(Volatility: Lesson 1)
{ Installing Volatility on BackTrack 5 R1 }
| Section 0. Background Information |
- Volatility Overview
- https://www.volatilesystems.com/
- The Volatility Framework is a completely open collection of tools, implemented in Python under the GNU General Public License, for the extraction of digital artifacts from volatile memory (RAM) samples. The extraction techniques are performed completely independent of the system being investigated but offer unprecedented visibility into the runtime state of the system. The framework is intended to introduce people to the techniques and complexities associated with extracting digital artifacts from volatile memory samples and provide a platform for further work into this exciting area of research.
- Pre-Requisite Lesson
-
Lab Notes
- In this lab we will do the following:
- Download Volatility 2.0
- Un-Tar Volatility 2.0
- Test Volatility 2.0
- In this lab we will do the following:
- Next Lesson
- Capabilities
-
The Volatility Framework currently provides the following extraction capabilities for memory samples
- Image date and time
- Running processes
- Open network sockets
- Open network connections
- DLLs loaded for each process
- Open files for each process
- Open registry handles for each process
- A process' addressable memory
- OS kernel modules
- Mapping physical offsets to virtual addresses (strings to process)
- Virtual Address Descriptor information
- Scanning examples: processes, threads, sockets, connections, modules
- Extract executables from memory samples
- Transparently supports a variety of sample formats (ie, Crash dump, Hibernation, DD)
- Automated conversion between formats
-
| Section 1: Login to BackTrack |
- Start Up VMWare Player
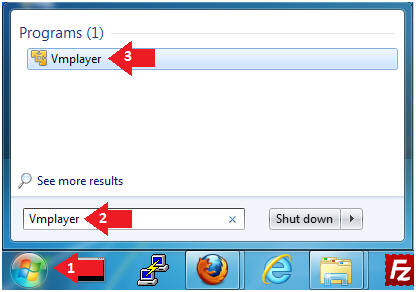
- Instructions:
- Click the Start Button
- Type Vmplayer in the search box
- Click on Vmplayer
- Instructions:
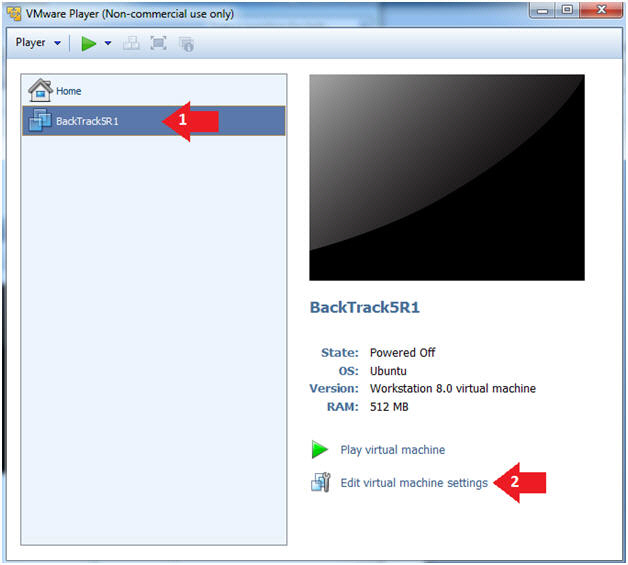
- Edit the BackTrack5R1 VM
- Instructions:
- Select BackTrack5R1 VM
- Click Edit virtual machine settings
- Instructions:
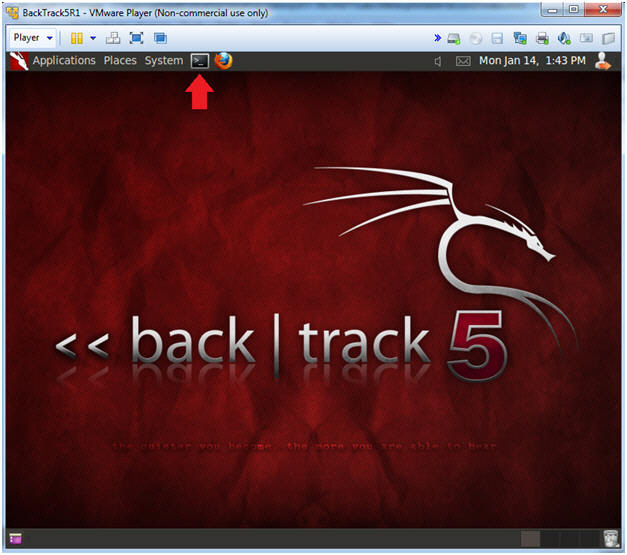
- Edit Virtual Machine Settings
- Instructions:
- Click on Network Adapter
- Click on the Bridged Radio button
- Click on the OK Button
- Instructions:
- Play the BackTrack5R1 VM
- Instructions:
- Click on the BackTrack5R1 VM
- Click on Play virtual machine
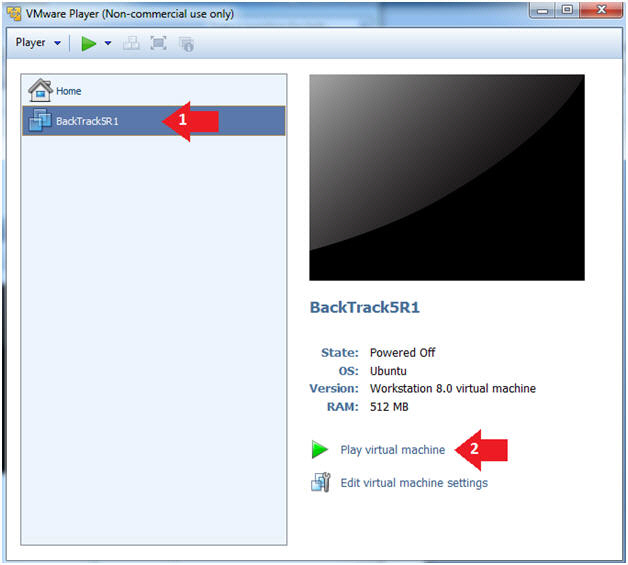
- Instructions:
- Login to BackTrack
- Instructions:
- Login: root
- Password: toor or <whatever you changed it to>.
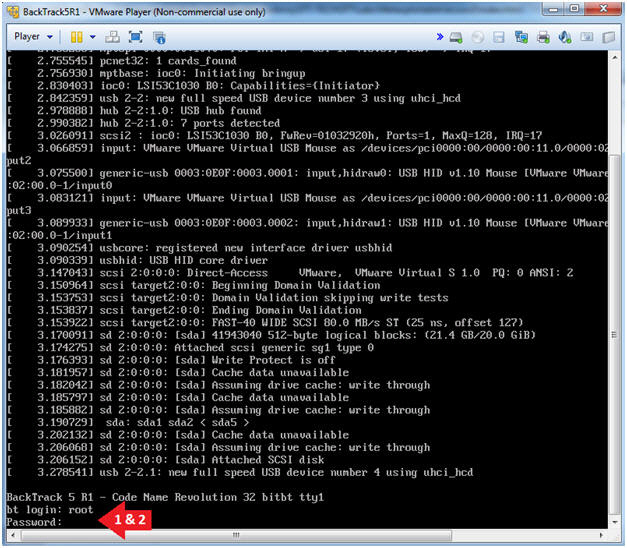
- Instructions:
- Bring up the GNOME
- Instructions:
- Type startx
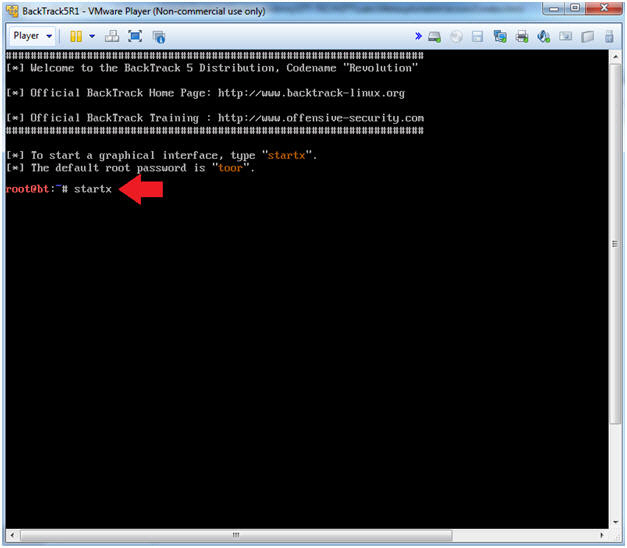
- Instructions:
| Section 2: Bring up a console terminal |
- Start up a terminal window
- Instructions:
- Click on the Terminal Window
- Instructions:
- Obtain the IP Address
- Instructions:
- ifconfig -a
- Note(FYI):
- My IP address 192.168.1.112.
- In your case, it will probably be different.
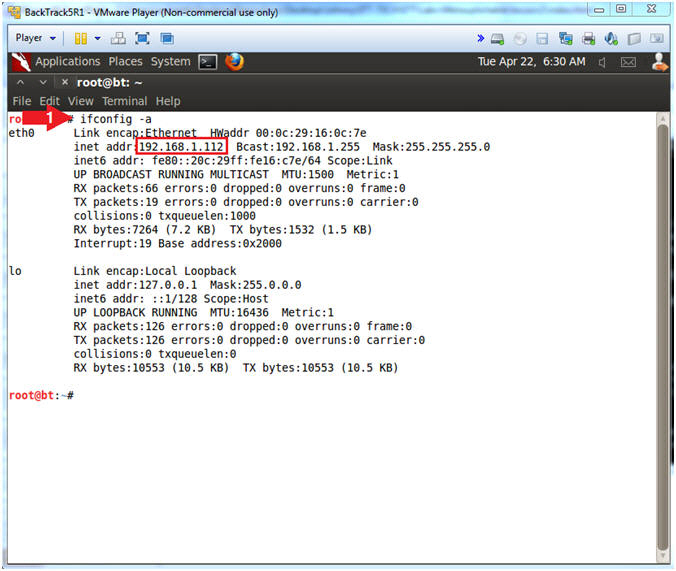
- Instructions:
| Section 3: Installing Volatility |
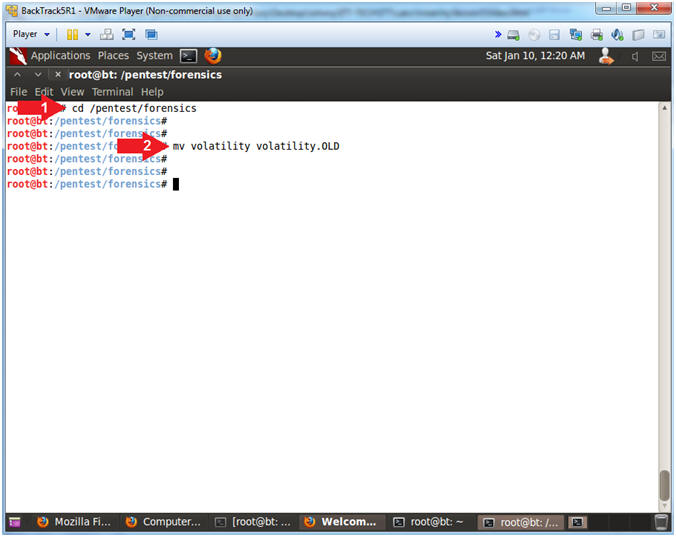
- Move Old Volatility Instance
- Instructions
- cd /pentest/forensics
- mv volatility volatility.OLD
- Instructions
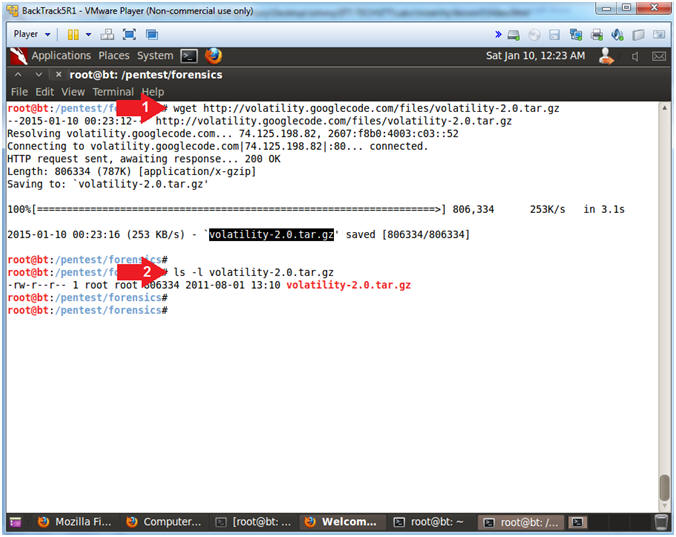
- Download Volatility 2.0
- Instructions
- wget --no-check-certificate https://storage.googleapis.com/google-code-archive-downloads/v2/code.google.com/volatility/volatility-2.0.tar.gz
- WGET is a non-interactive downloader.
- ls -l volatility-2.0.tar.gz
- wget --no-check-certificate https://storage.googleapis.com/google-code-archive-downloads/v2/code.google.com/volatility/volatility-2.0.tar.gz
- Instructions
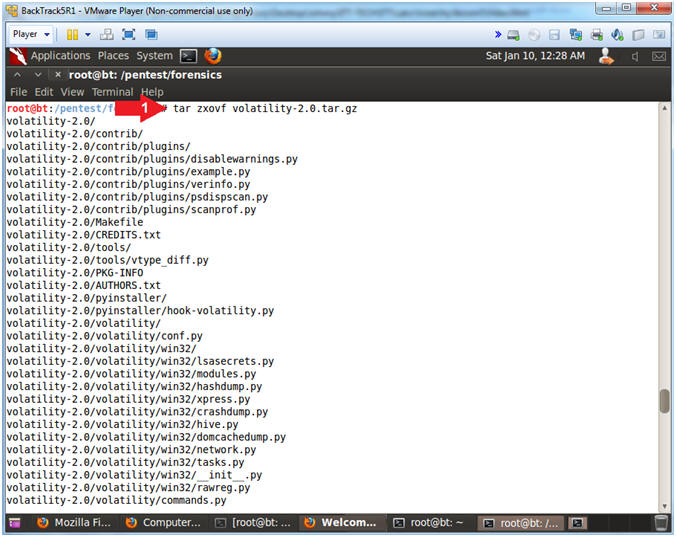
- Untar/Uncompress Volatility 2.0
- Instructions
- tar zxovf volatility-2.0.tar.gz
- Note(FYI)
- tar, stores and extracts files from a tape
or disk archive.
- z(unzip when used with "x"), x(extract), o(keep ownerships), v(verbose), and f(specify archive file)
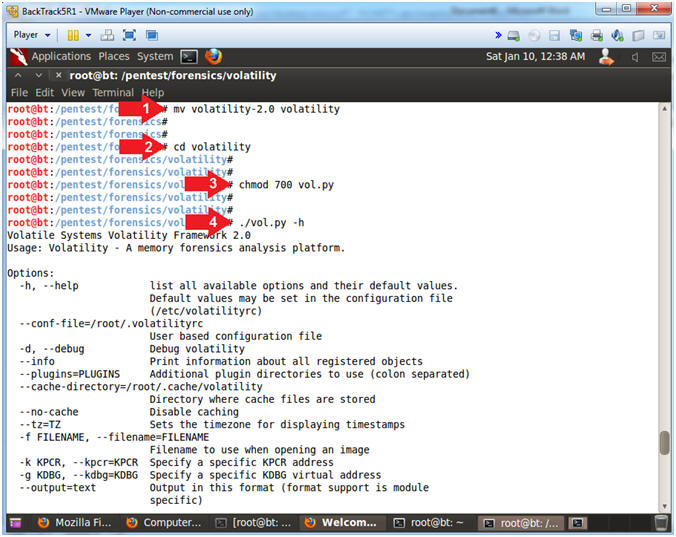
- Setup and Test Volatility
- Instructions
- mv volatility-2.0 volatility
- Move volatility 2.0 to the pre-existing volatility Directory
- cd volatility
- chmod 700 vol.py
- Give volatility World, Right and Execute User Permissions.
- ./vol.py -h
- Display the volatility help menu
| Section 5: Proof of Lab |
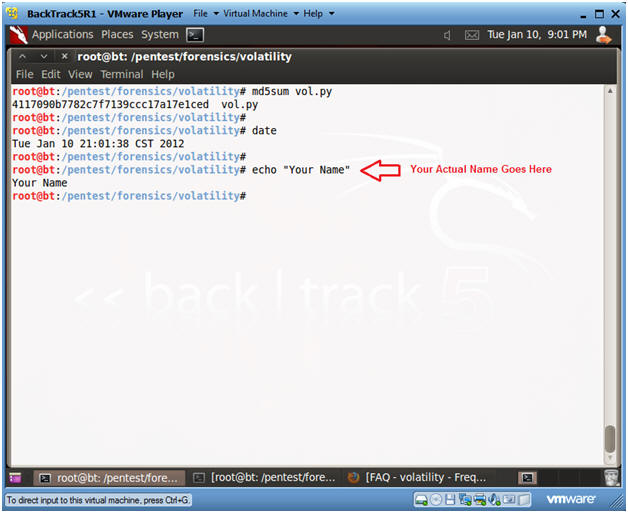
- Proof of Lab
- Instructions
- md5sum vol.py
- date
- echo "Your Name"
- Put in your actual name in place of "Your Name"
- e.g., echo "John Gray"
-
Proof of Lab
Instructions
- Press the <Ctrl> and <Alt> key at the same time.
- Press the <PrtScn> key.
- Paste into a word document
- Upload to Moodle
- Instructions