(Very Basic Perl Parsing #2: /var/log/auth.log)
{ Searching for SUDO}
| Background Information |
- Background
- The Authorization Log tracks usage of authorization systems, the mechanisms for authorizing users which prompt for user passwords, such as the Pluggable Authentication Module (PAM) system, the sudo command, remote logins to sshd and so on. The Authorization Log file may be accessed at /var/log/auth.log. This log is useful for learning about user logins and usage of the sudo command.
| Prerequisite |
- Login to your
TargetUbuntu02 VM, as username administrator
- For those of you that do not have access to my class, the TargetUbuntu02 VM is a Linux Ubuntu Operating System.
| Section 1: Creating a very very basic Perl Script To Parse /var/log/auth.log |
- Command:
vi parse_authlog2.pl
-
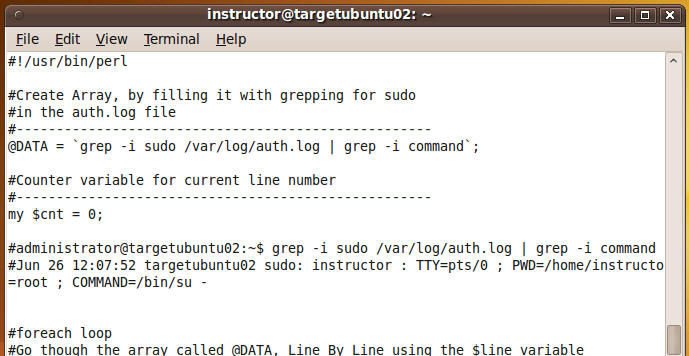
- Use the contents in the below
sample file to paste into your parse_auth2.pl
script.
- Command:
To save press the ESC Key, then type
:wq!
-
- Command:
chmod 700 parse_authlog2.pl
- chmod gives read, write and execute permissions to the perl script parse_authlog.pl
- Note: If a script does not have at least read(4) and execute(1) permission, then the script will not execute.
-
- Command:
./parse_authlog2.pl -OR- perl parse_authlog2.pl
- To execute a perl script you can do the
following
- ./parse_authlog.pl
-
- perl parse_authlog2.pl
-
- ./parse_authlog.pl
- To execute a perl script you can do the
following
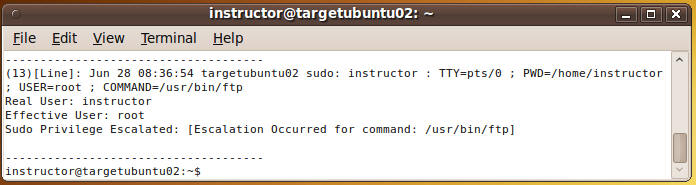
- Your contents should look like (See Below).
- Note: Pay attention to the USER and which COMMAND was run.
- It should be red flag that the usernames for "sudo: administrator" and "USER=root" are not both administrator.
-
| Proof of Lab |
- Do a screen print of Section 1, Step 6 into a word document and submit to Moodle.