(Perl: Lesson 13)
{ Policy Part 6: Interrogate Local Listening Services }
| Section 0. Background Information |
- What is Local Listening Service?
- A Local Listening Services is also called a daemon running on the server that listens on a particular port.
- e.g., HTTP: tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN
- Getting Perl
- For the purposes of these perl lesson, I will be using a perl package that comes standard on Backtrack, Ubuntu and most flavors of Linux and Unix.
- However, if you are using Windows, instead
of a Linux, Unix or MAC operating system, you still have options.
- Pre-Requisite
-
Lab
Notes
- In this lab we will do the following:
- We will download a basic perl program that interrogates local running services on the server.
- The program will provide extraction examples using split.
- In this lab we will do the following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- Your are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2013 No content replication of any kind is allowed without express written permission.
| Section 1. Login to BackTrack |
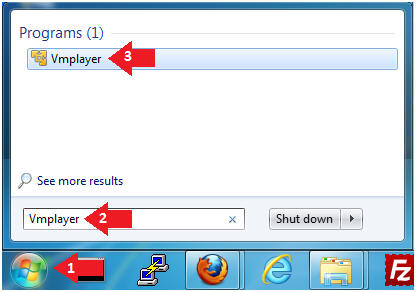
- Start Up VMWare Player
- Instructions:
- Click the Start Button
- Type Vmplayer in the search box
- Click on Vmplayer
-
- Instructions:
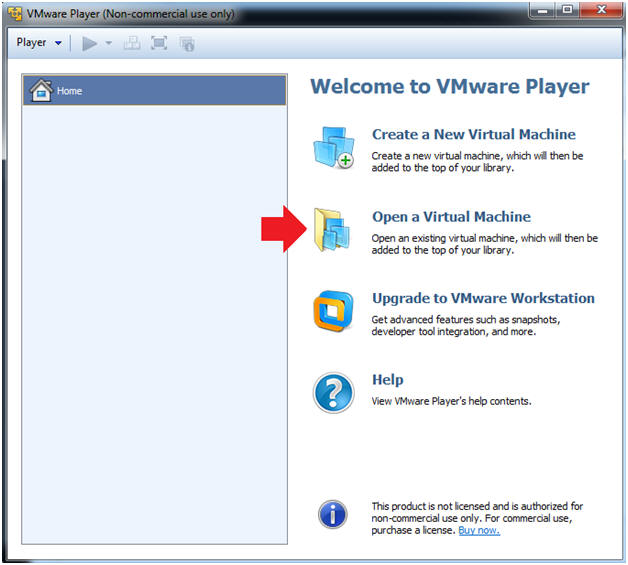
- Open a Virtual Machine
- Instructions:
- Click on Open a Virtual Machine
-
- Instructions:
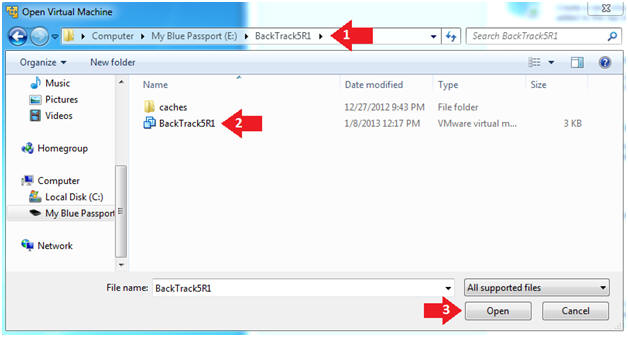
- Open the BackTrack5R1 VM
- Instructions:
- Navigate to where the BackTrack5R1 VM is located
- Click on on the BackTrack5R1 VM
- Click on the Open Button
-
- Instructions:
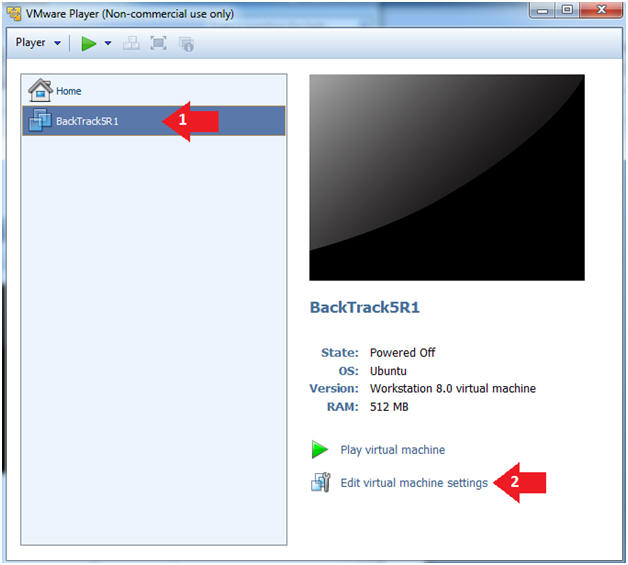
- Edit the BackTrack5R1 VM
- Instructions:
- Select BackTrack5R1 VM
- Click Edit virtual machine settings
-
- Instructions:
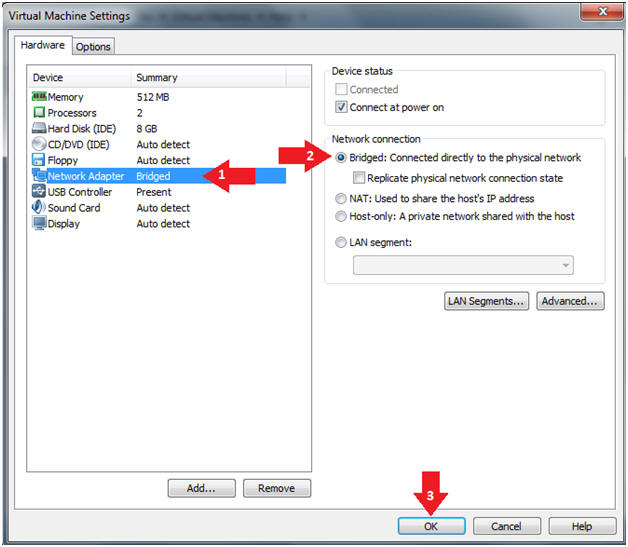
- Edit Virtual Machine Settings
- Instructions:
- Click on Network Adapter
- Click on the Bridged Radio button
- Click on the OK Button
- Instructions:
- Play the BackTrack5R1 VM
- Instructions:
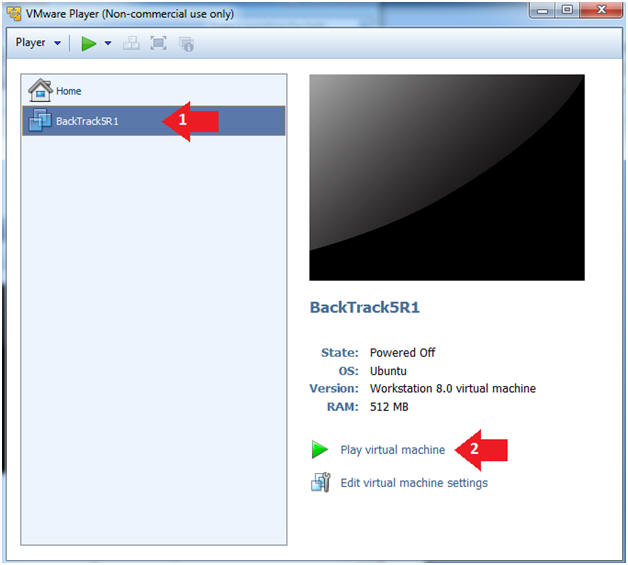
- Click on the BackTrack5R1 VM
- Click on Play virtual machine
-
- Instructions:
- Login to BackTrack
- Instructions:
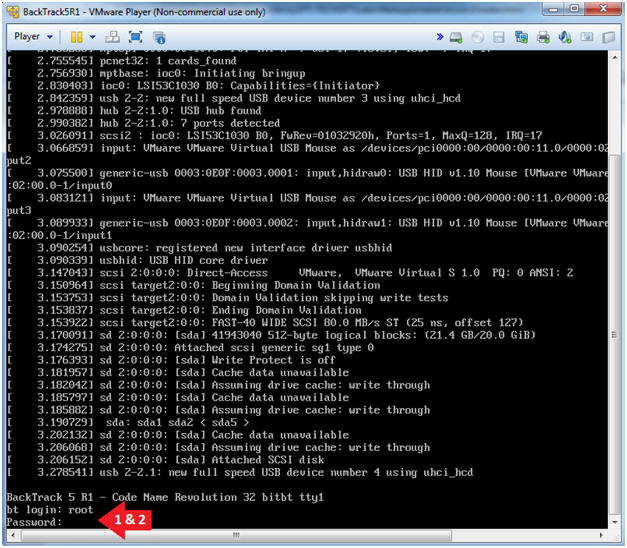
- Login: root
- Password: toor or <whatever you changed it to>.
-
- Instructions:
- Bring up the GNOME
- Instructions:
- Type startx
-
- Instructions:
| Section 2. Bring up a console terminal |
- Start up a terminal window
- Instructions:
- Click on the Terminal Window
- Instructions:
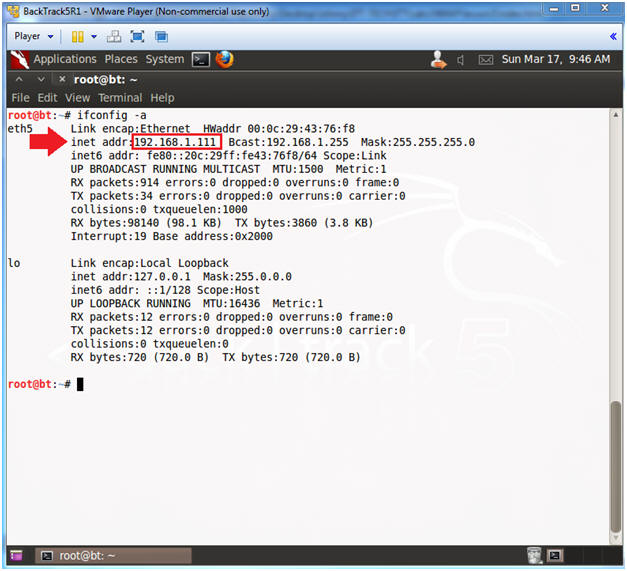
- Obtain the IP Address
- Instructions:
- ifconfig -a
- Note(FYI):
- My IP address 192.168.1.111.
- In your case, it will probably be different.
-
- Instructions:
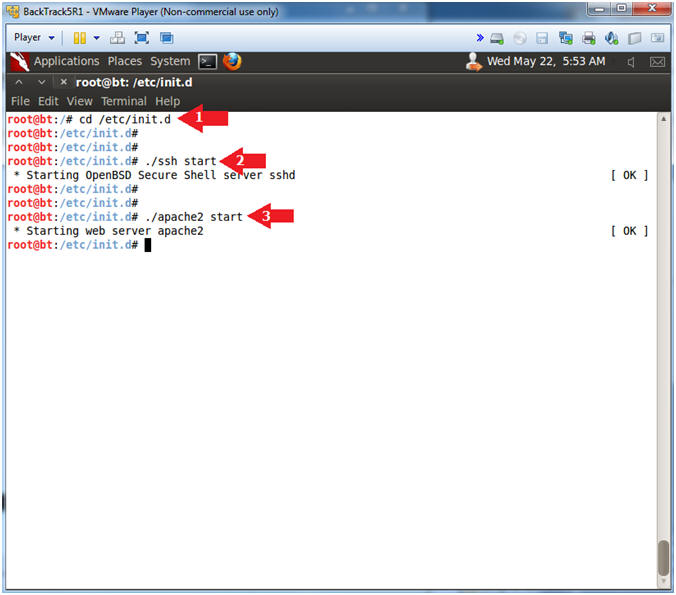
- Start SSH and Apache
- Note(FYI):
- We are starting SSH and Apache so the program will have some services to scan.
- Instructions:
- cd /etc/init.d
- ./ssh start
- ./apache2 start
- Note(FYI):
| Section 3. Download scan_running_services.pl |
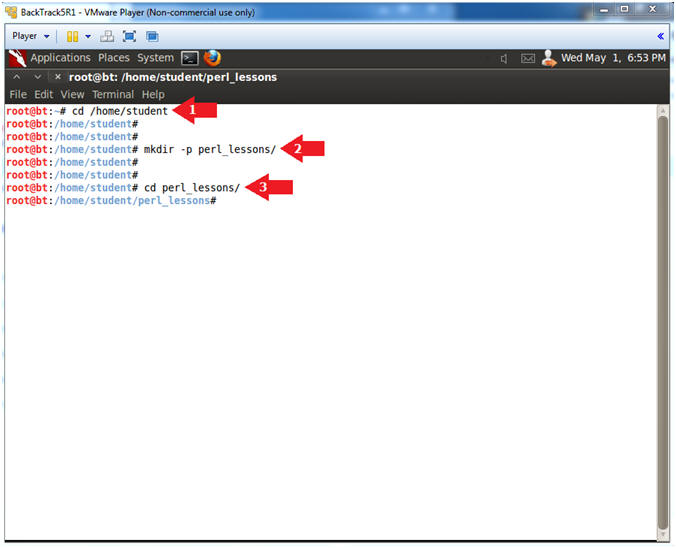
- Make a student directory
- Instructions:
- cd /home/student
- mkdir -p perl_lessons/
- cd perl_lessons/
- Instructions:
- Download scan_running_services.pl
- Instructions:
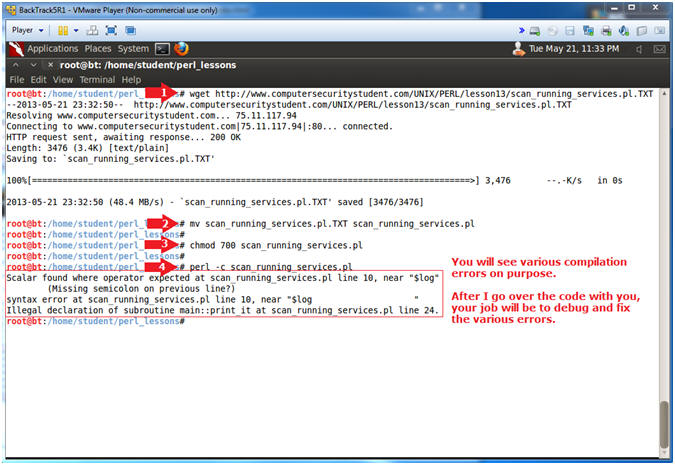
- wget http://www.computersecuritystudent.com/UNIX/PERL/lesson13/scan_running_services.pl.TXT
- mv scan_running_services.pl.TXT scan_running_services.pl
- chmod 700 scan_running_services.pl
- perl -c scan_running_services.pl
- Instructions:
| Section 4. Analyze The Code |
- SheBang Directive
- Instructions:
- vi scan_running_services.pl
- :set nu
- Press the <Enter> key
- Note(FYI):
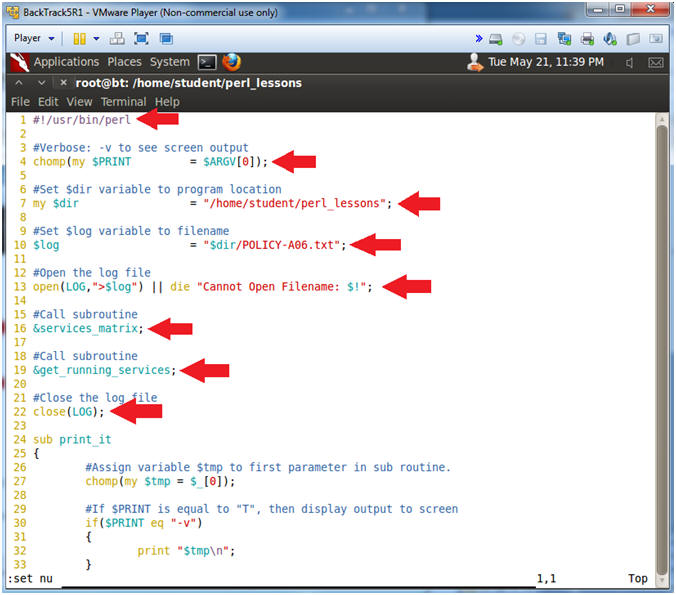
- Line 1: #!/usr/bin/perl
- #! - is called the SheBang Directive. SheBang is an interpreter directive that tells Linux to load the following program.
- /usr/bin/perl - is the Perl Interpreter. SheBang tells the program loader to run the Perl Interpreter.
- Line 4: chomp(my $PRINT = $ARGV[0]);
- $ARGV is a special perl array to receive command line arguments.
- $PRINT will be used to tell the program to output data to the screen.
- Line 7: my $dir = "/home/student/perl_lessons";
- Set the $dir variable to the directory location of the program.
- Line 10: $log = "$dir/POLICY-A04.txt";
- Set the $log variable to the output file name.
- Line 13: open(LOG,">$log") || die
"Cannot Open Filename: $!";
- Open the log file POLICY-A04.txt. LOG is the filehandle name. The greater than operator (>) mean to write to output.
- Line 16: &services_matrix;
- Execute the subroutine services_matrix.
- Line 19: &get_running_services;
- Execute the subroutine get_running_services.
- Line 22: close(LOG);
- Close the filehandle LOG, which is log file POLICY-A04.txt.
- Line 1: #!/usr/bin/perl
- Instructions:
- Explaining Lines 24 through 37
- Instructions:
- Arrow down to line 24
- Note(FYI):
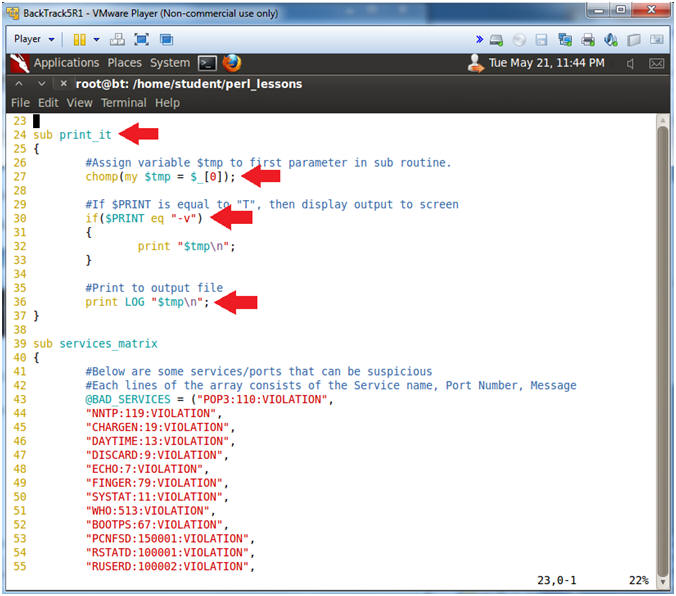
- Line 24 through 37: sub print_it
- This subroutine has two actions: (1) Print to Output (line 31), and (2) Print to Screen (Lines 25 to 28).
- Line 27: chomp(my $tmp = $_[0]);
- Assign variable $tmp to first parameter.
- Line 30 - 33: if($PRINT eq "-v")
- If $PRINT is equal to -v, then print output to screen.
- Line 36: print LOG "$tmp\n";
- Print output to the filehandle LOG, which means print to the output file POLICY-A06.txt.
- Line 24 through 37: sub print_it
- Instructions:
- Explaining Lines 39 through 65
- Instructions:
- Arrow down to line 39
- Note(FYI):
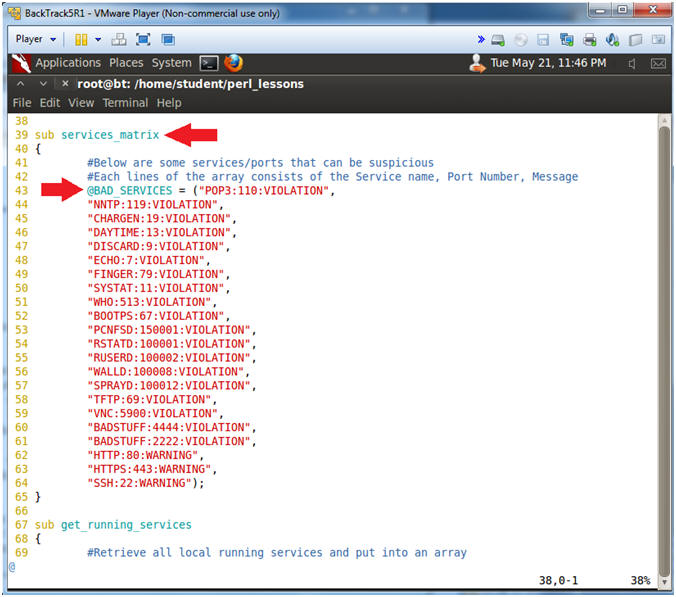
- Line 39: sub services_matrix
- The services_matrix subroutine create an array of all the ports/services that could be potentially malicious.
- Line 43: @BAD_SERVICES =
("POP3:110:VIOLATION",
- Each lines of the array consists of the Service name, Port Number, Message.
- Line 39: sub services_matrix
- Instructions:
- Explaining Lines 67 through 77
- Instructions:
- Arrow down to line 67
- Note(FYI):
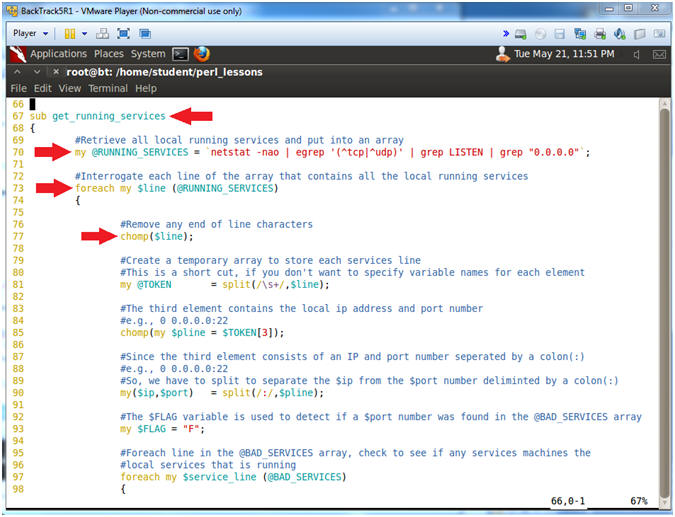
- Line 67: sub get_running_services
- This sub routine will interrogate each local running services against the @BAD_SERVICES array.
- Line 70:
my @RUNNING_SERVICES = `netstat -nao |
egrep '(^tcp|^udp)' | grep LISTEN | grep "0.0.0.0"`;
- Retrieve all local running services and put into an array.
- Line 73: foreach my $line (@RUNNING_SERVICES)
- Interrogate each line of the array that contains all the local running services.
- Line 77: chomp($line);
- Remove end of line characters.
- Line 67: sub get_running_services
- Instructions:
- Explaining Lines 81 through 93
- Instructions:
- Arrow down to line 81
- Note(FYI):
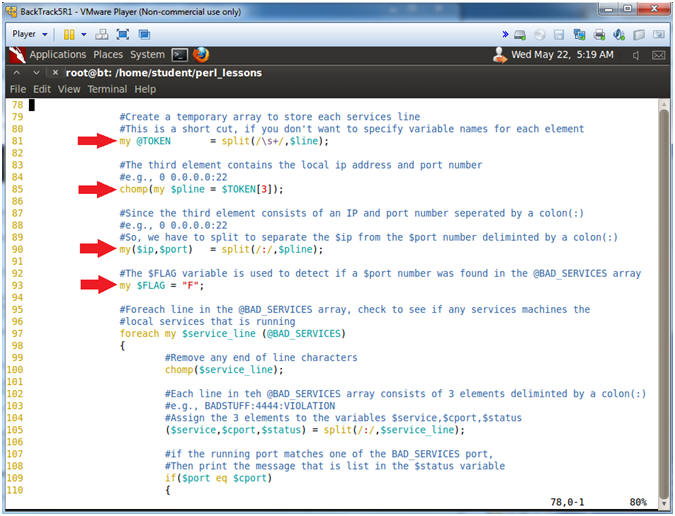
- Line 81: my @TOKEN =
split(/\s+/,$line);
- Create a temporary array to store each services line.
- This is a short cut, if you don't want to specify variable names for each element.
- Line 85: chomp(my $pline = $TOKEN[3]);
- The third element contains the local ip address and port number
- e.g., 0 0.0.0.0:22.
- Line 90: my($ip,$port) = split(/:/,$pline);
- Since the third element consists of an IP and port number seperated by a colon(:)
- e.g., 0 0.0.0.0:22
- So, we have to split to separate the $ip from the $port number deliminted by a colon(:)
- Line 93: my $FLAG = "F";
- The $FLAG variable is used to detect if a $port number was found in the @BAD_SERVICES array
- Line 81: my @TOKEN =
split(/\s+/,$line);
- Instructions:
- Explaining Lines 97 through 105
- Instructions:
- Arrow down to line 97
- Note(FYI):
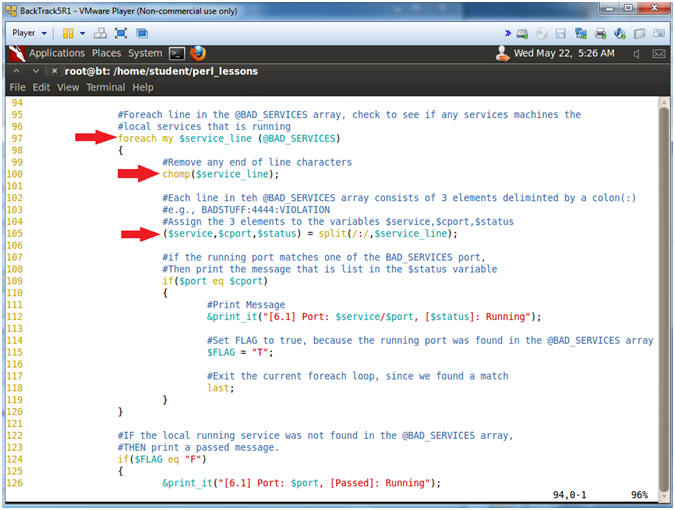
- Line 97: foreach my $service_line (@BAD_SERVICES)
- Foreach line in the @BAD_SERVICES array, check to see if any services machines the local services that is running.
- Line 98-118: chomp($service_line);
- Remove end of line characters.
- Line 105: ($service,$cport,$status) =
split(/:/,$service_line);
- Each line in teh @BAD_SERVICES array consists of 3 elements deliminted by a colon(:)
- e.g., BADSTUFF:4444:VIOLATION
- Assign the 3 elements to the variables $service,$cport,$status.
- Line 97: foreach my $service_line (@BAD_SERVICES)
- Instructions:
- Explaining Lines 109 through 118
- Instructions:
- Arrow down to line 109
- Note(FYI):
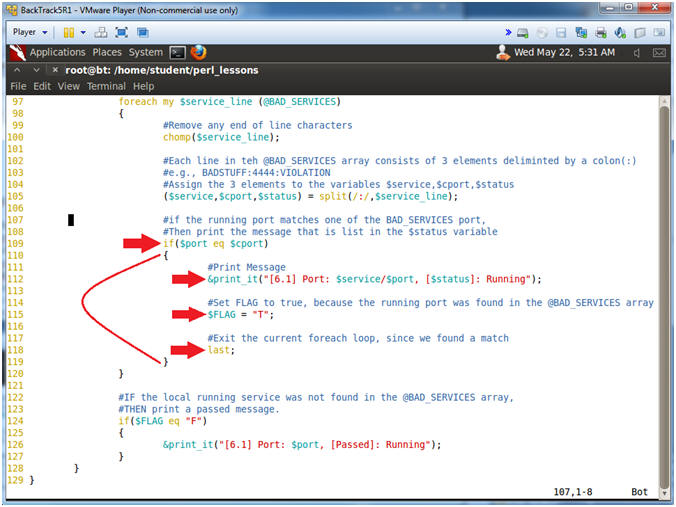
- Line 109-118: if($port eq $cport)
- IF the running port matches one of the BAD_SERVICES port, THEN print the message that is list in the $status variable.
- Line 112: &print_it("[6.1]
Port: $service/$port, [$status]: Running");
- Print Message.
- Line 115: $FLAG = "T";
- Set FLAG to true, because the running port was found in the @BAD_SERVICES array
- Line 118: last;
- Exit the current foreach loop, since we found a match
- Line 109-118: if($port eq $cport)
- Instructions:
- Explaining Lines 123 through 127
- Instructions:
- Arrow down to line 123
- Note(FYI):
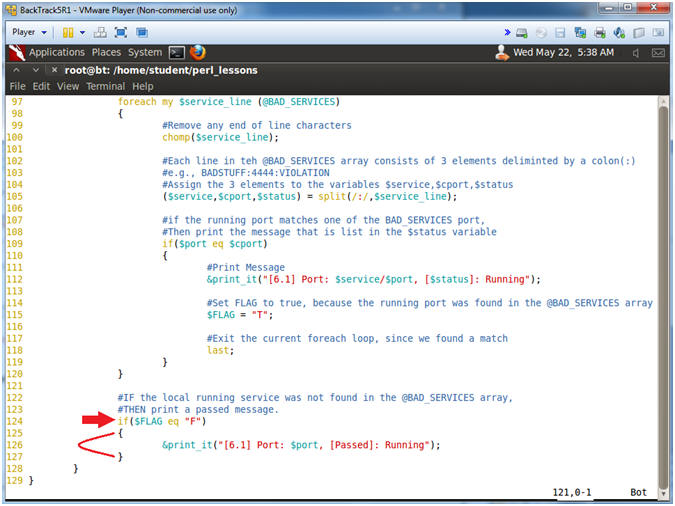
- Line 123-127: if($FLAG eq "F")
- IF the local running service was not found in the @BAD_SERVICES array,THEN print a passed message
- Line 123-127: if($FLAG eq "F")
- Instructions:
- Save and Quit
- Instructions:
- Press the <Esc> key
- :q!
- Press the <Enter> key
- Instructions:
| Section 5. Proof of Lab |
- Project
- Instructions:
- Your project is to DEBUG and FIX all the BUGS.
- perl -c scan_running_services.pl
- Look at compiler errors.
- Fix compiler errors.
- Keep compiling until the syntax reports to be OK.
- Instructions:
- Proof of Lab
- Instructions
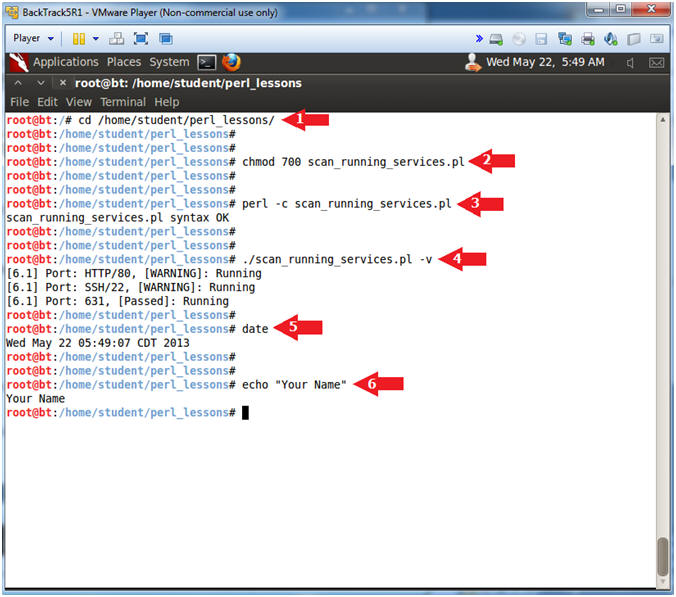
- cd /home/student/perl_lessons/
- chmod 700 scan_running_services.pl
- perl -c scan_running_services.pl
- ./scan_running_services.pl -v
- date
- echo "Your Name"
- Put in your actual name in place of "Your Name"
- e.g., echo "John Gray"
-
Proof Of Lab
Instructions:
- Press the <Ctrl><Alt> keys simultaneously
- Press the <PrtScn> key
- Paste into a word document
- Upload to Moodle
- Instructions