(Forensics: WinHex)
{ Very Basic Byte Level Checking }
| Background Information |
- Background
- WinHex is in its core a universal hexadecimal editor, particularly helpful in the realm of computer forensics, data recovery, low-level data processing, and IT security. An advanced tool for everyday and emergency use: inspect and edit all kinds of files, recover deleted files or lost data from hard drives with corrupt file systems or from digital camera cards. License type comparison.
- Reference Link:
| Prerequisite |
- Login to your
Instructor VM, as username
administrator
- For those of you that do not have access to my class, Instructor VM is a Windows XP Operating System.
- On the Instructor VM, go to
http://www.x-ways.net/winhex/
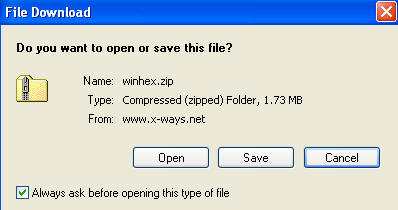
- Scroll down and click on Download (See Below)
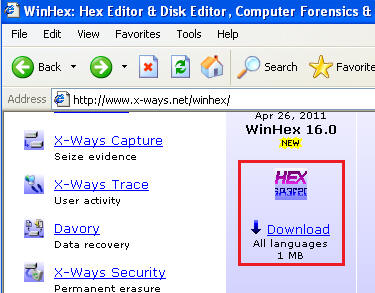
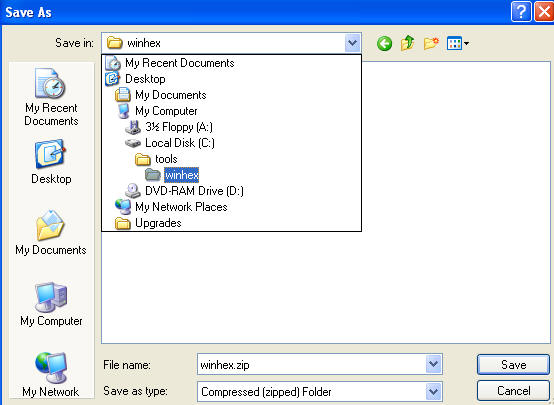
- Click on Save (See Below).
- Save to C:\tools\winhex
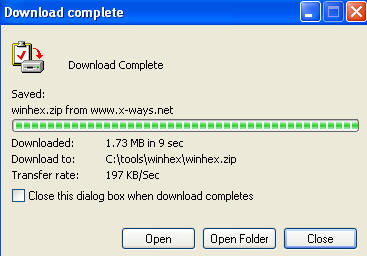
- Click on Open Folder
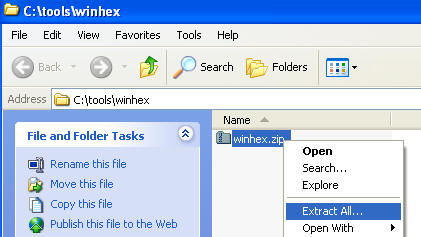
- Right Click on winhex.zip, and Extract All
- Click on Next
- Click on Next
- Click On Finish
| Section 1: Run winhex |
- On Your Instructor VM
- Bring up Windows Explorer
- Go To C:\tools\winhex
- Double Click on winhex.exe
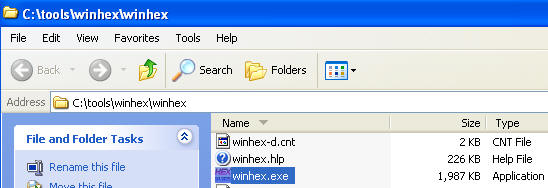
- Click on Run
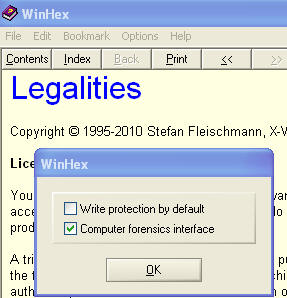
- Once winhex loads for the first timeyou will see a window
similar to the below.
- Select Computer Forensics Interface.
- Click on OK
- File Examination 1
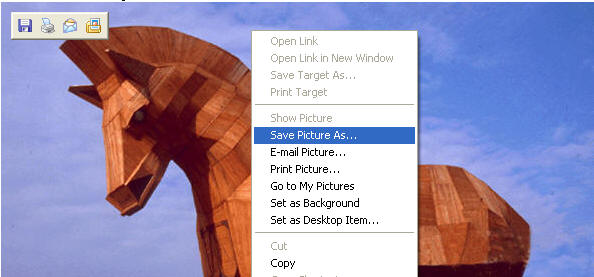
- The picture below is the first file you will examine with winhex.
- Please following the next steps

- Right Click on the Below Picture
- Select "Save Picture As..." (See Below)
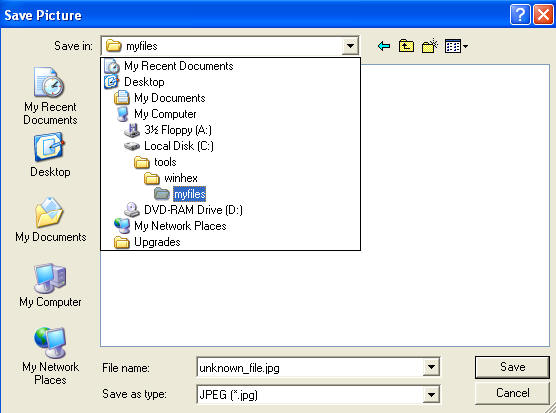
- Save the picture in
- C:\tools\winhex\myfiles
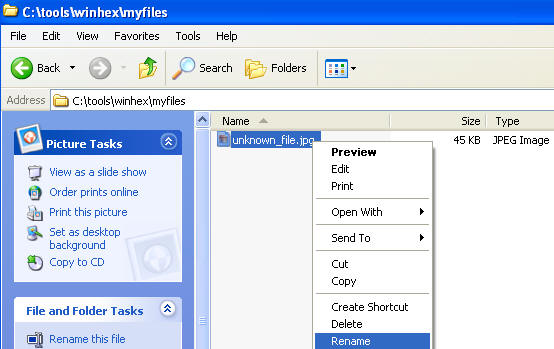
- Navigative your Windows Explorer to C:\tools\winhex\myfiles
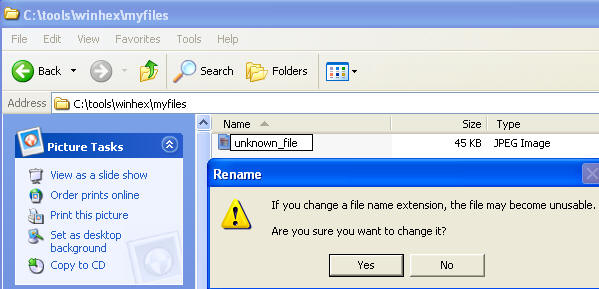
- Right click on unknown_file.jpb
- Click on Rename
- Rename unknown_file.jpg to unknown_file
- Answer Yes, when warned about the file becoming unusable.
| Section 2: Using winhex to look at an unknown file type |
- On Your Instructor VM
- Bring up Windows Explorer
- Go To C:\tools\winhex
- Double Click on winhex.exe

- Click on Run
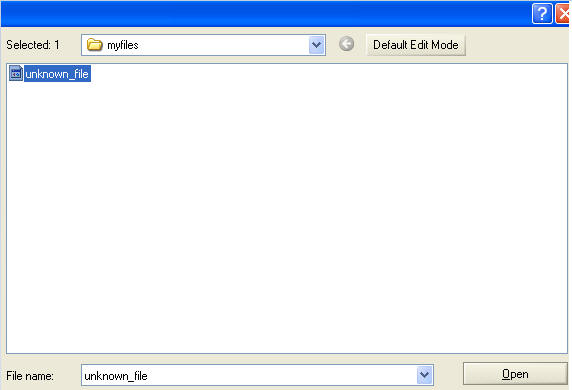
- Click on File, then Click on Open
- Navigate to
C:\tools\winhex\myfiles
- Click on file unknown_file.
- Click on Open
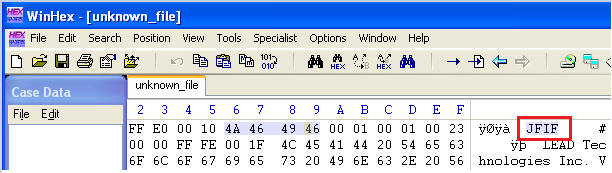
- Scroll over to the far left
- Notice on the first line it says JFIF. This is indicative of a JPEG file.
- Congratulations you have completed your first Byte Wise inspection of a file.
| Section 3: Using winhex to look at an encrypted file |
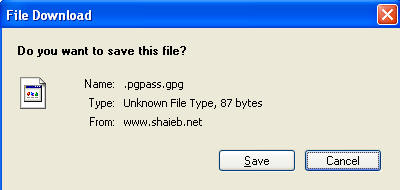
- Download Encrypted File
Here.
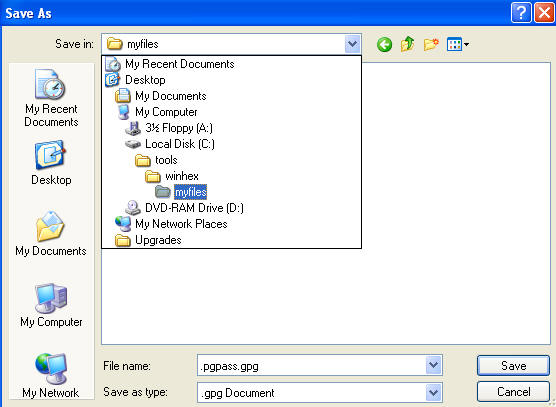
- Click Save
- Save File to
C:\tools\winhex\myfiles
- On Your Instructor VM
- Bring up Windows Explorer
- Go To C:\tools\winhex
- Double Click on winhex.exe

- Click on Run
- Click on File, then Click on Open
- Navigate to
C:\tools\winhex\myfiles
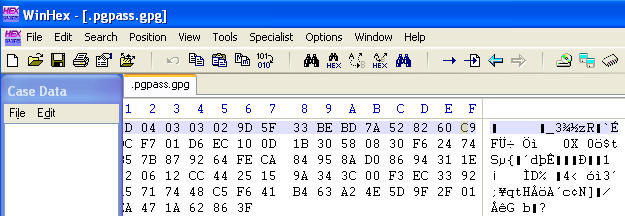
- Click on file .pgpass.gpg.
- Click on Open
- Scroll Over to the Far Right
- Notice that there is no relevant information that tells you what this file is about.
- It was first compressed with gzip, then it was encrypted with gpg.
| Proof of Lab |
- Do a screen print of Section 2, Step 5.
- Paste to a word document
- Submit to moodle.