(Tunnel HTTP Traffic Using Putty)
{ Putty, SSH, Firefox SOCK Proxy }
| Section 0: Background Information |
- Tunnel HTTP traffic using Putty and Firefox
SOCKS Proxy
- Sometimes companies block access to social networking and email websites. Occasionally, there might be a good reason to access your personal email during work.
- Or may be you are at a coffee shop and want to check your bank account on an open network.
- In either case, you can create a SSH tunnel using Putty between your PC and external server outside the network you are currently on. Then you can point your Firefox SOCKS Proxy to direct all traffic using the SSH Tunnel.
- Pre-Requisite Lab
- BackTrack: Lesson 1: Installing BackTrack 5 R1
-
BackTrack: Lesson 8: Configuring the SSH Server
- Do If Putty Cannot Connect to BackTrack
-
Lab Notes
- In this lab we will do the following:
- Create and Configure a Putty SSH Tunnel
- Configure Firefox SOCK Proxy
- Test if traffic is still blocked
- In this lab we will do the following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- Your are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2012 No content replication of any kind is allowed without express written permission.
| Section 1: Power On PENTEST-WXP |
- Edit Virtual Machine Settings
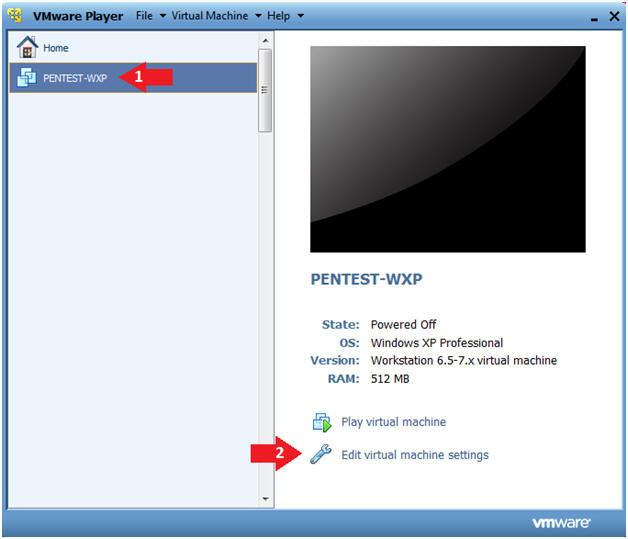
- Instructions:
- Click on PENTEST-WXP
- PENTEST-WXP is a Windows XP SP3 Virtual Machine.
- Click on Edit virtual machine
- Click on PENTEST-WXP
- Instructions:
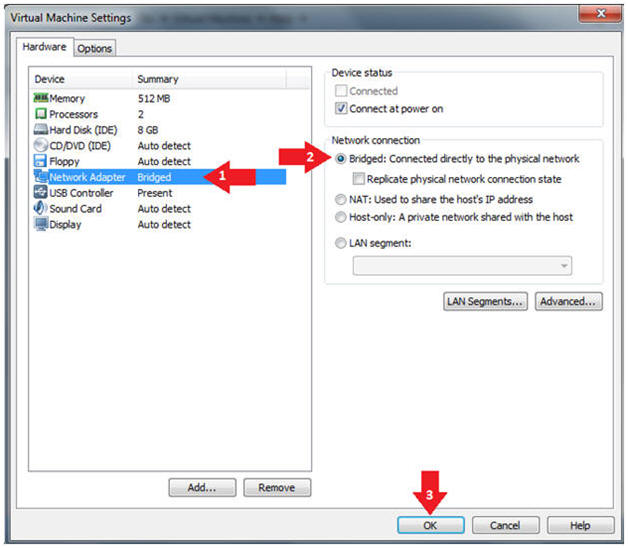
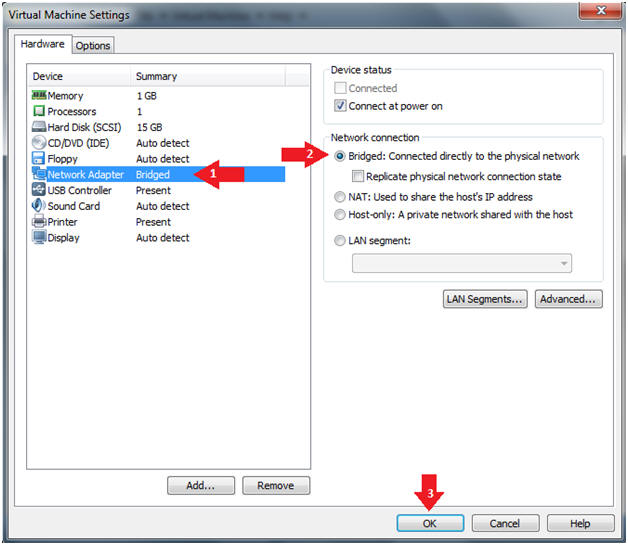
- Configure Network Adapter
- Instructions:
- Select Network Adapter
- Click the radio button "Bridged: Connected directly to the physical network."
- Click the Okay button
- Instructions:
- Start PENTEST-WXP
- Instructions:
- Click on PENTEST-WXP
- Click on Play virtual machine
- Instructions:
- Send Ctrl+Alt+Del
- Instructions:
- Virtual Machine --> Send Ctrl+Alt+Del
- Instructions:
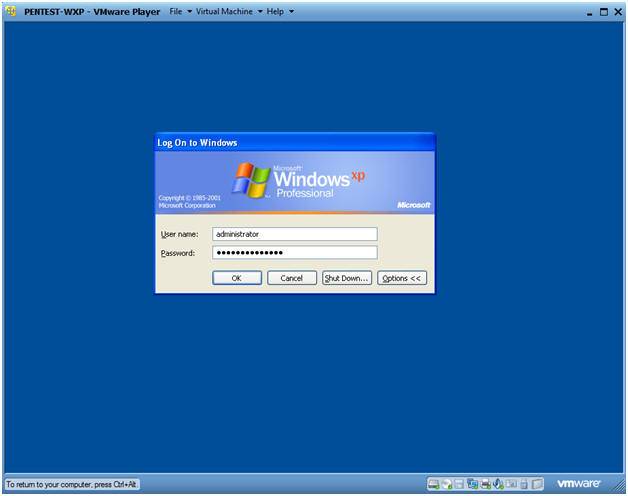
- Logging into PENTEST-WXP.
- Instructions:
- Username: administrator
- Password: Provide the Password
- Instructions:
- Open a Command Prompt
- Instructions:
- Start --> All Programs --> Accessories --> Command Prompt
- Instructions:
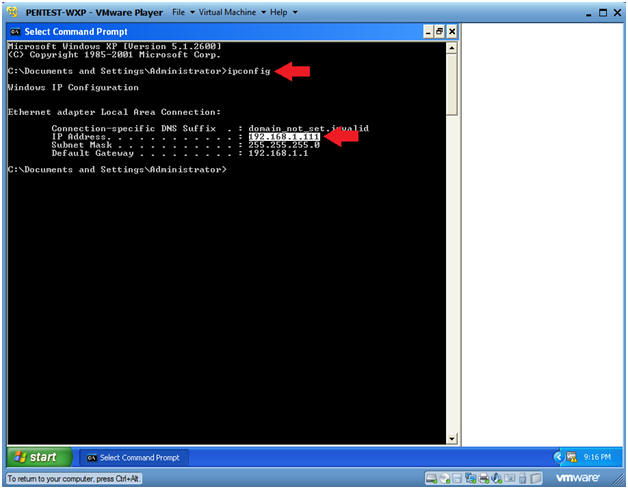
- Obtain PENTEST-WXP's IP Address
- Instructions:
- ipconfig
- Note(FYI):
- In my case, PENTEST-WXP's IP Address is 192.168.1.111.
- Your IP Address will be different.
- Instructions:
| Section 2: Power On BackTrack |
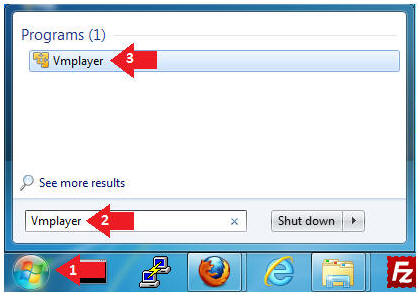
- Start Up VMWare Player
- Instructions:
- Click the Start Button
- Type Vmplayer in the search box
- Click on Vmplayer
- Instructions:
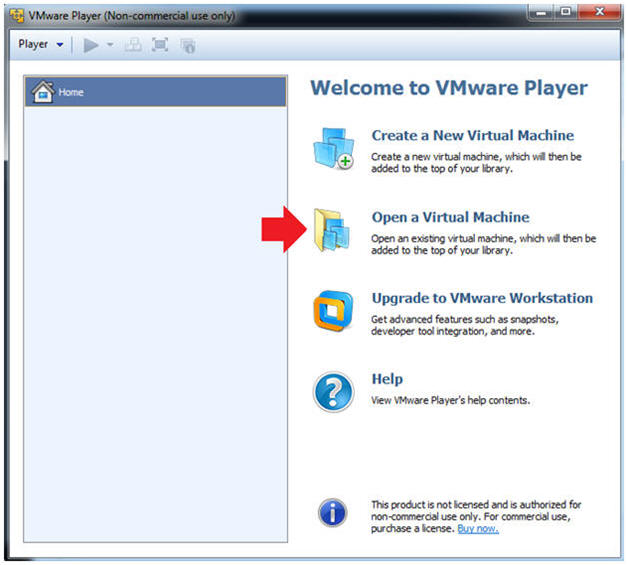
- Open a Virtual Machine
- Instructions:
- Click on Open a Virtual Machine
-
- Instructions:
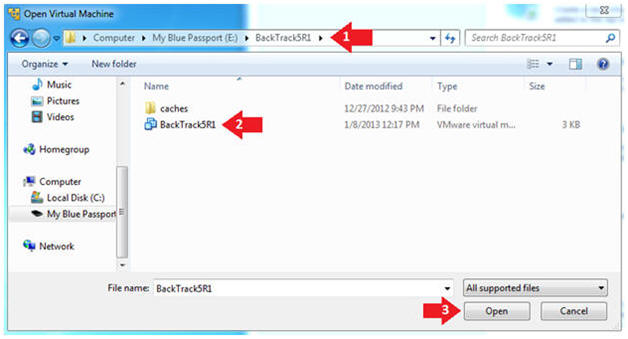
- Open the BackTrack5R1 VM
- Instructions:
- Navigate to where the BackTrack5R1 VM is located
- Click on on the BackTrack5R1 VM
- Click on the Open Button
-
- Instructions:
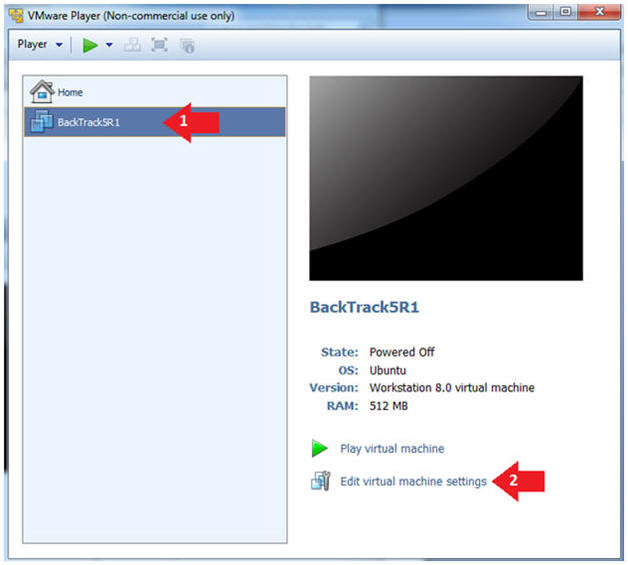
- Edit the BackTrack5R1 VM
- Instructions:
- Select BackTrack5R1 VM
- Click Edit virtual machine settings
-
- Instructions:
- Edit Virtual Machine Settings
- Instructions:
- Click on Network Adapter
- Click on the Bridged Radio button
- Click on the OK Button
- Instructions:
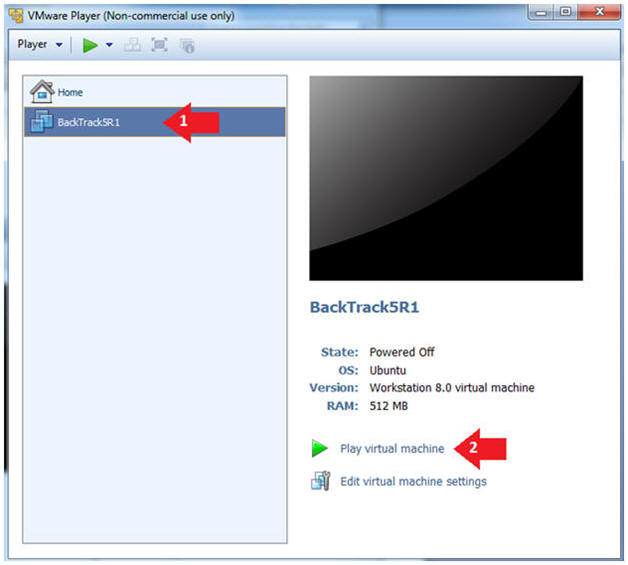
- Play the BackTrack5R1 VM
- Instructions:
- Click on the BackTrack5R1 VM
- Click on Play virtual machine
-
- Instructions:
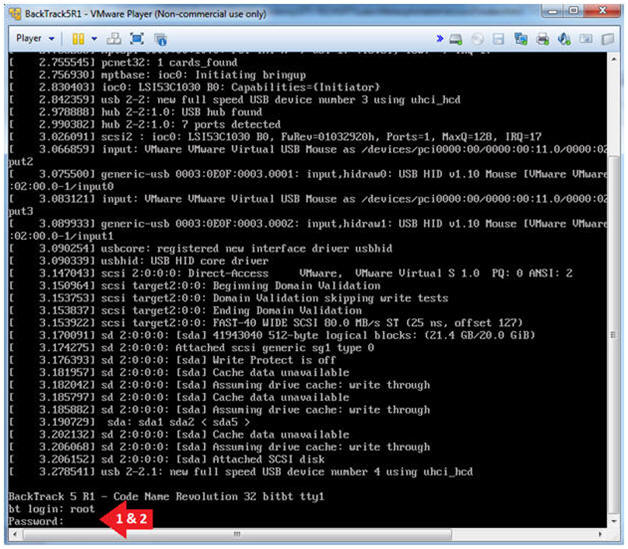
- Login to BackTrack
- Instructions:
- Login: root
- Password: toor or <whatever you changed it to>.
-
- Instructions:
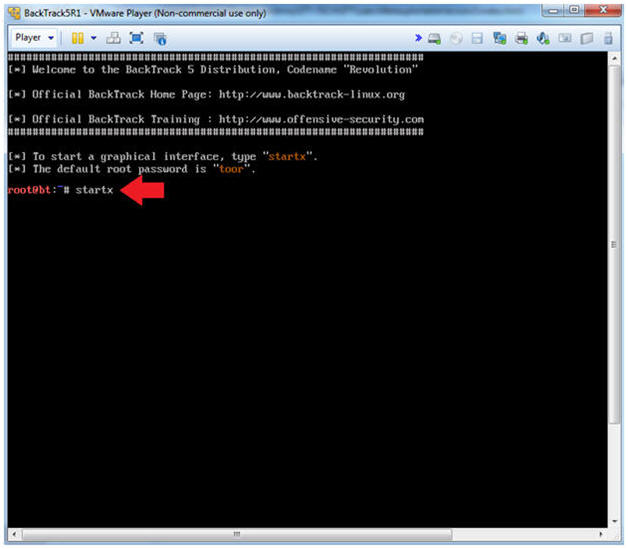
- Bring up the GNOME
- Instructions:
- Type startx
-
- Instructions:
| Section 3: Bring up a console terminal |
- Start up a terminal window
- Instructions:
- Click on the Terminal Window
- Instructions:
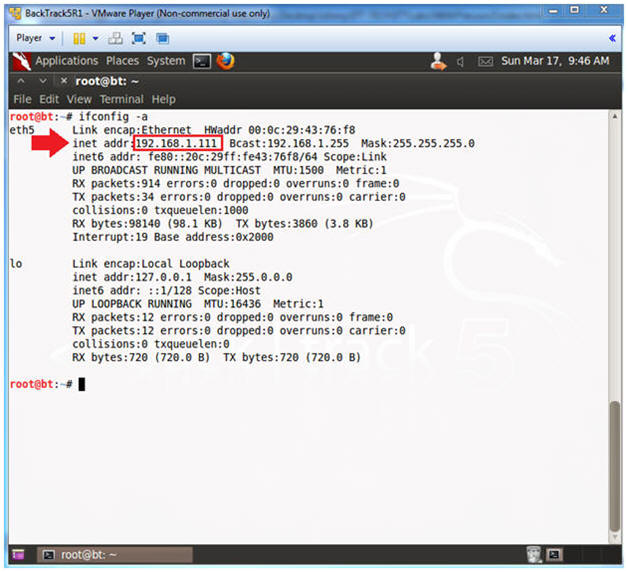
- Obtain the IP Address
- Instructions:
- ifconfig -a
- Note(FYI):
- My IP address 192.168.1.111.
- In your case, it will probably be different.
- Instructions:
| Section 4: Start the SSH Server |
- Start Up Putty
- Note(FYI):
- If SSHD does not start, follow the below directions.
- BackTrack: Lesson 8: Configuring the SSH Server
- Instructions:
- /etc/init.d/ssh start
- ps -eaf | grep sshd | grep -v grep
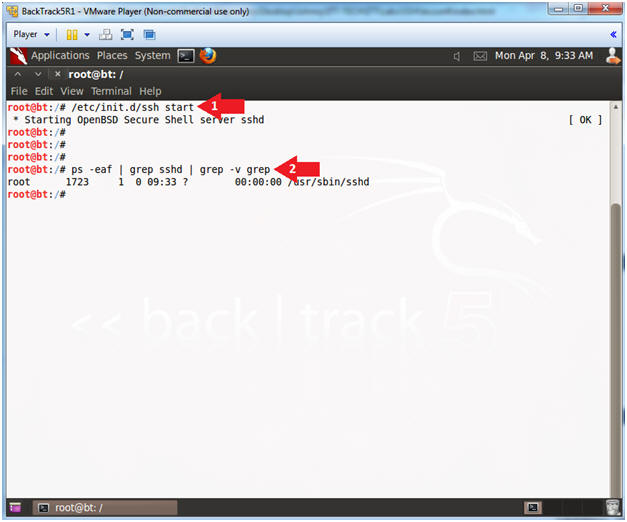
- Note(FYI):
| Section 5: Create Putty Tunnel |
- Start Up Putty
- Instructions:
- Click on Putty
- Instructions:
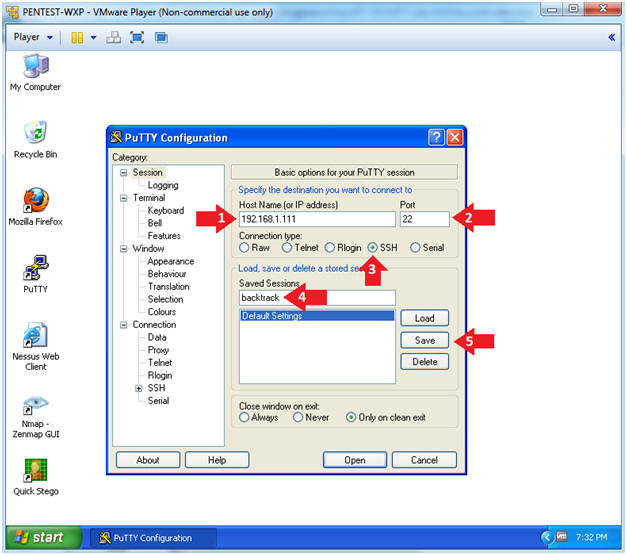
- Putty Basic Configuration
- Note(FYI):
- Replace 192.168.1.111 with BackTrack's IP Address obtained from (Section 3, Step 2).
- Instructions:
- Host Name: 192.168.1.111
- Port: 22
- Connection type: SSH
- Saved Sessions: backtrack
- Click the Save Button
- Note(FYI):
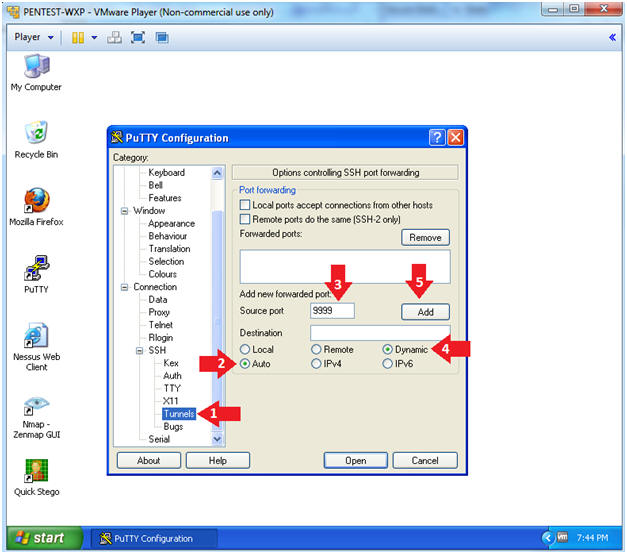
- Tunnel Configuration
- Instructions:
- Click on Connection --> SSH --> Tunnels
- Click on the Auto Radio Button
- Source port: 9999
- Click on the Dynamic Radio Button
- Click on the Add Button
- Instructions:
- Enable Logging
- Instructions:
- Click on Session --> Logging
- Session Logging: Click on the radio button "All session output"
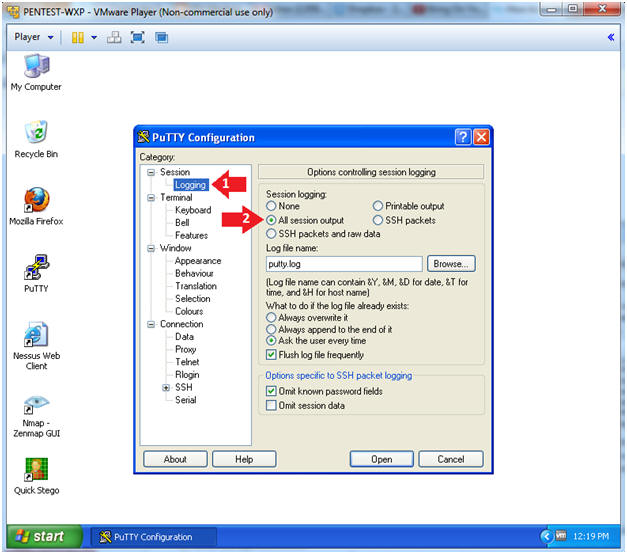
- Instructions:
- Open Session
- Instructions:
- Click on Session
- Click the Save Button
- Click the Open Button
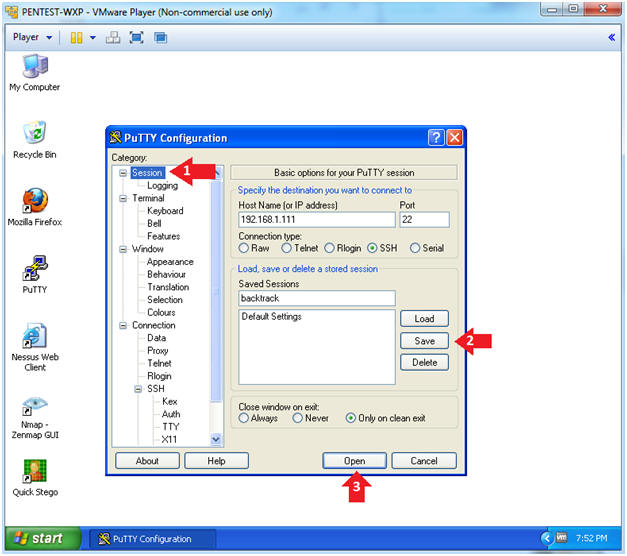
- Instructions:
- Putty Security Alert
- Instructions:
- Click the Yes Button
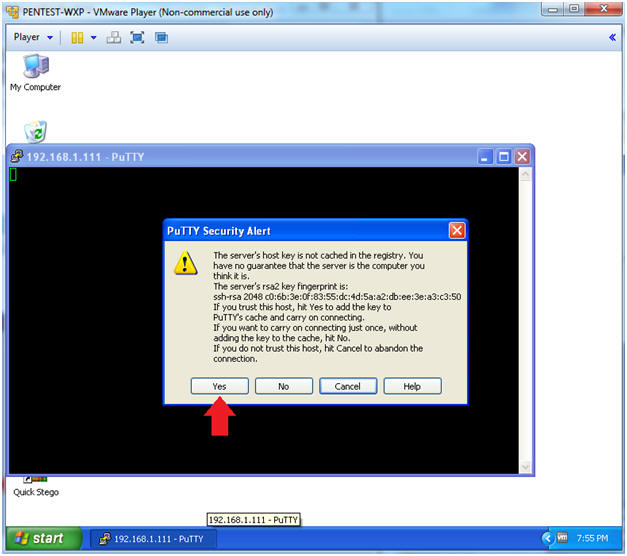
- Instructions:
- Login to BackTrack
- Instructions:
- Login: root
- Password: <Supply Password>
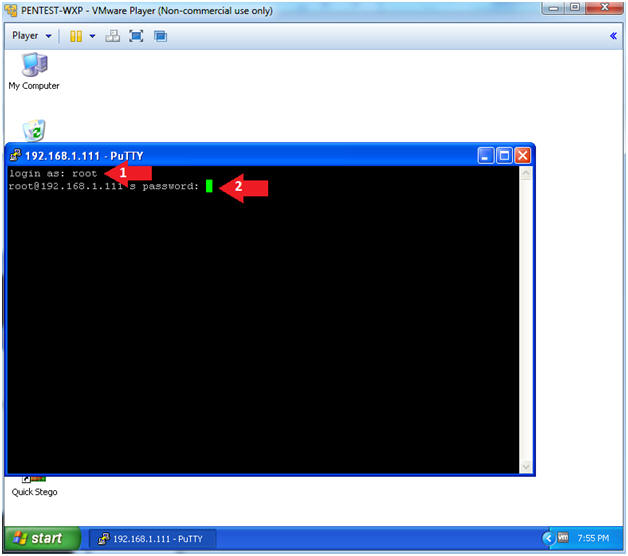
- Instructions:
| Section 5: Configure Firefox Proxy Settings |
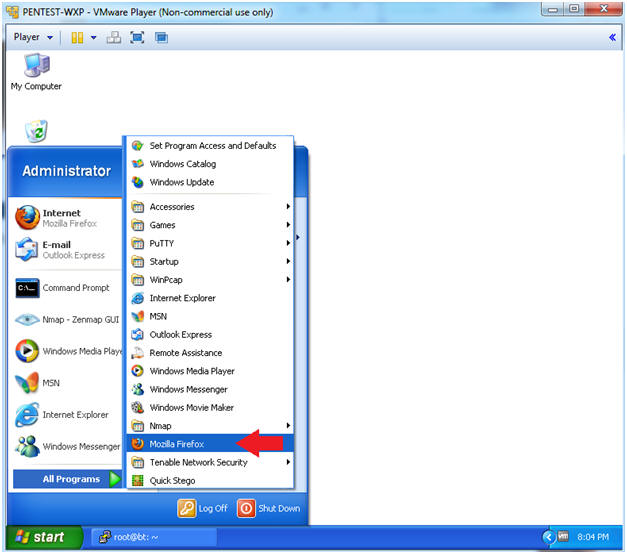
- Open Firefox
- Instructions:
- Start --> All Programs --> Mozilla Firefox
- Instructions:
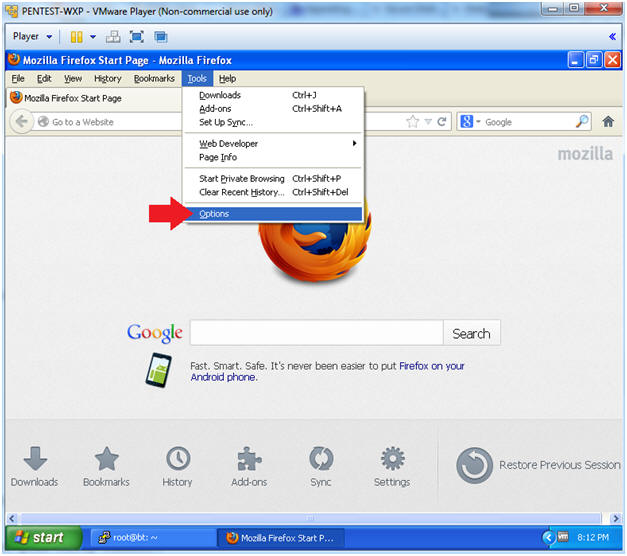
- Open Options
- Instructions:
- Tools --> Options
- Instructions:
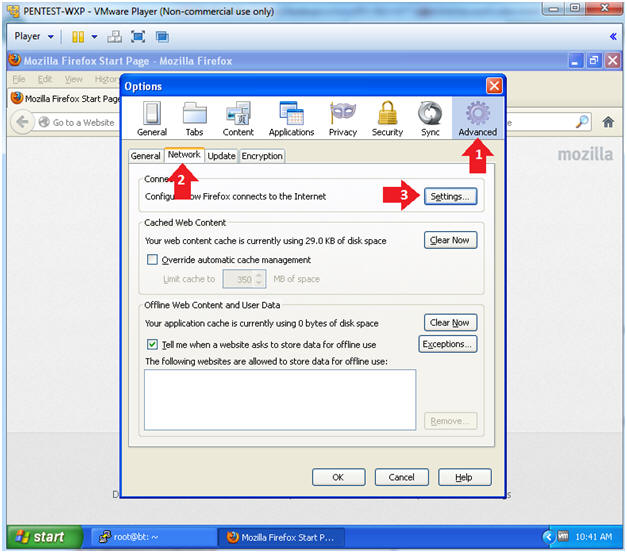
- Configure how Firefox connects to the Internet
- Instructions:
- Click Advanced
- Click the Network Tab
- Click the Settings button
- Instructions:
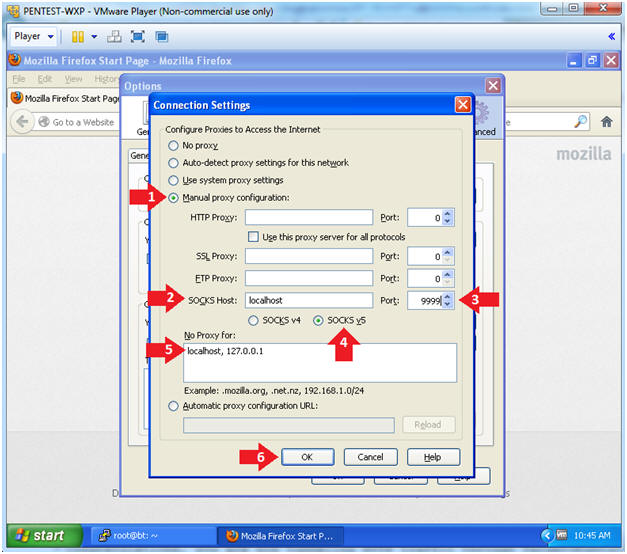
- Configure Firefox Proxy Settings
- Instructions:
- Click the radio button "Manual proxy configuration:"
- SOCKS Host: "localhost"
- Port: "9999"
- Click on the radio button "SOCKS v5"
- No Proxy for: "localhost, 127.0.0.1"
- Click the OK button
- Instructions:
- Close Out Options
- Instructions:
- Click the OK button
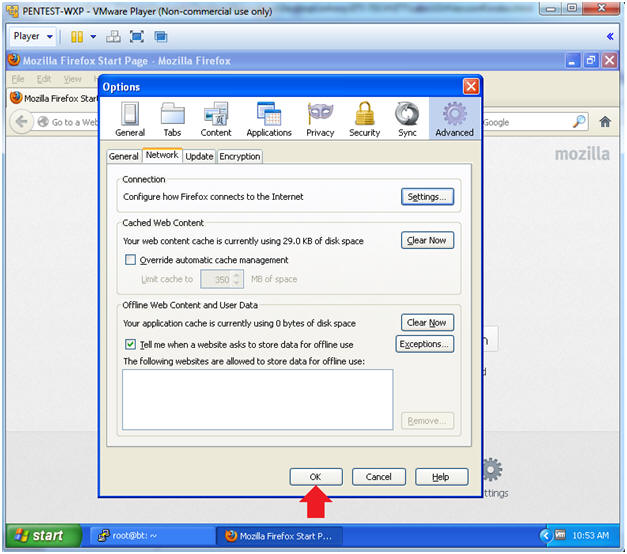
- Instructions:
| Section 6: Test Proxy Tunnel |
- Test Proxy Tunnel
- Instructions:
- Place the blocked URL (facebook,
youtube, etc) in the Address Textbox
- I used http://www.cnn.com
- Place the blocked URL (facebook,
youtube, etc) in the Address Textbox
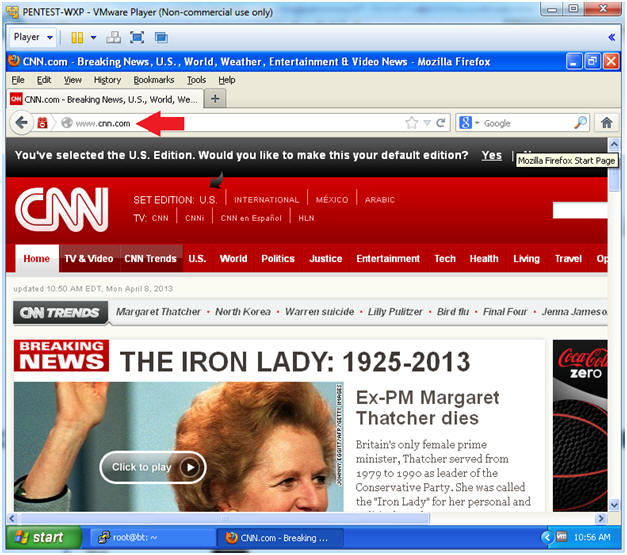
- Instructions:
| Section 7: View Putty Log |
- Open Event Log
- Instructions:
- Click on the Putty Icon
- Click on Event Log
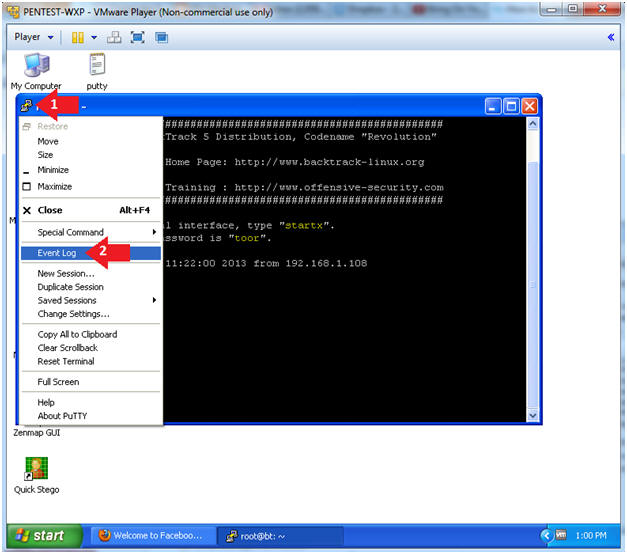
- Instructions:
- View the Event Log
- Instructions:
- Scroll through the event log from top to bottom. You will see how Firefox forward its traffic through the SSH tunnel over port 9999.
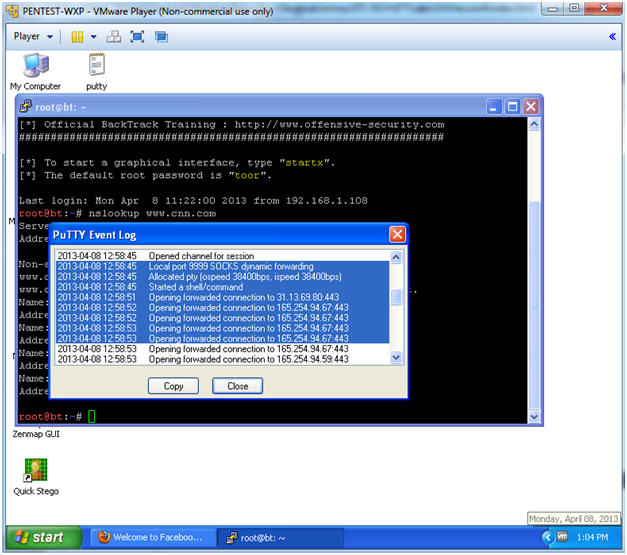
- Instructions:
| Section 8: Bring up a console terminal |
-
Proof of
Lab
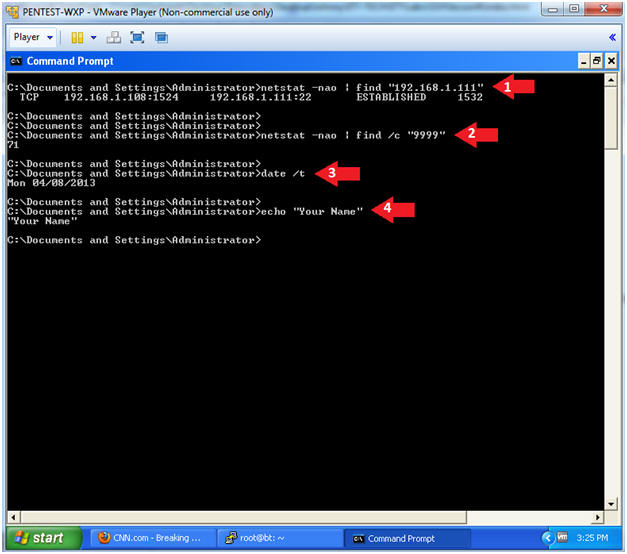
- Instructions:
- netstat -nao | find "192.168.1.108"
- Replace 192.168.1.108 with BackTrack's IP Address obtain from (Section x, Step y).
- netstat -nao | find /c "9999"
- date
- echo "Your Name"
- This should be your actual name.
- e.g., echo "John Gray"
- netstat -nao | find "192.168.1.108"
- Proof of Lab
Instructions:
- Do a PrtScn
- Paste into a word document
- Upload to Moodle
- Instructions: