(Metasploitable Project: Lesson 9)
{ Exploiting the Grub Menu to Gain the Root Password }
| Section 0. Background Information |
- Metasploitable
- Metasploitable is an intentionally vulnerable Linux virtual machine.
- This VM can be used to conduct security training, test security tools, and practice common penetration testing techniques.
- http://www.offensive-security.com/metasploit-unleashed/Metasploitable
- Pre-Requisite Lab
- Ubuntu 8.04 Physical Exploit.
- This lab illustrates how easy it is to compromise the root password (1) if you have physical access to the machine, and (2) don't know the root password.
- A counter-measure to this exploit, is to set the power-on password.
-
Lab Notes
- In this lab we will do the following:
- We will access the Grub menu during the boot process.
- We will edit the Grub menu to boot into single user mode.
- We will change the root password.
- In this lab we will do the following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- You are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2013 No content replication of any kind is allowed without express written permission.
| Section 1: Start Up the Metasploitable VM |
- Start Up VMWare Player
- Instructions:
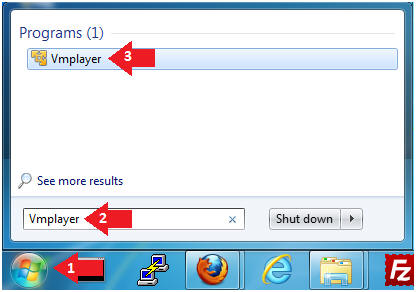
- Click the Start Button
- Type Vmplayer in the search box
- Click on Vmplayer
- Instructions:
- Open a Virtual Machine
- Instructions:
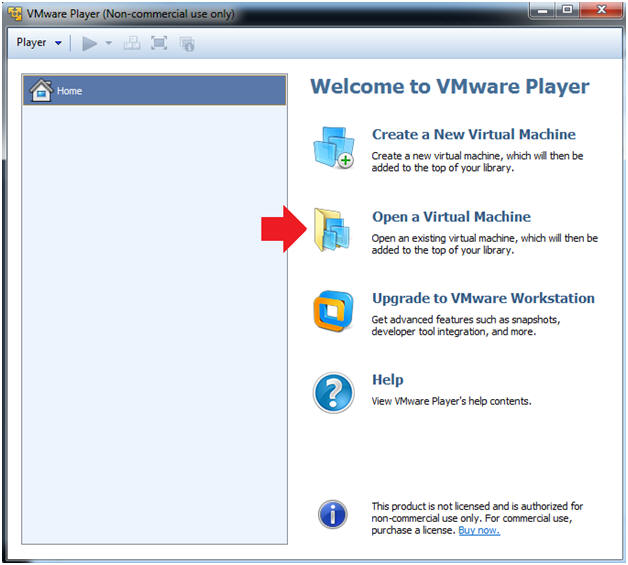
- Click on Open a Virtual Machine
- Instructions:
- Open the Metasploitable VM
- Instructions:
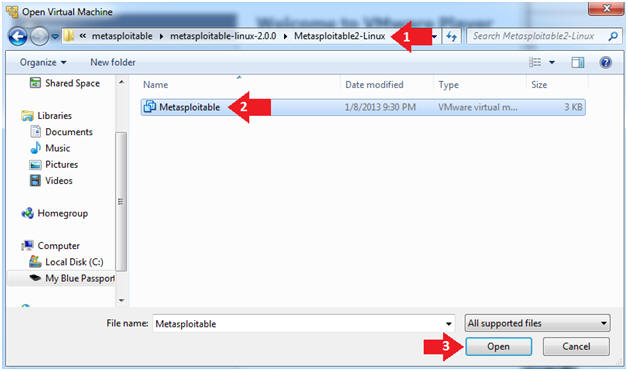
- Navigate to where the Metasploitable VM is located
- Click on on the Metasploitable VM
- Click on the Open Button
- Instructions:
- Edit the Metasploitable VM
- Instructions:
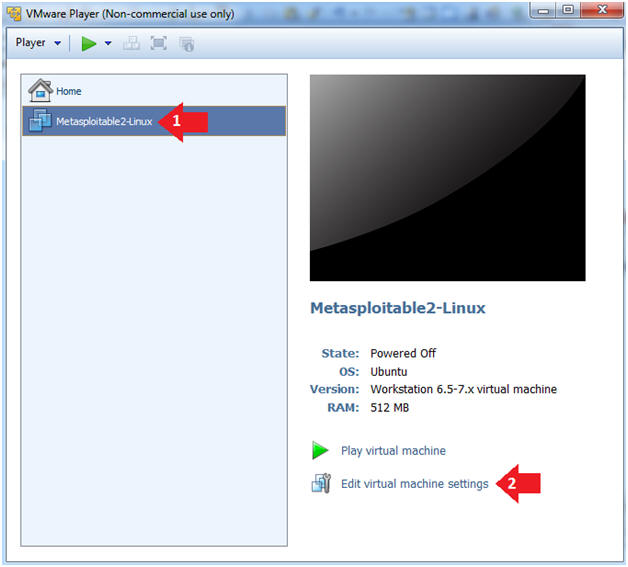
- Select Metasploitable2-Linux VM
- Click Edit virtual machine settings
- Instructions:
- Edit the Metasploitable VM
- Instructions:
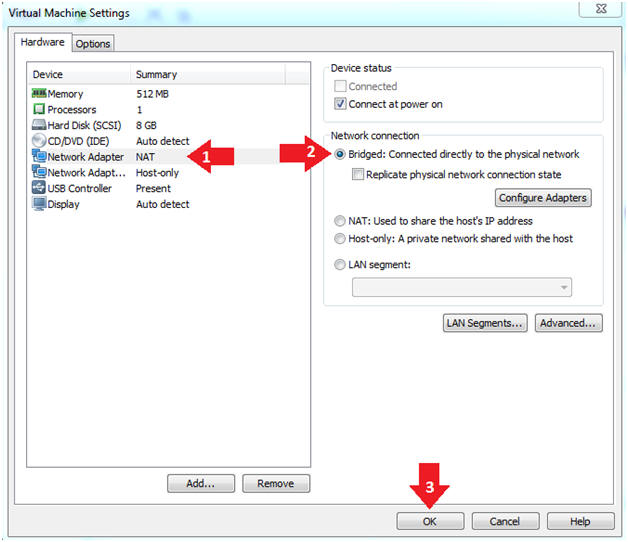
- Click on "Network Adapter NAT"
- Select the radio button "Bridged: Connected directly to the physical network"
- Click on the OK button
- Warning:
- By changing from NAT to Bridged opens the VM and network up to potential attacks.
- To maintain a safe network, you could (1) skip this section and only use the host-only network, (2) unplug your router from the internet, (3) use an ACL to not allow traffic into your network, etc.
- Instructions:
- Play the Metasploitable VM
- Instructions:
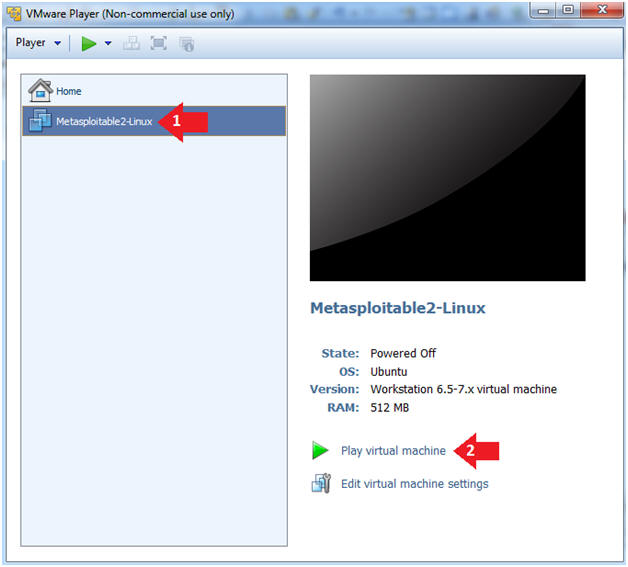
- Click on the Metasploitable VM
- Click on Play virtual machine
- Instructions:
| Section 2: Boot to Grub Menu |
- VMWare Menu
- Instructions
- Once you see the below vmware screen, (1) Left Click in the screen
- Instructions
- Access the Grub Menu
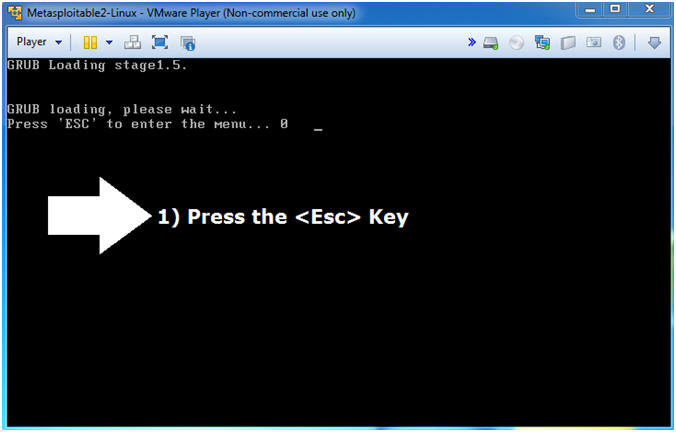
- Instructions
- Press the <Esc> key
- Instructions
| Section 3: Edit Grub Menu |
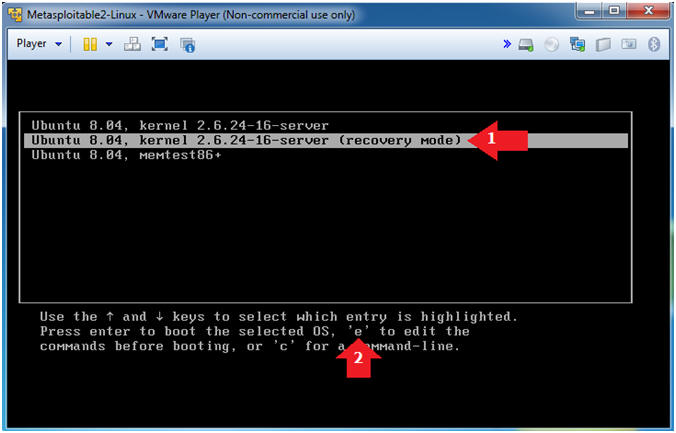
- Select Recovery Kernel
- Instructions
- Highlight: Ubuntu 8.04, kernel 2.6.24-16-server (recovery mode)
- Press "e" to edit
- Instructions
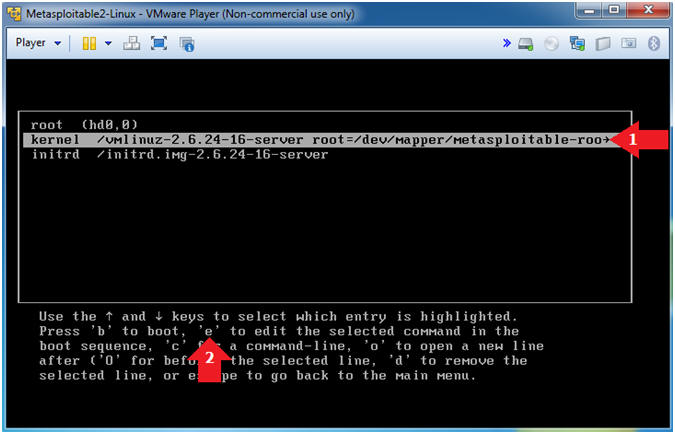
- Select the kernel
- Instructions
- Highlight: kernel /vmlinuz-2.6.24-16-server
- Press "e" to edit
- Instructions
- Edit kernel setting (Part 1)
- Instructions
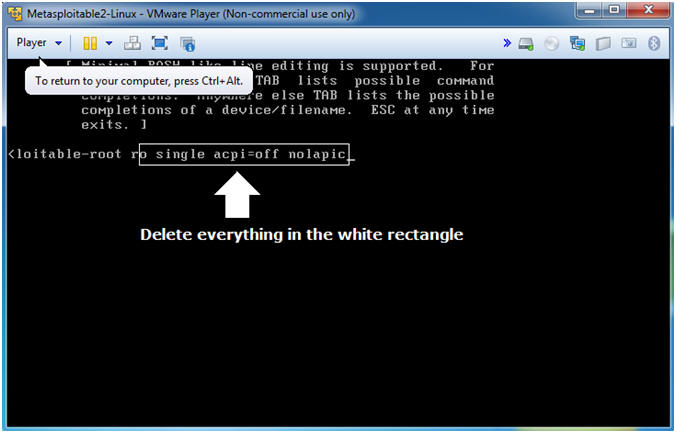
- Delete everything until you reach the "r" in "ro".
- Instructions
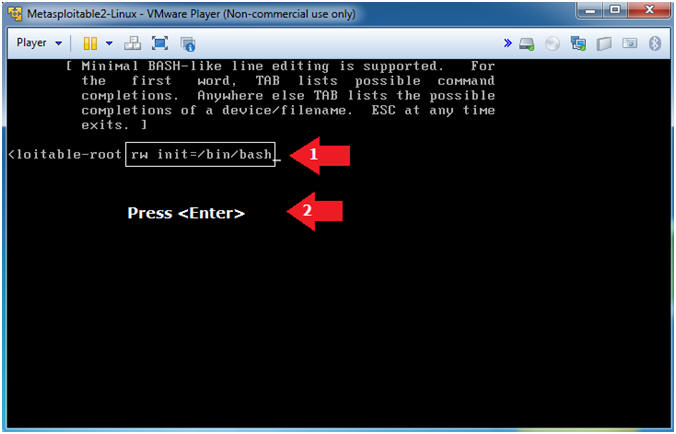
- Edit kernel setting (Part 2)
- Instructions
- Add the string rw init=/bin/bash
- Press <Enter>
- Instructions
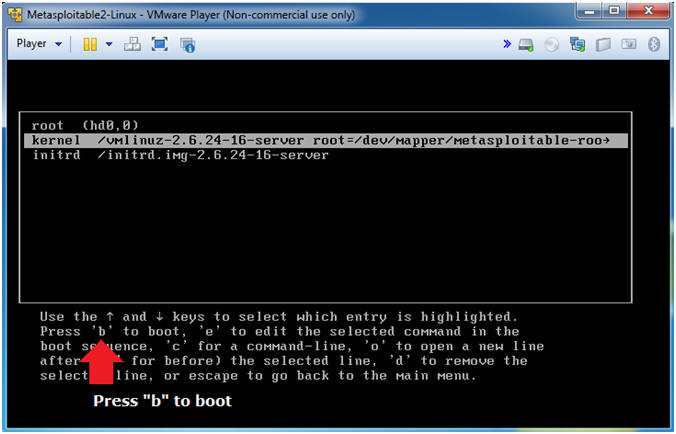
- Boot From Kernel
- Instructions
- Press "b" to boot.
- Instructions
| Section 4: Reset Root Password |
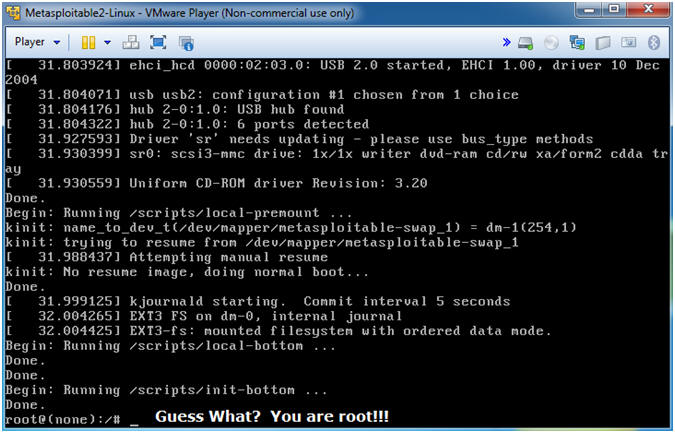
- Admire your work
- Note(FYI)
- You are now root
- Continue to next step.
- Note(FYI)
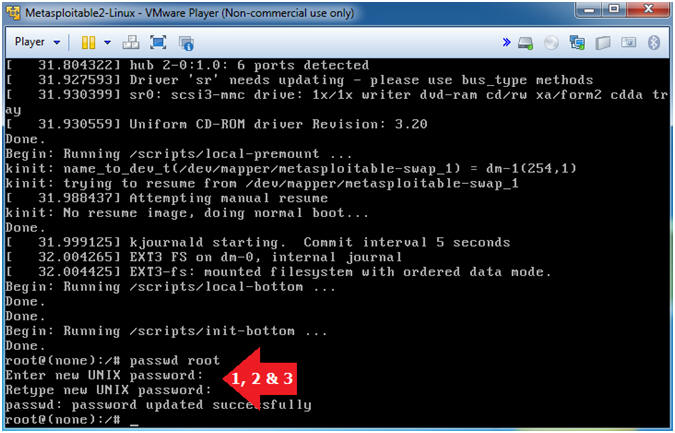
- Reset Root Password
- Instructions
- passwd root
- Enter new UNIX password:
- Retype new UNIX password:
- Instructions
| Section 5: Test Root Password |
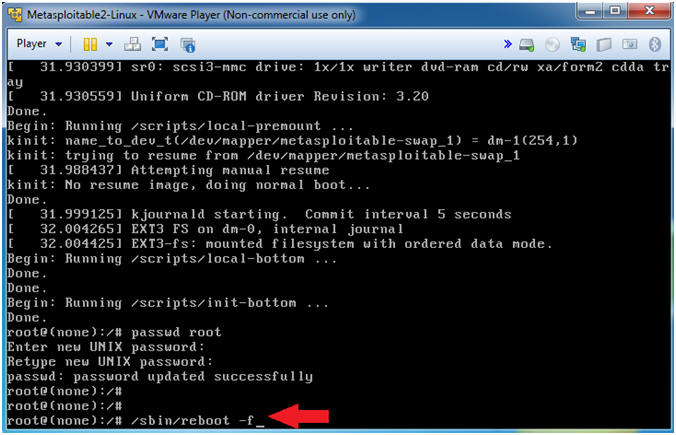
- Reboot Machine
- Instructions
- /sbin/reboot -f
- Instructions
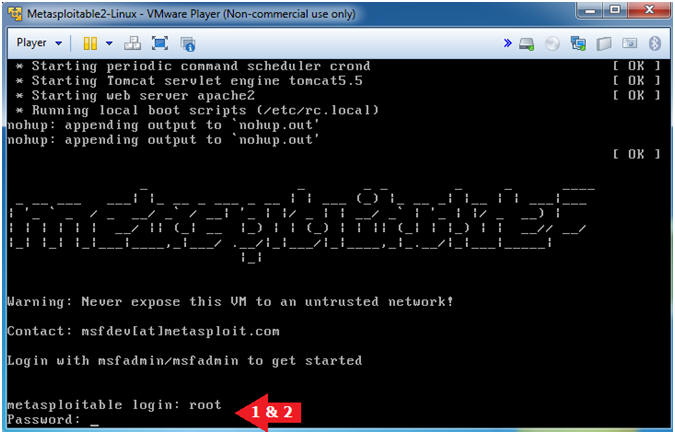
- Test Root Password
- Instructions
- metasploitable login: root
- Password:
- Instructions
| Section 6: Proof of Lab |
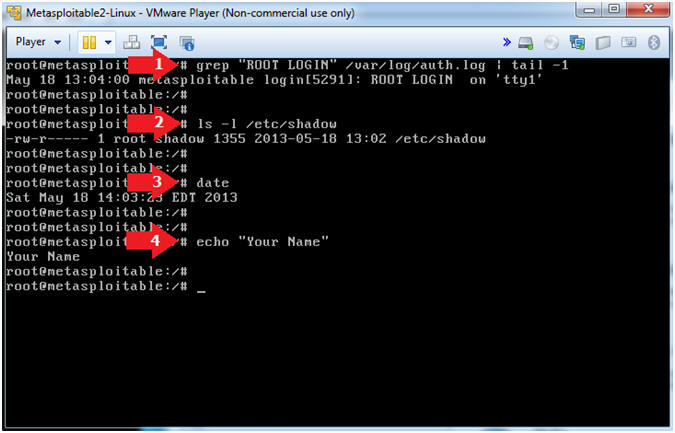
- Proof of Lab
- Instructions:
- grep "ROOT LOGIN" /var/log/auth.log | tail -1
- ls -l /etc/shadow
- date
- echo "Your Name"
- Put in your actual name in place of "Your Name"
- e.g., echo "John Gray"
-
Proof of Lab
Instructions
- Press the <Ctrl> and <Alt> key at the same time.
- Press the <PrtScn> key.
- Paste into a word document
- Upload to Moodle
- Instructions: