(Damn Vulnerable Windows XP: Lesson 2)
{ How to setup the Adobe Flash Player Exploit }
| Section 0. Background Information |
- What is Damn Vulnerable Windows XP?
- This is a Windows XP Virtual Machine that provides a practice environment to conduct ethical penetration testing, vulnerability assessment, exploitation and forensics investigation.
- The Microsoft Software License Terms for the IE VMs are included in the release notes.
- By downloading and using this software, you agree to these license terms.
- What is
Adobe Flash Player
Exploit?
- This vulnerability (CVE-2011-0609) could cause a browser crash and potentially allow an attacker to take control of the affected system.
- This critical vulnerability exists in Adobe Flash Player 10.2.152.33 and earlier versions (Adobe Flash Player 10.2.154.18 and earlier for Chrome users) for Windows, Macintosh, Linux and Solaris operating systems, Adobe Flash Player 10.1.106.16 and earlier versions for Android, and the Authplay.dll component that ships with Adobe Reader and Acrobat X (10.0.1) and earlier 10.x and 9.x versions of Reader and Acrobat for Windows and Macintosh operating systems.
- Pre-Requisite
-
Lab Notes
- In this lab we will do the following:
- Download Adobe Flash 10.2.152.26
- Install Adobe Flash 10.2.152.26
- Weaken Internet Explorer Security Settings
- In this lab we will do the following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- You are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2015 No content replication of any kind is allowed without express written permission.
| Section 1: Log into Damn Vulnerable WXP-SP2 |
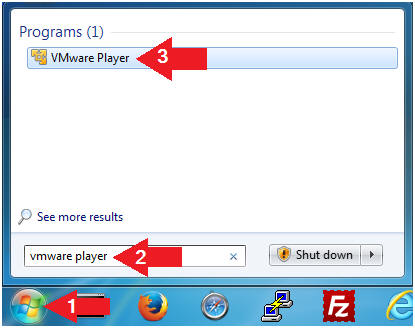
- Open VMware Player on your windows machine.
- Instructions:
- Click the Start Button
- Type "vmware player" in the search box
- Click on VMware Player
- Instructions:
- Edit Virtual Machine Settings
- Instructions:
- Click on Damn Vulnerable WXP-SP2
- Edit Virtual Machine Settings
- Note:
- Before beginning a lesson it is necessary to check the following VM settings.
- Instructions:
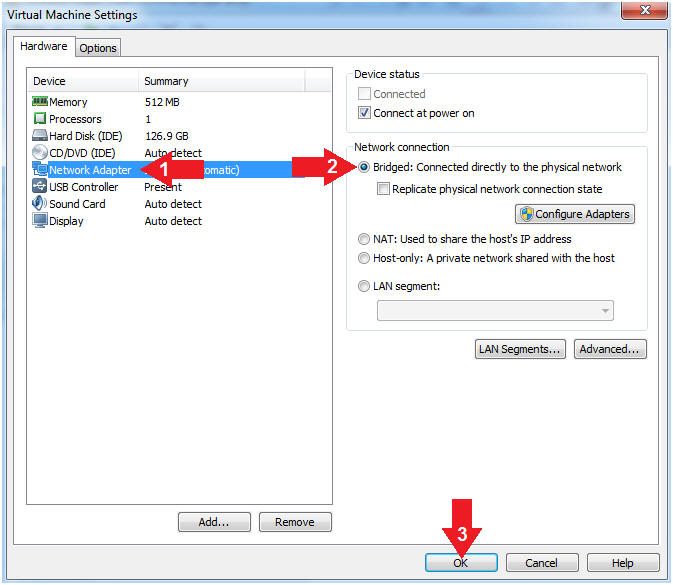
- Set Network Adapter
- Instructions:
- Click on Network Adapter
- Click on the radio button "Bridged: Connected directly to the physical network".
- Click the OK Button
- Instructions:
- Start Up Damn Vulnerable WXP-SP2.
- Instructions:
- Start Up your VMware Player
- Play virtual machine
- Instructions:
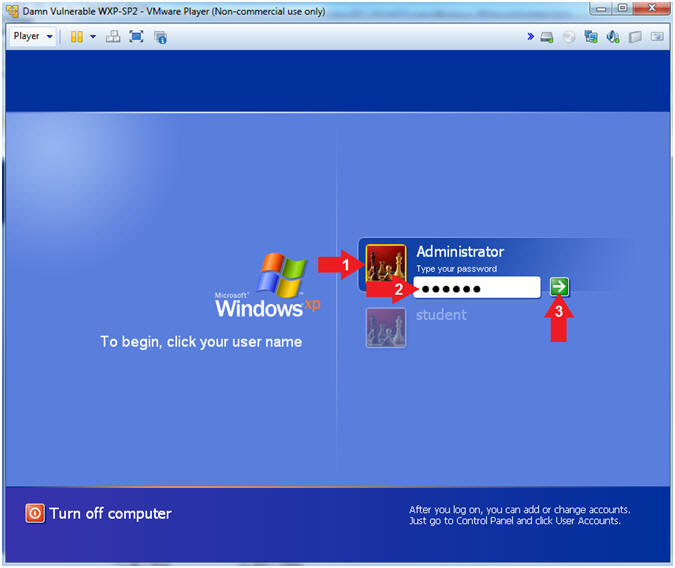
- Logging into Damn Vulnerable WXP-SP2.
- Instructions:
- Click on Administrator
- Password: Supply Password
- (See Note)
- Press <Enter> or Click the Arrow
- Note(FYI):
- Password was created in (Lab 1, Section 1, Step 8)
- Instructions:
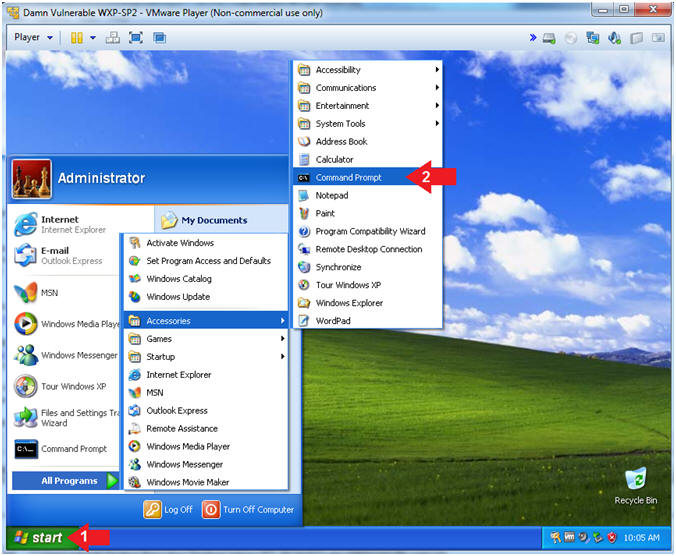
- Open the Command Prompt
- Instructions:
- Click the Start Button
- All Programs --> Accessories --> Command Prompt
- Instructions:
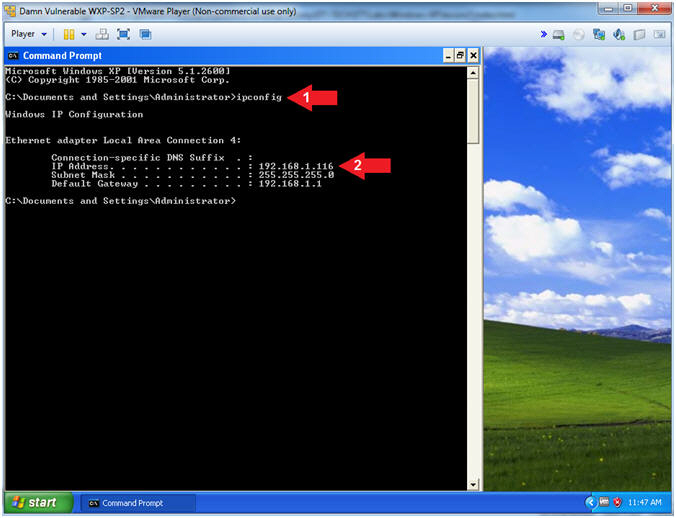
- Obtain Damn Vulnerable WXP-SP2's IP Address
- Instructions:
- ipconfig
- Record Your IP Address
- Note(FYI):
- In my case, Damn Vulnerable WXP-SP2's IP Address 192.168.1.116.
- This is the IP Address of the Victim Machine.
- Instructions:
| Section 2: Install Adobe Flash 10.2.152.26 |
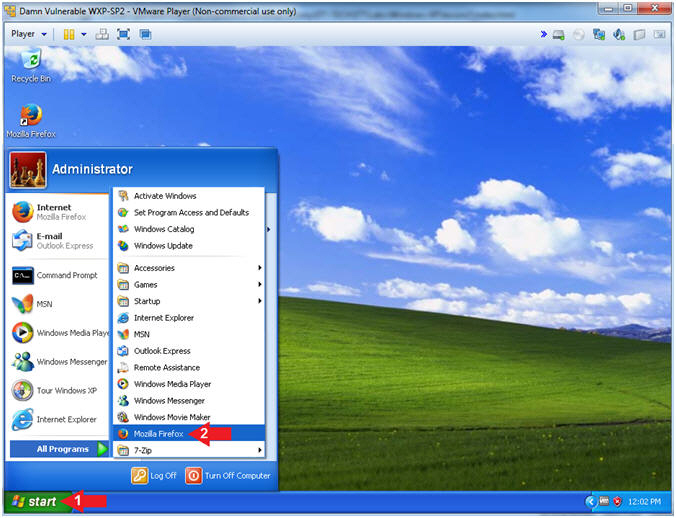
- Open Firefox
- Instructions:
- Click the Start Button
- All Programs --> Mozilla Firefox
- Instructions:
- Download Flash 10.2.152.26 (Part 1)
- Instructions:
- Navigate to the following
URL
- http://www.computersecuritystudent.com/WINDOWS/DVW/WXP_IE6/lesson2/fp_10.2.152.26_archive.zip
- Click the Save File Radio Button
- Click the OK Button
- Navigate to the following
URL
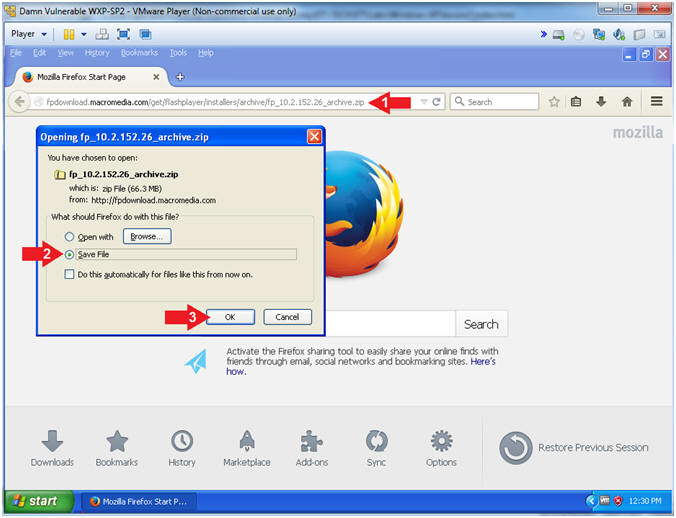
- Instructions:
- Download Flash 10.2.152.26 (Part 2)
- Instructions:
- Navigate to Desktop --> My Documents --> Downloads
- Click the Save Button
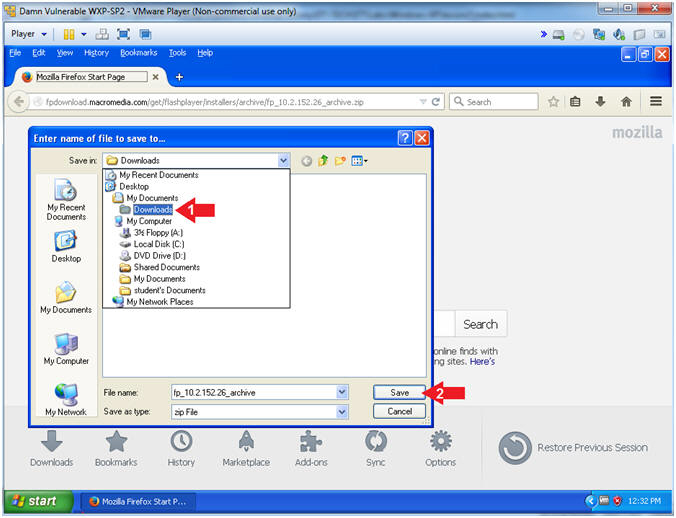
- Instructions:
- Open Download Folder
- Instructions:
- Tools --> Downloads
- Right Click on fp_10.2.152.26_archive.zip
- Click on Open Containing Folder
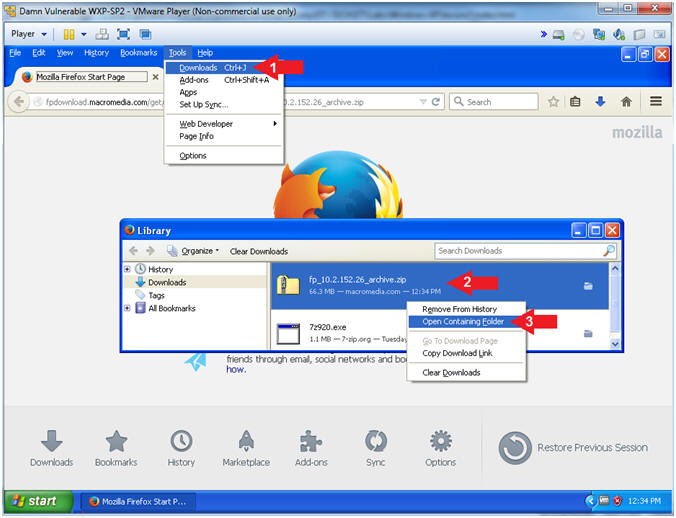
- Instructions:
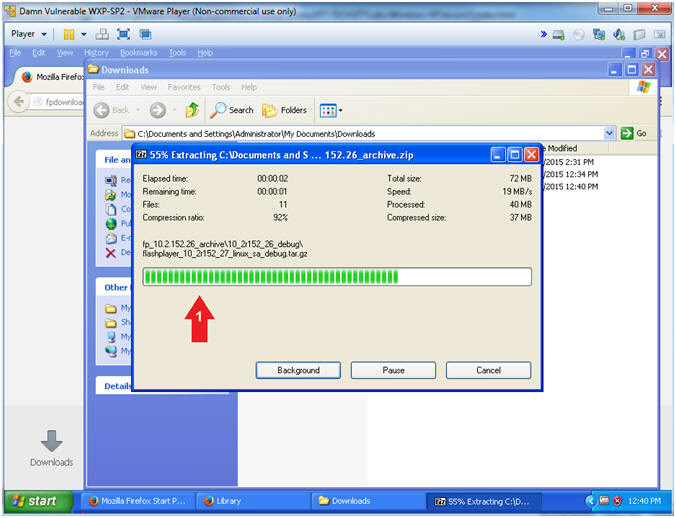
- Uncompress
fp_10.2.152.26_archive.zip
- Instructions:
- Right Click on fp_10.2.152.26_archive.zip
- Hover mouse over 7-Zip
- Select Extract to "fp_10.2.152.26_archive\"
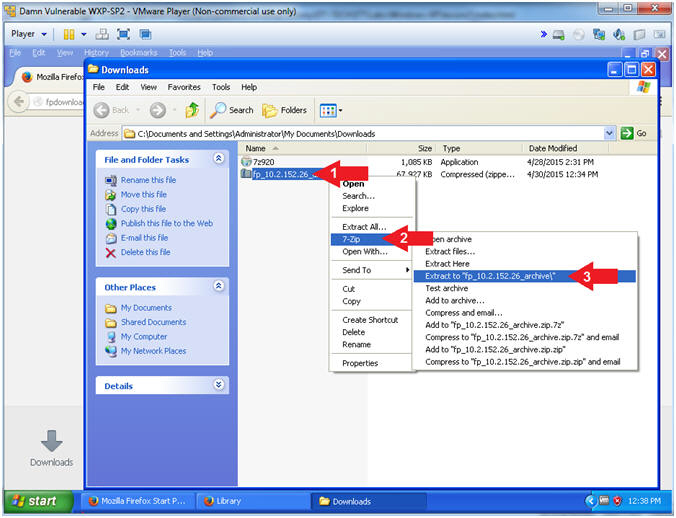
- Instructions:
- Extracting
- Note(FYI):
- The extraction process will take 5 to 10 seconds
- Continue to next step
- Note(FYI):
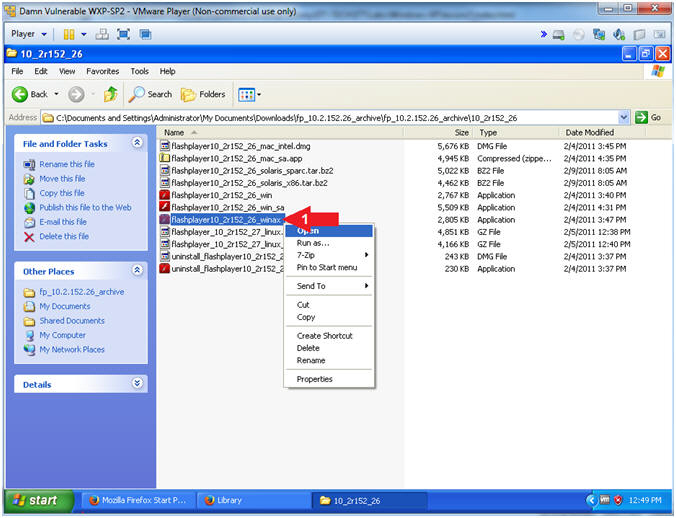
- Navigate to 10_2r152_26
- Instructions:
- Click on fp_10.2.152.26_archive, and continue navigating down to 10_2r152_26 directory
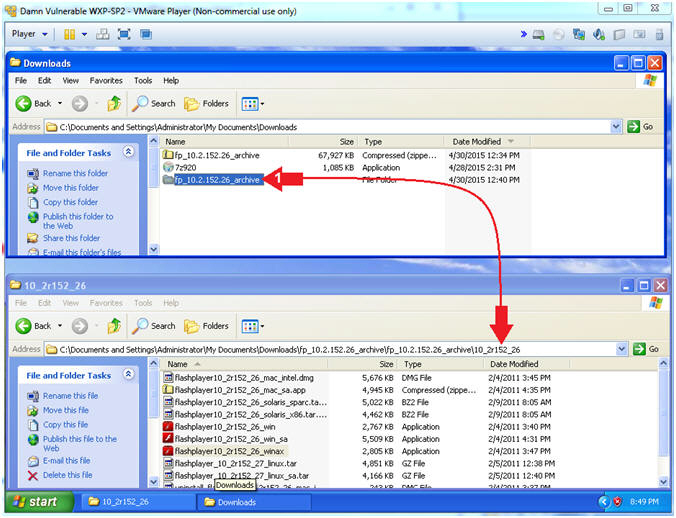
- Instructions:
- Open flashplayer10_2r152_26_winax
- Instructions:
- Click on flashplayer10_2r152_26_winax
- Instructions:
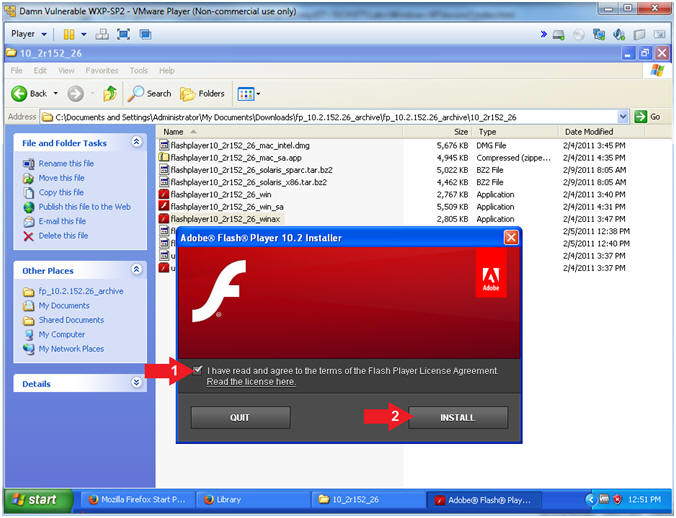
- Adobe Flash Player 10.2 Installer
- Instructions:
- Click the checkbox
- Click the Install Button
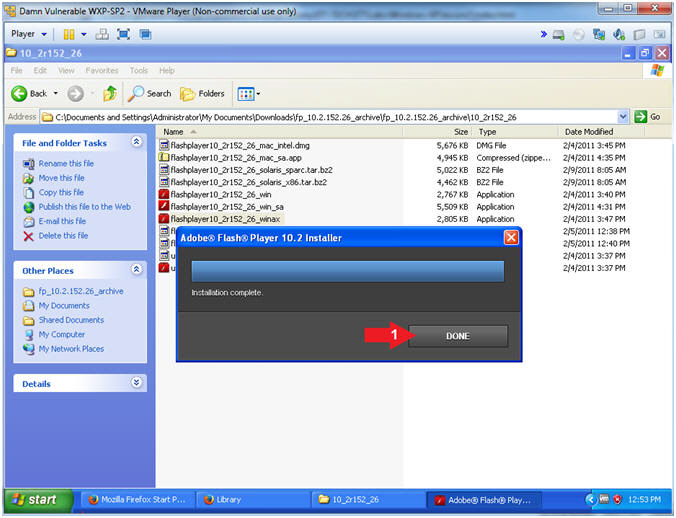
- Instructions:
- Adobe Flash Installation Complete
- Instructions:
- Click the Done Button
- Instructions:
| Section 3: Weaken Internet Explorer Security Settings |
- Open Internet Explorer
- Instructions:
- Click on the Start Button
- All Programs --> Internet Explorer
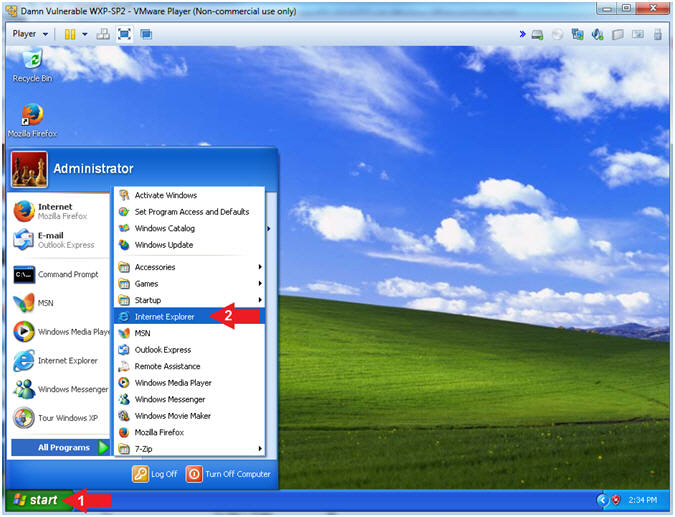
- Instructions:
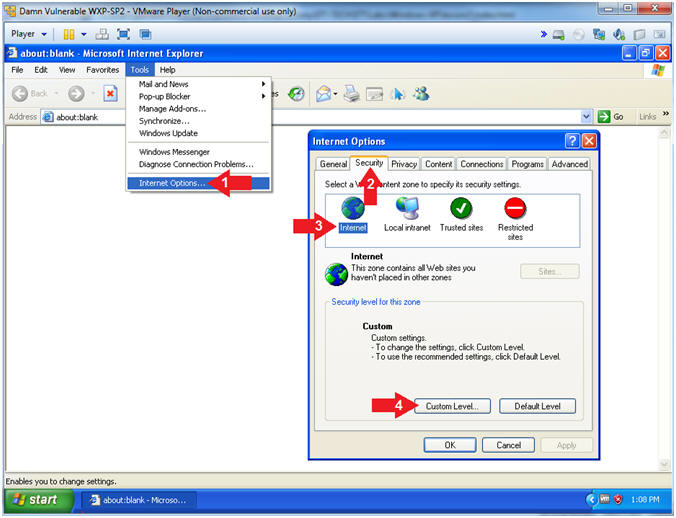
- Open Internet Options
- Instructions:
- Tools --> Internet Options
- Click the Security Tab
- Click the Internet Icon
- Click the Custom Level Button
- Instructions:
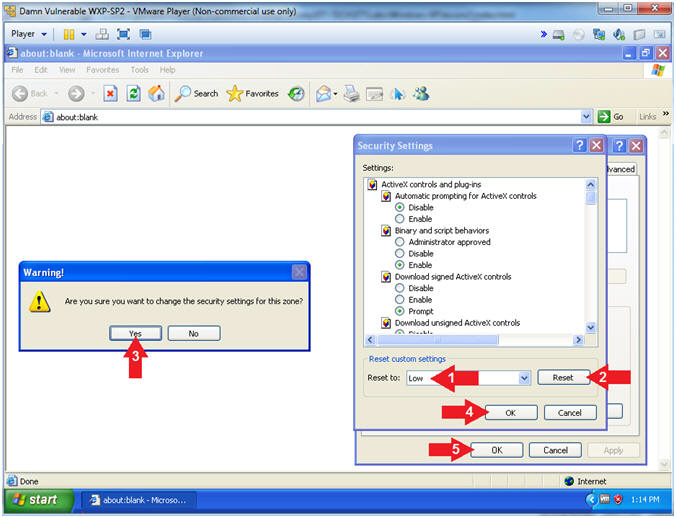
- Configure Internet Explorer Security Settings
- Instructions:
- Reset to: Low
- Click the Reset Button
- The the Yes Button, after the Warning box appears.
- Click the OK Button
- Click the OK Button
- Note(FYI):
- Obviously, it is never a good idea to select the lowest browser security settings, thereby enabling all the ActiveX controls.
- Accordingly, this VM will later be used to illustrate the Adobe Flash Player AVM Bytecode Verification Vulnerability.
- See CVE-2011-0609
- Instructions:
| Section 4: Proof of Lab |
- Open the Command Prompt
- Instructions:
- Click the Start Button
- All Programs --> Accessories --> Command Prompt
- Instructions:
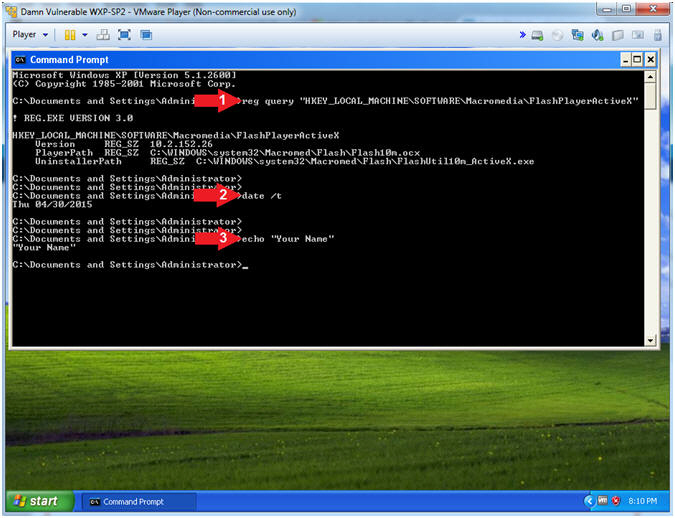
- Proof of Lab
- Instructions:
- reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Macromedia\FlashPlayerActiveX"
- date /t
- echo "Your Name"
- Put in your actual name in place of "Your Name"
- e.g., echo "John Gray"
-
Proof of Lab
Instructions
- Press the <Ctrl> and <Alt> key at the same time.
- Press the <PrtScn> key.
- Paste into a word document
- Upload to Moodle
- Instructions: