(Volatility 2.2: Lesson 2)
{ Analyzing Stuxnet }
| Section 0. Background Information |
- What is Stuxnet?
- Stuxnet is a threat targeting a specific industrial control system likely in Iran, such as a gas pipeline or power plant. The ultimate goal of Stuxnet is to sabotage that facility by reprogramming programmable logic controllers (PLCs) to operate as the attackers intend them to, most likely out of their specified boundaries. [4]
- Pre-Requisite
- References
- Author: @PROFESX0R
- Michael Hale: Stuxnet's Footprint in Memory with Volatility
- Mark Russinovich: Analyzing a Stuxnet Infection with the Sysinternals Tools, Part I
- Michael Hale: http://code.google.com/p/volatility/wiki/CommandReference
- Symantec's: W32.Stuxnet Dossier
-
Lab Notes
- In this lab we will do the following:
- Download a Stuxnet memory capture.
- Analyze a Stuxnet memory capture using the above references.
- In this lab we will do the following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- Your are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2013 No content replication of any kind is allowed without express written permission.
| Section 1. Login to BackTrack |
- Start Up VMWare Player
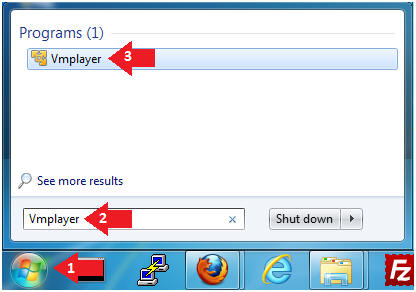
- Instructions:
- Click the Start Button
- Type Vmplayer in the search box
- Click on Vmplayer
- Instructions:
- Open a Virtual Machine
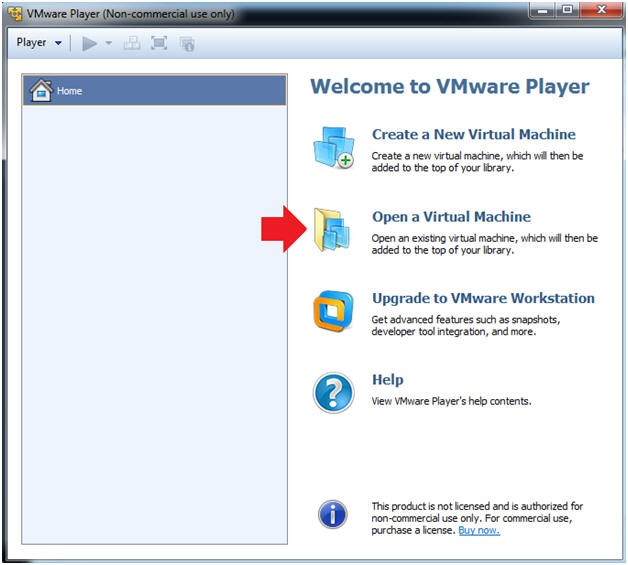
- Instructions:
- Click on Open a Virtual Machine
- Instructions:
- Open the BackTrack5R1 VM
- Instructions:
- Navigate to where the BackTrack5R1 VM is located
- Click on on the BackTrack5R1 VM
- Click on the Open Button
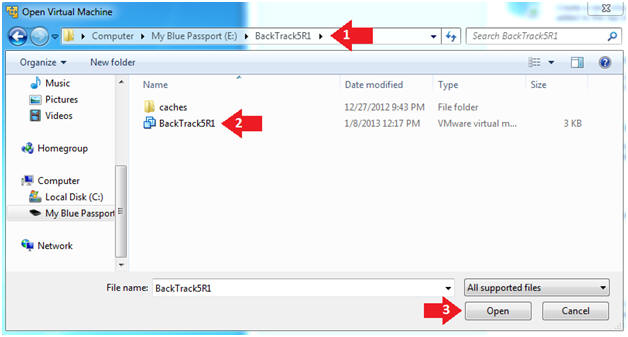
- Instructions:
- Edit the BackTrack5R1 VM
- Instructions:
- Select BackTrack5R1 VM
- Click Edit virtual machine settings
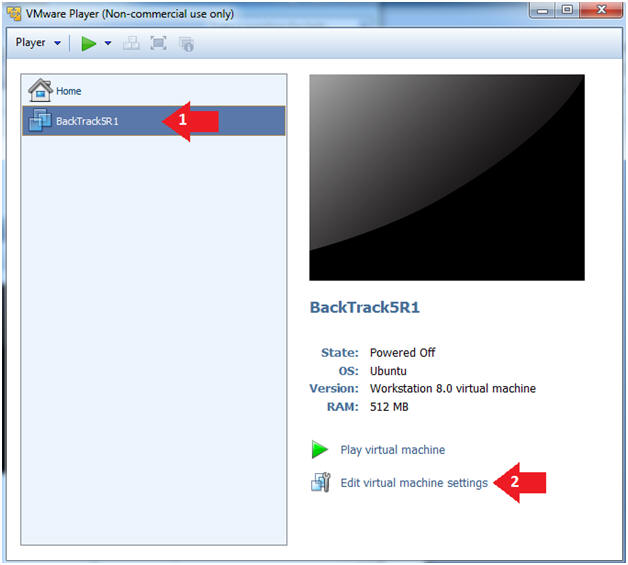
- Instructions:
- Edit Virtual Machine Settings
- Instructions:
- Click on Network Adapter
- Click on the Bridged Radio button
- Click on the OK Button
- Instructions:
- Play the BackTrack5R1 VM
- Instructions:
- Click on the BackTrack5R1 VM
- Click on Play virtual machine
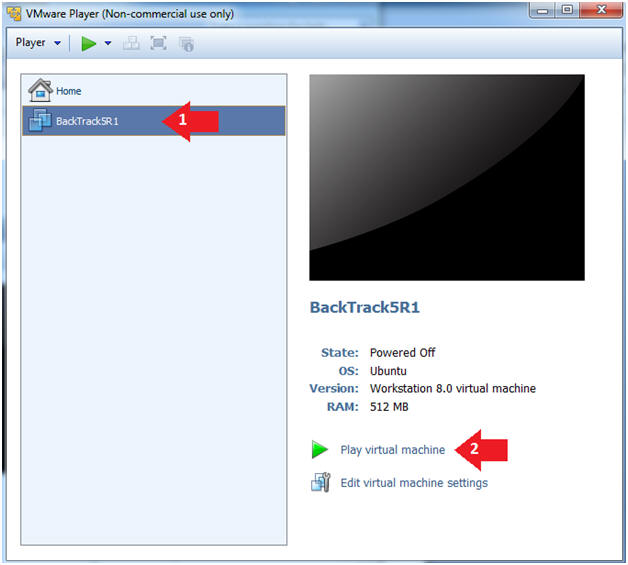
- Instructions:
- Login to BackTrack
- Instructions:
- Login: root
- Password: toor or <whatever you changed it to>.
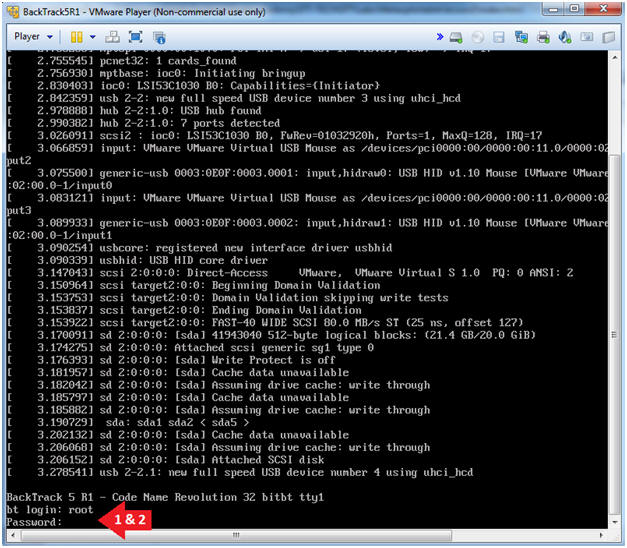
- Instructions:
- Bring up the GNOME
- Instructions:
- Type startx
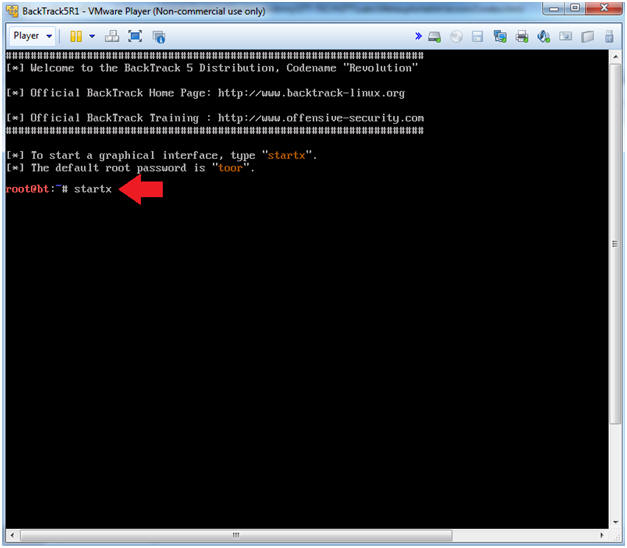
- Instructions:
| Section 2. Bring up a console terminal |
- Start up a terminal window
- Instructions:
- Click on the Terminal Window
- Instructions:
- Obtain the IP Address
- Instructions:
- ifconfig -a
- Note(FYI):
- My IP address 192.168.1.108.
- In your case, it will probably be different.
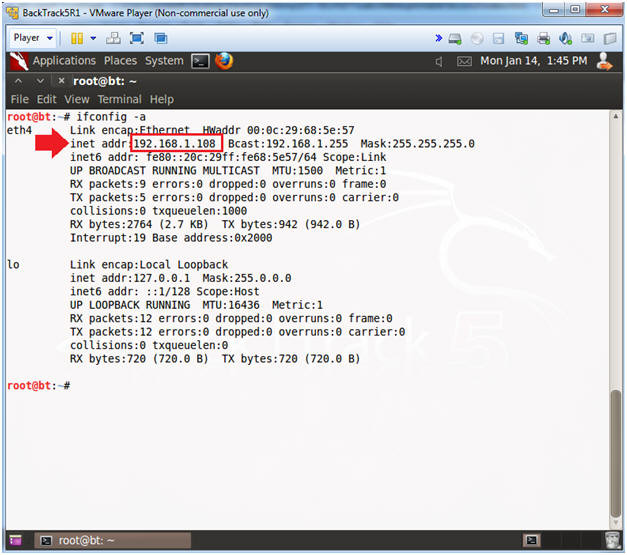
- Instructions:
| Section 3. Download a Stuxnet Image |
- Download a Stuxnet Image
- Instructions
- cd /pentest/forensics/volatility-2.2
- mkdir -p images/stuxnet/output
- cd images/stuxnet/
- wget http://malwarecookbook.googlecode.com/svn/trunk/stuxnet.vmem.zip
- unzip stuxnet.vmem.zip
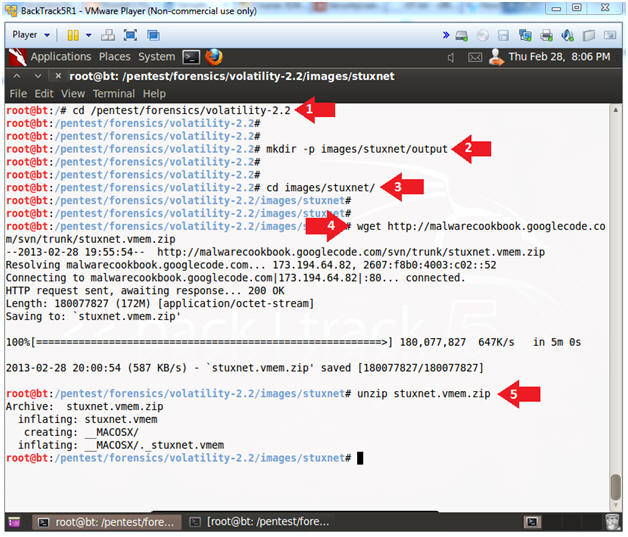
- Instructions
| Section 4. Determine Volatility Image |
- Determine Which Profile to Use
- Instructions
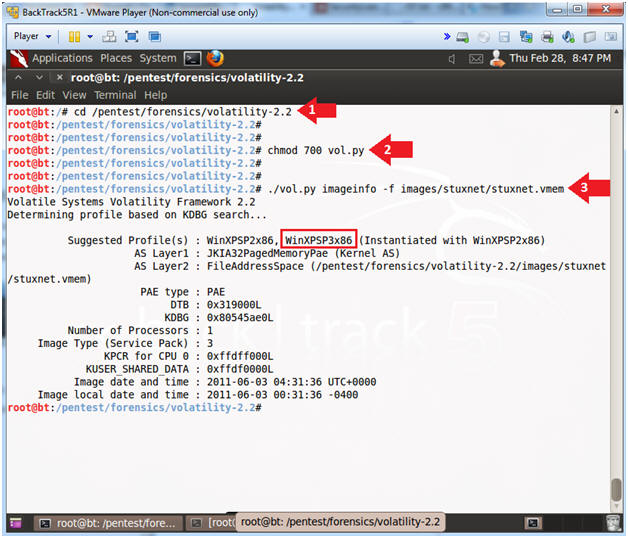
- cd /pentest/forensics/volatility-2.2
- chmod 700 vol.py
- Make vol.py executable.
- ./vol.py imageinfo -f images/stuxnet/stuxnet.vmem
- Note(FYI):
- For this image Volatility tells us to use the WinXPSP3x86 profile.
| Section 4. Analyze Stuxnet Process Tree |
- Basic Stuxnet Description
- Note(FYI):
- A normal Windows XP installation has just one instance of lsass.exe that the Winlogon process creates when the system boots. (Wininit creates it on Windows Vista and higher).
- [The following] process tree [example] reveals that the two new lsass.exe instances were both created by services.exe [], the Service Control Manager, which implies that Stuxnet somehow got its' code into the Services.exe process. [1][2].
- Mrxnet.sys is the driver that ... implements the rootkit that hides files, and Mrxcls.sys is a second Stuxnet driver file that launches the malware when the system boots. [1]
- What is lsass.exe
- Note(FYI):
- LSASS, or local security authority subsystem service, is a process that functions as part of the Microsoft Windows operating system.
- LSASS is part of the process for maintaining and enforcing the security protocols on the operating system.
- LSASS performs several important functions
- To ensure that the system remains free from unauthorized access
- LSASS oversees access to a computer or server.
- LSASS recognizes any restrictions on access to any information on the hard drive or the server.
- LSASS makes sure that only recognized access codes or other login credentials will allow persons to interact with password protected files, directories, etc.
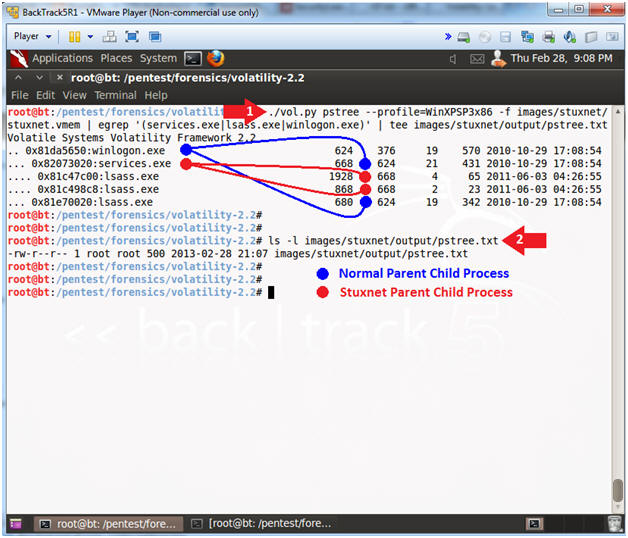
- Analyze Stuxnet Process Tree
- Instructions
- ./vol.py pstree --profile=WinXPSP3x86 -f images/stuxnet/stuxnet.vmem | egrep '(services.exe|lsass.exe|winlogon.exe)' | tee images/stuxnet/output/pstree.txt
- ls -l images/stuxnet/output/pstree.txt
- Note(FYI):
- The normal Parent-Child relation
- winlogon.exe (624) kicks off, DATE:
2010-10-29 17:08:54
- services.exe (668), DATE: 2010-10-29 17:08:54
- lsass.exe (680), 2010-10-29 17:08:54
- winlogon.exe (624) kicks off, DATE:
2010-10-29 17:08:54
- The Stuxnet Parent-Child relation
- services.exe(668) is NOT supposed
to, but kicks off
- lsass.exe (1928), DATE: 2011-06-03 04:26:55
- lsass.exe (868), DATE: 2011-06-03 04:26:55
- Notice these two lsass.exe processes were created 216 after winlogin.exe was started.
- services.exe(668) is NOT supposed
to, but kicks off
| Section 5. Analyze Sockets |
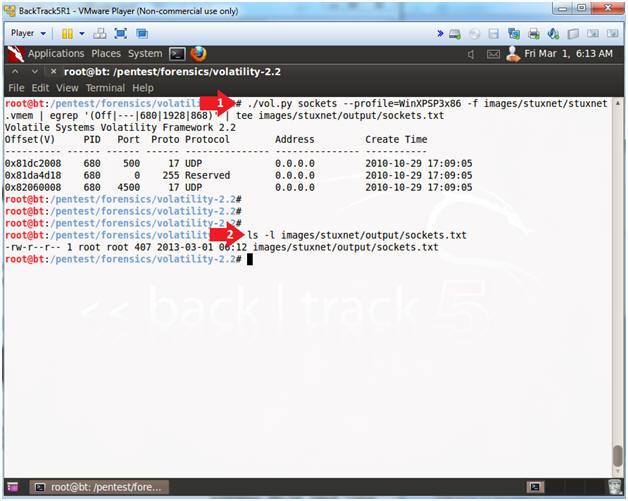
- Analyze Sockets
- Instructions
- ./vol.py sockets --profile=WinXPSP3x86 -f images/stuxnet/stuxnet.vmem | egrep '(Off|---|680|1928|868)' | tee images/stuxnet/output/sockets.txt
- ls -l images/stuxnet/output/sockets.txt
- Note(FYI):
- Another way that you can tell the good lsass.exe (680) processes from the bad (1928 & 868) lsass.exe process is that PID 680 are bound to Port 500 and 4500, while PIDs 1928 & 868 are not.
| Section 6. Analyze DLL's |
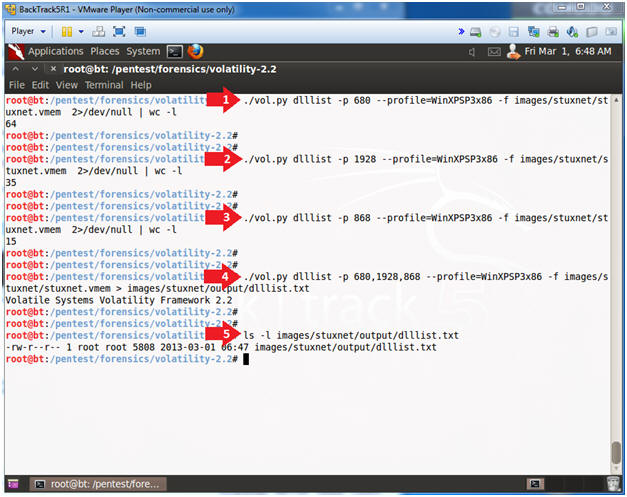
- Analyze lsass dll's
- Instructions
- ./vol.py dlllist -p 680 --profile=WinXPSP3x86 -f images/stuxnet/stuxnet.vmem 2>/dev/null | wc -l
- ./vol.py dlllist -p 1928 --profile=WinXPSP3x86 -f images/stuxnet/stuxnet.vmem 2>/dev/null | wc -l
- ./vol.py dlllist -p 868 --profile=WinXPSP3x86 -f images/stuxnet/stuxnet.vmem 2>/dev/null | wc -l
- ./vol.py dlllist -p 680,1928,868 --profile=WinXPSP3x86 -f images/stuxnet/stuxnet.vmem > images/stuxnet/output/dlllist.txt
- ls -l images/stuxnet/output/dlllist.txt
- Note(FYI):
- [A]nother suspicious characteristic of the two superfluous processes is the fact that they have very few DLLs loaded. [1][2].
- DLLs are automatically added ... when a process call the LoadLibrary. [3]
- Notice that the good PID (680) has 64 DLLs attached to its' process.
- Notice that the bad PID (1928) has 35 DLLs attached to its' process.
- Notice that the bad PID (868) has 15 DLLs attached to its' process.
| Section 7. Analyze Process IDs with malfind |
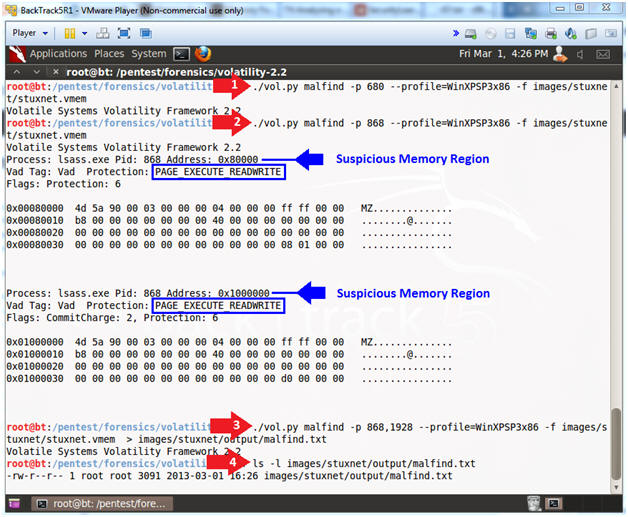
- Analyze Process IDs with malfind
- Instructions
- ./vol.py malfind -p 680 --profile=WinXPSP3x86 -f images/stuxnet/stuxnet.vmem
- ./vol.py malfind -p 868 --profile=WinXPSP3x86 -f images/stuxnet/stuxnet.vmem
- ./vol.py malfind -p 868,1928 --profile=WinXPSP3x86 -f images/stuxnet/stuxnet.vmem > images/stuxnet/output/malfind.txt
- ls -l images/stuxnet/output/malfind.txt
- Note(FYI):
- The malfind command has several purposes. You can use it to find hidden or injected code/DLLs in user mode memory, based on characteristics such as VAD tag and page permissions. [3]
- Services.exe, Lsass.exe or Explorer.exe should not have write permission.
- Notice, that PID(680) did not return any results, while PID(868 & 1928) do.
| Section 8. Bypassing Behavior Blocking Wheb Loading DLLs |
- What is Address space layout randomization (ASLR)
- Note(FYI):
- Address space layout randomization (ASLR) is a computer security method which involves randomly arranging the positions of key data areas, usually including the base of the executable and position of libraries, heap, and stack, in a process's address space.
- Bypassing Behavior Blocking When Loading DLLs
- Note(FYI):
- Whenever Stuxnet needs to load a DLL, including itself, it uses a special method designed to bypass behavior- blocking and host intrusion-protection based technologies that monitor LoadLibrary calls. Stuxnet calls Load - Library with a specially crafted file name that does not exist on disk and normally causes LoadLibrary to fail. However, W32.Stuxnet has hooked Ntdll.dll to monitor for requests to load specially crafted file names. These specially crafted filenames are mapped to another location instead—a location specified by W32.Stuxnet. That location is generally an area in memory where a .dll file has been decrypted and stored by the threat previously. The filenames used have the pattern of KERNEL32.DLL.ASLR.[HEXADECIMAL] or SHELL32.DLL.ASLR. [HEXA - DECIMAL], where the variable [HEXADECIMAL]is a hexadecimal values. [4]
- Hiding DLLs
- Instructions
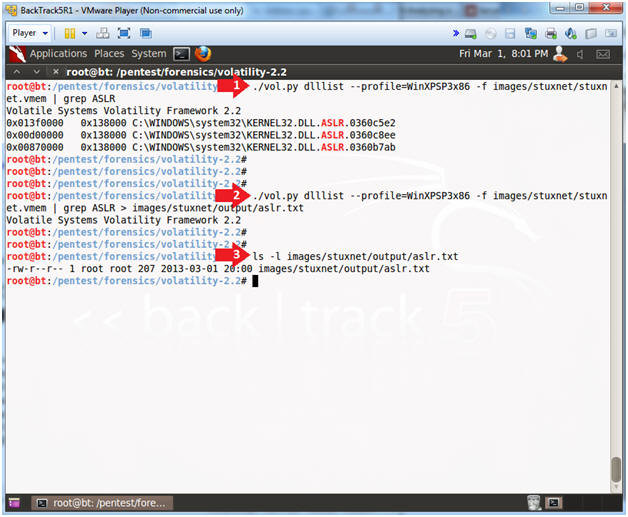
- ./vol.py dlllist --profile=WinXPSP3x86 -f images/stuxnet/stuxnet.vmem | grep ASLR
- ./vol.py dlllist --profile=WinXPSP3x86 -f images/stuxnet/stuxnet.vmem | grep ASLR > images/stuxnet/output/aslr.txt
- ls -l images/stuxnet/output/aslr.txt
- Note(FYI):
- Step 1 displays the Stuxnet specially crafted files designed to bypass the ASRL.
| Section 9. Using ldrmodules to find hidden DLLs |
- Using ldrmodules to find hidden DLLs
- Note(FYI):
- There are many ways to hide a DLL. One of the ways involves unlinking the DLL from one (or all) of the linked lists in the PEB (Process Enviroment Block). However, when this is done, there is still information contained within the VAD (Virtual Address Descriptor) which identifies the base address of the DLL and its full path on disk. To cross-reference this information (known as memory mapped files) with the 3 PEB lists, use the ldrmodules command. For each memory mapped Portable Executable (PE) file, the ldrmodules command prints a 0 or a 1 if the PE exists in the PEB lists. [3]
- Using ldrmodules
- Instructions
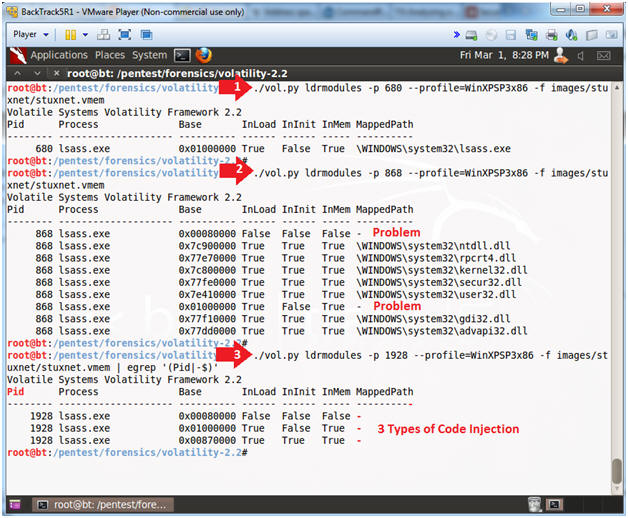
- ./vol.py ldrmodules -p 680
--profile=WinXPSP3x86 -f images/stuxnet/stuxnet.vmem
- This is normal.
- ./vol.py ldrmodules -p 868
--profile=WinXPSP3x86 -f images/stuxnet/stuxnet.vmem
- Notice the lines identified by the word "Problem".
- ./vol.py ldrmodules -p 1928 --profile=WinXPSP3x86 -f images/stuxnet/stuxnet.vmem | egrep '(Pid|-$)'
- Note(FYI):
- The lines identified as a problem are either suspicious because an entry is missing from one of the PEB (Process Enviroment Block) lists or because the path name is blank.
| Section 10. Using procexedump to dump process executables |
- Using procexedump to dump process executables
- Note(FYI):
- To dump a process's executable (not including the slack space), use the procexedump command.
- Using procexedump
- Instructions
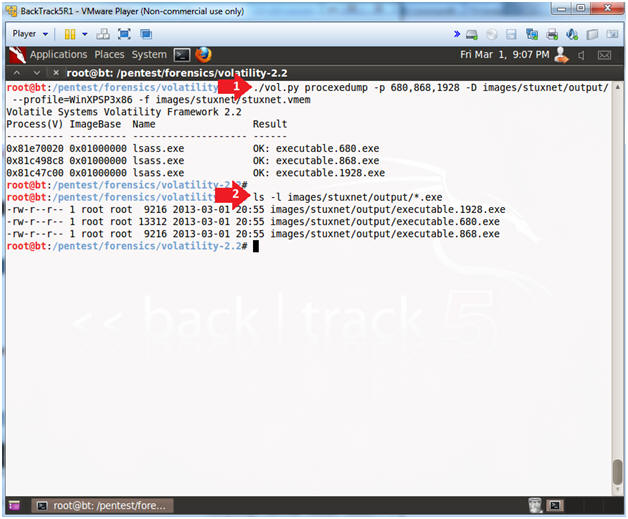
- ./vol.py procexedump -p 680,868,1928 -D images/stuxnet/output/ --profile=WinXPSP3x86 -f images/stuxnet/stuxnet.vmem
- ls -l images/stuxnet/output/*.exe
- Looking at Malicious Hooks
- Instructions
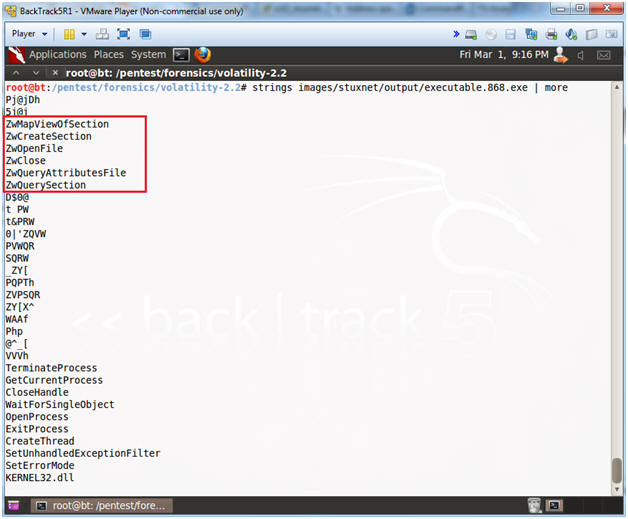
- strings images/stuxnet/output/executable.868.exe | more
- Note(FYI):
- The below example is the second type of code injection used by Stuxnet. The names of the APIs inside of the red rectangle are the ones hooked by the malware PID 868. [3].
- Analyzing a Stuxnet Infection with the Sysinternals Tools, Part I, See Page 13.
| Section 11. Proof of Lab |
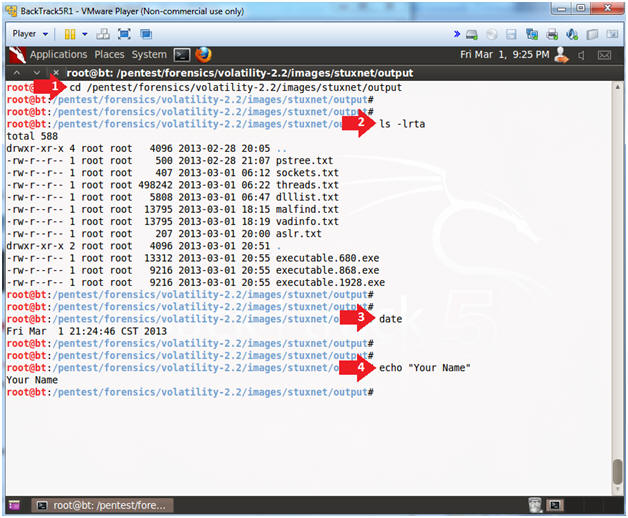
- Proof of Lab
-
Proof Of Lab Instructions:
- Do a PrtScn of the below commands
- Paste into a word document
- Upload to Moodle
- Instructions
- cd /pentest/forensics/volatility-2.2/images/stuxnet/output
- ls -lrts
- date
- echo "Your Name"
- Put in your actual name in place of "Your Name"
- e.g., echo "John Gray"
-
Proof Of Lab Instructions: