5R1 VM
- Instructions:
- Click on the BackTrack5R1 VM
- Click on Play virtual machine
- Instructions:
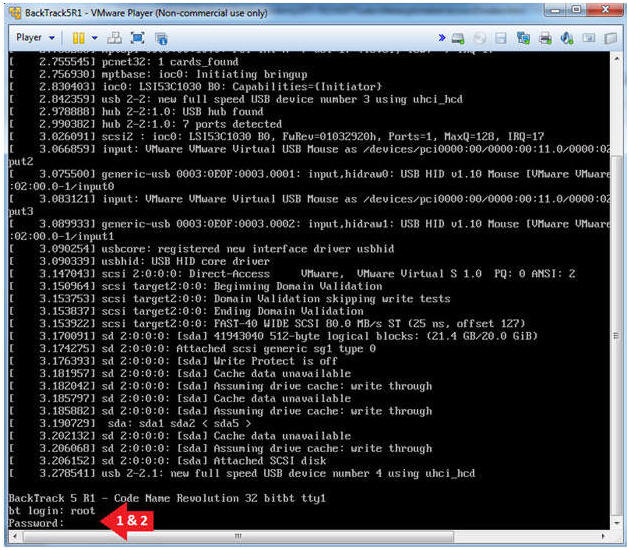
- Login to BackTrack
- Instructions:
- Login: root
- Password: toor or <whatever you changed it to>.
- Instructions:
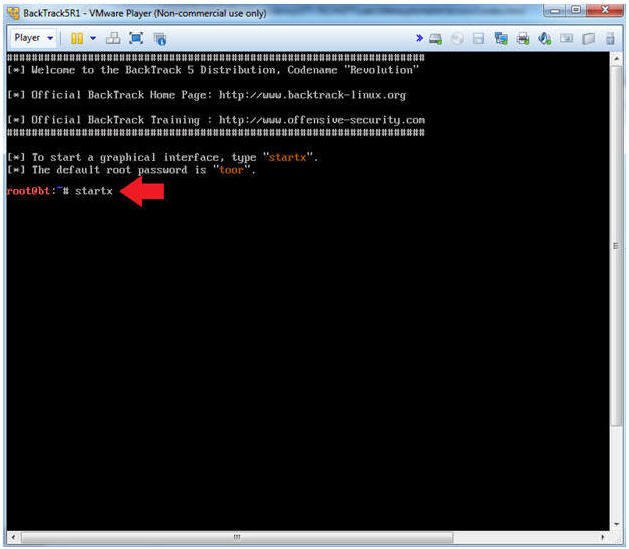
- Bring up the GNOME
- Instructions:
- Type startx
- Instructions:
| Section 6: Open Console Terminal and Retrieve IP Address |
- Start up a terminal window
(On
BackTrack5R1)
- Instructions:
- Click on the Terminal Window
- Instructions:
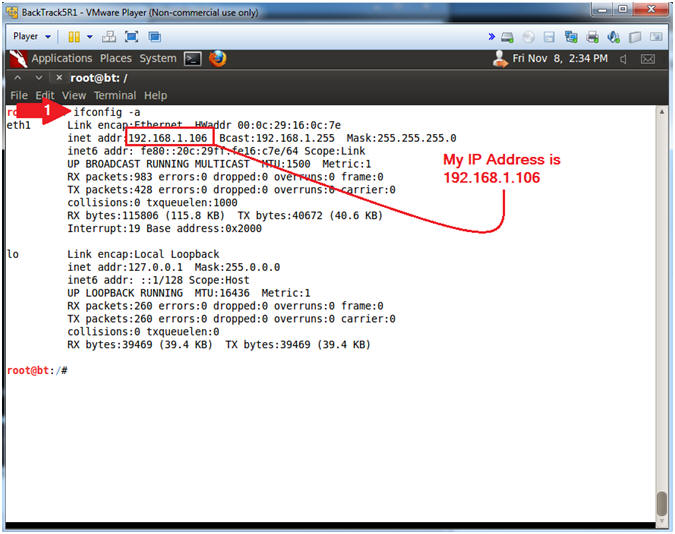
- Obtain the IP Address
- Instructions:
- ifconfig -a
- Note(FYI):
- My IP address 192.168.1.106.
- In your case, it will probably be different.
- This is the machine that will be use to attack the victim machine (Mutillidae).
- Instructions:
| Section 7: Test SSH Between BackTrack and Fedora |
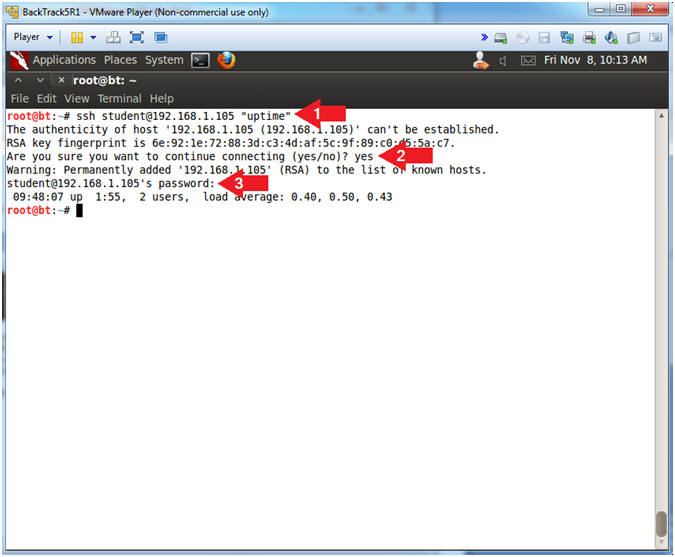
- Test SSH from Backtrack to Fedora (On
BackTrack5R1)
- Instructions:
- ssh
student@192.168.1.105
"uptime"
- If you do not have a student account on Fedora, replace it with the system account you create in Lab 1.
- connecting (yes/no)? yes
- Provide Password
- ssh
student@192.168.1.105
"uptime"
- Note(FYI):
- Replace 192.168.1.105 with Fedora's IP Address obtained from (Section 3, Step 4).
- Instructions:
| Section 8: Inspect Fedora's Security Log |
- Check Fedora's secure log (On
Fedora14)
- Note(FYI):
- Replace 192.168.1.106 with BackTracks's IP Address obtained from (Section 6, Step 2).
- Instructions:
- grep "Accepted password" /var/log/secure | grep "192.168.1.106"
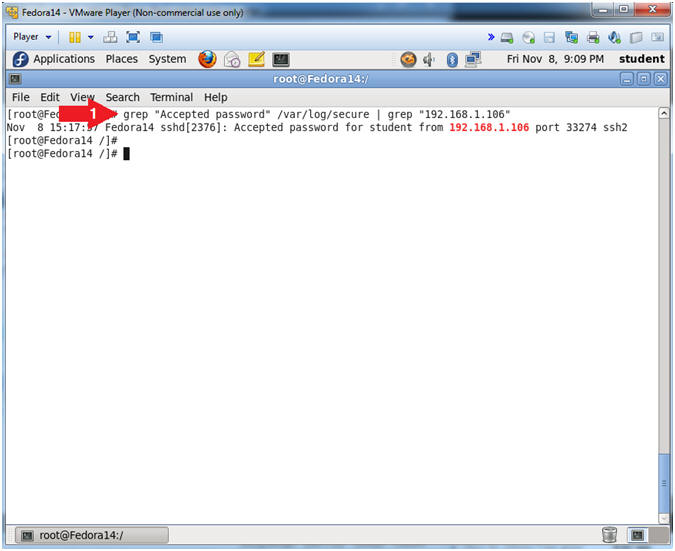
- Note(FYI):
| Section 9: Install and run BruteSSH.py against Fedora |
- Search for BruteSSH.py (On
BackTrack5R1)
- Note(FYI):
- Issue the below commands from the BackTrack Terminal.
- IF BRUTESSH IS ALREADY INSTALLED, THEN CONTINUE TO SECTION 10.
- Instructions:
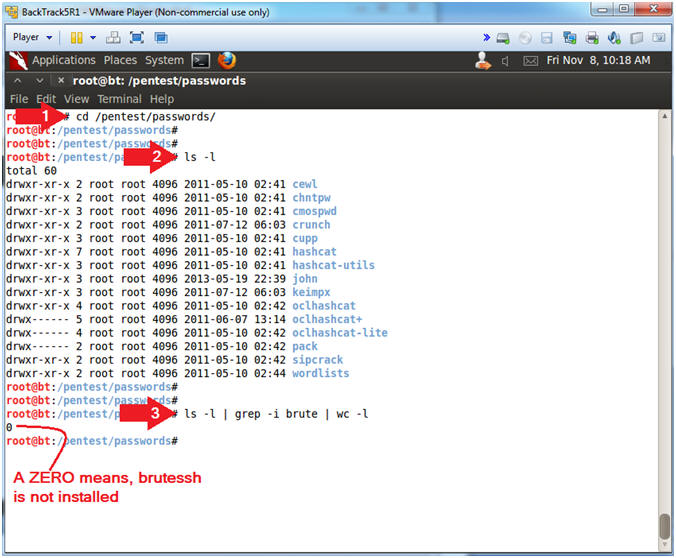
- cd /pentest/passwords/
- In BackTrack, the password cracking programs are typically located in this directory.
- ls -l
- ls -l | grep -i brute | wc -l
- ls -l, list all the files and directories under the directory /pentest/passwords.
- grep -i brute, return only listings that contain the string "brute"
- wc -l, count anything that is returned.
- Notice a zero(0) is return, which infers BruteSSH is not installed.
- cd /pentest/passwords/
- Note(FYI):
- Download, Unzip and Untar brutessh-0.5.tar.bz2
- Instructions:
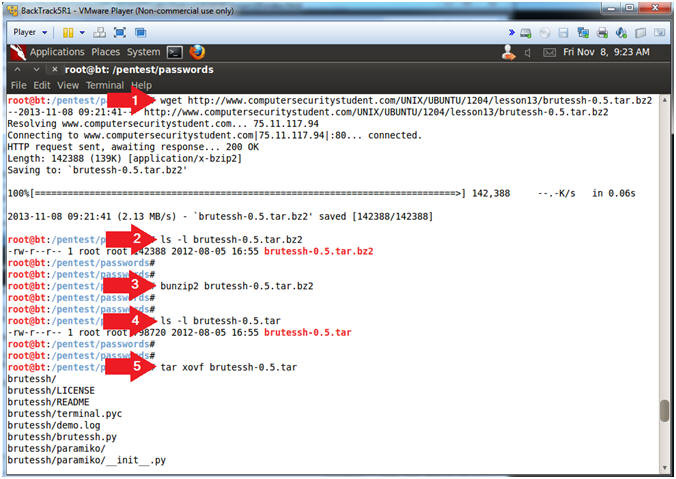
- wget http://www.computersecuritystudent.com/UNIX/UBUNTU/1204/lesson13/brutessh-0.5.tar.bz2
- ls -l brutessh-0.5.tar.bz2
- bunzip2 brutessh-0.5.tar.bz2
- ls -l brutessh-0.5.tar
- tar xovf brutessh-0.5.tar
- Instructions:
- BruteSSH House Cleaning
- Instructions:
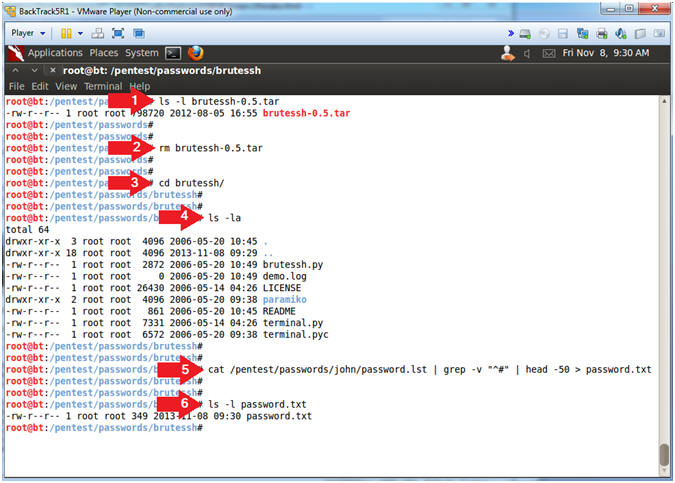
- ls -l brutessh-0.5.tar
- rm brutessh-0.5.tar
- We no longer need the tar file.
- cd brutessh/
- ls -la
- cat /pentest/passwords/john/password.lst
| grep -v "^#" | head -50 > password.txt
- I grabbed the first 50 passwords from John the Ripper to create enough future brute force ssh traffic for denyhosts to block.
- ls -l password.txt
- Instructions:
- Using BruteSSH
- Instructions:
- python brutessh.py -help
- The -help flag produced the usage options.
- python brutessh.py -help
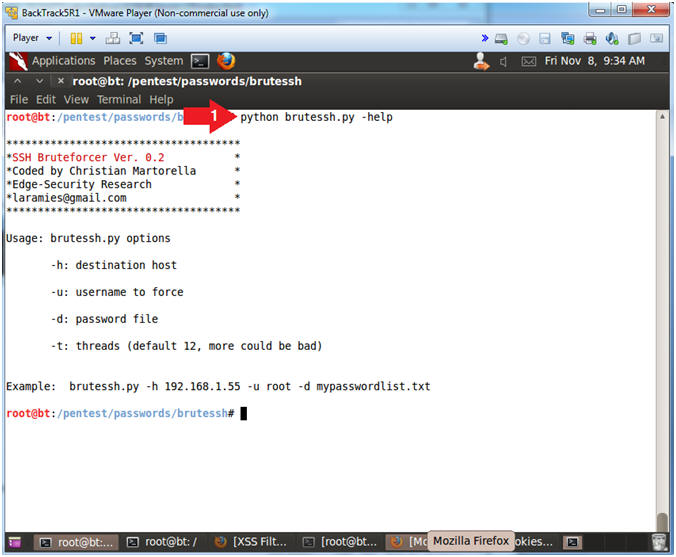
- Instructions:
- Using BruteSSH Against DenyHosts
- Note(FYI):
- Replace 192.168.1.105 with Fedora's IP Address obtained from (Section 3, Step 4).
- Instructions:
- python brutessh.py -h 192.168.1.105 -u root -d password.txt
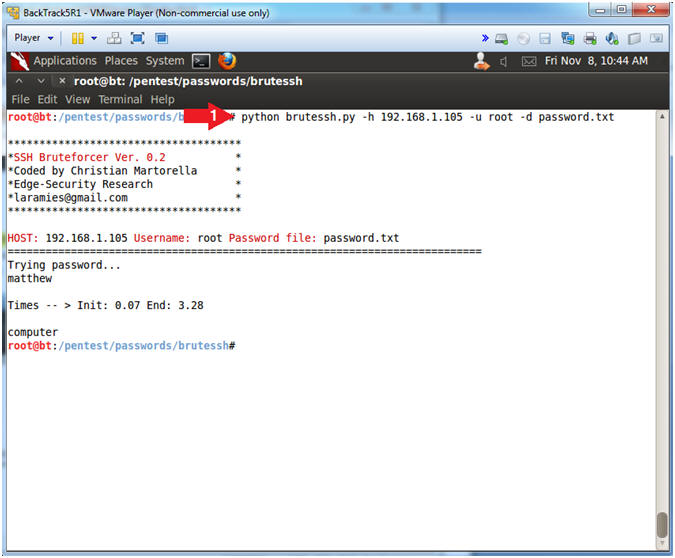
- Note(FYI):
| Section 10: Testing Blocked SSH Traffic from BackTrack to Fedora |
- Testing Blocked SSH Connection (On
BackTrack5R1)
- Note(FYI):
- Replace 192.168.1.105 with Fedora's IP Address obtained from (Section 3, Step 4).
- Instructions:
- ssh
student@192.168.1.105
- Note: DenyHosts on the Fedora server is now blocking the ssh protocol from connecting to port 22.
- telnet
192.168.1.105 22
- Here I am testing to see if IP Addressed is really blocked or if just SSH traffic is blocked.
- Note: Although BackTrack SSH traffic is now blocked, it is still possible to connect using TCP over port 22.
- ssh
student@192.168.1.105
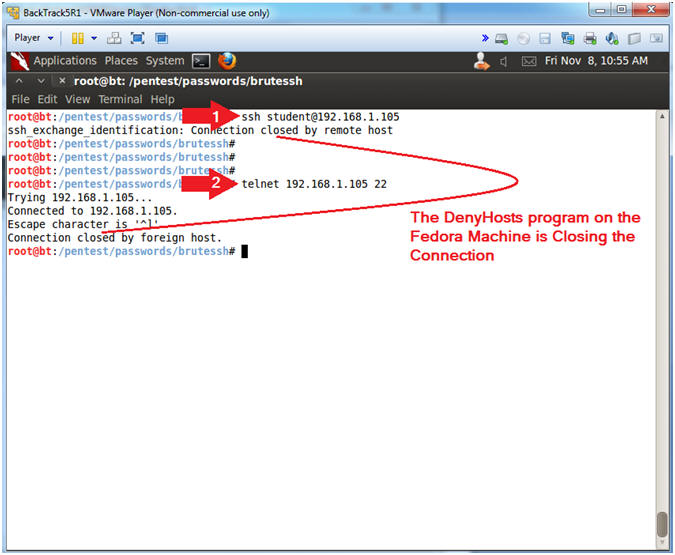
- Note(FYI):
| Section 11: Analyzing Fedora Deny Host Logs |
- Analyzing Fedora Deny Host Logs (On
Fedora)
- Note(FYI):
- Replace 192.168.1.106 with BackTracks's IP Address obtained from (Section 6, Step 2).
- Instructions:
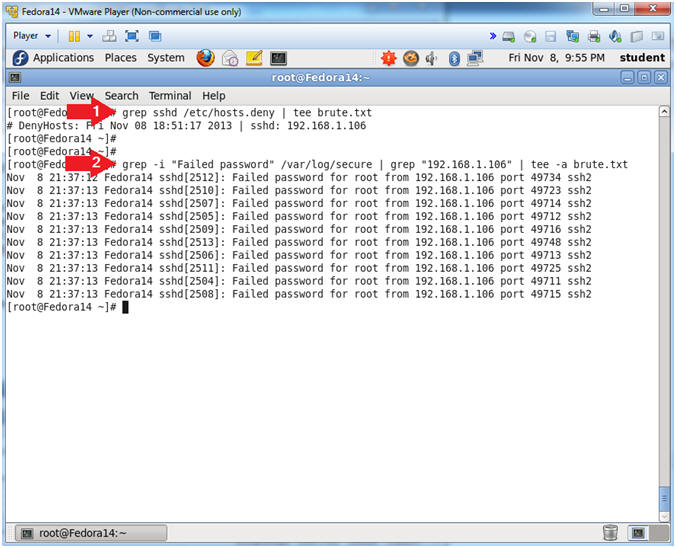
- grep sshd /etc/hosts.deny | tee
brute.txt
- The hosts.deny file contains all the IP Addresses that have been blocked by the denyhosts daemon.
- grep -i "Failed password" /var/log/secure
| grep "192.168.1.106"
| tee -a brute.txt
- Search the /var/log/secure file for the phrase "Failed password" AND IP Address "192.168.1.106".
- grep sshd /etc/hosts.deny | tee
brute.txt
- Note(FYI):
| Section 14: Unblock BackTrack |
- Stop rsyslog and denyhosts (On
Fedora)
- Instructions:
- fuser /var/log/secure
- The command fuser identifies Process IDs (PID)s that have open sockets to a file.
- Notice that PIDs 2715 and 2738 currently have open sockets to the secure file.
- ps -eaf | grep -v grep | egrep
'(2715|2738)'
- Replace 2715 and 2738 with the Process IDs (PIDs) that fuser lists in your session.
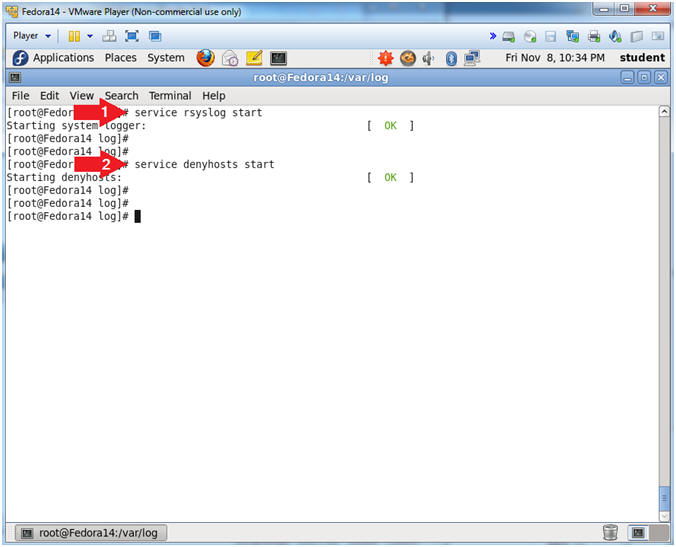
- service rsyslog stop
- service denyhosts stop
- fuser /var/log/secure
- Notice no Process IDs are returned.
- fuser /var/log/secure
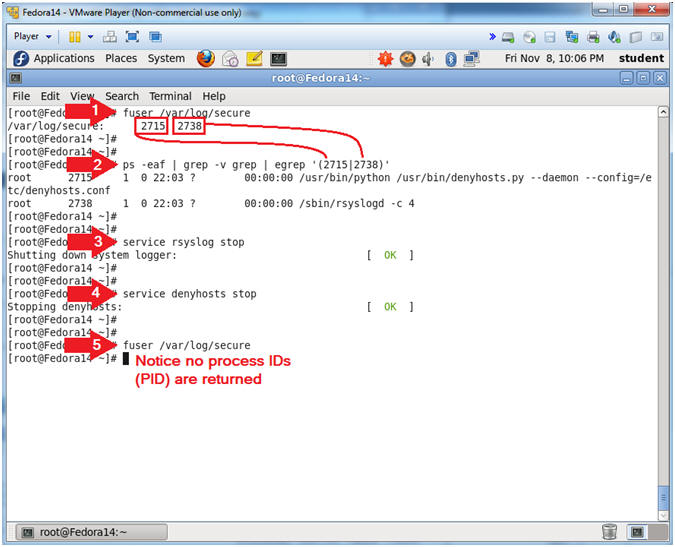
- Instructions:
- Scrub the hosts.deny file
- Note(FYI):
- Replace 192.168.1.106 with BackTracks's IP Address obtained from (Section 6, Step 2).
- Instructions:
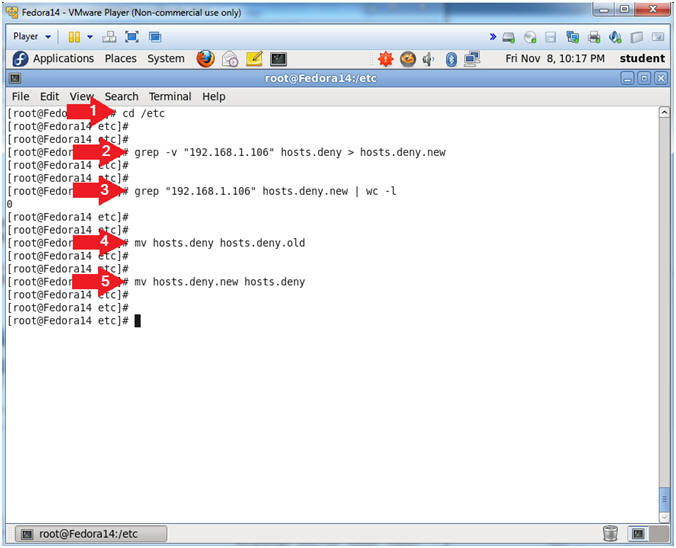
- cd /etc
- grep -v "192.168.1.106" hosts.deny > hosts.deny.new
- grep "192.168.1.106" hosts.deny.new | wc -l
- mv hosts.deny hosts.deny.old
- mv hosts.deny.new hosts.deny
- Note(FYI):
- Scrub the secure file
- Note(FYI):
- Replace 192.168.1.106 with BackTracks's IP Address obtained from (Section 6, Step 2).
- Instructions:
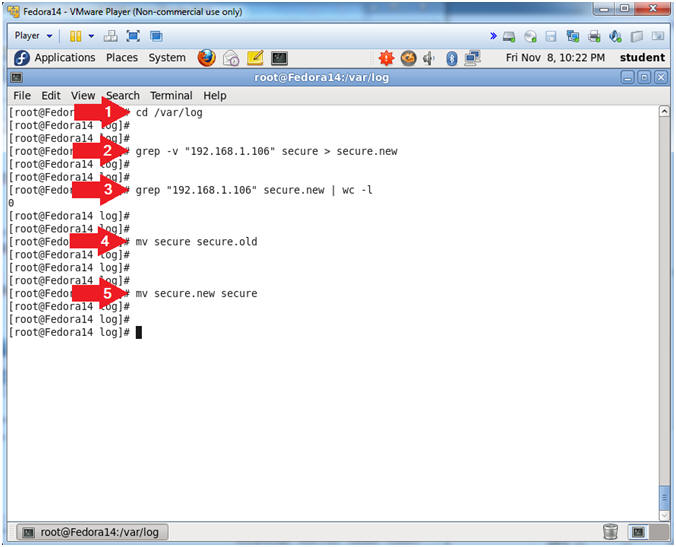
- cd /var/log/
- grep -v "192.168.1.106" secure > secure.new
- grep "192.168.1.106" secure.new | wc -l
- mv secure secure.old
- mv secure.new secure
- Note(FYI):
- Scrub the denyhosts file
- Note(FYI):
- Replace 192.168.1.106 with BackTracks's IP Address obtained from (Section 6, Step 2).
- Instructions:
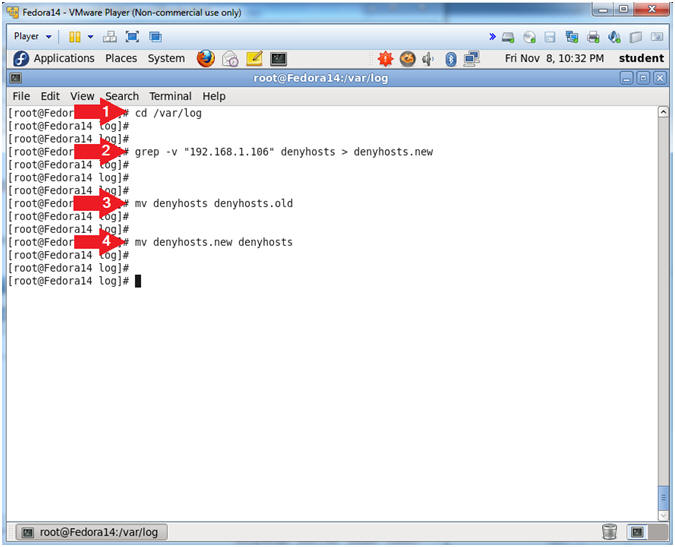
- cd /var/log/
- grep -v "192.168.1.106" denyhosts > denyhosts.new
- mv denyhosts denyhosts.old
- mv denyhosts.new denyhosts
- Note(FYI):
- Start syslog and denyhosts
- Instructions:
- service rsyslog start
- service denyhosts start
- Instructions:
| Section 15: Test SSH From BackTrack To Fedora |
- Test SSH Connection from BackTrack to Fedora (On
BackTrack)
- Note(FYI):
- Replace 192.168.1.105 with Fedora's IP Address obtained from (Section 3, Step 4).
- Instructions:
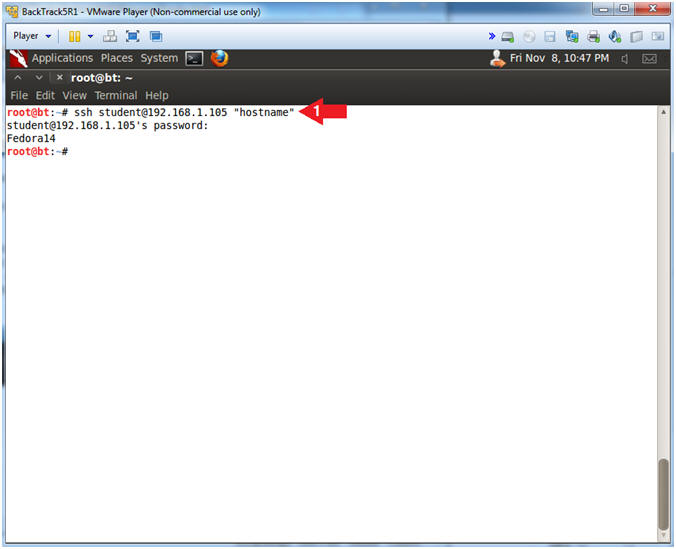
- ssh student@192.168.1.105 "hostname"
- Provide Password.
- Note(FYI):
| Section 16: Proof of Lab |
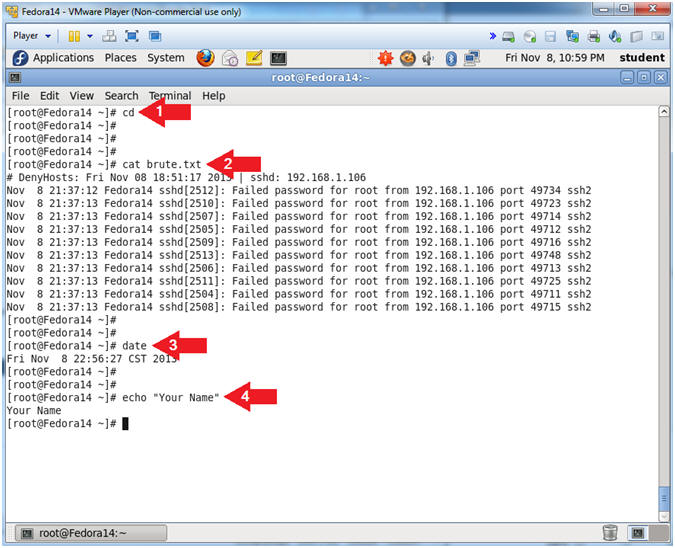
- Proof of Lab
- Instructions:
- cd
- cat brute.txt
- date
- echo "Your Name"
- Replace the string "Your Name" with your actual name.
- e.g., echo "John Gray"
-
Proof of Lab
Instructions
- Do a <PrtScn>
- Paste into a word document
- Upload to Moodle
- Instructions: