(Fedora: Lesson 6)
{ Configuring /etc/login.defs }
| Section 0. Background Information |
- What is the /etc/login.defs files.
- The /etc/login.defs file defines the site-specific configuration for the shadow password suite.
- PASS_MAX_DAYS (number)
- The maximum number of days a password may be used.
- If the password is older than this, a password change will be forced.
- If not specified, -1 will be assumed (which disables the restriction).
- PASS_MIN_DAYS (number)
- The minimum number of days allowed between password changes.
- Any password changes attempted sooner than this will be rejected.
- If not specified, -1 will be assumed (which disables the restriction).
- PASS_WARN_AGE (number)
- The number of days warning given before a password expires.
- A zero means warning is given only upon the day of expiration, a negative value means no warning is given.
- If not specified, no warning will be provided
- Pre-requisites
-
Lab
Notes
- In this lab we will do the following:
- We will edit the /etc/login.def file and set PASS_MAX_DAYS.
- We will edit the /etc/login.def file and set PASS_MIN_DAYS.
- We will edit the /etc/login.def file and set PASS_WARN_AGE.
- In this lab we will do the following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- Your are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2013 No content replication of any kind is allowed without express written permission.
| Section 1: Edit Virtual Machine |
- Open Your VMware Player
- Instructions:
- On Your Host Computer, Go To
- Start --> All Program --> VMWare --> VMWare Player
- Instructions:
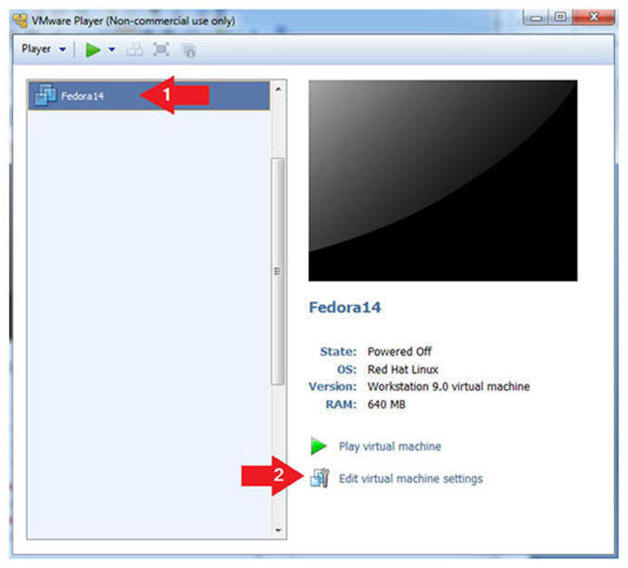
- Edit Fedora 14 Virtual Machine Settings
- Instructions:
- Highlight Fedora14
- Click Edit virtual machine settings
- Instructions:
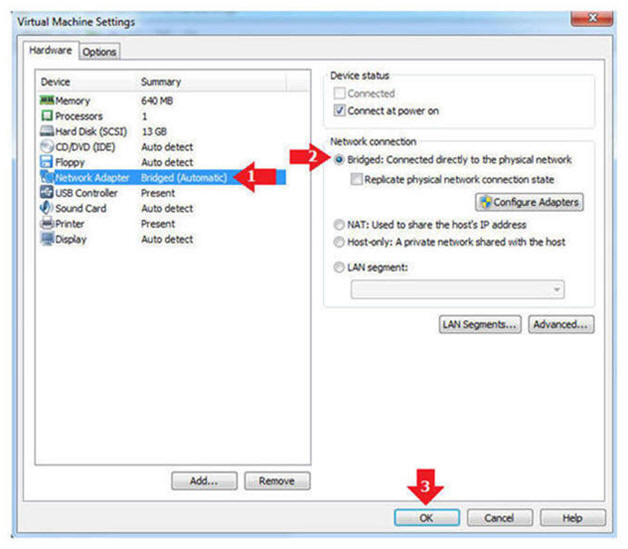
- Edit Network Adapter
- Instructions:
- Highlight Network Adapter
- Select Bridged
- Click the OK Button
- Instructions:
| Section 2: Play Virtual Machine |
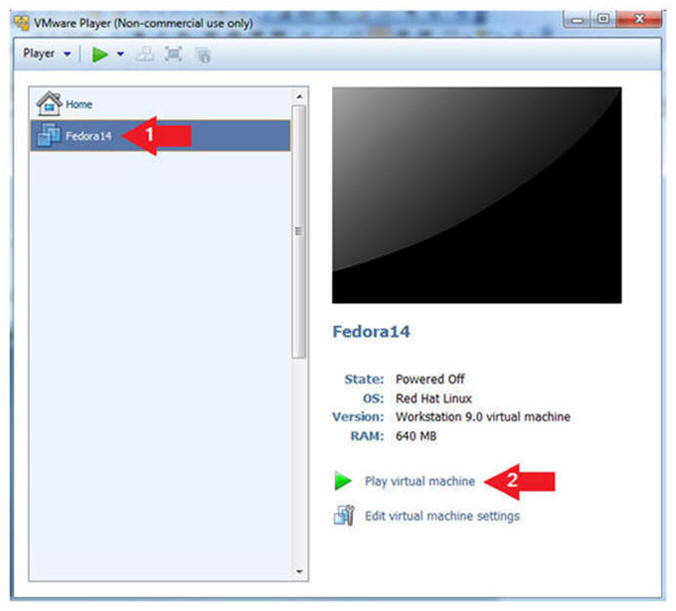
- Start the Fedora14 VM
- Instructions:
- Click on the Fedora14 VM
- Click on Play virtual machine
- Instructions:
| Section 3: Login to your Fedora14 server. |
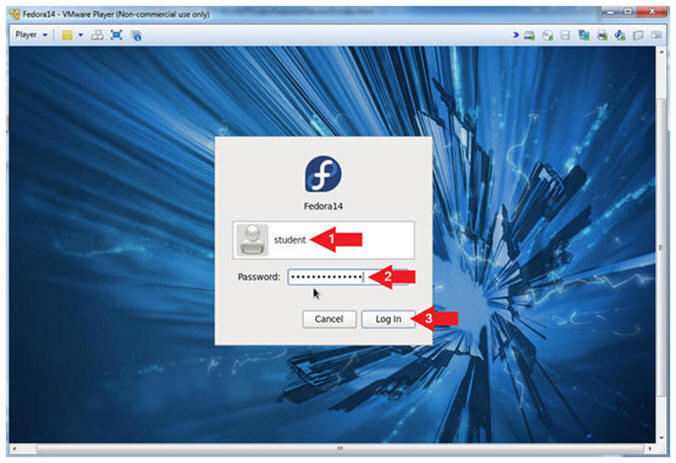
- Login As student
- Instructions:
- Click on student
- Provide student password
- Click the Login Button
- Instructions:
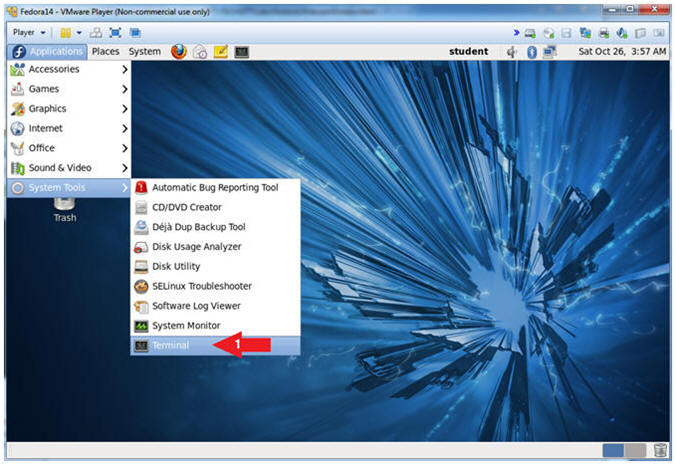
- Start Up A Terminal.
- Applications --> System Tools --> Terminal
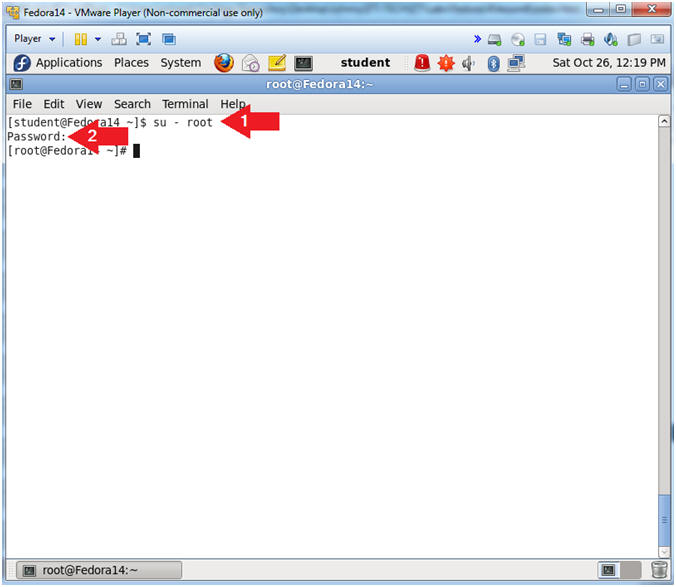
- Switch User to root
- Instruction:
- su - root
- Supply the Root Password
- Instruction:
| Section 4: Editing /etc/login.defs |
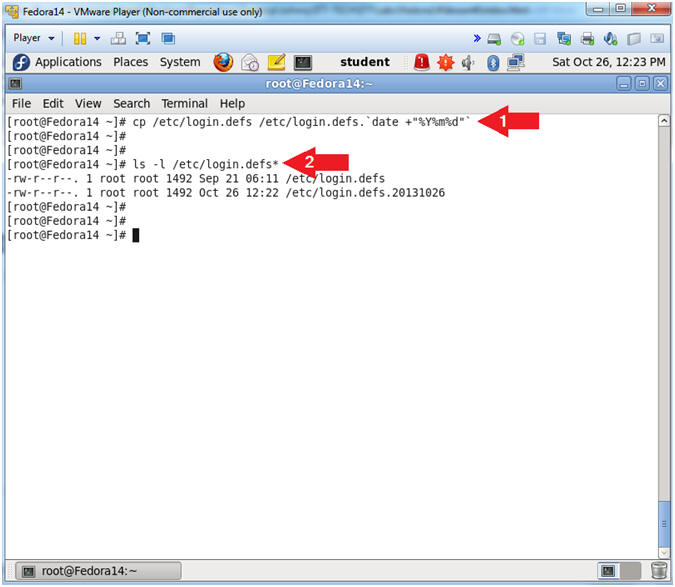
- Backing Up /etc/login.defs
- Instructions:
- cp /etc/login.defs /etc/login.defs.`date +"%Y%m%d"`
- ls -l /etc/login.defs*
- Instructions:
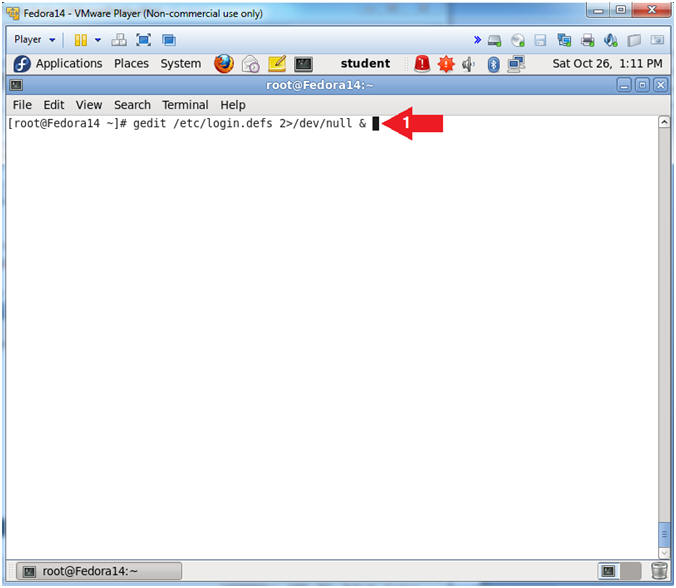
- Open the /etc/login.defs file.
- Instructions:
- gedit /etc/login.defs 2>/dev/null &
- Note(FYI):
- gedit is a text editor for the GNOME desktop environment, Mac OS X and Microsoft Windows.
- 2>/dev/null, means send standard error to a back hole (/dev/null).
- &, means run gedit in the background.
- Instructions:
- Changing the PASS_MAX_DAYS Password Aging
Control.
- Instructions:
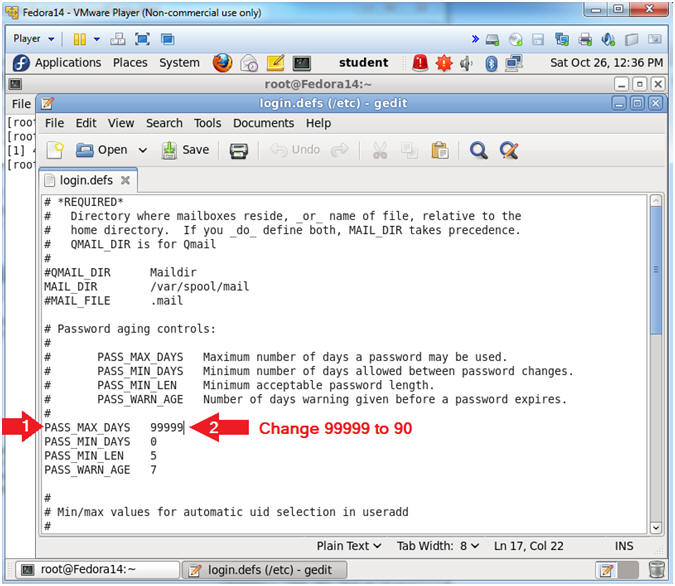
- Arrow down to the PASS_MAX_DAYS line.
- Change PASS_MAX_DAYS from 99999 to 90
- Note(FYI):
- By changing PASS_MAX_DAYS to 90 days, each user will be forced to change their password every 90 days.
- Instructions:
- Changing the PASS_MIN_DAYS Password Aging
Control.
- Instructions:
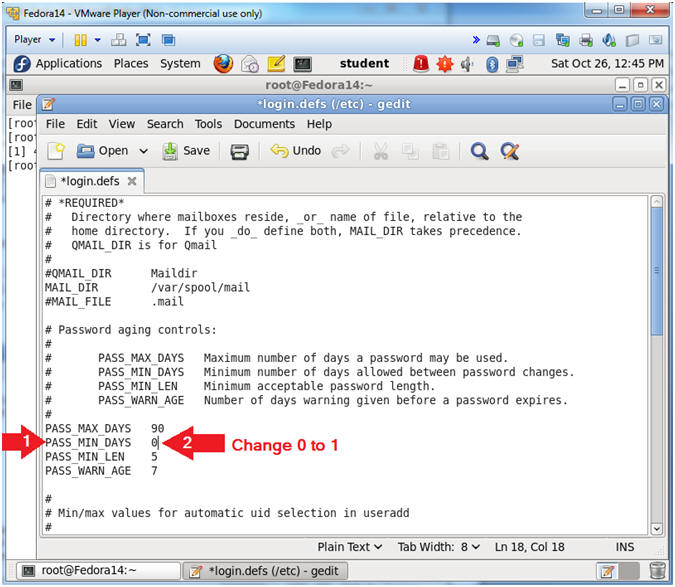
- Arrow down to the PASS_MIN_DAYS line.
- Change PASS_MIN_DAYS from 0 to 1
- Note(FYI):
- By setting PASS_MIN_DAYS to 1, the each user will be forced to wait 1 day before changing their password after the initial change.
- This is an attempt to thwarts brute force password changes back to your favorite password.
- Instructions:
- Changing the PASS_MIN_LEN Password Aging
Control.
- Instructions:
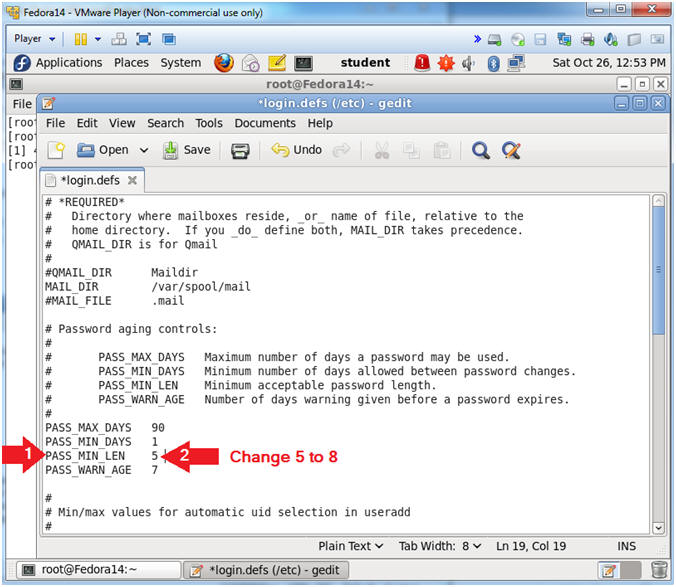
- Arrow down to the PASS_MIN_LEN line.
- Change PASS_MIN_LEN from 5 to 8
- Note(FYI):
- By setting PASS_MIN_LEN to 8, will require each user password to be at least 8 characters long.
- Instructions:
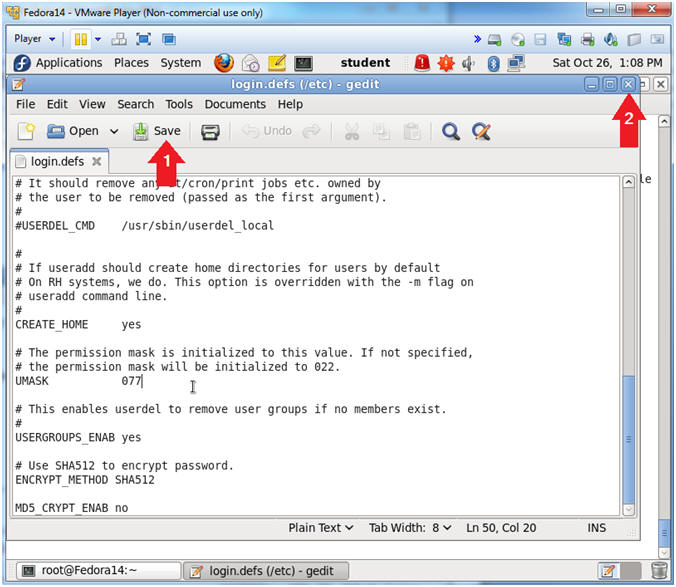
- Verifying the UMASK.
- Instructions:
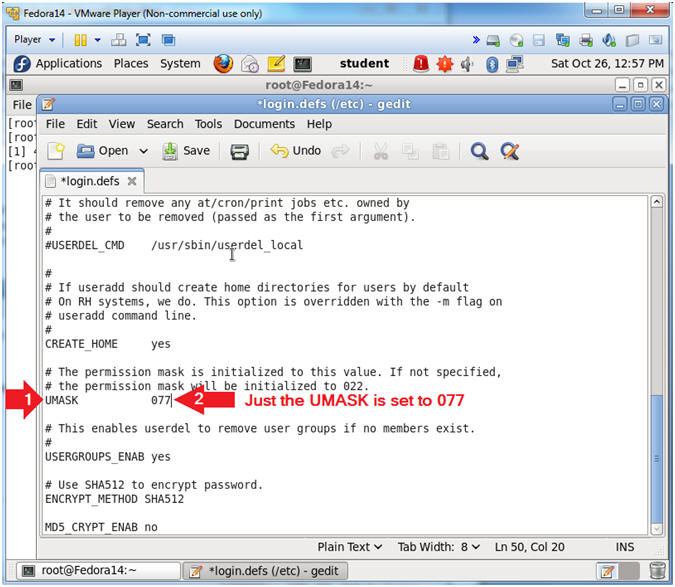
- Arrow down to the UMASK line.
- Make sure UMASK is set to 077.
- Note(FYI):
- By setting UMASK to 077, this will ensure that only the user of the home directory will have read, write, and execute permissions to their own home directory.
- Instructions:
- Save the /etc/login.defs file
- Instructions:
- Click the Save Button
- Click "X" to Close
- Instructions:
| Section 5: Proof of Lab |
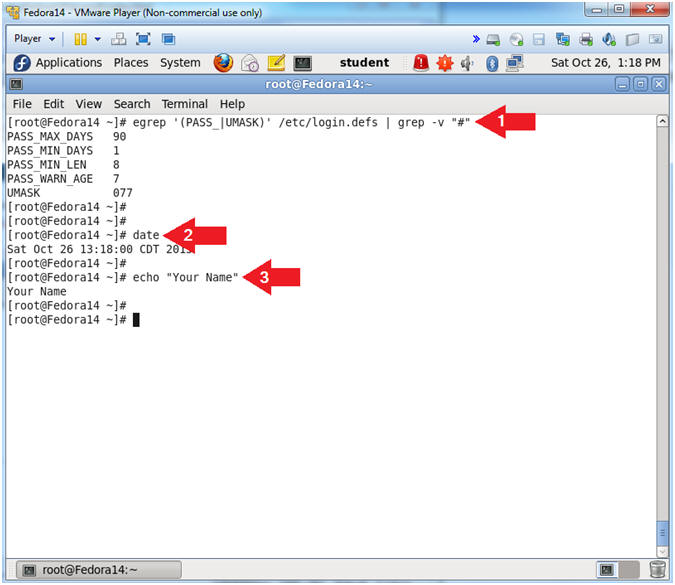
- Proof of Lab
- Instructions:
- egrep '(PASS_|UMASK)' /etc/login.defs | grep -v "#"
- date
- echo "Your Name"
- Put in your actual name in place of "Your Name"
- e.g., echo "John Gray"
-
Proof of Lab
Instructions
- Press the <Ctrl> and <Alt> key at the same time.
- Press the <PrtScn> key.
- Paste into a word document
- Upload to Moodle
- Instructions: