(Nmap: Lesson: 2)
{ Nmap Basic Usage }
| Section 0: Background Information |
- NMAP
- Nmap (Network Mapper) is a security scanner used to discover hosts and services on a computer network, thus creating a "map" of the network. To accomplish its goal, Nmap sends specially crafted packets to the target host and then analyzes the responses. Unlike many simple port scanners that just send packets at some predefined constant rate, Nmap accounts for the network conditions (latency fluctuations, network congestion, the target interference with the scan) during the run.
- Prerequisite
-
Lab Notes
- In this lab we will do the following:
- We will use the PENTEST-WXP VM (Attacker) to NMAP scan the Damn Vulnerable WXP-SP2 VM (Victim)
- In this lab we will do the following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- Your are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2012 No content replication of any kind is allowed without express written permission.
| Section 1: Power On PENTEST-WXP |
- Edit Virtual Machine Settings
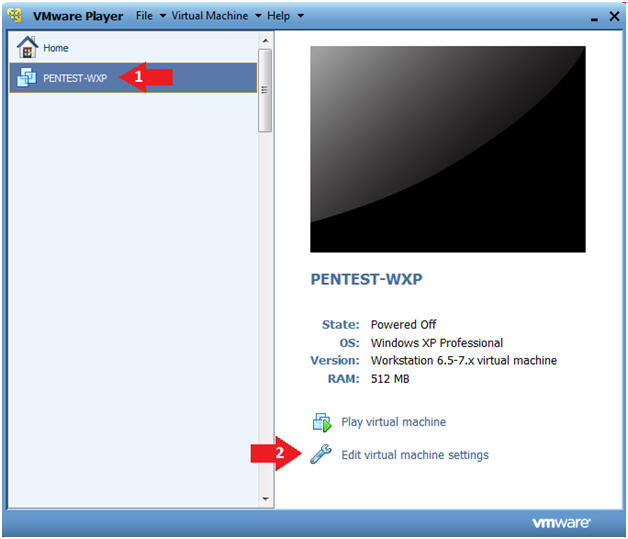
- Instructions:
- Click on PENTEST-WXP
- Click on Edit virtual machine
- Instructions:
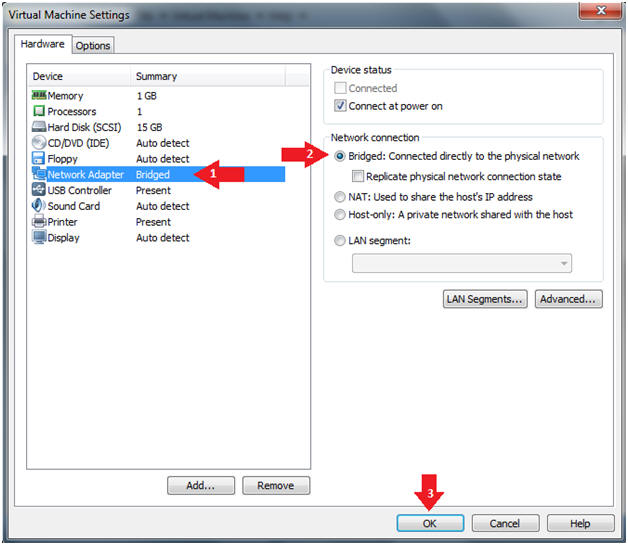
- Configure Network Adapter
- Instructions:
- Select Network Adapter
- Click the radio button "Bridged: Connected directly to the physical network."
- Click the Okay button
- Instructions:
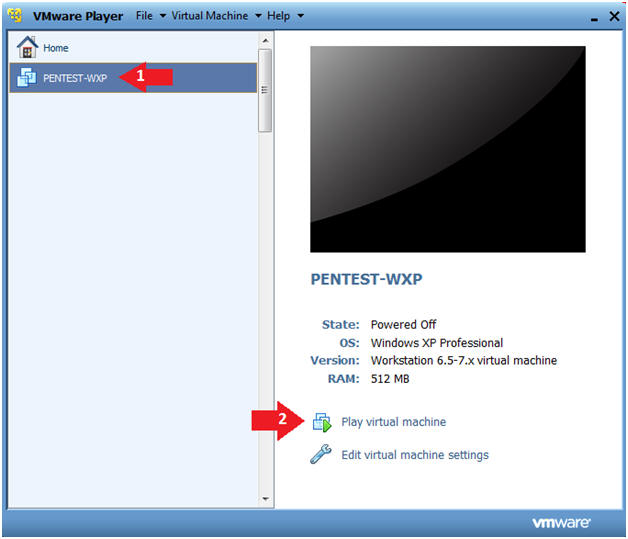
- Start PENTEST-WXP
- Instructions:
- Click on PENTEST-WXP
- Click on Play virtual machine
- Instructions:
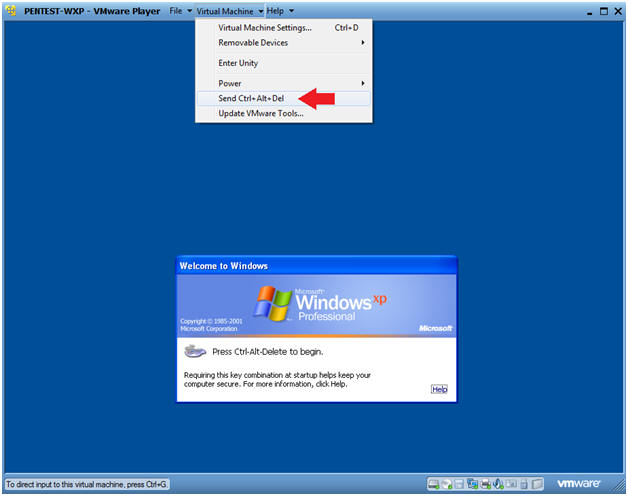
- Send Ctrl+Alt+Del
- Instructions:
- Virtual Machine --> Send Ctrl+Alt+Del
- Instructions:
- Logging into Damn PENTEST-WXP.
- Instructions:
- Username: administrator
- Password: Use the Class Password or whatever you set it.
- Instructions:
- Open a Command Prompt
- Instructions:
- Start --> All Programs --> Accessories --> Command Prompt
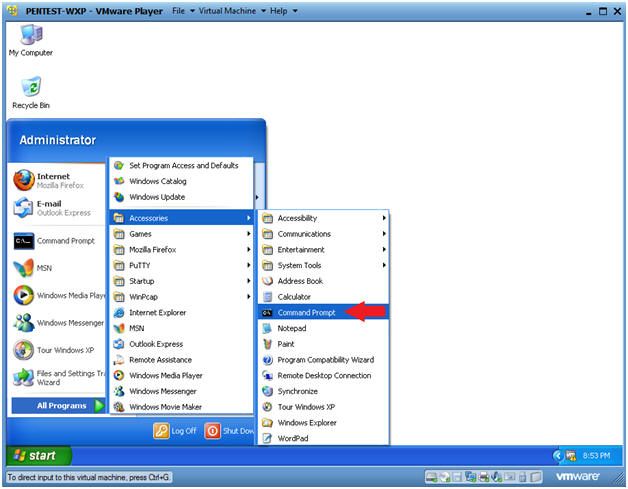
- Instructions:
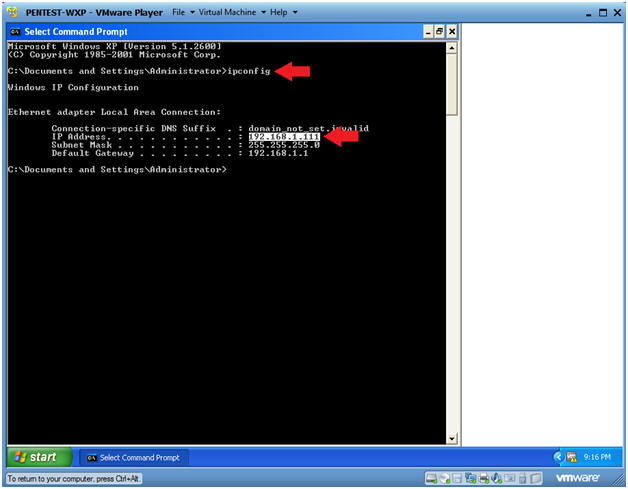
- Obtain PENTEST-WXP's IP Address
- Instructions:
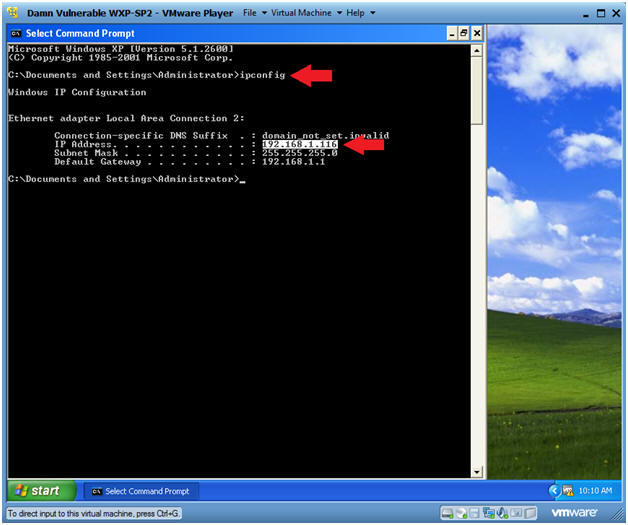
- ipconfig
- Note(FYI):
- This is the IP Address of the Scanning Machine.
- In my case, PENTEST-WXP's IP Address is 192.168.1.111.
- Your IP Address will be different.
- Record your PENTEST-WXP's IP Address.
- Instructions:
| Section 2: Power On Damn Vulnerable WXP-SP2 |
- Start Up Damn Vulnerable WXP-SP2.
- Instructions:
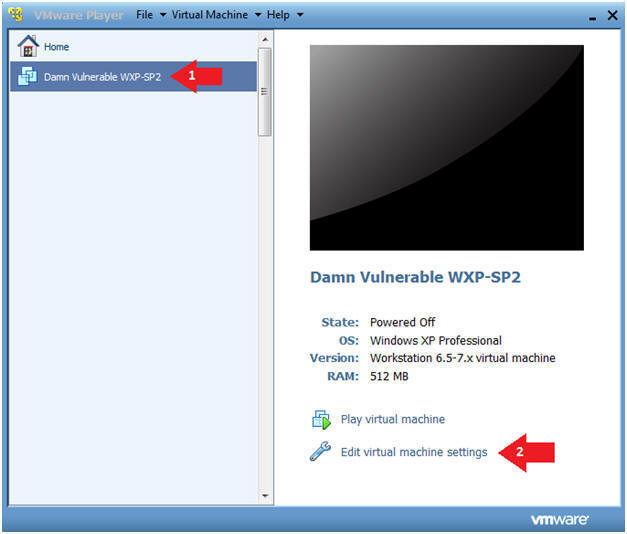
- Click on Damn Vulnerable WXP-SP2
- Click on Edit virtual machine Settings
- Note(FYI):
- For those of you not part of my class, this is a Windows XP machine running SP2.
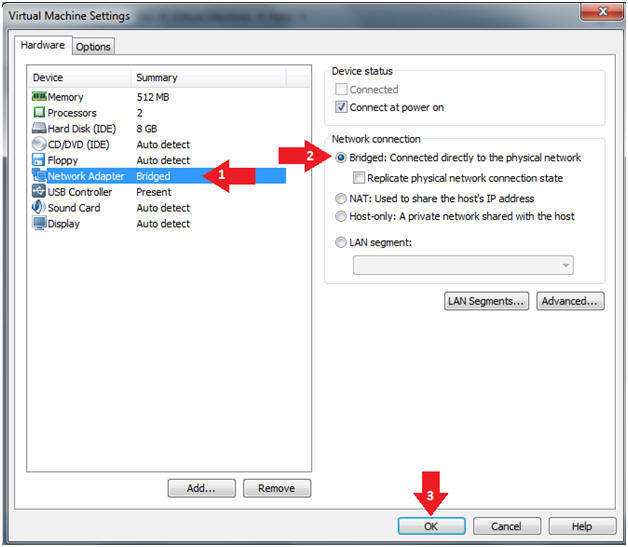
- Instructions:
- Edit Virtual Machine Settings
- Instructions:
- Click on Network Adapter
- Click on the Bridged Radio button
- Click on the OK Button
- Instructions:
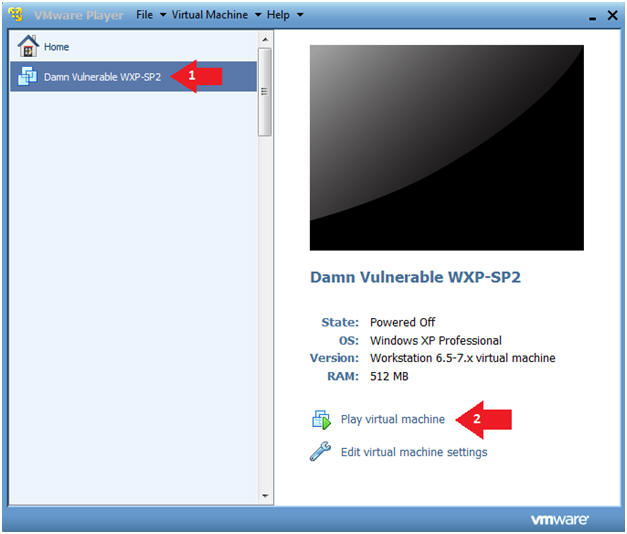
- Play Virtual Machine
- Instructions:
- Click on Damn Vulnerable WXP-SP2
- Click on Play virtual machine
- Instructions:
- Logging into Damn Vulnerable WXP-SP2.
- Instructions:
- Username: administrator
- Password: Use the Class Password or whatever you set it.
- Instructions:
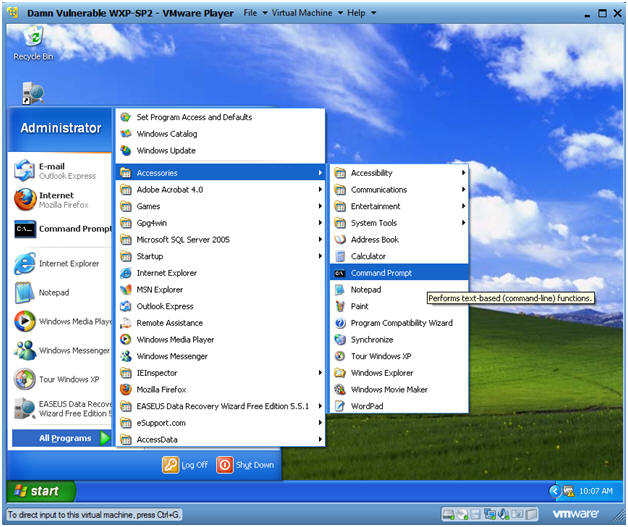
- Open a Command Prompt
- Instructions:
- Start --> All Programs --> Accessories --> Command Prompt
- Instructions:
- Obtain Damn Vulnerable WXP-SP2's IP Address
- Instructions:
- ipconfig
- Note(FYI):
- In my case, Damn Vulnerable WXP-SP2's IP Address 192.168.1.116.
- This is the IP Address of the Victim Machine that will be attacked by Metasploit.
- Record your Damn Vulnerable WXP-SP2's IP Address.
- Instructions:
| Section 3: Perform Nmap Quick Scan |
- Perform NMAP Quick Scan
- Instructions:
- Make sure you are on the PENTEST-WXP VM Machine
- Start Up NMAP by clicking on your NMAP icon located on your desktop.
- Instructions:
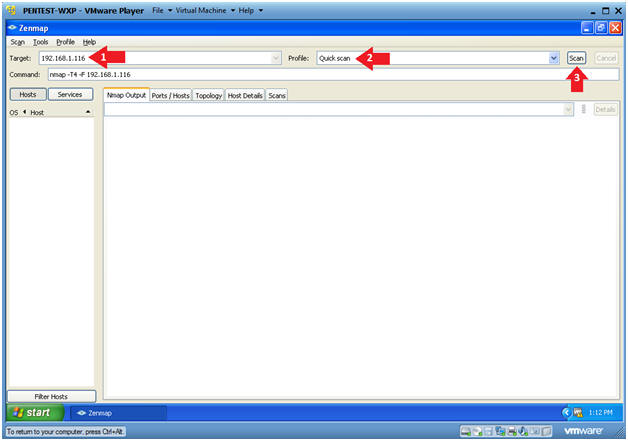
- Perform a quick scan by doing the following:
(See Below).
- Note(FYI):
- Replace 192.168.1.116 with Damn Vulnerable WXP-SP2's IP Address obtained in (Section 2, Step 6).
- Instructions:
- Target: 192.168.1.116
- You will be using PENTEST-WXP to scan Damn Vulnerable WXP-SP2.
- Profile: Select Quick Scan
- The Click Scan.
- Target: 192.168.1.116
- Note(FYI):
- Output Analysis
- Notes(FYI):
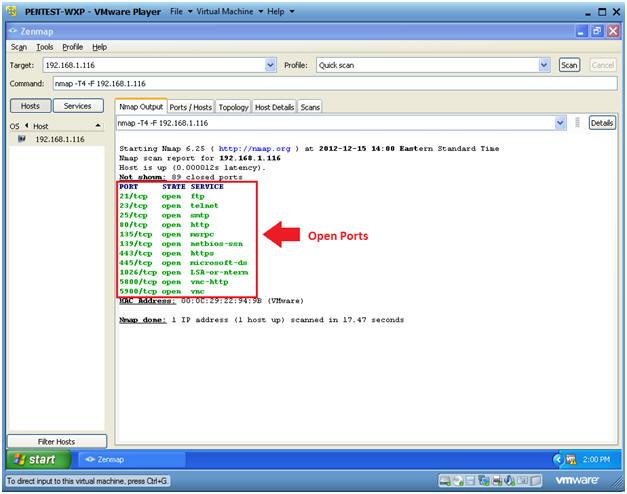
- Nmap's quick scan displays the
following basic network
metrics:
- If the host is up.
- How many ports are closed.
- Which ports are open and their service
name.
- e.g., 21 (ftp)
- Also, the MAC address is display with Nmap's guess of the OS being VMware.
- Nmap's quick scan displays the
following basic network
metrics:
- Notes(FYI):
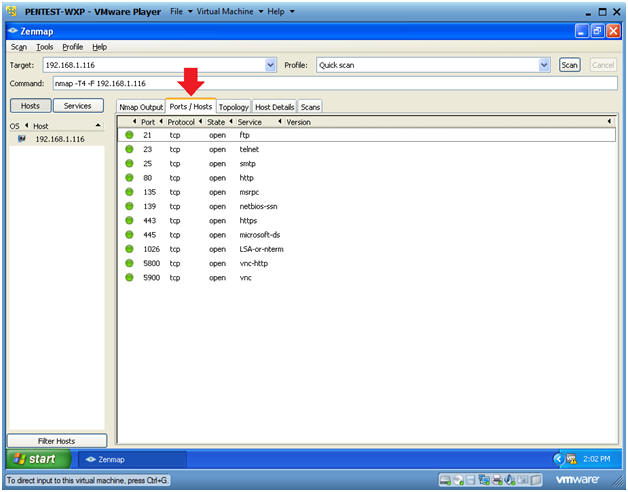
- Click on the Ports / Hosts tab
- Instructions:
- Click on the Ports/Hosts Tab
- Notes(FYI):
- This tabs represents all the open ports, protocol, state and service names.
- Instructions:
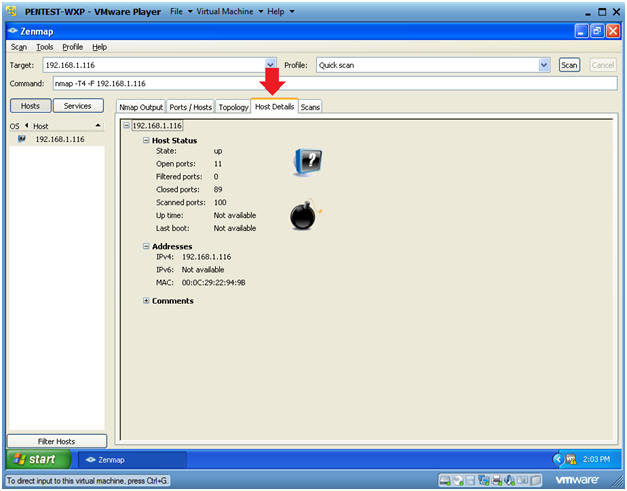
- Click on Host Details
- Instructions:
- Click on the Host Details Tab
- Notes(FYI):
- This tab represents the status of the host and its corresponding IP and MAC Addresses information.
- Instructions:
| Section 4: Nmap Intense Scan |
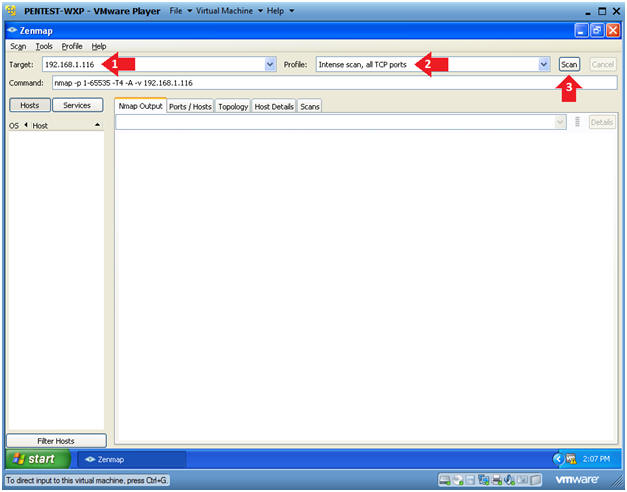
- Perform Intense Scan
- Note(FYI):
- Replace 192.168.1.116 with Damn Vulnerable WXP-SP2's IP Address obtained in (Section 2, Step 6).
- Instructions:
- Target: 192.168.1.116
- Change Profile to: Intense scan, all TCP ports
- Click Scan.
- Note(FYI):
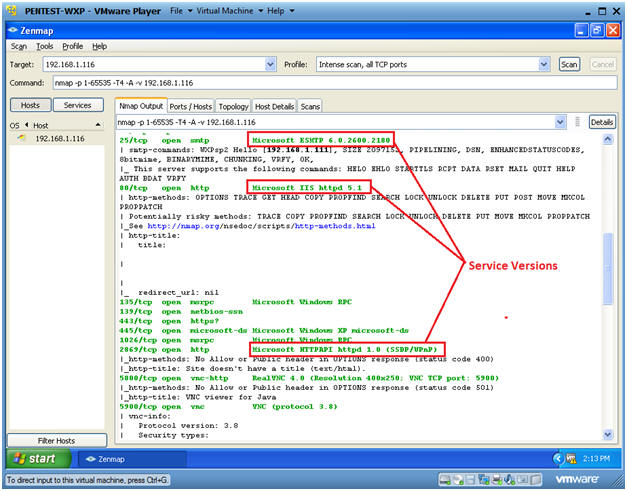
- Version Analysis
- Notes(FYI):
- Notice the results are more verbose.
- The actual version of the service was added to service
name.
- You can use this information to investigate possible exploits.
- For Example, Microsofts ISS http 5.1 webserver.
- Notes(FYI):
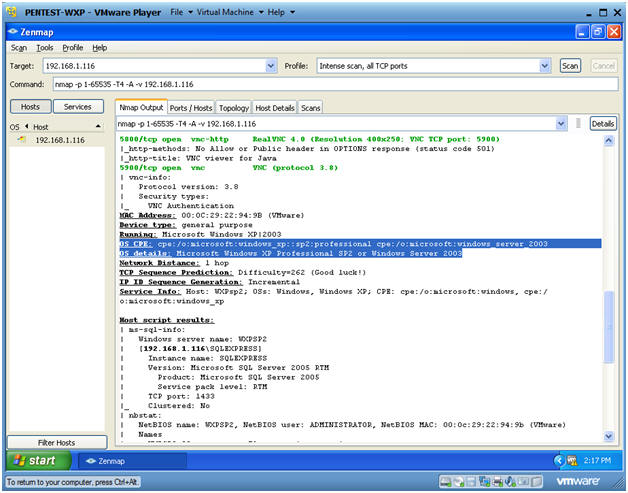
- Operating System Footprinting Analysis
- Notes(FYI):
- The OS details shows us that the actual
OS is Windows XP, and it is running SP2.
- In this case, an attacker might start salivating due to the MS08-067 exploit for SP2.
- The OS details shows us that the actual
OS is Windows XP, and it is running SP2.
- Notes(FYI):
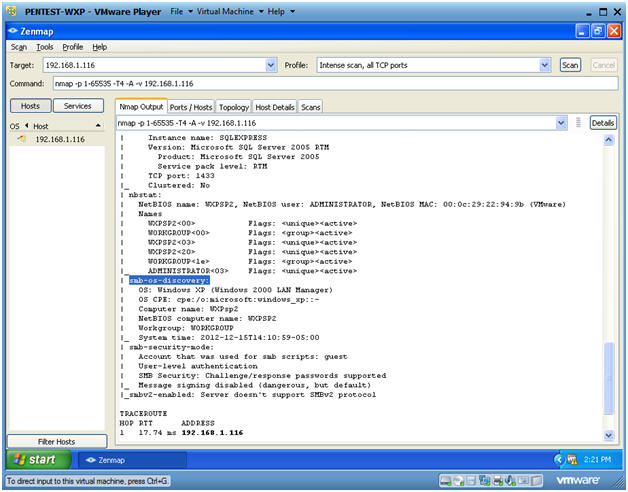
- Host Script Results Analysis
- Notes(FYI):
- Nmap runs nbstat to determine the NetBIOS
name and user.
- This information could be used for a brute force attack.
- Notice that SMB is running.
- The Server Message Block (SMB) Protocol is a network file sharing protocol, and as implemented in Microsoft Windows is known as Microsoft SMB Protocol.
- SMB Critical Updates
- Nmap runs nbstat to determine the NetBIOS
name and user.
- Notes(FYI):
| Section 5: Nmap Network Scan |
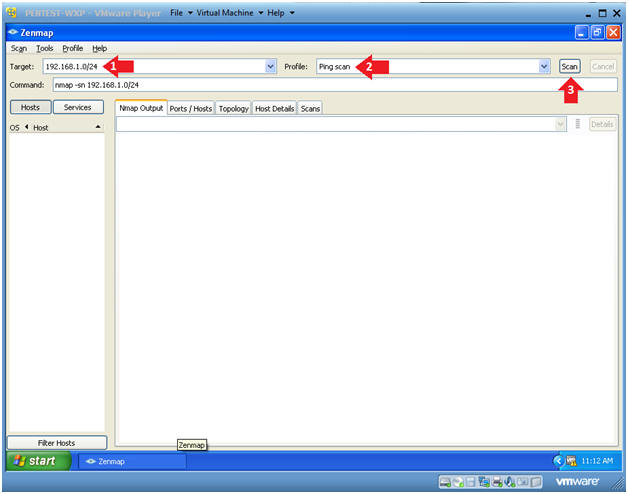
- Subnet Ping Scan
- Instructions:
- Change Target to the subnet address of
Damn Vulnerable WXP-SP2.
- In my case, 192.168.1.0/24
- Notice, that I replaced the last octet of my IP address with a 0.
- Change Profile to: Ping Scan
- Click Scan
- Change Target to the subnet address of
Damn Vulnerable WXP-SP2.
- Instructions:
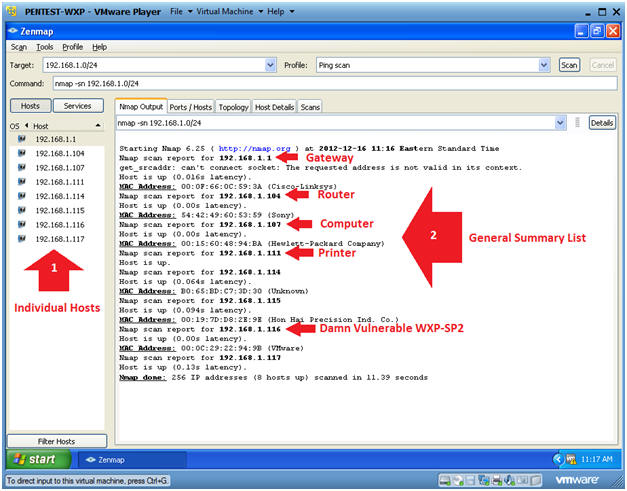
- Nmap Output Analysis
- Instructions:
- Big Red Arrow #1
- This displays a list of all the devices that returned an ICMP packet.
- You can click on each host to get their specific details.
- Big Red Arrow #2
- This displays a general list of all the
devices found which includes
- IP Address
- MAC Address
- And guess as to what it is.
- This displays a general list of all the
devices found which includes
- Big Red Arrow #1
- Instructions:
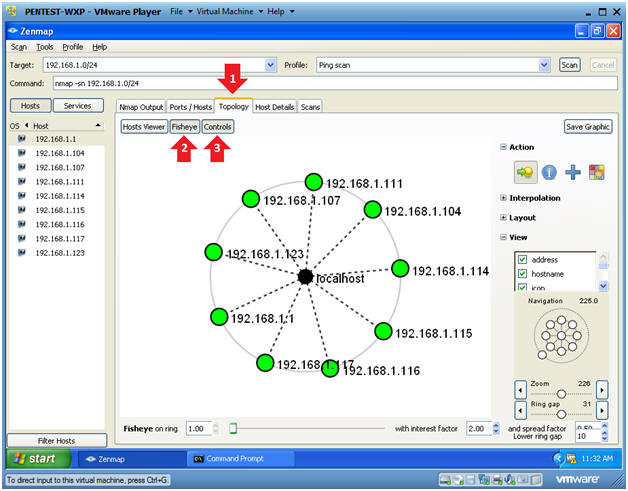
- Topology Analysis
- Instructions:
- Click on the Topology Tab.
- Click on Fisheye
- This will allow you to increase the size of the network picture.
- Click on Controls
- This will allow you to increase the size of the network rings.
- Note(FYI):
- This will give you a visual representation of how your network is laid out.
- When presenting a customer or management with a penetration testing analysis, this would be a good picture to throw into the report.
- Instructions:
| Section 6: Proof of Lab |
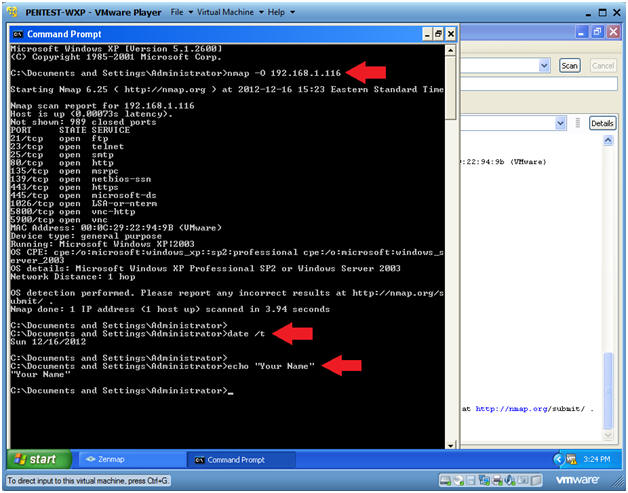
- Open a Command Prompt
- Instructions:
- Start --> All Programs --> Accessories --> Command Prompt

- Instructions:
-
Proof of Lab Instruction:
- Note(FYI):
- Replace 192.168.1.116 with Damn Vulnerable WXP-SP2's IP Address obtained in (Section 2, Step 6).
- Instructions:
- nmap -O 192.168.1.116
- date /t
- echo "Your Name"
- Replace the string "Your Name" with your actual name.
- e.g., echo "John Gray"
- Proof of Lab
Instructions:
- Press the PrtScn Button on your keyboard
- Paste into a word document
- Upload to Moodle
- Note(FYI):