(Perl: Lesson 8)
{ Policy Part 1: Parsing /etc/login.defs }
| Section 0. Background Information |
- What is /etc/login.defs?
- /etc/login.defs - This is a file used in conjunction with pam to configure /etc/shadow file.
- UMASK (number) - The permission mask is initialized to this value. If not specified, the permission mask will be initialized to 077.
- PASS_MAX_DAYS (number) - The maximum number of days a password may be used. If the password is older than this, a password change will be forced. If not specified, -1 will be assumed (which disables the restriction).
- PASS_MIN_DAYS (number) - The minimum number of days allowed between password changes. Any password changes attempted sooner than this will be rejected. If not specified, -1 will be assumed (which disables the restriction).
- Getting Perl
- For the purposes of these perl lesson, I will be using a perl package that comes standard on Backtrack, Ubuntu and most flavors of Linux and Unix.
- However, if you are using Windows, instead
of a Linux, Unix or MAC operating system, you still have options.
- Pre-Requisite
-
Lab
Notes
- In this lab we will do the following:
- We will download a program that contains various extraction examples for the strings "PASS_MAX_DAYS 99999" and "PASS_MAX_DAYS=99999".
- The program will provide extraction examples using split, the binding operator =~, and using the special perl back reference variables $1 and $2.
- In this lab we will do the following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- Your are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2013 No content replication of any kind is allowed without express written permission.
| Section 1. Login to BackTrack |
- Start Up VMWare Player
- Instructions:
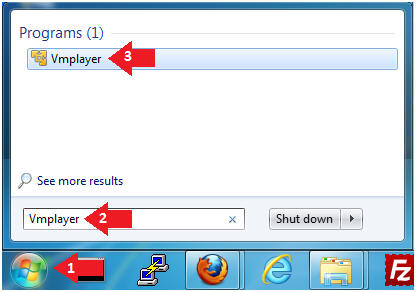
- Click the Start Button
- Type Vmplayer in the search box
- Click on Vmplayer
-
- Instructions:
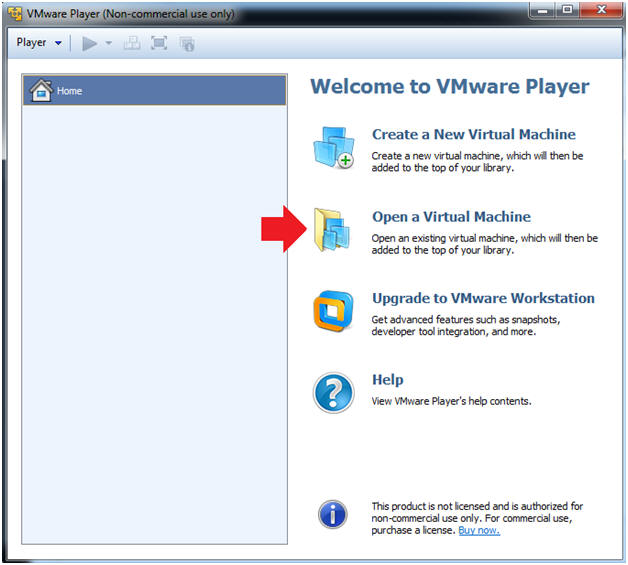
- Open a Virtual Machine
- Instructions:
- Click on Open a Virtual Machine
-
- Instructions:
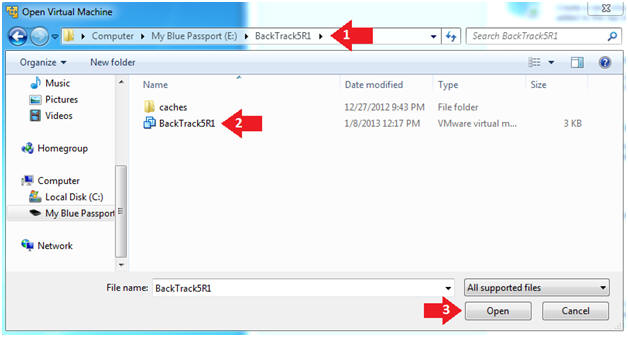
- Open the BackTrack5R1 VM
- Instructions:
- Navigate to where the BackTrack5R1 VM is located
- Click on on the BackTrack5R1 VM
- Click on the Open Button
-
- Instructions:
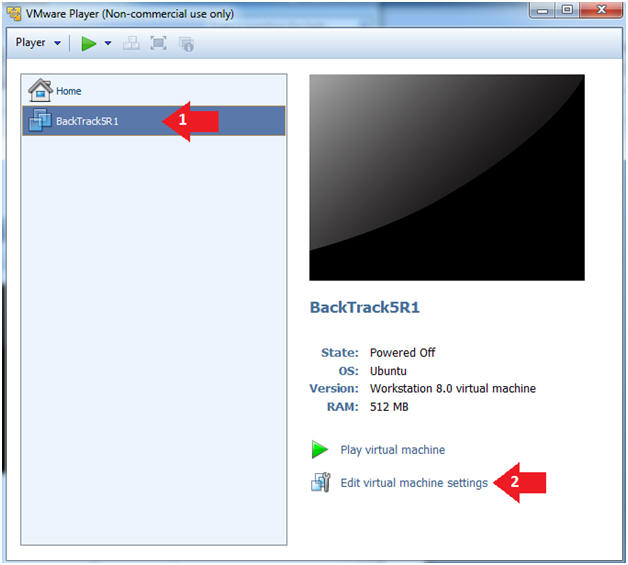
- Edit the BackTrack5R1 VM
- Instructions:
- Select BackTrack5R1 VM
- Click Edit virtual machine settings
-
- Instructions:
- Edit Virtual Machine Settings
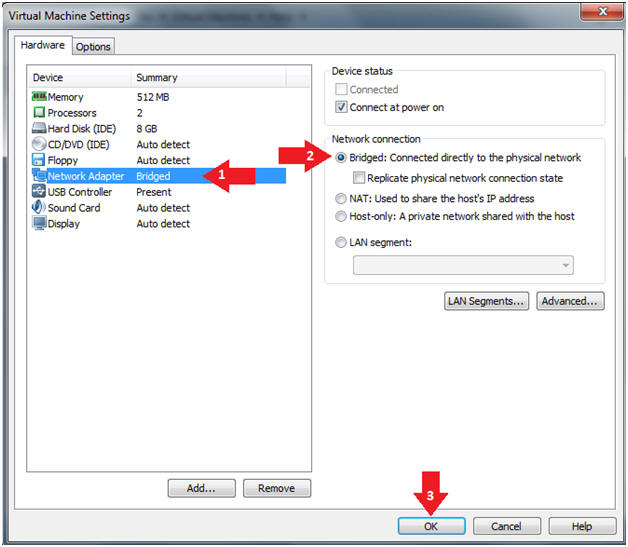
- Instructions:
- Click on Network Adapter
- Click on the Bridged Radio button
- Click on the OK Button
- Instructions:
- Play the BackTrack5R1 VM
- Instructions:
- Click on the BackTrack5R1 VM
- Click on Play virtual machine
-
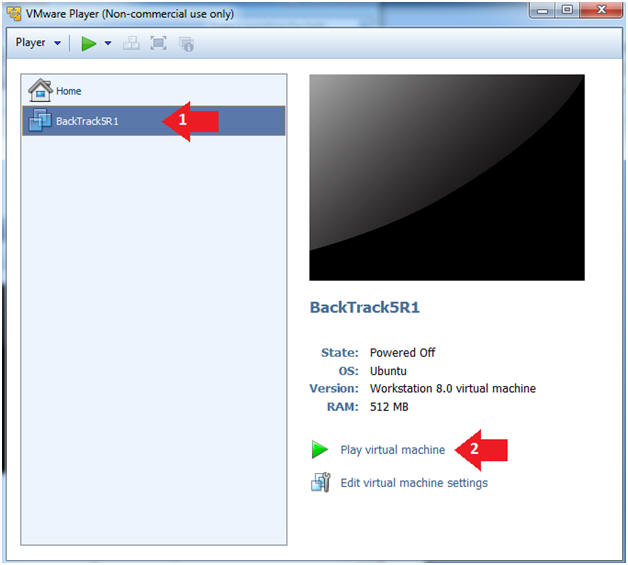
- Instructions:
- Login to BackTrack
- Instructions:
- Login: root
- Password: toor or <whatever you changed it to>.
-
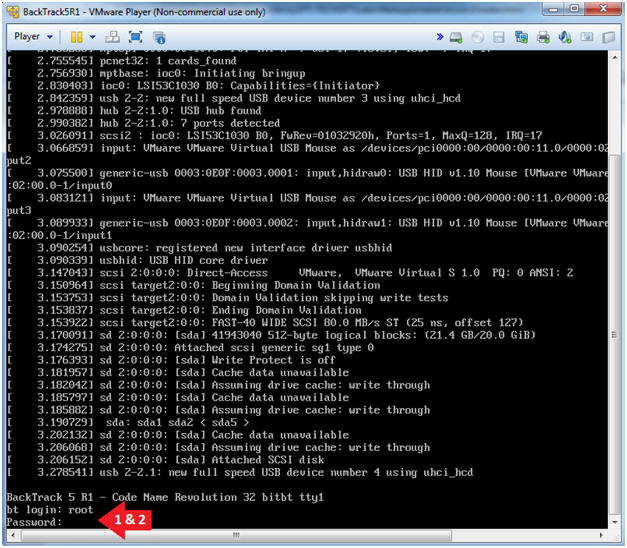
- Instructions:
- Bring up the GNOME
- Instructions:
- Type startx
-
- Instructions:
| Section 2. Bring up a console terminal |
- Start up a terminal window
- Instructions:
- Click on the Terminal Window
- Instructions:
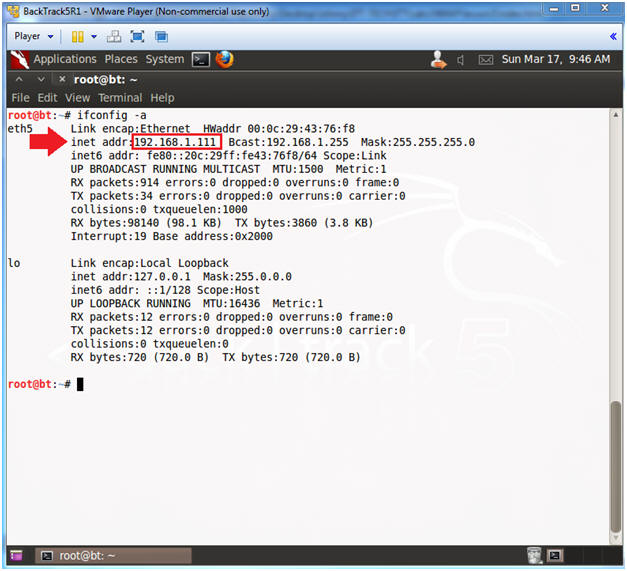
- Obtain the IP Address
- Instructions:
- ifconfig -a
- Note(FYI):
- My IP address 192.168.1.111.
- In your case, it will probably be different.
-
- Instructions:
| Section 3. Download scan_login.defs.pl |
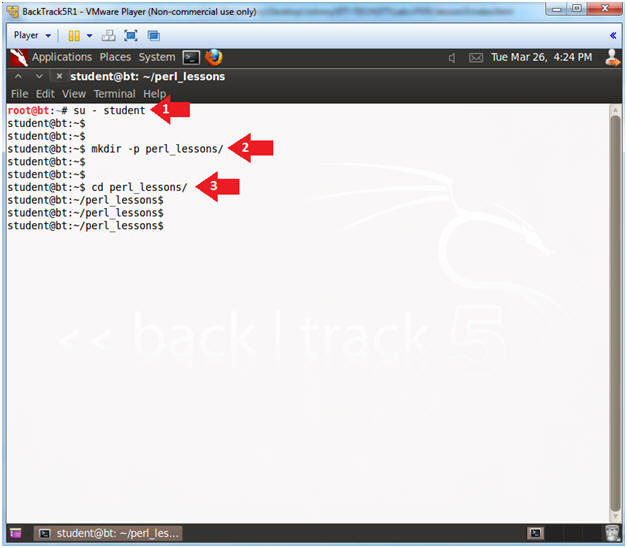
- Become the student user and make a directory
- Instructions:
- su - student
- mkdir -p perl_lessons
- cd perl_lessons
- Instructions:
- Download scan_login.defs.pl
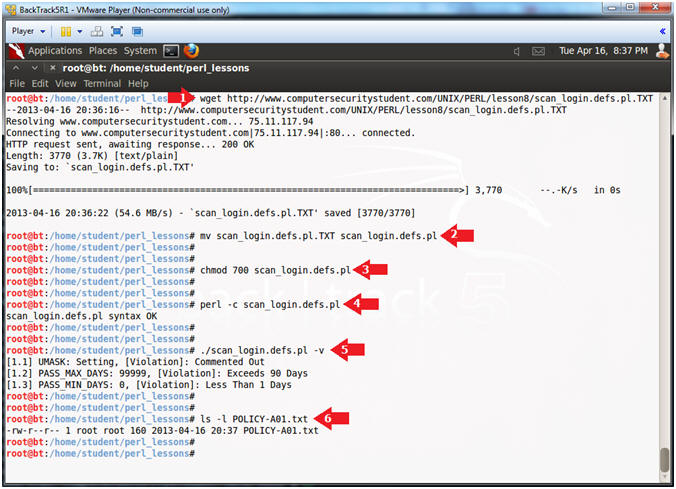
- Instructions:
- wget http://www.computersecuritystudent.com/UNIX/PERL/lesson8/scan_login.defs.pl.TXT
- mv scan_login.defs.pl.TXT scan_login.defs.pl
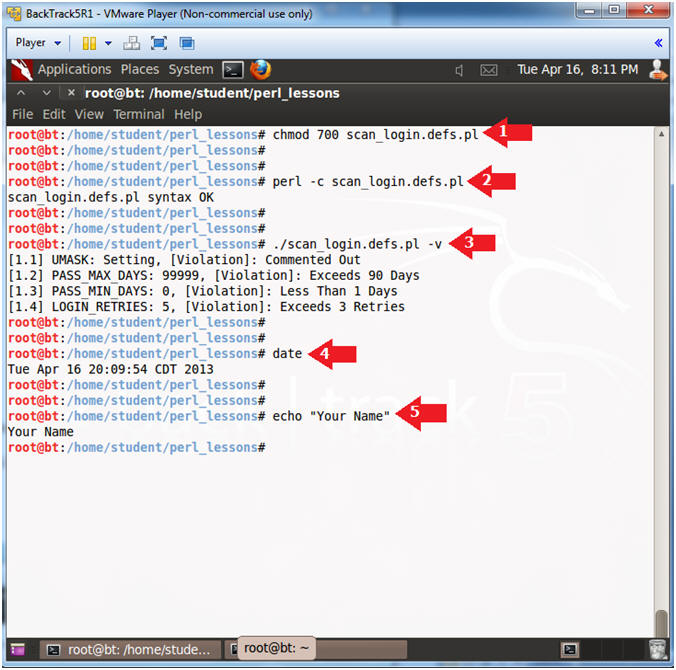
- chmod 700 scan_login.defs.pl
- perl -c scan_login.defs.pl
- ./scan_login.defs.pl -v
- ls -l POLICY-A01.txt
- Instructions:
| Section 4. Analyze The Code |
- SheBang Directive
- Instructions:
- vi scan_login.defs.pl
- :set nu
- Press the <Enter> key
- Note(FYI):
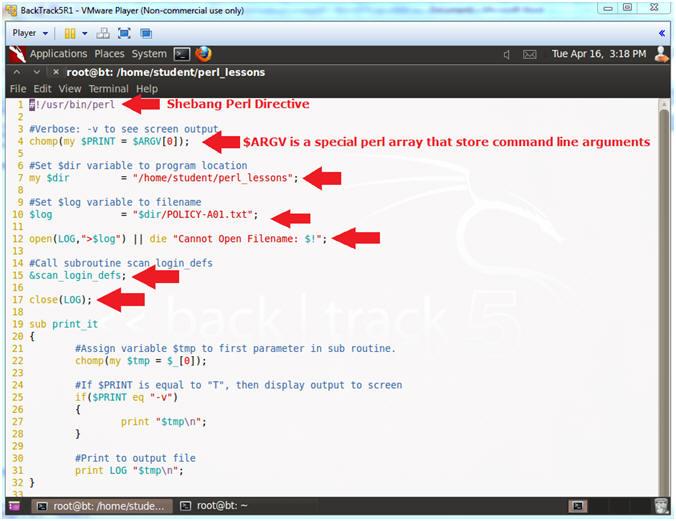
- Line 1: #!/usr/bin/perl
- #! - is called the SheBang Directive. SheBang is an interpreter directive that tells Linux to load the following program.
- /usr/bin/perl - is the Perl Interpreter. SheBang tells the program loader to run the Perl Interpreter.
- Line 4: chomp(my $PRINT = $ARGV[0]);
- $ARGV is a special perl array to receive command line arguments.
- $PRINT will be used to tell the program to output data to the screen.
- Line 7: my $dir = "/home/student/perl_lessons";
- Set the $dir variable to the directory location of the program.
- Line 10: $log = "$dir/POLICY-A01.txt";
- Set the $log variable to the output file name.
- Line 12: open(LOG,">$log") || die
"Cannot Open Filename: $!";
- Open the log file POLICY-A01.txt. LOG is the filehandle name. The greater than operator (>) mean to write to output.
- Line 15: &scan_login_defs;
- Execute the subroutine scan_login_defs.
- Line 17: close(LOG);
- Close the filehandle LOG, which is log file POLICY-A01.txt.
- Line 1: #!/usr/bin/perl
- Instructions:
- Explaining Lines 19 through 32
- Instructions:
- Arrow down to line 19
- Note(FYI):
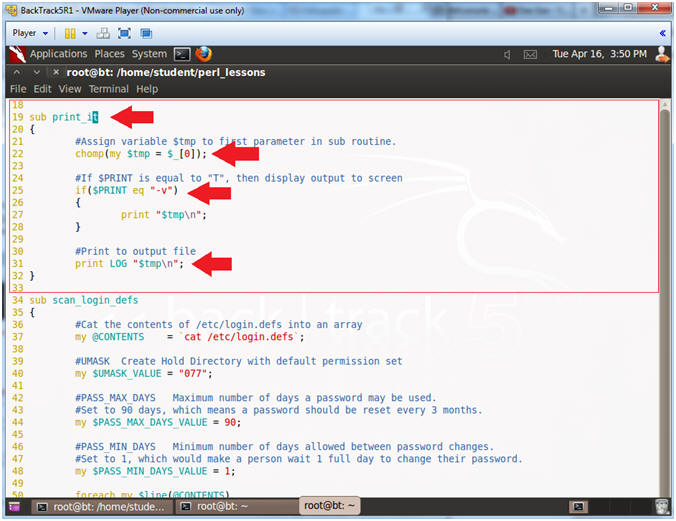
- Line 4, 20 & 32: sub print_it
- This subroutine has to actions: (1) Print to Output (line 31), and (2) Print to Screen (Lines 25 to 28).
- Line 22: chomp(my $tmp = $_[0]);
- Assign variable $tmp to first parameter.
- Line 25 - 28: if($PRINT eq "-v")
- If $PRINT is equal to -v, then print output to screen.
- Line 31: print LOG "$tmp\n";
- Print output to the filehandle LOG, which means print to the output file POLICY-A01.txt.
- Line 4, 20 & 32: sub print_it
- Instructions:
- Explaining Lines 34 through 48
- Instructions:
- Arrow down to line 34
- Note(FYI):
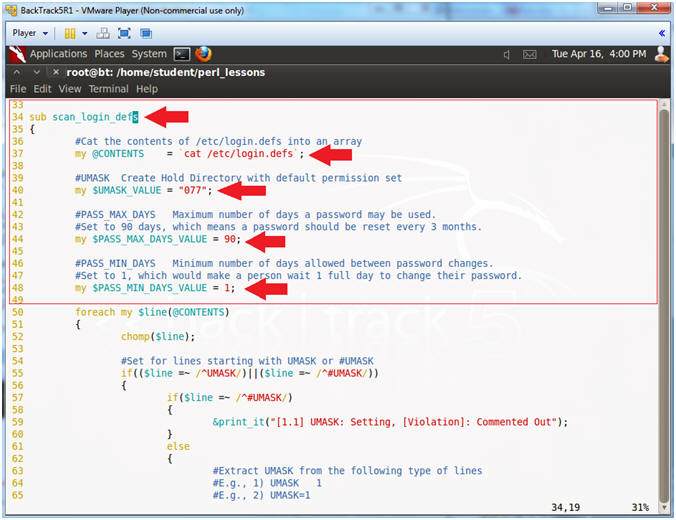
- Line 34: sub scan_login_defs
- The scan_login_defs subroutine scans the /etc/login.defs file.
- Line 37: my @CONTENTS = `cat /etc/login.defs`;
- This cats the contents of the /etc/login.defs file into an array.
- Line 40: my $UMASK_VALUE = "077";
- UMASK - Creates Home Directory with a default permission set. I.e., a user directory will be create with 700 permissions.
- Line 44: my $PASS_MAX_DAYS_VALUE = 90;
- $PASS_MAX_DAYS_VALUE is used as a threshold variable to determine if PASS_MAX_DAYS in the /etc/login.defs file is set higher than 90 days
- Line 48: my $PASS_MIN_DAYS_VALUE = 1;
- $PASS_MIN_DAYS_VALUE is used as a threshold variable to determine if PASS_MIN_DAYS in the /etc/login.defs file is set lower than 1 day.
- PASS_MIN_DAYS Minimum number of days allowed between password changes
- Line 34: sub scan_login_defs
- Instructions:
- Explaining Lines 50 through 52
- Instructions:
- Arrow down to line 50
- Note(FYI):
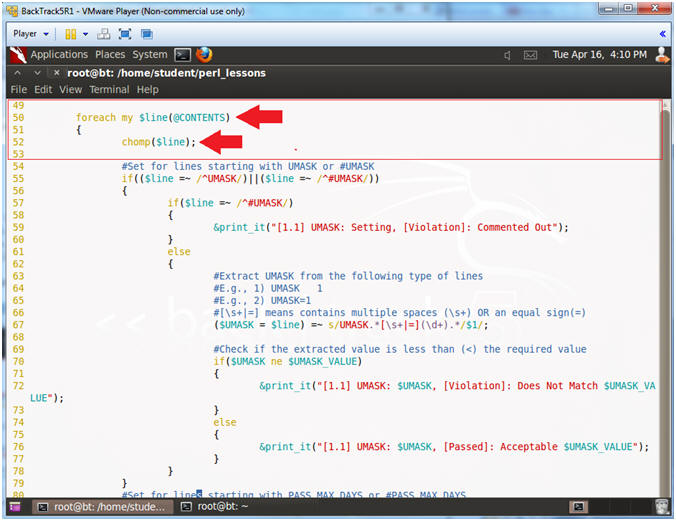
- Line 50: foreach my $line (@CONTENTS)
- This is a foreach loop. We will go through the array @CONTENTS line by line. Remember the @CONTENTS array contains the /etc/login.defs file.
- Line 22: chomp($line);
- Perl has a built in function called chomp that removes any end of line characters.
- Line 50: foreach my $line (@CONTENTS)
- Instructions:
- Explaining Lines 55 through 79
- Instructions:
- Arrow down to line 55
- Note(FYI):
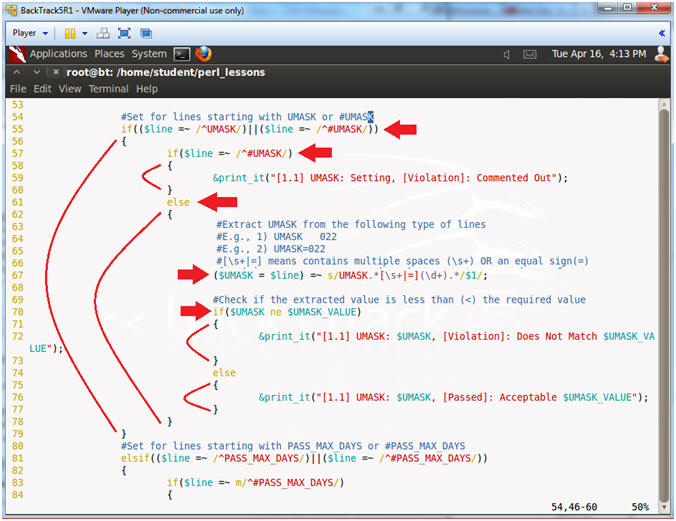
- Line 55: if(($line =~ /^UMASK/)||($line
=~ /^#UMASK/))
- Find a line that starts with either UMASK OR #UMASK. "^" means starts withs. "||" means OR.
- Line 57-60: if($line =~ /^#UMASK/)
- If line starts with #UMASK, then display Comment Out Violation.
- Line 61: else
- If line does not start with #UMASK, then go else clause.
- Line 67: ($UMASK
= $line) =~ s/UMASK.*[\s+|=](\d+).*/$1/;
- Find a match for a group of numbers, designated by (\d+), which occurs after the pattern "UMASK " or "UMASK=".
- [\s+|=] - Means one or more spaces OR an equal sign.
- Line 70: if($UMASK ne $UMASK_VALUE)
- If the extracted $UMASK value from line 67 is equal to the threshold value from line 40 are equal, print passed (line 76), else print violation (line 72).
- Line 55: if(($line =~ /^UMASK/)||($line
=~ /^#UMASK/))
- Instructions:
- Explaining Lines 81 through 105
- Instructions:
- Arrow down to line 81
- Note(FYI):
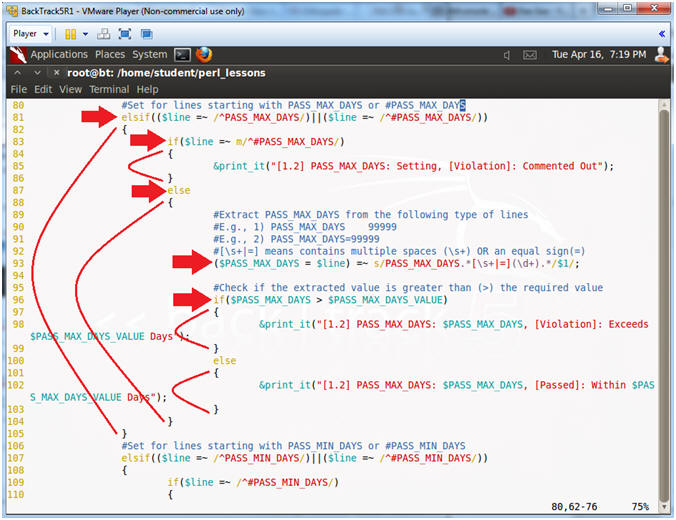
- Line 81:
if(($line =~ /^PASS_MAX_DAYS/)||($line =~ /^#PASS_MAX_DAYS/))
- Find a line that starts with either PASS_MAX_DAYS OR #PASS_MAX_DAYS. "^" means starts withs. "||" means OR.
- Line 83-86: if($line =~ /^#PASS_MAX_DAYS/)
- If line starts with #PASS_MAX_DAYS, then display Comment Out Violation.
- Line 87: else
- If line does not start with #UMASK, then go else clause.
- Line 93: ($PASS_MAX_DAYS
= $line) =~ s/PASS_MAX_DAYS.*[\s+|=](\d+).*/$1/;
- Find a match for a group of numbers, designated by (\d+), which occurs after the pattern "PASS_MAX_DAYS " or "PASS_MAX_DAYS=".
- [\s+|=] - Means one or more spaces OR an equal sign.
- Line 70: if($PASS_MAX_DAYS > $PASS_MAX_DAYS_VALUE)
- If the extracted $PASS_MAX_DAYS value from line 93 is greater than the threshold value from line 44, print violation (line 98), else print passed (line 102).
- Line 81:
if(($line =~ /^PASS_MAX_DAYS/)||($line =~ /^#PASS_MAX_DAYS/))
- Instructions:
- Explaining Lines 107 through 135
- Instructions:
- Arrow down to line 107
- Note(FYI):
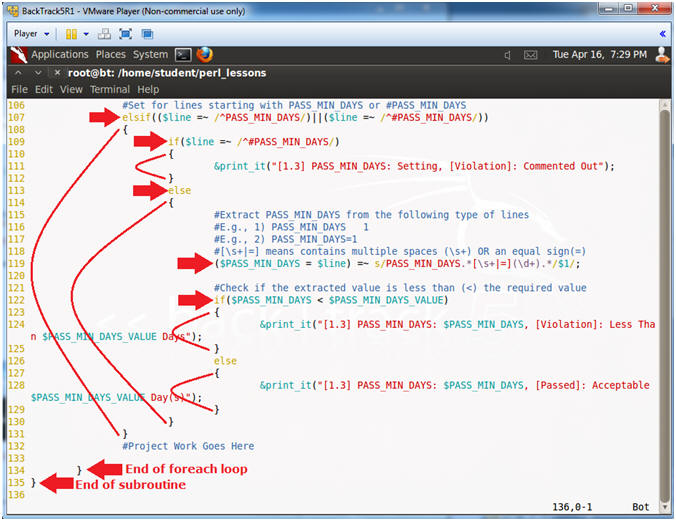
- Line 107:
if(($line =~ /^PASS_MIN_DAYS/)||($line =~ /^#PASS_MIN_DAYS/))
- Find a line that starts with either PASS_MIN_DAYS OR #PASS_MIN_DAYS. "^" means starts withs. "||" means OR.
- Line 109-112: if($line =~ /^#PASS_MIN_DAYS/)
- If line starts with #PASS_MIN_DAYS, then display Comment Out Violation.
- Line 113: else
- If line does not start with #PASS_MIN_DAYS, then go else clause.
- Line 119: ($PASS_MIN_DAYS
= $line) =~ s/PASS_MIN_DAYS.*[\s+|=](\d+).*/$1/;
- Find a match for a group of numbers, designated by (\d+), which occurs after the pattern "PASS_MIN_DAYS " or "PASS_MIN_DAYS=".
- [\s+|=] - Means one or more spaces OR an equal sign.
- Line 122: if($PASS_MIN_DAYS < $PASS_MIN_DAYS_VALUE)
- If the extracted $PASS_MIN_DAYS value from line 119 is less than the threshold value from line 48, print violation (line 124), else print passed (line 128).
- Line 134: {
- End of foreach loop
- Line 135: {
- End of subroutine
- Line 107:
if(($line =~ /^PASS_MIN_DAYS/)||($line =~ /^#PASS_MIN_DAYS/))
- Instructions:
- Save and Quit
- Instructions:
- Press the <Esc> key
- :q!
- Press the <Enter> key
- Instructions:
| Section 5. Proof of Lab |
- Project
- Instructions:
- cp scan_login.defs.pl scan_login.defs.pl.BKP
- Your project is interrogate the string "LOGIN_RETRIES 5" the same way the program interrogates the string "PASS_MAX_DAYS 99999".
- vi scan_login.defs.pl
- After the line that contains "my $PASS_MIN_DAYS_VALUE
= 1;", create a variable for LOGIN_RETRIES.
- my $LOGIN_RETRIES_VALUE = 3;
- After the line that contains "#Project
Work Goes Here", place the below code.
-
elsif(($line =~ /^LOGIN_RETRIES/)||($line =~ m/^#LOGIN_RETRIES/)) { if($line =~ /^#LOGIN_RETRIES/) { &print_it("[1.4] LOGIN_RETRIES: Setting, [Violation]: Commented Out"); } else { ($LOGIN_RETRIES = $line) =~ s/LOGIN_RETRIES.*[\s+|=](\d+).*/$1/; #Check if the extracted value is greater than (>) the required value if($LOGIN_RETRIES > $LOGIN_RETRIES_VALUE) { &print_it("[1.4] LOGIN_RETRIES: $LOGIN_RETRIES, [Violation]: Exceeds $LOGIN_RETRIES_VALUE Retries"); } else { &print_it("[1.4] LOGIN_RETRIES: $LOGIN_RETRIES, [Passed]: Within $LOGIN_RETRIES_VALUE Retries"); } } }
-
- Press <Esc>
- :wq!
- Instructions:
- Proof of Lab
- Instructions
- chmod 700 scan_login.defs.pl
- perl -c scan_login.defs.pl
- ./scan_login.defs.pl -v
- date
- echo "Your Name"
- Put in your actual name in place of "Your Name"
- e.g., echo "John Gray"
-
Proof Of Lab
Instructions:
- Press the <Ctrl><Alt> keys simultaneously
- Press the <PrtScn> key
- Paste into a word document
- Upload to Moodle
- Instructions