(Student Help: ITT-Technical Institute)
{ Free Cyber Security Dojo Trial Memberships }
| Section 0. Legal Disclaimer |
-
Legal Disclaimer
- By using or accessing this website you are accepting all the terms of this Legal Disclaimer, User Agreement, Payment Agreement and Privacy Agreement. If you do not agree with anything in the above statement you should not use or access this website.
- As a condition of your use of this Web site, you warrant to Computer Security Student, LLC that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- You are on notice, that continuing and/or using this educational website outside your "own" test environment is considered malicious and is against the law.
- © 2016 No content replication of any kind is allowed without express written permission.
- What is Our Affiliation with ITT Technical Institute?
- Although Computer Security Student, LLC is in not affiliated with ITT Technical Institute, we sincerely sympathize with the innocent and affected students, instructors, and alumni. We have many friends that were affected in Texas, Ohio and Florida.
- Therefore, we would like to humbly offer, to any ITT Technical Institute student, instructor, or alumni, a free trial membership to our Cyber Security Martial Arts Training Program (Hac-King-Do) that meets the requirements outlined in (Section 1).
- Why are we offering assistance?
- Computer Security Student, LLC has provided free online Cyber Security training in the local Houston Texas area community for over 4 years. We have provided free seminars and workshops to several of the Local Houston Community Colleges and Technical Institutes.
- We do not want students to give up on their dreams to become Cyber Security Professions.
- Therefore, Computer Security Student, LLC in its own little way, wants to help those ITT Technical students, instructors, and alumni continue their training, while they are trying figure out their next move.
- ITT Technical Institute Links
- General Information
- Colleges Accepting ITT Tech
Students
- http://itt-tech.info/education-options/
- Dear ITT Tech students, be careful of the schools that invite you in with open arms that do not accept your classes.
- Department of Education
-
https://studentaid.ed.gov/sa/about/announcements/itt
- Search for "Closed School Loan Discharge".
- https://studentaid.ed.gov/sa/about/announcements/itt/faq
-
https://studentaid.ed.gov/sa/about/announcements/itt
- In the News
| Section 1. Free Trial Memberships Requirements |
- Free Trial Memberships for ITT-TECH Students
- If you are a ITT-TECH student, instructor or alumni, Computer Security Student, LLC would like to offer you a free 4 week trial membership.
- Free Trial Memberships for ITT-Tech Veterans
- If you are a ITT-TECH student, instructor or alumni that happens to be a United States Veteran, Computer Security Student, LLC would like to offer you a free 6 week trial membership.
- How to contact us?
- Instructions:
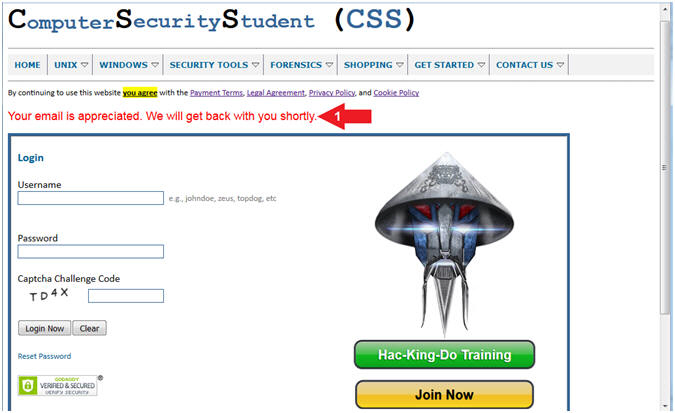
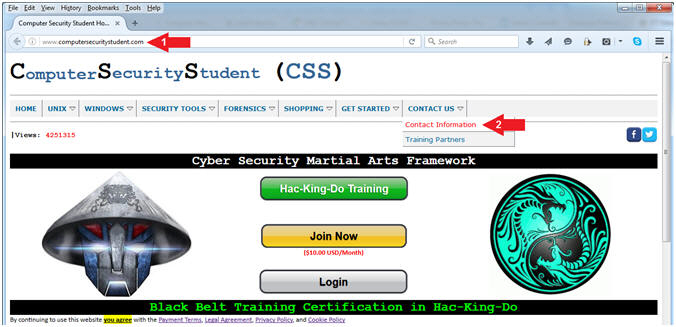
- Go to the following URL
- CONTACT US --> Contract Information
- Instructions:
- Email US
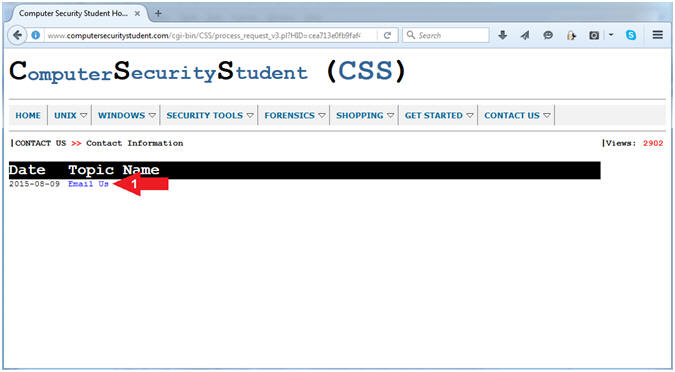
- Instructions:
- Click on Email US
- Instructions:
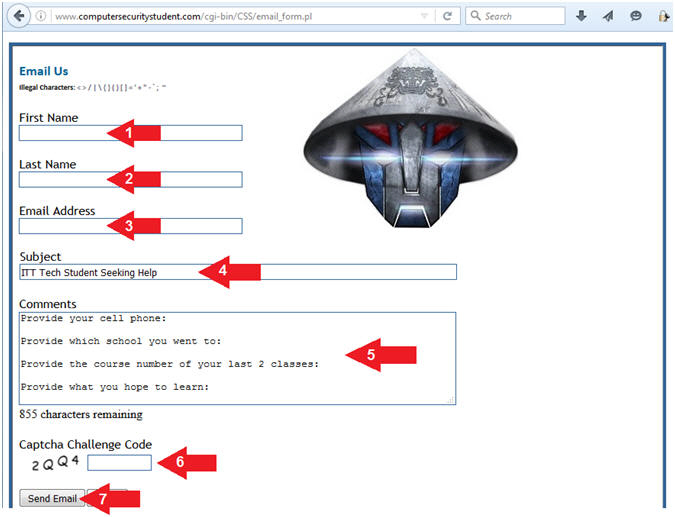
- Fill Out The Email Form
- Instructions:
- First Name: Please provide your real first name
- Last Name: Please provide your real last name
- Email: Please provide your real working email address
- Subject: ITT Tech Student Seeking Help
- Comments:
- Please provide your cell phone, so we can call you.
- Please provide the ITT Tech school that you went to.
- Please provide the course number of your last 2 classes at ITT Tech, along with your past instructors name.
- Please provide what areas of Cyber Security you are most interested in learning about.
- Captcha Challenge Code: Provide the correct code
- Click the Send Email button
- Instructions:
- We Will Contact You
- Note(FYI):
- Arrow #1: We will do our best to get back with you within 24 to 48 hours.
- Please, do not register, until we contact you. Our virtual seats are limited, and we want to make sure that we can provide you with a truly rewarding experience without any additional frustrations that you have already experienced.
- Note(FYI):
| Section 2. Our Philospy |
- What is Hac-King-Do?
- Computer Security Student, LLC is pleased to offer a unique training certification in "Hac-King-Do (HKD)", which is a "Cyber Security Martial Arts Framework."
- Hac-King-Do bridges the gap between theory and actual hands-on experience.
- As you might know, becoming a Cyber Security Professional does not happen over night. There is a Karate Kid "WaxOn[1] / WaxOff[0]" approach that not only needs to occur from the ground up to create a strong foundation, but also requires daily practice to acquire discipline.


- Hands-On Philosophy
- Hac-King-Do is very similar to the Korean
Tae Kwon Do Martial Arts Methodology in which a student must complete
all the lessons under the White Belt in order to be promoted to Yellow
Belt and eventually to a Level-1 Black Belt. The Level-1 Black Belt in
the Hac-King-Do curriculum includes over 130+ lessons in the following
Attack Vectors:
- (1) Installing, Breaking into, and Securing Operating Systems,
- (2) Penetration Testing,
- (3) Vulnerability Assessment,
- (4) Operating System and Web Application Exploitation, and
- (5) Forensics Investigation.
- Below are the learning activities associated with each belt level.
- Hac-King-Do is very similar to the Korean
Tae Kwon Do Martial Arts Methodology in which a student must complete
all the lessons under the White Belt in order to be promoted to Yellow
Belt and eventually to a Level-1 Black Belt. The Level-1 Black Belt in
the Hac-King-Do curriculum includes over 130+ lessons in the following
Attack Vectors:
|
Belt |
Learning | ||
|
|
Installing, Building and Password Clearing. (BackTrack, Kali, Damn Vulnerable Windows, Hiren's, Pogo Stick, CD and Grub Attacks). | ||
|
|
Penetration Testing (nmap); Vulnerability Assessment (Nessus); and Exploitation (Metasploit); and Sniffing. | ||
|
|
Fedora: Building, Breaking Into and Securing the Operating System & Applications. | ||
|
|
Damn Vulnerable Web App: Installing; JavaScript, SQL & Command Injections; Cross Site Scripting & Forgery; Burp Suite; Tamper Data; Man-In-The-Middle; Backdoor; Bruteforce. | ||
|
|
Metasploitable: Installing, OS Exploits, Database Exploits, Application Exploits, Volatility Profile Creation, Lime Memory Capture & more. | ||
|
|
Ubuntu: Building, Breaking Into and Securing the Operating System & Applications. | ||
|
|
Mutillidae: Installing; JavaScript, SQL & Command Injections; Cross Site Scripting & Forgery; Union Attacks; Burp Suite; Tamper Data; Cookie Harvesting; PHP Backdoor; Bruteforce & more. | ||
|
|
Advanced Metasploit (Windows and Application Attacks); Password Circumvention; Trojan Horse Creation; Forensics Preparation (Installing LosBuntu VM); Live Attack Capture. | ||
|
|
Forensics: File recovery; Collection; and Analysis. (Autopsy, FTK, Helix, WinPMEM, Lime, Volatility, MimiKatz, Foremost, Bmap, Steganography, Knoppix; Capturing Live Attacks & more) | ||
| Section 3. Accessing The Curriculum, Creating Help Tickets, Submitting Lessons |
- How To Access the Hac-King-Do Curriculum
- How to Create a CSS Help Ticket
- How to Create a Proof of Lab Submission Ticket
 Remember to WaxOn[1] and WaxOff[0] |