(CentOS 6.6: Lesson 8)
{ Testing denyhosts and brutessh.py }
| Section 0. Background Information |
- What is denyhosts
- DenyHosts is a log-based intrusion prevention security tool for SSH servers written in Python. It is intended to prevent brute force attacks on SSH servers by monitoring invalid login attempts in the authentication log and blocking the originating IP addresses.
- http://denyhosts.sourceforge.net/
- What is brutessh.py
- Brutessh is a program that uses the paramiko ssh library, to launch bruteforce passwords attacks to the sshd service. The tools is multithreading and uses a dictionary for the passwords.
- Prerequisite
-
Lab Notes
- In this lab we will how to do the
following:
- We will use brutessh on Kali to attack the ssh daemon on CentOS.
- Will we install denyhosts on CentOS.
- CentOS will block Kali
- We will unblock Kali
- In this lab we will how to do the
following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- You are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2015 No content replication of any kind is allowed without express written permission.
| Section 1. Configure CentOS-6.6 Virtual Machine Settings |
- Open Your VMware Player
- Instructions:
- On Your Host Computer, Go To
- Start --> All Program --> VMWare --> VMWare Player
- Instructions:
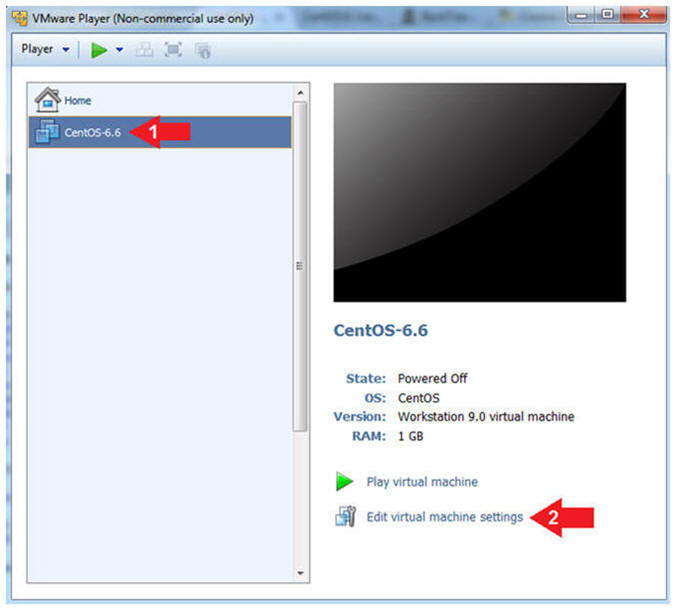
- Edit CentOS-6.6 Virtual Machine Settings
- Instructions:
- Highlight CentOS-6.6
- Click Edit virtual machine settings
- Instructions:
- Auto Detect Hard Drive
- Instructions:
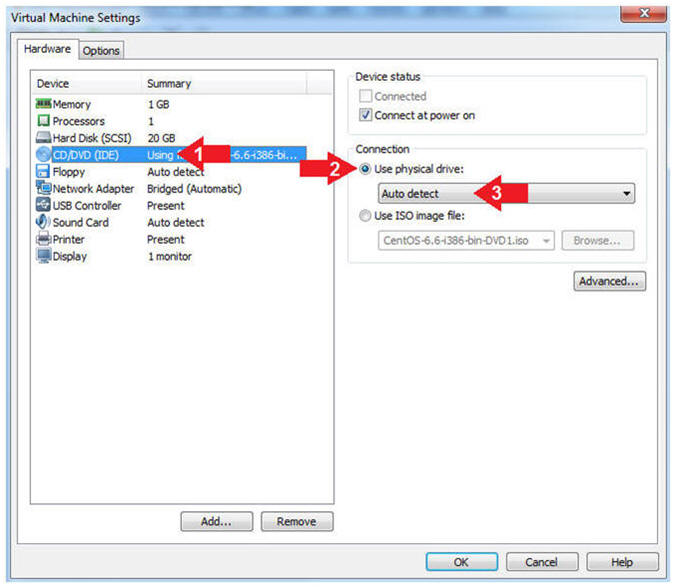
- Click on CD/DVD(IDE)
- Click the Use physical drive: radio button
- Make sure Auto detect is selected
- Instructions:
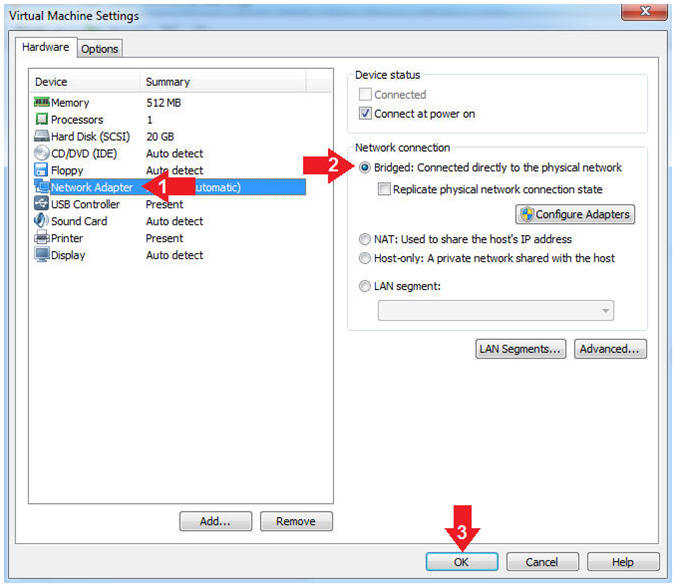
- Edit Network Adapter
- Instructions:
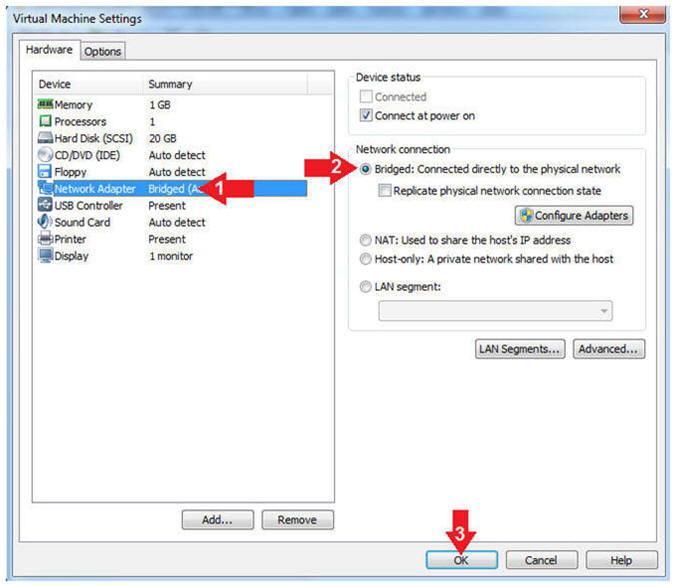
- Highlight Network Adapter
- Select Bridged
- Click the OK Button
- Instructions:
| Section 2. Play Virtual Machine |
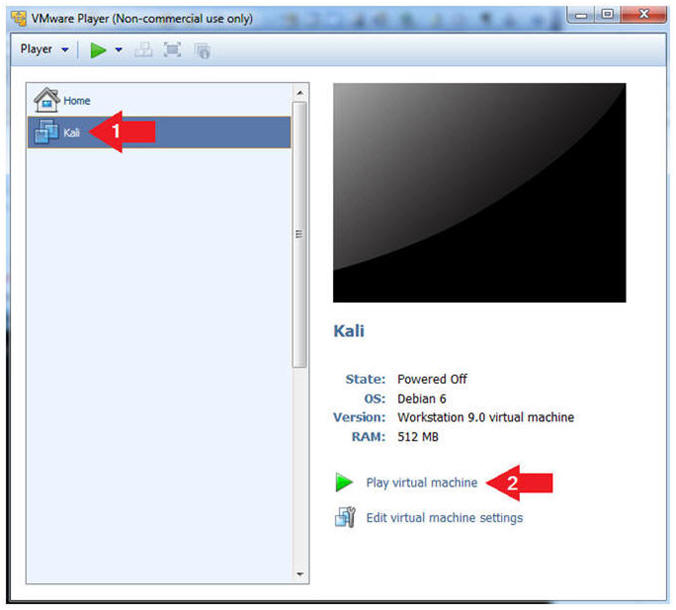
- Start the CentOS-6.6 VM
- Instructions:
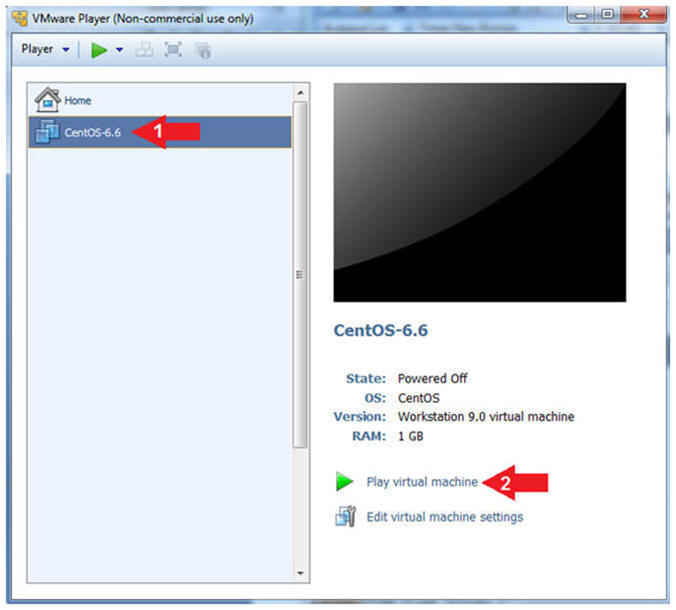
- Click on the CentOS-6.6 VM
- Click on Play virtual machine
-
- Instructions:
| Section 3. Login to CentOS |
- Login to CentOS
- Note(FYI):
- Until you click the user, in this case Security Student, the Password field will not be displayed.
- Instructions:
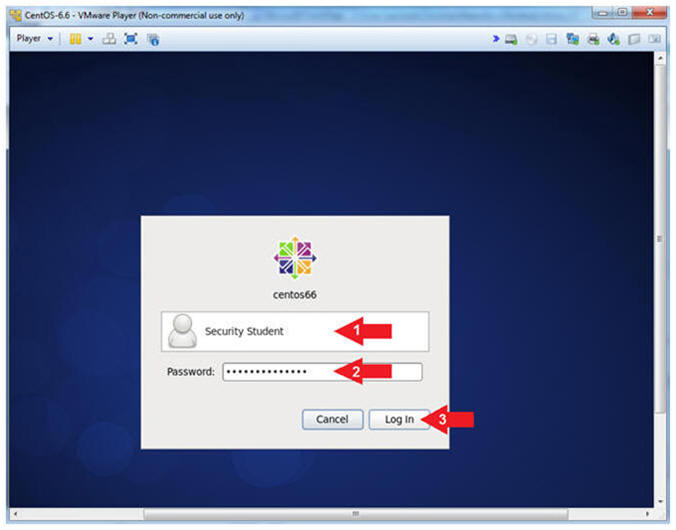
- Click on Security Student
- This will display the password text box.
- Supply its' password
- Click the Log In Button
- Click on Security Student
- Note(FYI):
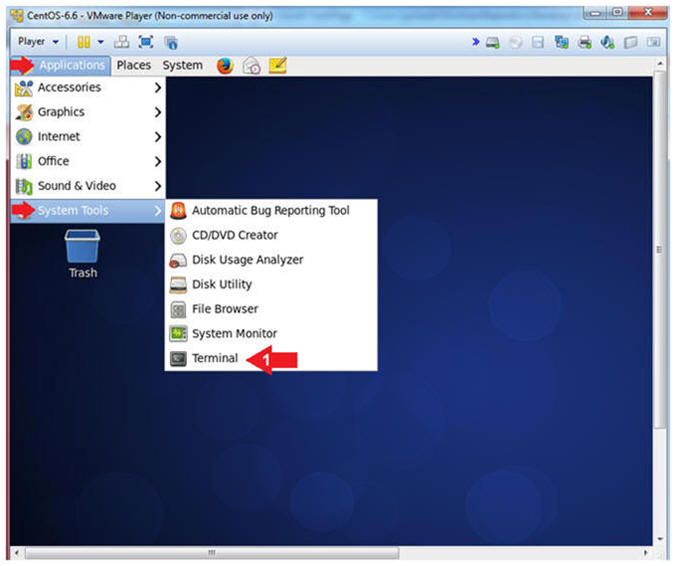
- Open a Terminal
- Instructions:
- Applications --> System Tools --> Terminal
- Instructions:
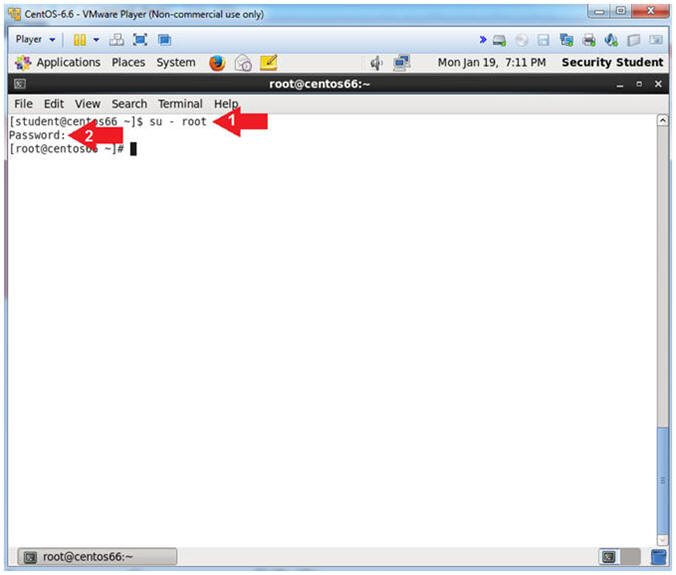
- Switch User to root
- Instruction:
- su - root
- Supply the Root Password
- Notes (FYI):
- su - root, this command allows the user student to switch user to user root, provided the root password can be supplied.
- Instruction:
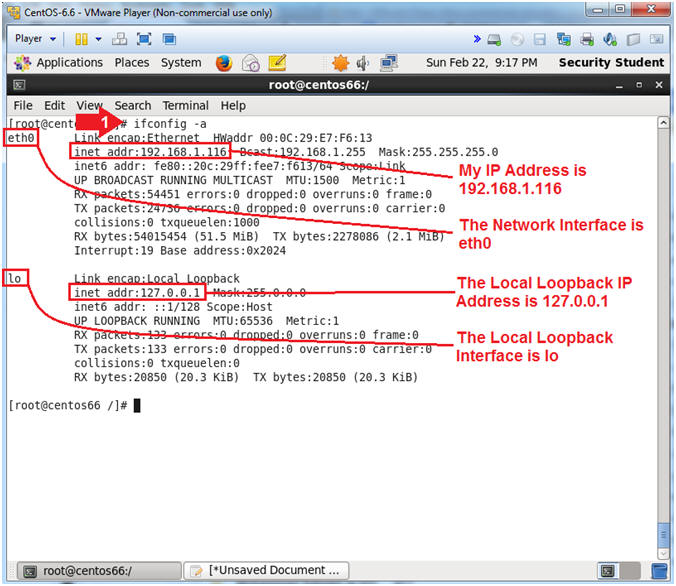
- Get IP Address
- Instructions:
- ifconfig -a
- Notes (FYI):
- As indicated below, my IP address is
192.168.1.116 for Network Interface eth1.
- Please record your IP address
- The Local Loopback Address is 127.0.0.1
for Network Interface lo.
- The loopback device is a special, virtual network interface that your computer uses to communicate with itself. When the network or wifi is disconnected the loopback exists so applications running on your computer can always connect to servers on the same machine.
- As indicated below, my IP address is
192.168.1.116 for Network Interface eth1.
- Instructions:
| Section 4. Set Easy Password |
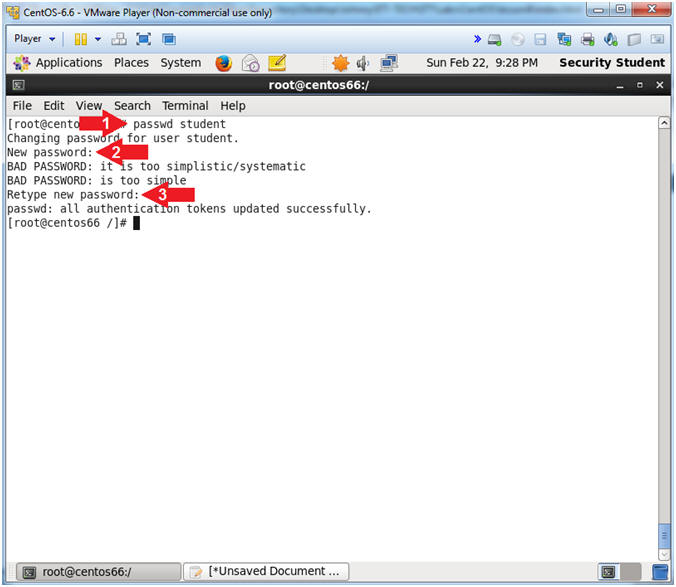
- Set Easy Password
- Instruction:
- passwd student
- New password: abc123
- Retype new password: abc123
- Note(FYI):
- Obviously, abc123 is a bad password. Even the CentOS operating system warns against. Later this lesson, brutessh.py will be use to launch a brute ssh account and will be successful.
- Instruction:
| Section 5. Start Kali |
- Start VMware Player
- Instructions
- For Windows 7
- Start --> All Programs --> VMware Player
- For Windows XP
- Starts --> Programs --> VMware Player
- For Windows 7
- Instructions
- Edit Virtual Machine Settings
- Instructions:
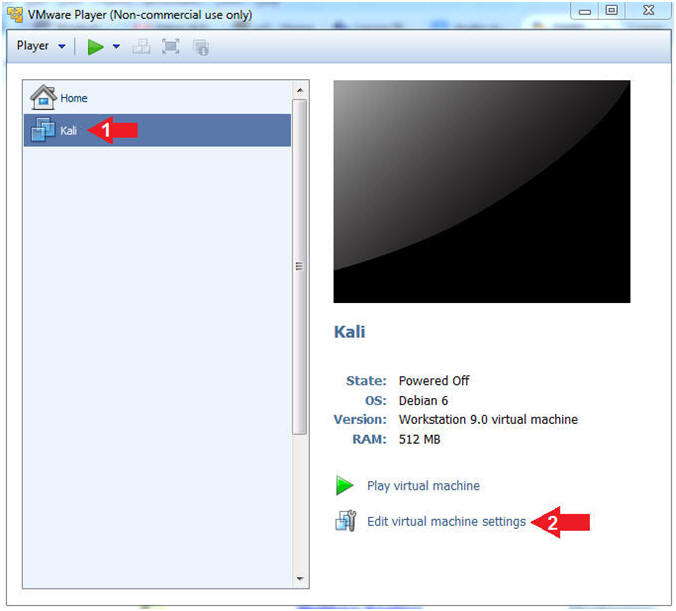
- Click on the Kali VM
- Click on Edit virtual machine settings
- Instructions:
- Auto Detect Hard Drive
- Instructions:
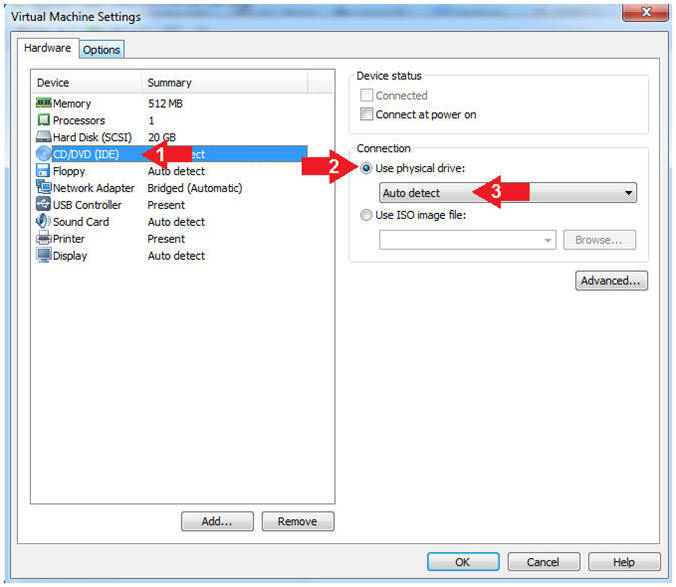
- Click on CD/DVD(IDE)
- Click the Use physical drive: radio button
- Make sure Auto detect is selected
- Instructions:
- Edit Network Adapter
- Instructions:
- Highlight Network Adapter
- Select Bridged
- Click the OK Button
- Instructions:
- Start the Kali VM
- Instructions:
- Click on the Kali VM
- Click on Play virtual machine
- Instructions:
| Section 6. Login to Kali |
- Supply Username
- Instructions:
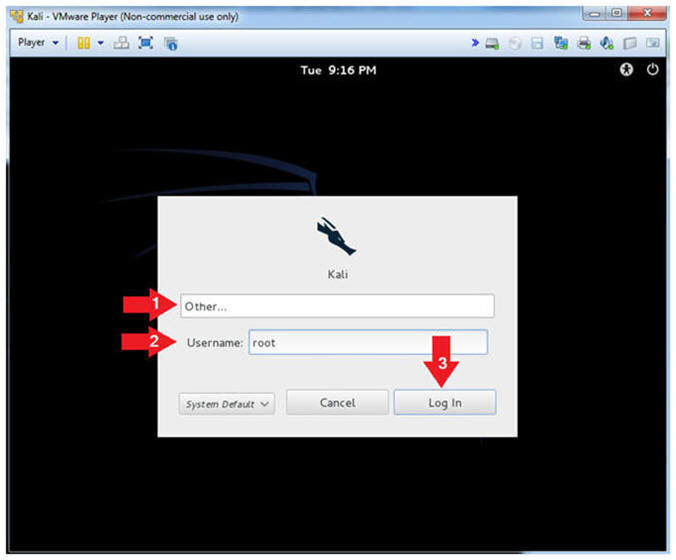
- Click Other
- Username: root
- Click the Login Button
- Instructions:
- Supply Password
- Instructions:
- Password: Provide the root password
- Click the Login Button
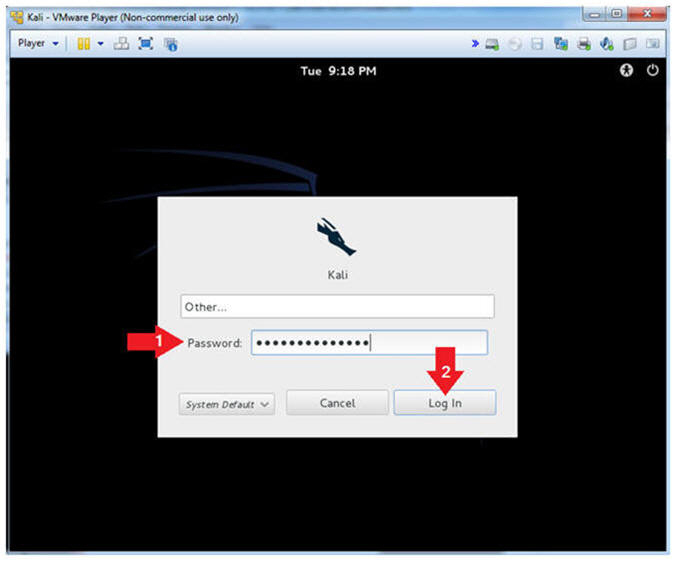
- Instructions:
| Section 7. Obtain IP Address Address |
- Open a Terminal
- Instructions:
- Applications --> Accessories --> Terminal
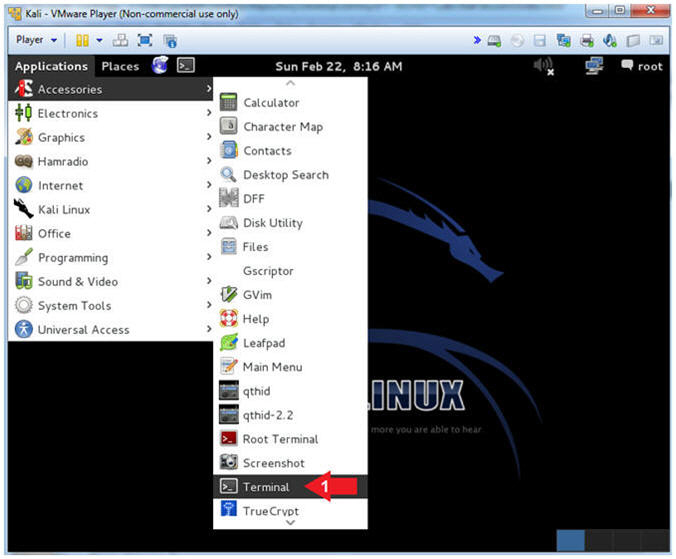
- Instructions:
- Get IP Address
- Instructions:
- ifconfig -a
- Notes (FYI):
- As indicated below, my IP address is
192.168.1.115 for Network Interface eth0.
- Please record your IP address
- The Local Loopback Address is 127.0.0.1
for Network Interface lo.
- The loopback device is a special, virtual network interface that your computer uses to communicate with itself. When the network or wifi is disconnected the loopback exists so applications running on your computer can always connect to servers on the same machine.
- As indicated below, my IP address is
192.168.1.115 for Network Interface eth0.
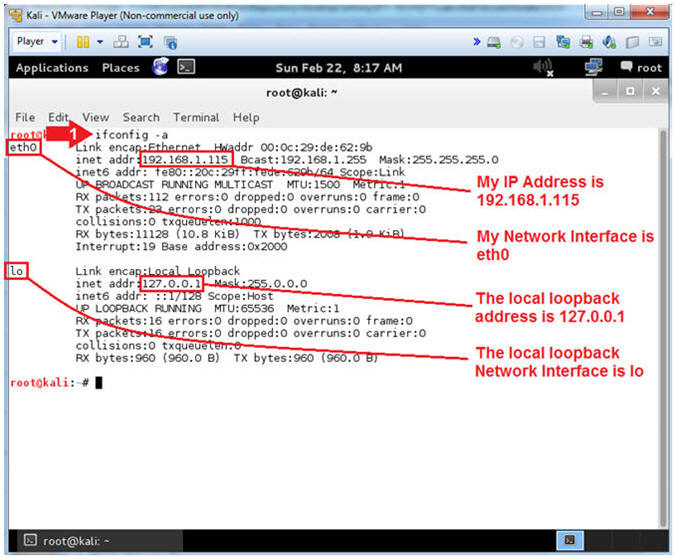
- Instructions:
| Section 8. Test SSH Connectivity Between Kali and CentOS |
- Test SSH from Kali to CentOS (On
Kali)
- Instructions:
- ssh
student@192.168.1.116
"uptime"
- If you do not have a student account on CentOS, replace it with the system account you created in Lab 1.
- connecting (yes/no)? yes
- Provide Password
- ssh
student@192.168.1.116
"uptime"
- Note(FYI):
- Replace 192.168.1.116 with CentOS's IP Address obtained from (Section 3, Step 4).
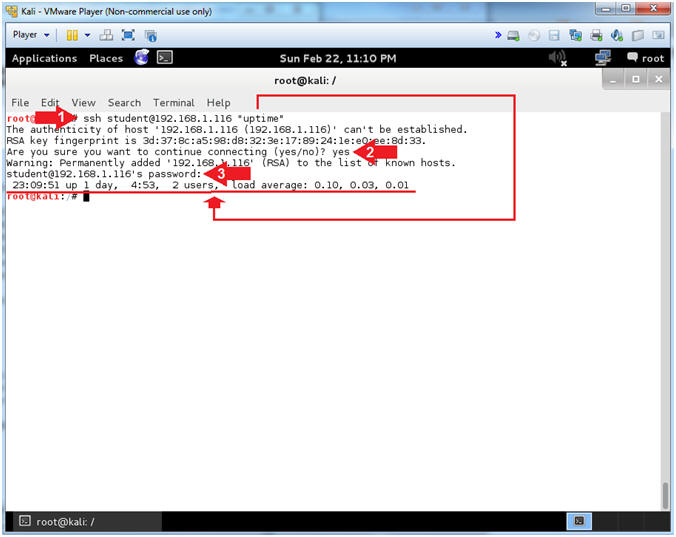
- Instructions:
| Section 9. Inspect CentOS Security Log |
- View CentOS secure log (On
CentOS)
- Note(FYI):
- Replace 192.168.1.115 with Kali's IP Address obtained from (Section 7, Step 2).
- You will notice that password was accepted.
- Instructions:
- grep -i "accepted password" /var/log/secure | grep "192.168.1.115"
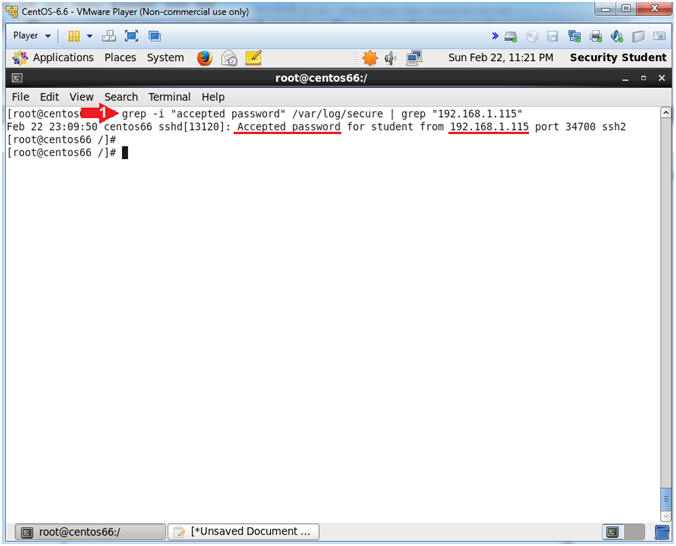
- Note(FYI):
| Section 10. Inspect CentOS Security Log |
- Using BruteSSH (On
Kali)
- Instructions:
- cd /pentest/brutessh/
- python brutessh.py -help
- The -help flag produced the usage options.
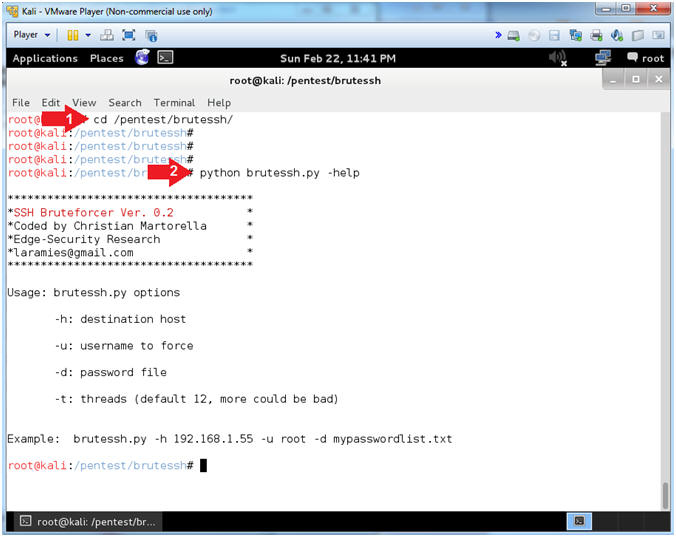
- Instructions:
- Using BruteSSH Against DenyHosts
- Note(FYI):
- Replace 192.168.1.116 with CentOS's IP Address obtained from (Section 3, Step 4).
- In the case below, we are attacking the student account, because we set it to an easy to guess password(abc123). Most of the time, attackers will often target the root account.
- Instructions:
- python brutessh.py -h 192.168.1.116 -t 0 -u student -d password.txt
- Note(FYI):
- Notice my Times: End(.15) and Init(.06), which means it took .09 seconds to discover the easy password.
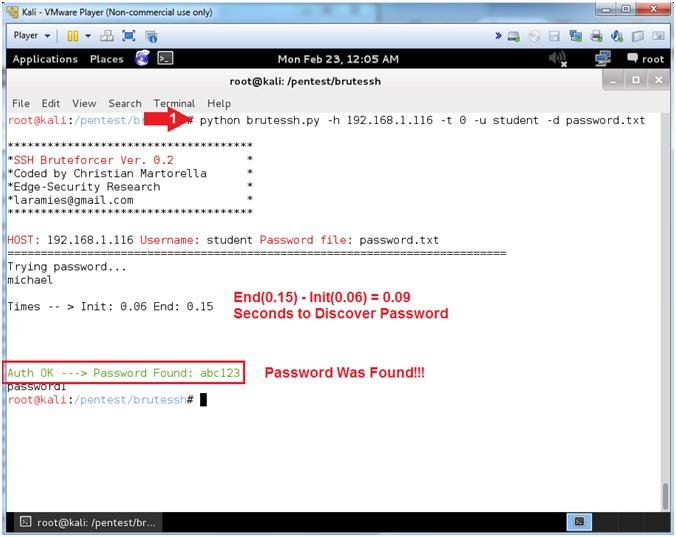
- Note(FYI):
| Section 11. Investigate Authentication Failures |
- Check CentOS secure log (On
CentOS)
- Note(FYI):
- Replace 192.168.1.115 with Kali's IP Address obtained from (Section 7, Step 2).
- Instructions:
- grep -i "failed password" /var/log/secure | grep "192.168.1.115"
- Note(FYI):
- Notice all the failed login attempts for the student account, that occurred in less then a second.
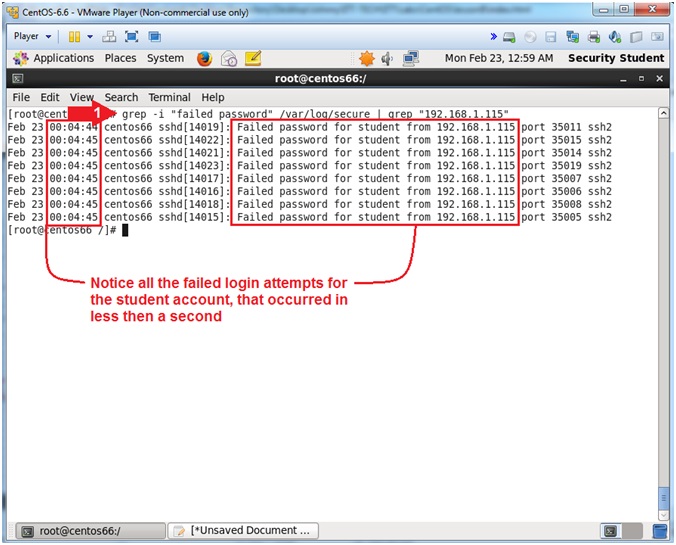
- Note(FYI):
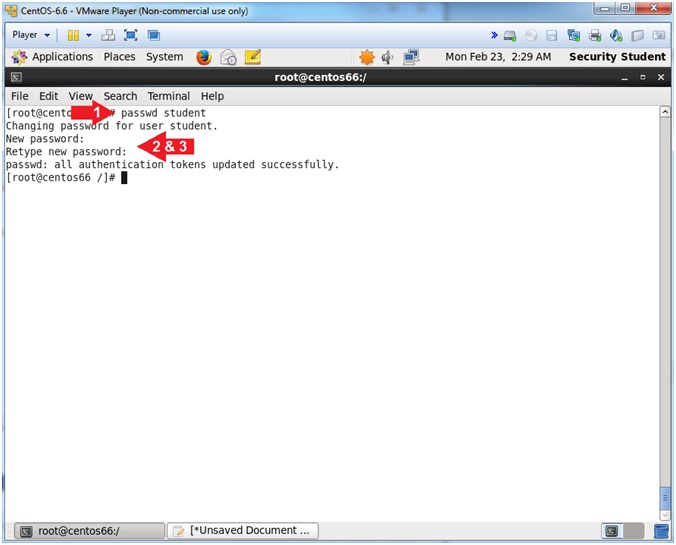
- Change student password
- Instructions:
- passwd student
- New password: <Supply a Strong Password>
- Retype new password: <Supply a Strong Password>
- Instructions:
| Section 12. Install DenyHosts |
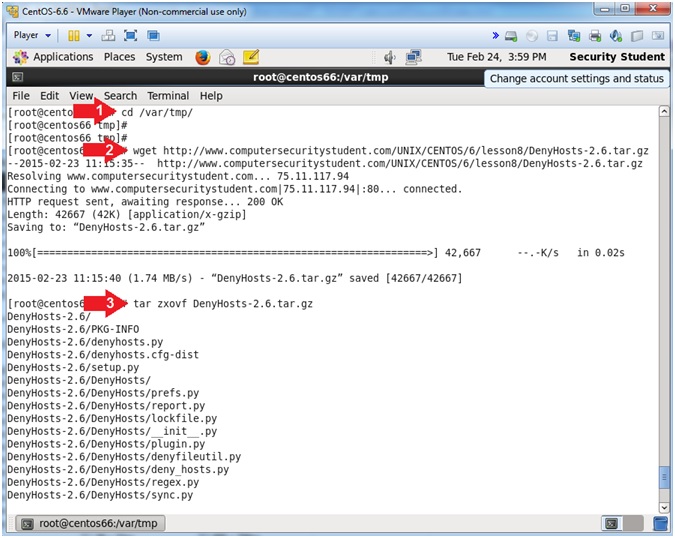
- Download DenyHosts (On
CentOS)
- Instructions:
- cd /var/tmp
- wget http://www.computersecuritystudent.com/UNIX/CENTOS/6/lesson8/DenyHosts-2.6.tar.gz
- tar zxovf DenyHosts-2.6.tar.gz
- Instructions:
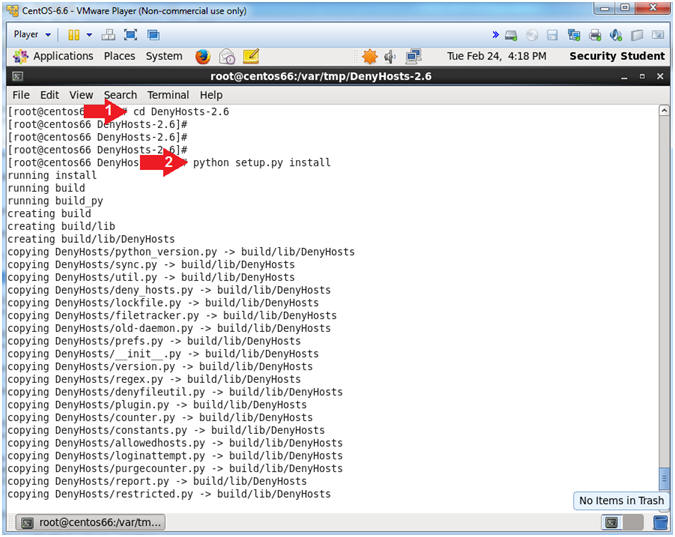
- Install DenyHosts
- Instructions:
- cd DenyHosts-2.6
- python setup.py install
- Instructions:
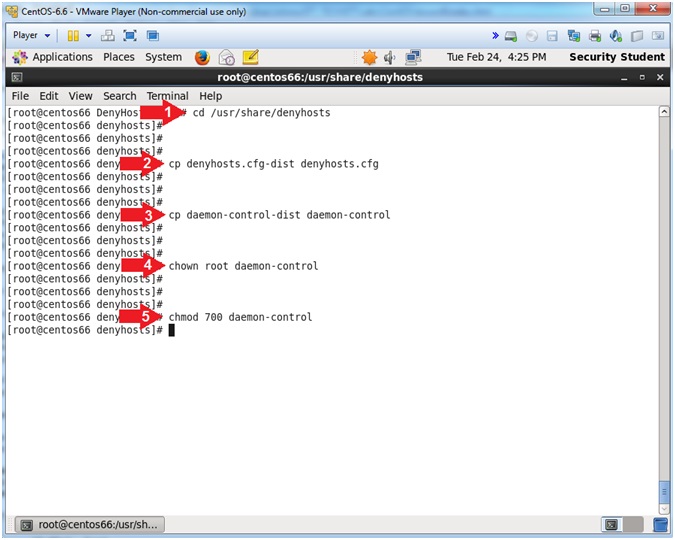
- Install DenyHosts
- Instructions:
- cd /usr/share/denyhosts
- cp denyhosts.cfg-dist denyhosts.cfg
- cp daemon-control-dist daemon-control
- chown root daemon-control
- chmod 700 daemon-control
- Note(FYI):
- By default the directory /usr/share/denyhosts will be created and a sample configuration file will be copied into it.
- denyhosts.cfg-dist is the sample configuration file.
- daemon-control-dist is the sample daemon configuration file.
- Instructions:
| Section 13. Configure Startup Scripts |
- Create DenyHosts Start Up Scripts (On
CentOS)
- Instructions:
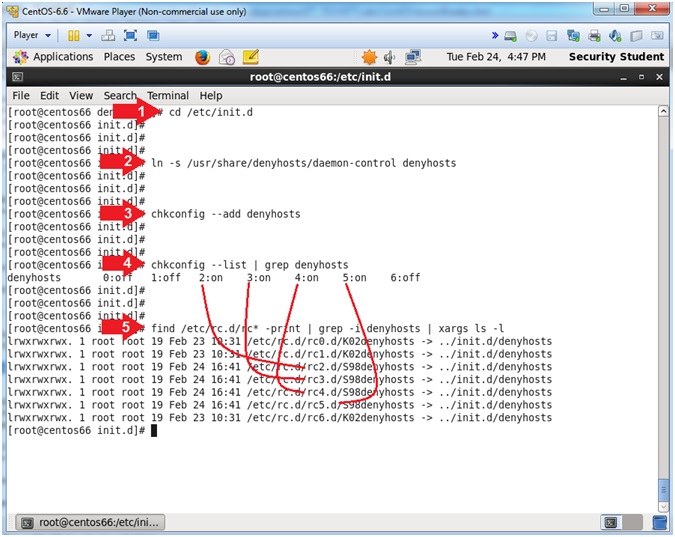
- cd /etc/init.d
- ln -s /usr/share/denyhosts/daemon-control denyhosts
- chkconfig --add denyhosts
- chkconfig --list | grep denyhosts
- find /etc/rc.d/rc* -print| grep -i denyhosts | xargs ls -l
- Note(FYI):
- The /etc/init.d directory contains a number of start and stop scripts for various services on your system.
- Add the denyhosts startup script to /etc/init.d
- Add startup script to runlevel 2, 3, 4, and 5.
- Verify the start up scripts for runlevel 2, 3, 4, and 5 are turned on.
- List the denyhosts start up scripts for runlevel 2, 3, 4, and 5
- Instructions:
- Let's start up the denyhosts daemon.
- Instruction:
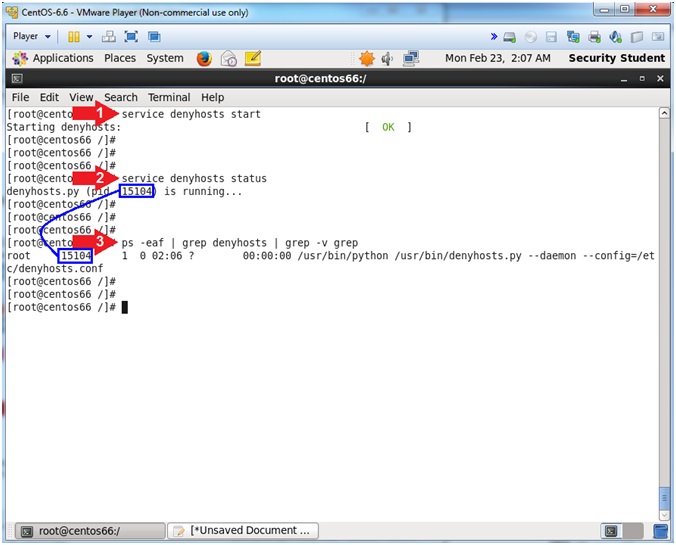
- service denyhosts start
- service denyhosts status
- ps -eaf | grep denyhosts | grep -v grep
- Note(FYI):
- Start up the denyhosts service.
- Check the status of the denyhosts service, which shows the PID.
- ps -eaf | grep denyhosts | grep -v grep
- You can use the (ps) command to view the actual denyhosts process. Notice how my process IDs of 15104 match. Do yours match?
- Instruction:
| Section 16. Testing Brutessh.py against Denyhost |
- Attempt Brutessh.py against Denyhosts (On
Kali)
- Note(FYI):
- Replace 192.168.1.116 with CentOS's IP Address obtained from (Section 3, Step 4).
- Instruction:
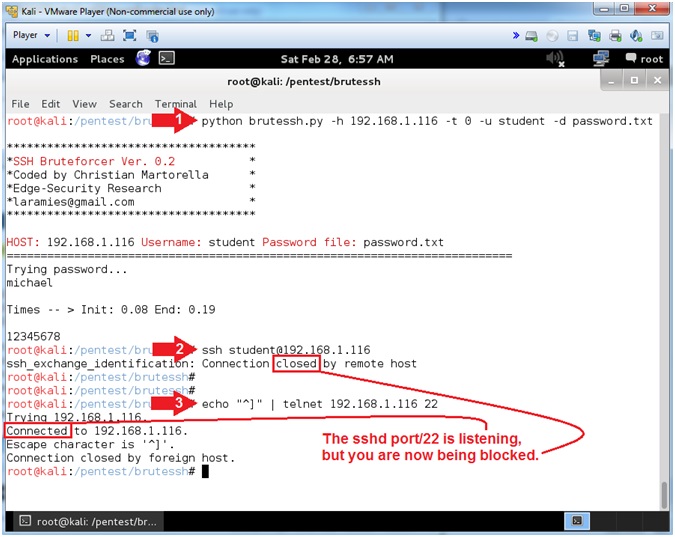
- python brutessh.py -h 192.168.1.116 -t 0 -u student -d password.txt
- ssh student@192.168.1.116
- echo "^]" | telnet 192.168.1.116 22
- Note(FYI):
- Attempt a brute force ssh attack against the CentOS machine.
- Notice the ssh connection is closed by the CentOS machine.
- Notice you can connect to port/22, but that is about it.
- Note(FYI):
| Section 17. How to Unblock a host from Denyhosts |
- Check CentOS secure log (On
CentOS)
- Instructions:
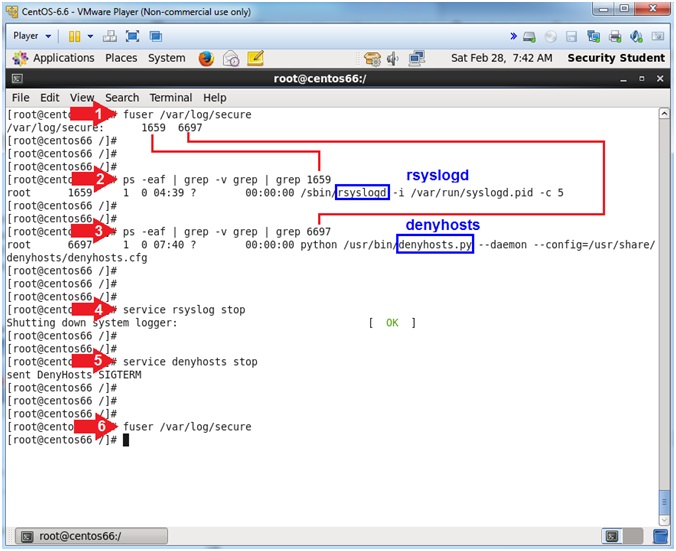
- fuser /var/log/secure
- The command fuser identifies Process IDs (PID)s that have open sockets to a file.
- In my case, PIDs 1659(rsyslogd) and 6697(denyhosts) currently have open sockets to the secure file.
- ps -eaf | grep -v grep | grep
1659
- This is the PID for rsyslog
- ps -eaf | grep -v grep | grep
6697
- This is the PID for denyhosts
- service rsyslog stop
- service denyhosts stop
- fuser /var/log/secure
- Notice no Process IDs are returned because rsyslogd and denyhosts were stopped.
- fuser /var/log/secure
- Note(FYI):
- fuser is a utility that identifies processes using files or sockets.
- Rsyslogd is a system utility that provides support for message logging.
- Instructions:
- Scrub the hosts.deny file
- Note(FYI):
- Replace 192.168.1.115 with your Kali IP Address obtained from (Section 7, Step 2).
- Instructions:
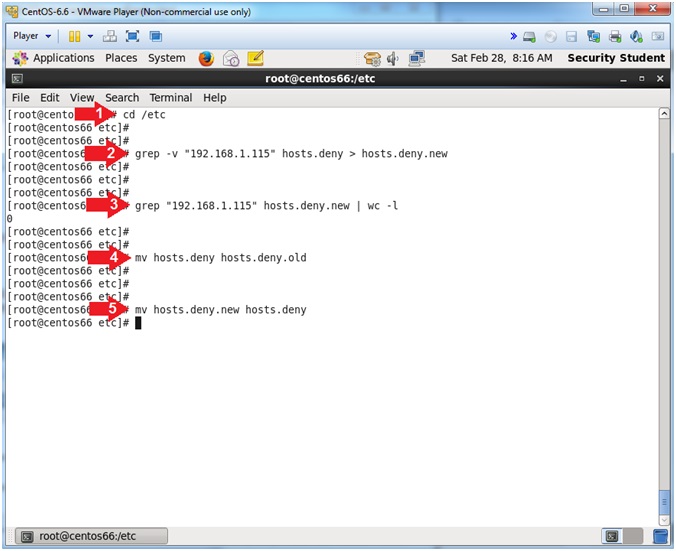
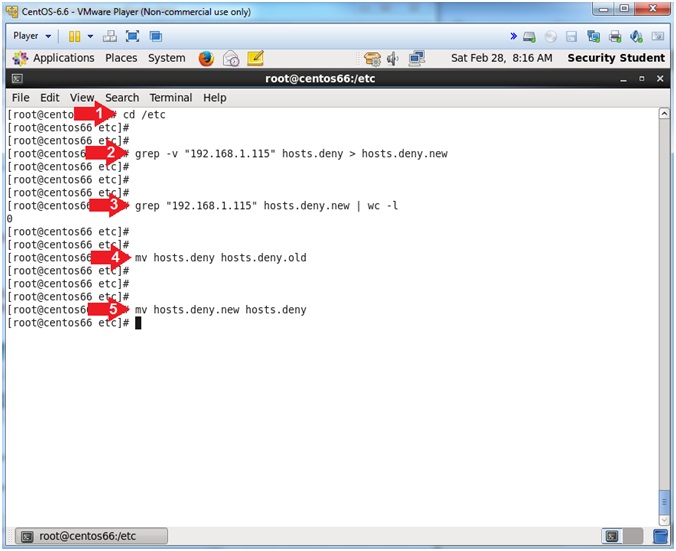
- cd /etc
- grep -v "192.168.1.115" hosts.deny > hosts.deny.new
- grep "192.168.1.115" hosts.deny.new | wc -l
- mv hosts.deny hosts.deny.old
- mv hosts.deny.new hosts.deny
- Note(FYI):
- Scrub the secure file
- Note(FYI):
- Replace 192.168.1.115 with your Kali IP Address obtained from (Section 7, Step 2).
- Instructions:
- cd /var/log/
- grep -v "192.168.1.115" secure > secure.new
- grep "192.168.1.115" secure.new | wc -l
- mv secure secure.old
- mv secure.new secure
- Note(FYI):
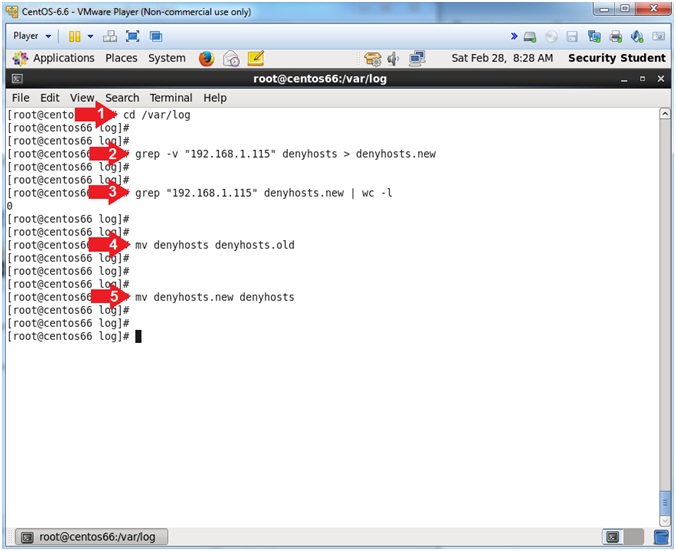
- Scrub the denyhosts file
- Note(FYI):
- Replace 192.168.1.115 with your Kali IP Address obtained from (Section 7, Step 2).
- Instructions:
- cd /var/log/
- grep -v "192.168.1.115" denyhosts > denyhosts.new
- grep -v "192.168.1.115" denyhosts.new | wc -l
- mv denyhosts denyhosts.old
- mv denyhosts.new denyhosts
- Note(FYI):
- Verify Services are running
- Instructions:
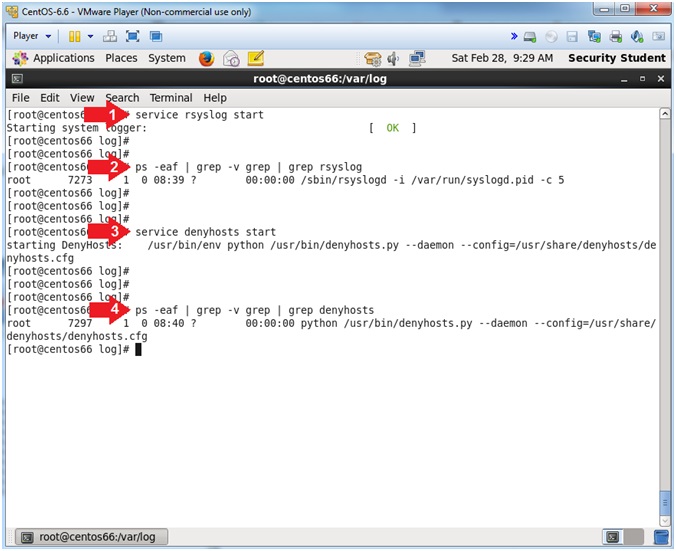
- service rsyslog start
- ps -eaf | grep -v grep | grep rsyslog
- service denyhosts start
- ps -eaf | grep -v grep | grep denyhosts
- Instructions:
| Section 18. Test if host is unblocked |
- Check CentOS secure log (On
Kali)
- Note(FYI):
- Replace 192.168.1.116 with CentOS's IP Address obtained from (Section 3, Step 4).
- Instructions:
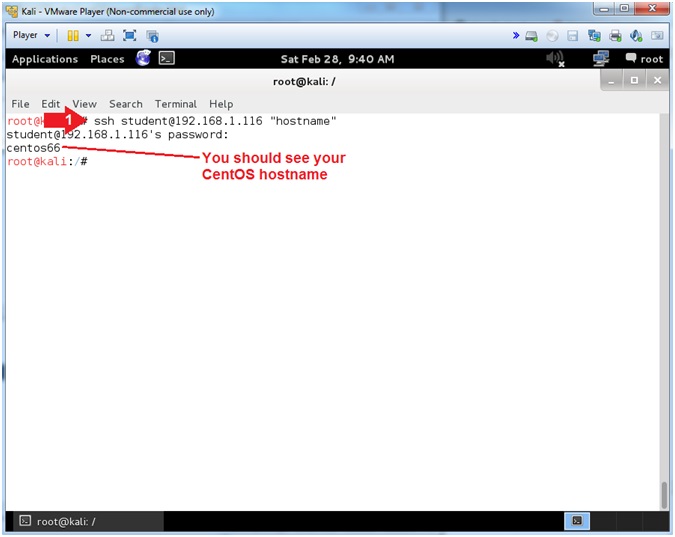
- ssh student@192.168.1.116 "hostname"
- Note(FYI):
- If you successfully unblock the Kali Host, you should now see the CentOS hostname.
- Note(FYI):
| Section 19. Proof of Lab |
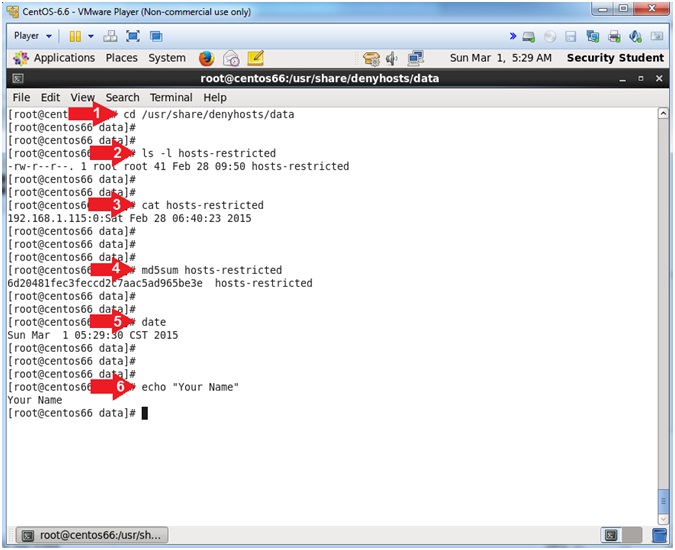
- Proof of Lab
- Instructions:
- cd /usr/share/denyhosts/data
- ls -l hosts-restricted
- cat hosts-restrictedcat hosts-restricted
- md5sum hosts-restricted
- date
- echo "Your Name"
- Replace the string "Your Name" with your actual name.
- e.g., echo "John Gray"
-
Proof of Lab Instructions:
- Do a PrtScn
- Paste into a word document
- Upload to Moodle
-
- Instructions: