(Metasploit: Getting Started on Backtrack 4)
{ Configure IP Address, Starting MSF Console }
| 1. Logging into Backtrack01 |
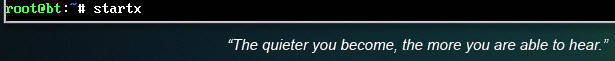
- Login to your
Backtrack01 VM, as username root
- startx
- Issue the startx command if you are currently are only seeing a console and not a graphical user interface.
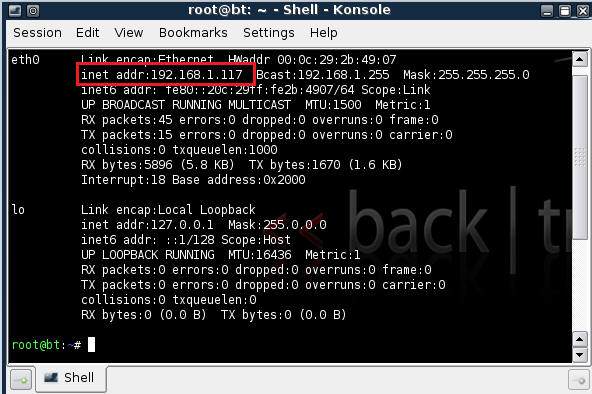
| 2. Confirm Backtrack01 has an IP Address |
- Fire up a console or terminal window
- System --> Konsole
- ifconfig
- Example: No IP Address for eth0
- If a valid IP address for eth0 is not displayed please move onto step 3.
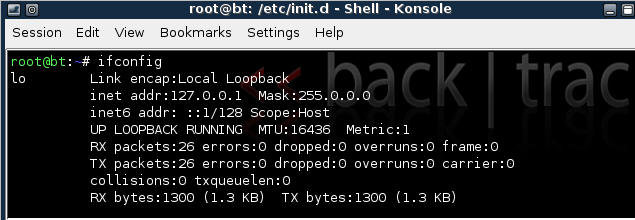
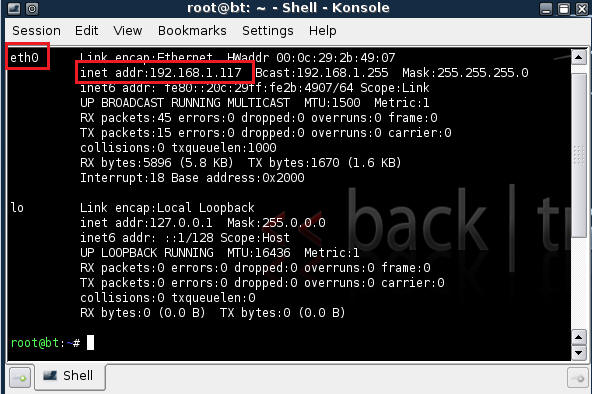
- Example: Valid IP Address for eth0
- Example: No IP Address for eth0
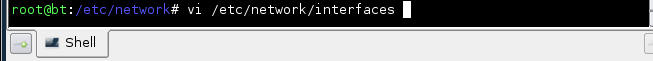
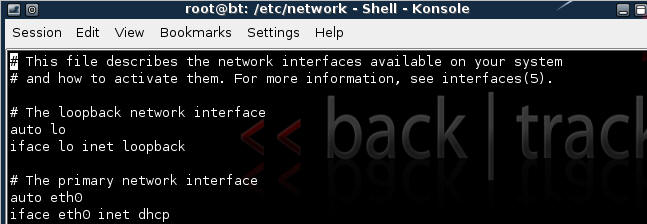
- vi /etc/network/interfaces
- Your file should look similar to the below
screen shot
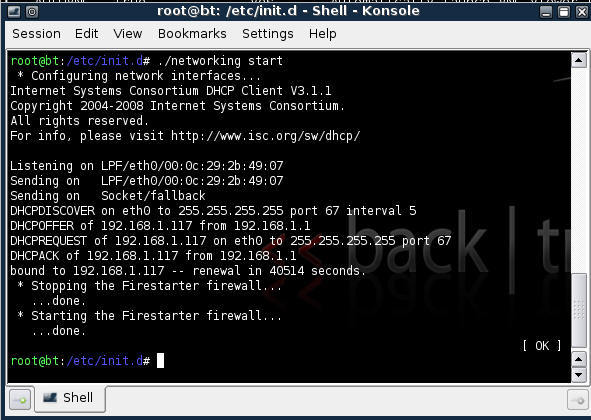
- cd /etc/init.d/
- ./networking start
- Confirm you have a valid IP address for eth0
- In my case, eth0's IP address is 192.168.1.107.
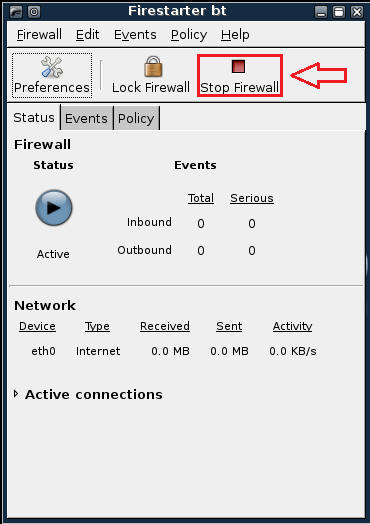
| 3. Stop Firewall on Backtrack01 |
- Start Firestarter
- System --> Firestarter
- Click on Stop Firewall
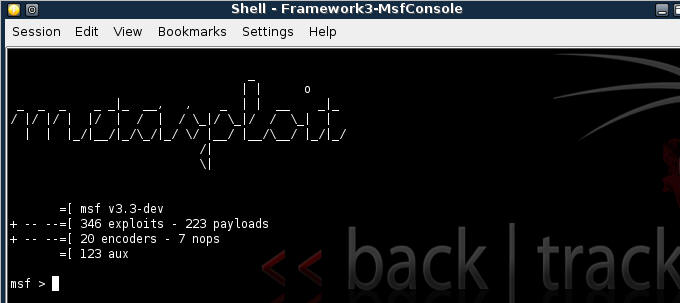
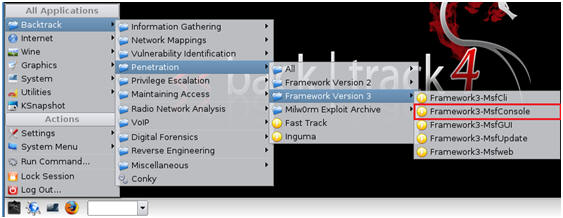
| 5. Starting up the Metasploit MSF Console |
- Fire up the MSF Console (See Below)
- Note It might take a while to start.
- Once MSF Loads (See Below)