(LosBuntu: VirusTotal)
{ Configure VirusTotal API KEY with Perl and Curl }
| Section 0: Background Information |
- What is the scenario?
- Incident Response Engineers often need to analyze mountains of data very quickly for malware and abnormalities. Consequently, interrogating each executable with one Anti-Virus scanner is not only time consuming, but very inefficient. Accordingly, most Anti-Virus Scanners don't have the resources to alert on everything. But what if there is way to remotely query all the most popular Anti-Virus Scanners using a simple Perl Script?
- The following lesson will walk you through setting up your VirusTotal API Key with a Perl Script to remotely query VirusTotal. In addition this Perl Script will simultaneously create a simply spreadsheet to display Anti-Virus Scanner results for management using the KISS methodology.
- What is VirusTotal?
- VirusTotal, a subsidiary of Google, is a free online service that analyzes files and URLs enabling the identification of viruses, worms, trojans and other kinds of malicious content detected by antivirus engines and website scanners. VirusTotal aggregates 55 antivirus products and 61 online scan engines to check for viruses that the user's own antivirus may have missed, or to verify against any false positives.
- What is LosBuntu?
- I wanted to thank my good friend Carlos Cajigas (@carlos_cajigas) for creating LosBuntu and for his generous guidance and mentorship in Cyber Forensics.
- LosBuntu is a Linux Live DVD distribution (distro) that can be used to assist in data forensic investigations. It is a compilation of Master Cajigas' many years of experience as a former law enforcement agent and IBM forensics investigator.
- Reference
- Pre-Requisite Lab
-
Lab Notes
- In this lab we will do the following:
- Join the VirusTotal Community
- Obtain VirusTotal API Key
- Configure VirusTotal Perl Script
- Test VirusTotal Perl Script
- In this lab we will do the following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- You are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2016 No content replication of any kind is allowed without express written permission.
| Section 1: Power On the LosBuntu VM |
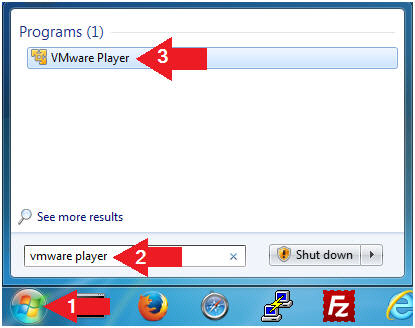
- Open VMware Player on your windows machine.
- Instructions:
- Click the Start Button
- Type "vmware player" in the search box
- Click on VMware Player
- Instructions:
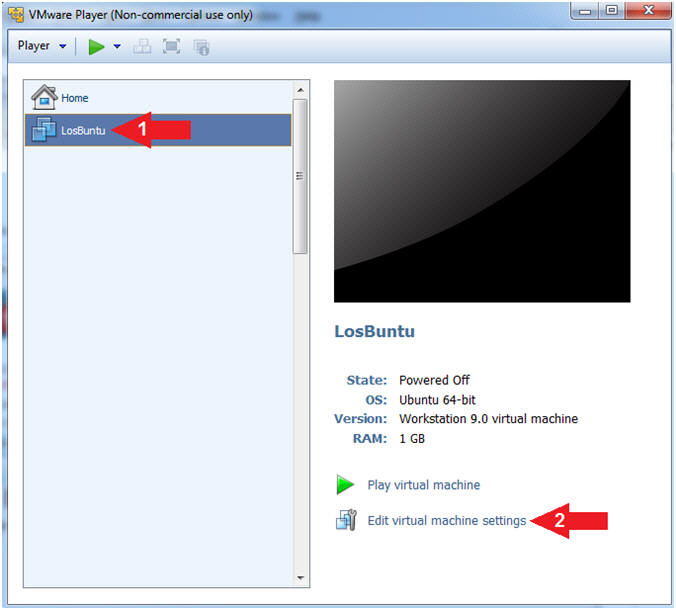
- Edit Virtual Machine Settings
- Instructions:
- Select LosBuntu
- Click Edit Virtual Machine Settings
- Instructions:
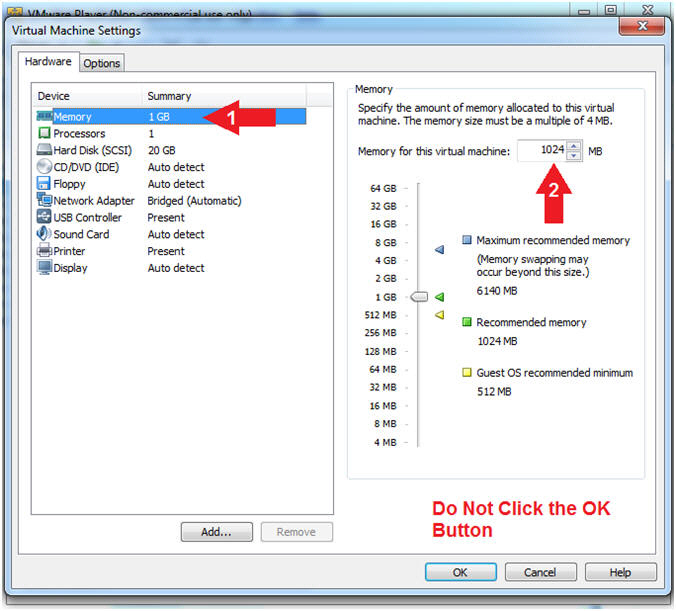
- Configure Memory
- Instructions:
- Click on Memory.
- Up the memory to 1 GB
- Note(FYI):
- LosBuntu really needs 1.5 to 2 GB; however, you are only configuring MimiKatz with Volatility in this lesson.
- Do NOT Click the OK Button, we still have more to configure.
- Instructions:
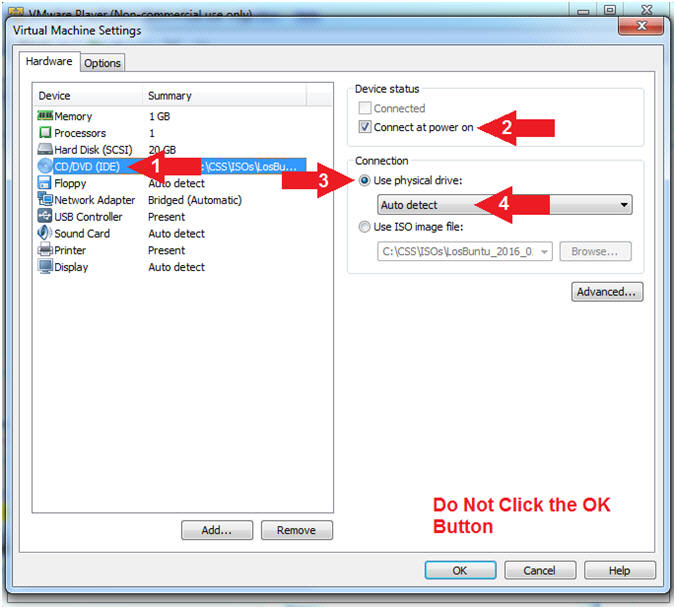
- Configure CD/DVD(IDE)
- Instructions:
- Click on CD/DVD(IDE)
- Device status: Check Connect at power on
- Connection: Click Use physical drive
- Select Auto detect
- Note(FYI):
- Do NOT Click the OK Button, we still have more to configure
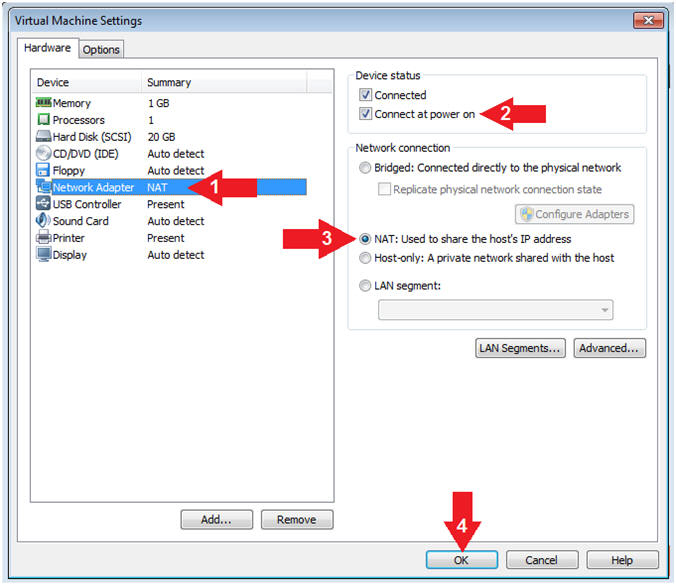
- Instructions:
- Configure Network Adapter
- Instructions:
- Click on Network Adapter
- Device status: Check Connect at power on
- Network Connection: Click NAT: Used to share the ....
- Click the OK Button
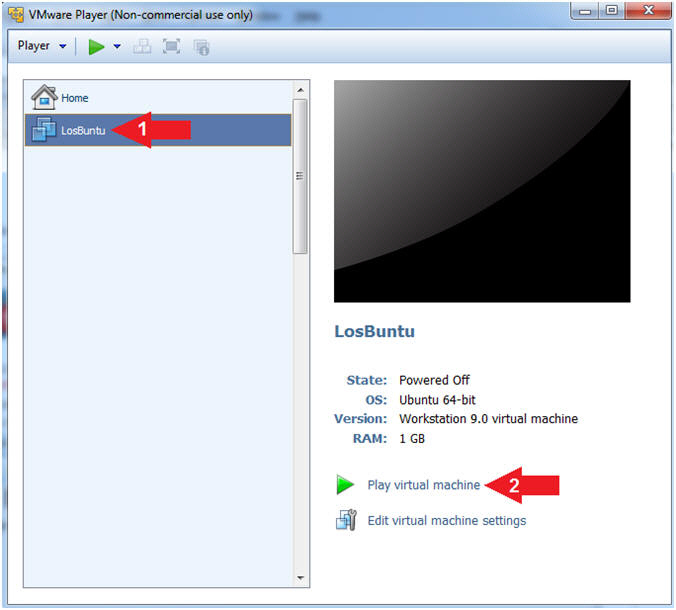
- Instructions:
- Play LosBuntu Virtual Machine
- Instructions:
- Select LosBuntu
- Click Play virtual machine
- Instructions:
| Section 2: Login to LosBuntu |
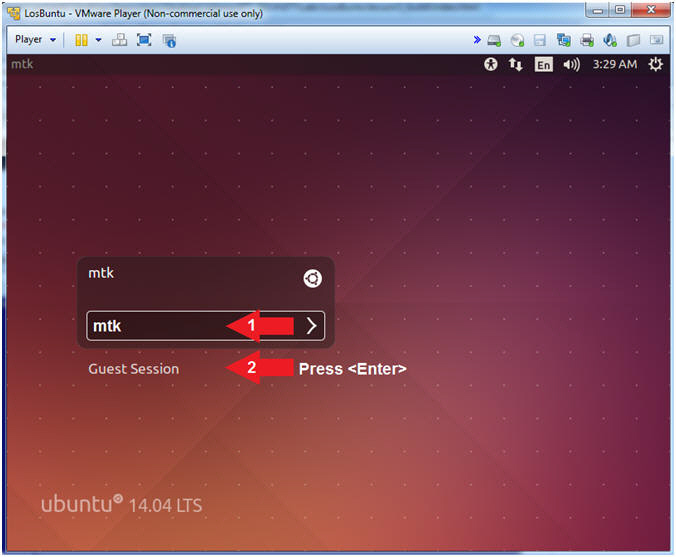
- Login to LosBuntu
- Instructions:
- Password: mtk
- Press <Enter>
- Instructions:
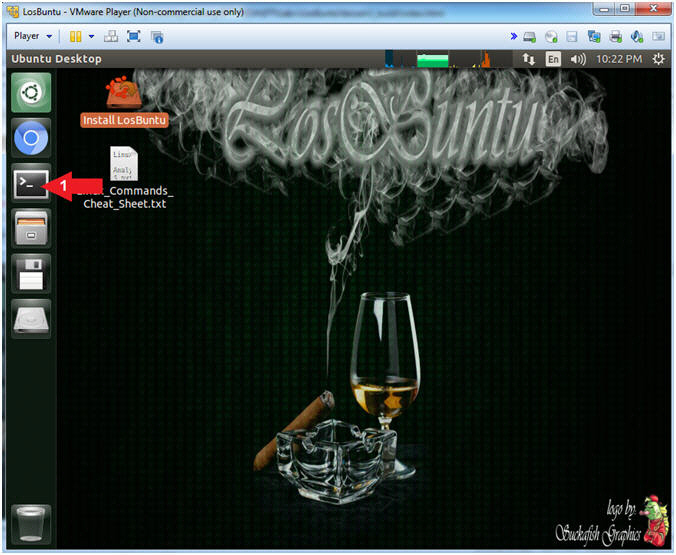
- Open Terminal Windows
- Instructions:
- Click on the Terminal Window

- Click on the Terminal Window
- Instructions:
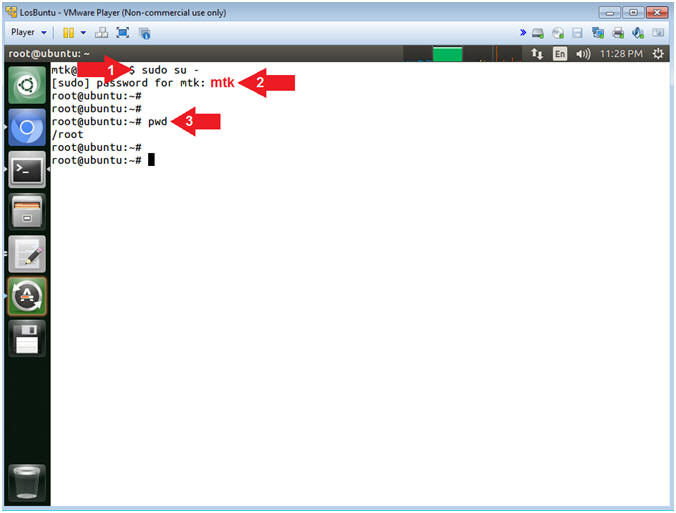
- Become root
- Instructions:
- sudo su -
- password: mtk
- pwd
- Note(FYI):
- Command #1, Use (sudo su -) to simulate an initial root login where the /etc/profile, .profile and .bashrc are executed. Not only will the root user's environment be present, but also the root user will be placed in it's own home directory (/root).
- Command #2, Use (pwd) to display the current working directory of the particular user.
- Instructions:
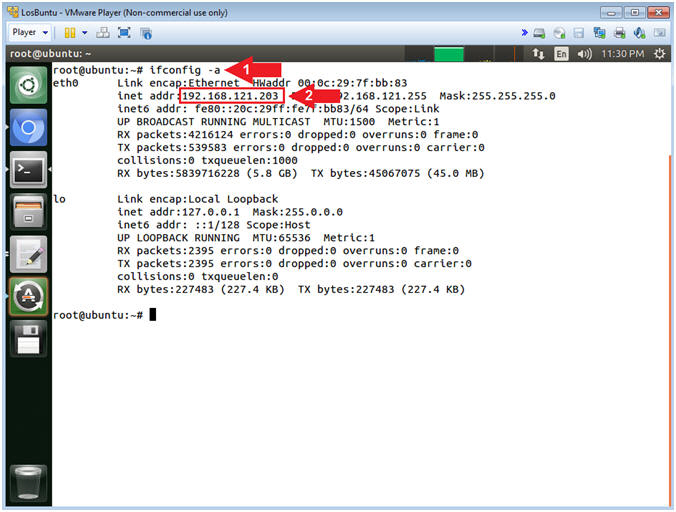
- Obtain IP Address
- Instructions:
- ifconfig -a
- Record Your IP Address
- Note(FYI):
- Command #1, Use (ifconfig) to view all
(-a) IP Addresses associated with LosBuntu. You should only have
two interfaces: eth0 and lo.
- eth0 - Is the primary interface. In my case, the IP Address is 192.168.121.203.
- lo - Is the local loopback address. The loopback address is used to establish an IP connection to the same machine or computer being used by the end-user. The loopback construct gives a computer or device capable of networking the capability to validate or establish the IP stack on the machine.
- If your host machine has Internet
Connectivity, but LosBuntu does not have an IP Address associated
with eth0, then issue the following command as root.
- dhclient -v
- Command #1, Use (ifconfig) to view all
(-a) IP Addresses associated with LosBuntu. You should only have
two interfaces: eth0 and lo.
- Instructions:
| Section 3: VirusTotal Registration |
- Search Icon
- Instructions:
- Click on the Search Icon
- Instructions:
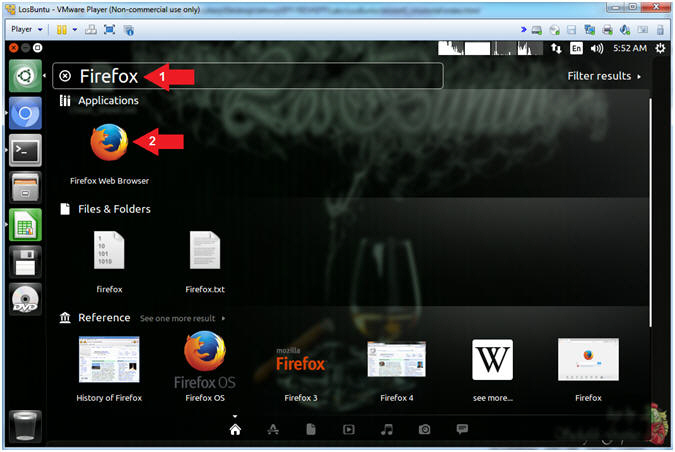
- Start Firefox
- Instructions:
- Search for FireFox
- Click on the Firefox Web Browser Icon
- Instructions:
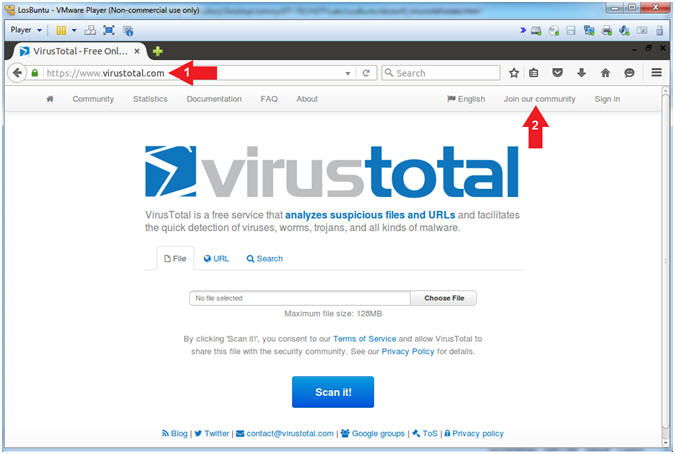
- Navigate to VirusTotal
- Instructions:
- Navigate to VirusTotal
- https://www.virustotal.com
- Click on Join our community
- Navigate to VirusTotal
- Note(FYI):
- Command #1, The VirusTotal application allows you to submit and scan files again 60 of the most well known Anti-Virus databases.
- Instructions:
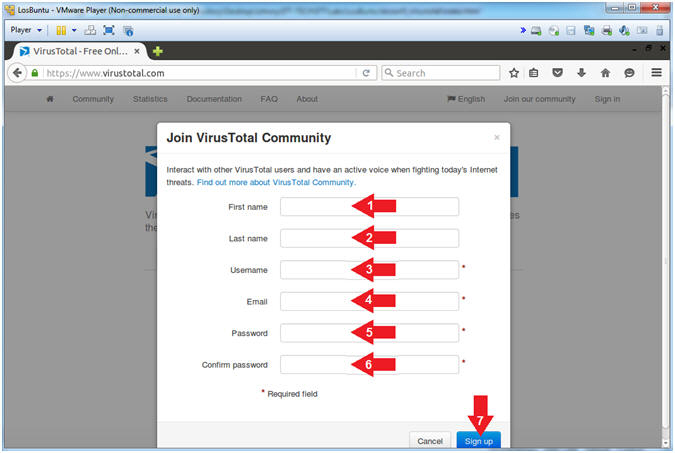
- Join VirusTotal Community
- Instructions:
- First Name
- Last Name
- Username
- Password: Do not use your actual email password.
- Confirm Password
- Click the Sign up Button
- Note(FYI):
- In order to use their API, you must join the community. Trust me, their Cyber Kung-Fu is worth it.
- Instructions:
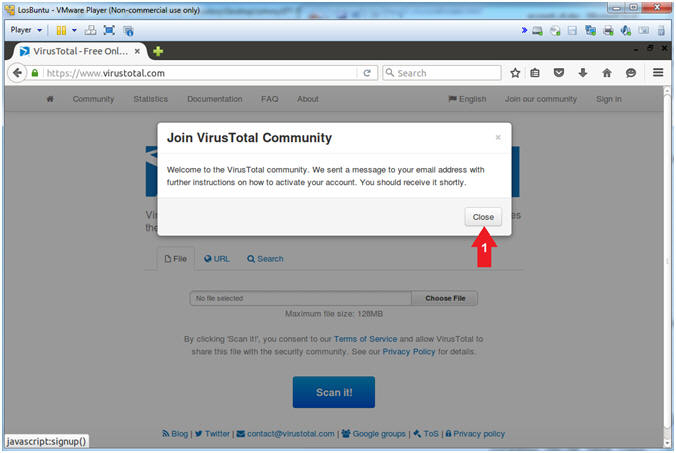
- VirusTotal Welcome Note
- Instructions:
- Click the Close Button
- Note(FYI):
- A message was sent to your email address with further activation instructions.
- Instructions:
| Section 4: VirusTotal API Key |
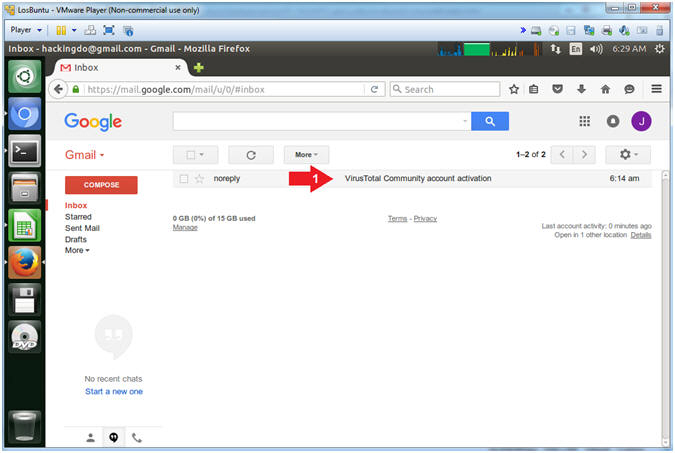
- View VirusTotal Email
- Instructions:
- Go to your Inbox and click on the
message from VirusTotal
- Subject: VirusTotal Community account activation
- Go to your Inbox and click on the
message from VirusTotal
- Instructions:
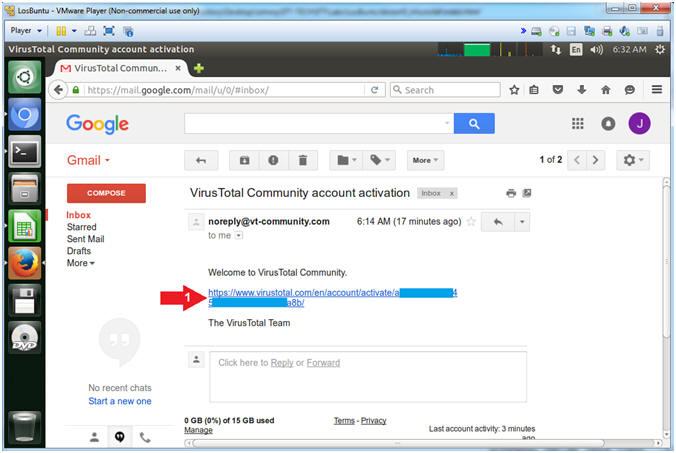
- VirusTotal Activation Code
- Instructions:
- Click the Activation Link
- Note(FYI):
- Obviously, my link will be different than yours.
- Instructions:
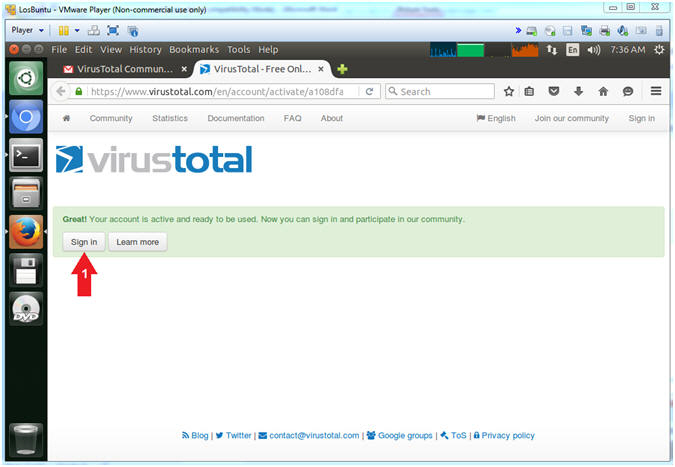
- VirusTotal Sign in
- Instructions:
- Click the Sign in Button
- Instructions:
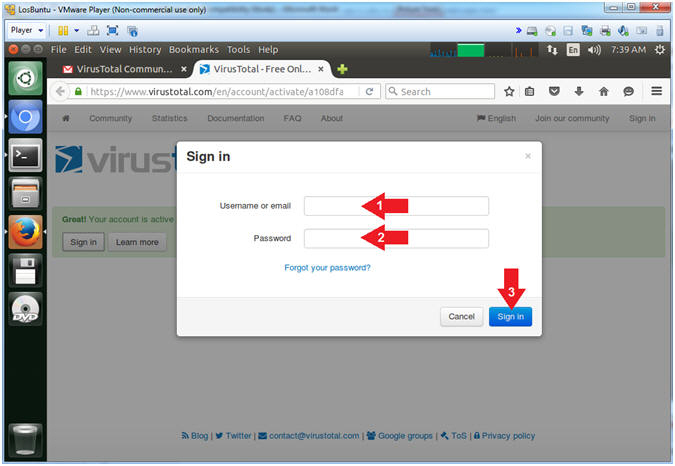
- VirusTotal Login
- Instructions:
- Supply Username or email
- Supply Password
- Click the Sign in Button
- Instructions:
- Access API Key
- Instructions:
- Click on Your Name
- Click on My API key

- Instructions:
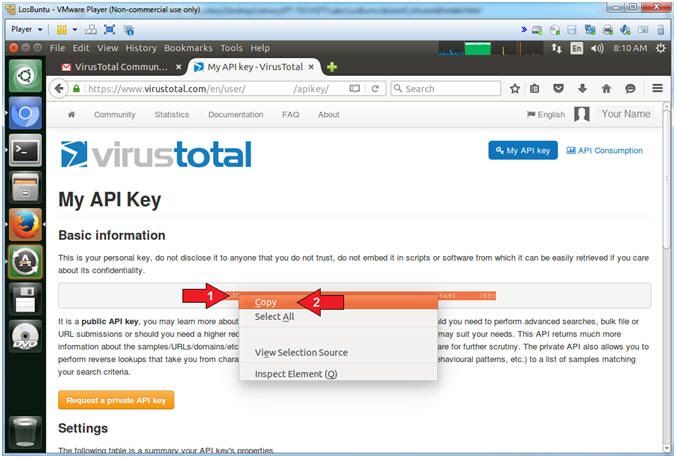
- Copy API Key
- Instructions:
- Highlight and Right Click on Your Name
- Select Copy
- Instructions:
- Search Icon
- Instructions:
- Click on the Search Icon

- Instructions:
- Open gedit
- Instructions:
- Search for: gedit
- Click on the gedit text editor

- Instructions:
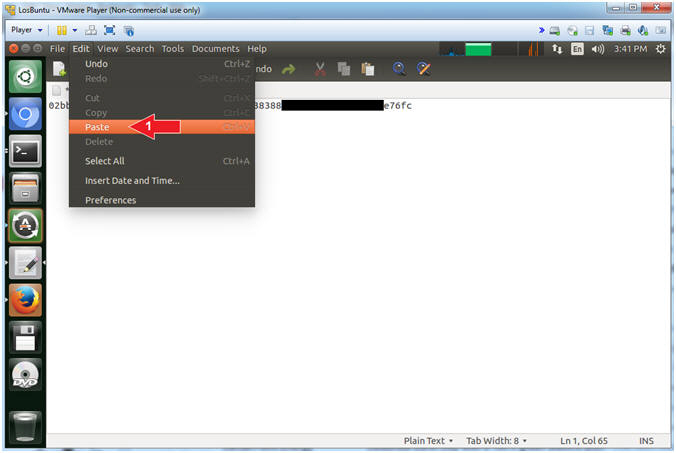
- Paste Key
- Instructions:
- Edit --> Paste
- Instructions:
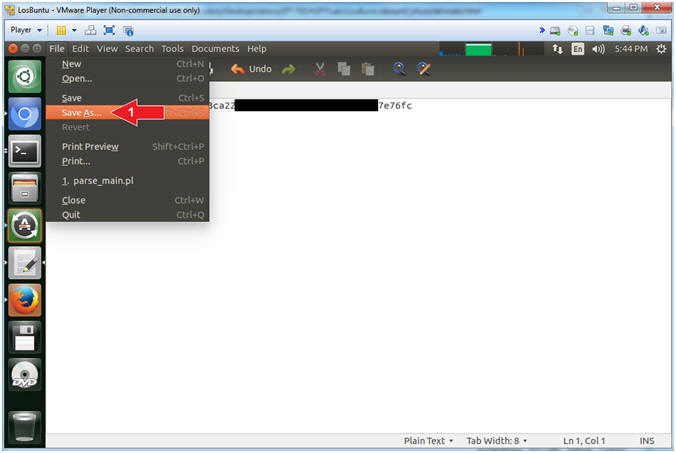
- Save File (Part 1)
- Instructions:
- Edit --> Save As
- Instructions:
- Save File (Part 2)
- Instructions:
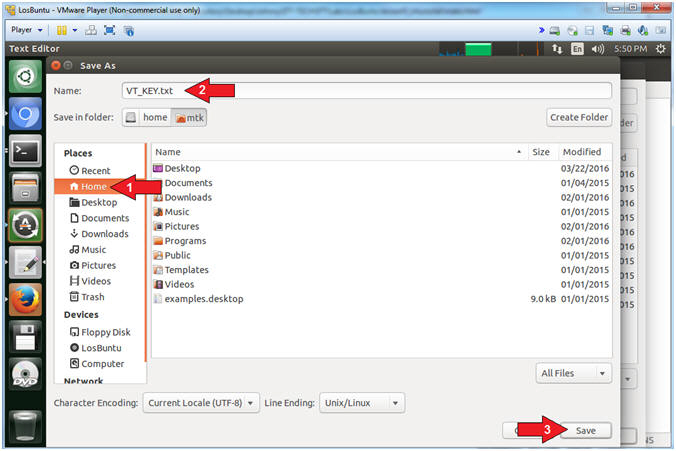
- Name: VT_KEY.txt
- Click on Home
- Click the Save Button
- Note(FYI):
- Command #1, This is the file that will contain your virus total api key.
- Instructions:
| Section 5: Download VirusTotal Perl Script |
- Open Terminal Windows
- Instructions:
- Click on the Terminal Window

- Click on the Terminal Window
- Note(FYI):
- Command #1, Clicking on the Terminal Window icon will display your previous Terminal Window, if you already did not close it.

- Instructions:
- Download VirusTotal Perl Script
- Instructions:
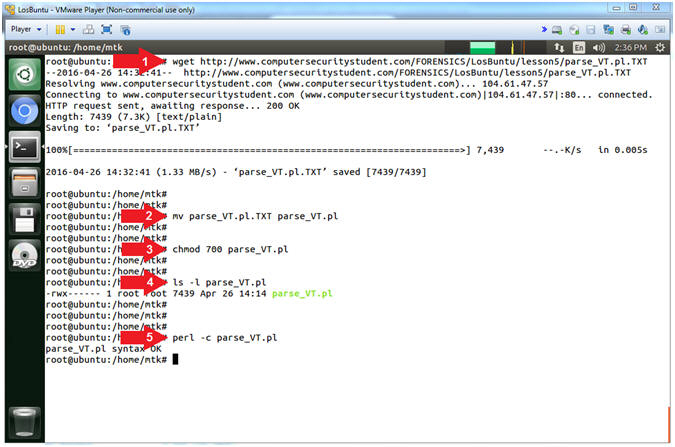
- wget http://www.computersecuritystudent.com/FORENSICS/LosBuntu/lesson5/parse_VT.pl.TXT
- mv parse_VT.pl.TXT parse_VT.pl
- chmod 700 parse_VT.pl
- ls -l parse_VT.pl
- perl -c parse_VT.pl
- Note(FYI):
- Command #1, Use (wget) to download a perl script that uses curl and a VirusTotal API key to POST a SHA-256 signature to the VirusTotal Application. This Perl Script is in no way associated with VirusTotal. It was written by (Computer Security Student, LLC) to demonstrate very basic perl programming and automation.
- Command #2, Use (mv) to rename parse_VT.pl.TXT -to- parse_VT.pl.
- Command #3, Use (chmod) to provide the owner of (parse_VT.pl) read(4), write(2) and execute(1) permission.
- Command #4, Use (ls -l) to list the permission and ownership details of (parse_VT.pl).
- Command #5, Use (perl -c) to allow the perl interpreter to check the grammar/code for syntax errors.
- Instructions:
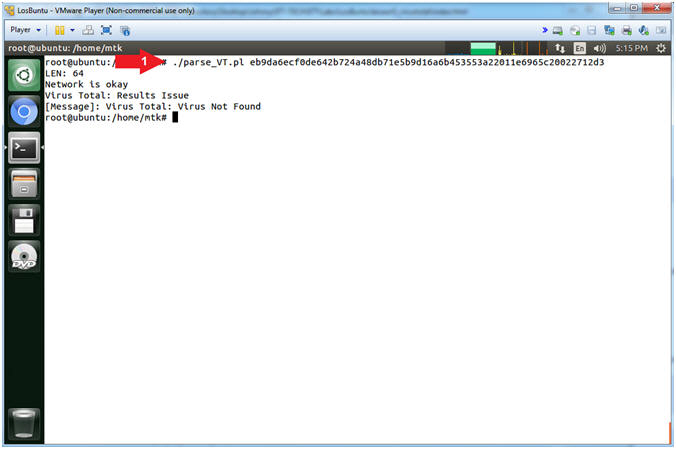
- Scan Non-Malicious SHA-256 Hash
- Instructions:
- ./parse_VT.pl eb9da6ecf0de642b724a48db71e5b9d16a6b453553a22011e6965c20022712d3
- Note(FYI):
- Command #1, The above SHA-256 Hash was taken from a non-infected cmd.exe file. The SHA-256 Hash was checked against VirusTotal's 65 Anti-Virus databases.
- Instructions:
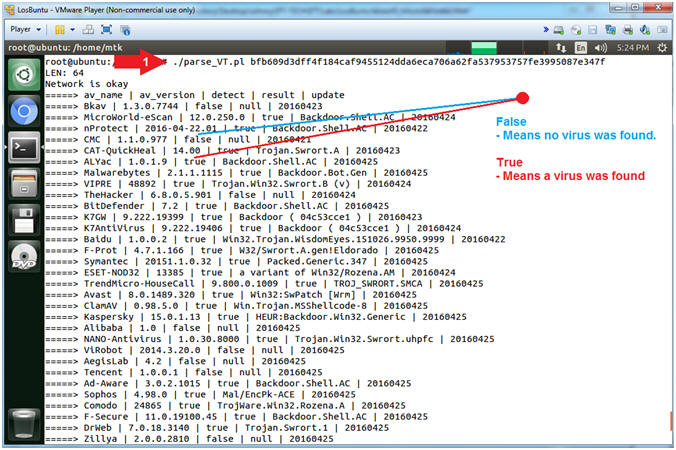
- Scan Non-Malicious SHA-256 Hash
- Instructions:
- ./parse_VT.pl bfb609d3dff4f184caf9455124dda6eca706a62fa537953757fe3995087e347f
- Note(FYI):
- Command #1, This SHA-256 Hash was taken from a (exploit/windows/local/bypassuac) stager. 40 out of 65 Anti-Virus engines were able to identify the stagger as malware (Backdoor, Trojan, etc).
- Instructions:
- View Primitive VirusTotal CSV
- Instructions:
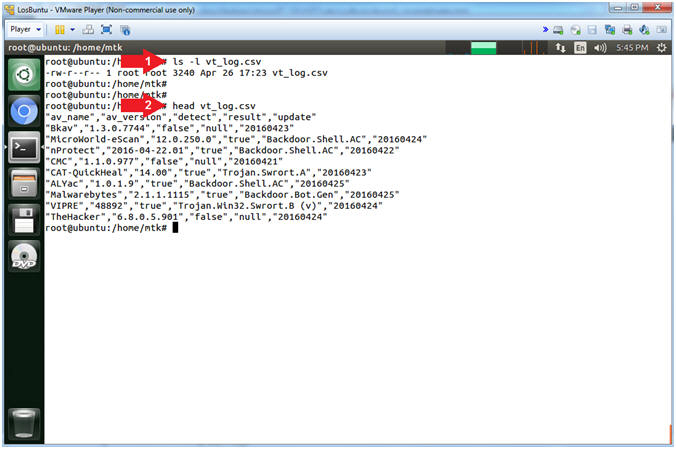
- ls -l vt_log.csv
- head vt_log.csv
- Note(FYI):
- A CSV file stands for Comma Separated
Value. This file can be easily imported into a spreadsheet.
Notice that each column is separated by quotes(") and commas(,).
- E.g., "Column1","Column2","Column3"
- Command #1, Use (ls -l) to view the permissions and ownership of the vt_log.csv file.
- Command #2, Use (head) to view the first 10 lines of the vt_log.csv file.
- A CSV file stands for Comma Separated
Value. This file can be easily imported into a spreadsheet.
Notice that each column is separated by quotes(") and commas(,).
- Instructions:
| Section 6: Convert VirusTotal Output to Spreadsheet |
- Search Icon
- Instructions:
- Click on the Search Icon

- Instructions:
- Open LibreOffice
- Instructions:
- Search For: libreoffice
- Click on LibreOffice
- Instructions:
- Open VirusTotal Spreadsheet (Part 1)
- Instructions:
- File --> Open
- Instructions:
- Open VirusTotal Spreadsheet (Part 2)
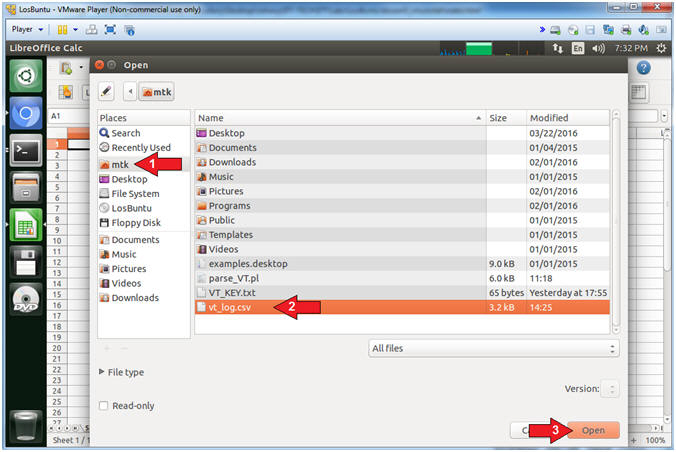
- Instructions:
- Click on the mtk folder
- Select the vt_log.csv file
- Click the Open Button
- Instructions:
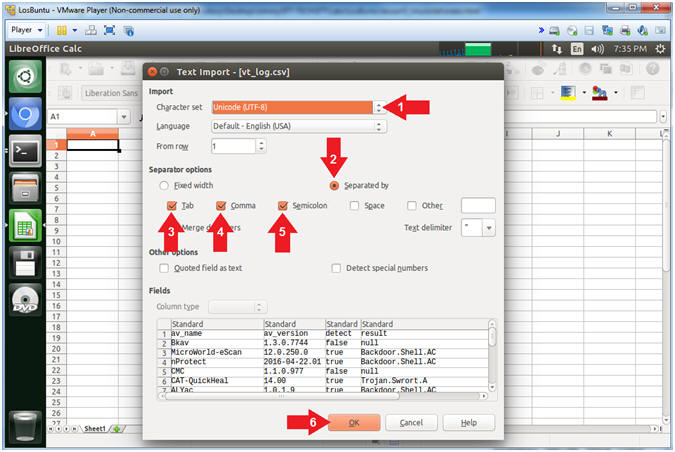
- Import VirusTotal CSV File
- Instructions:
- Character set: Unicode (UTF-8)
- Separator options: Separated by
- Check Tab
- Check Comma
- Check Semicolon
- Click the OK Button
- Instructions:
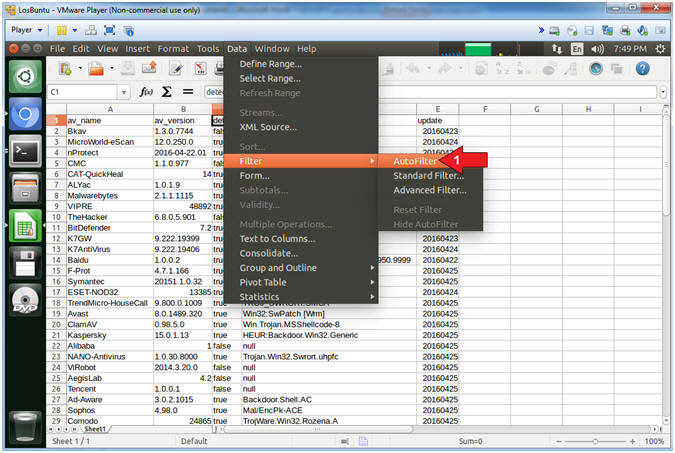
- Turn on Auto Filtering
- Instructions:
- Data --> Filter --> AutoFilter
- Instructions:
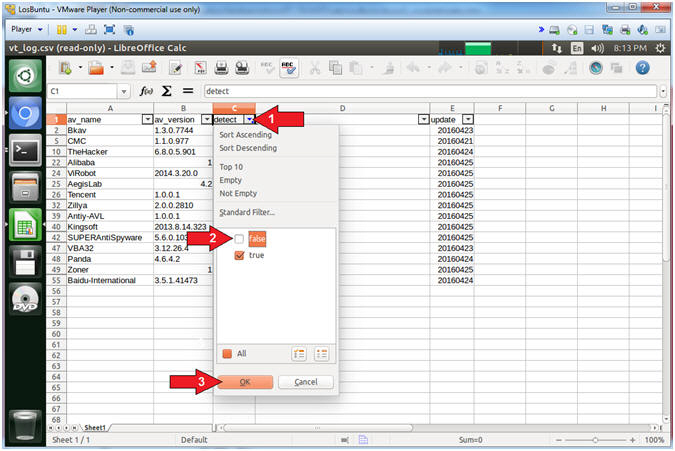
- Filter by Detection
- Instructions:
- Select the Detect Down Arrow
- Uncheck false
- Click the OK Button
- Instructions:
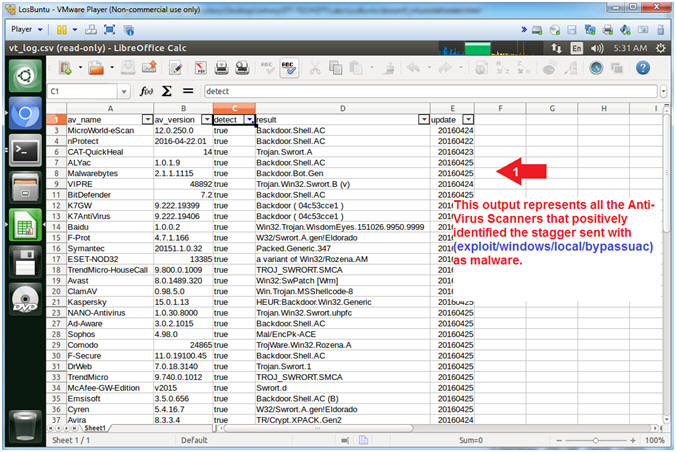
- View VirusTotal Detection Results
- Note(FYI):
- The results display the Anti-Virus Scanners that detected the SHA-256 Hash to represent a Virus. This could make a nice clean simple report for management. Typically, upper level management does not like all the bells and whistles to contribute to their ADHD. So, it is best to practice KISS. (KISS = Keep It Simple Stupid).
- Note(FYI):
| Section 7: Proof of Lab |
- Resume Terminal Session
- Instructions:
- Click the Terminal Icon
- Instructions:
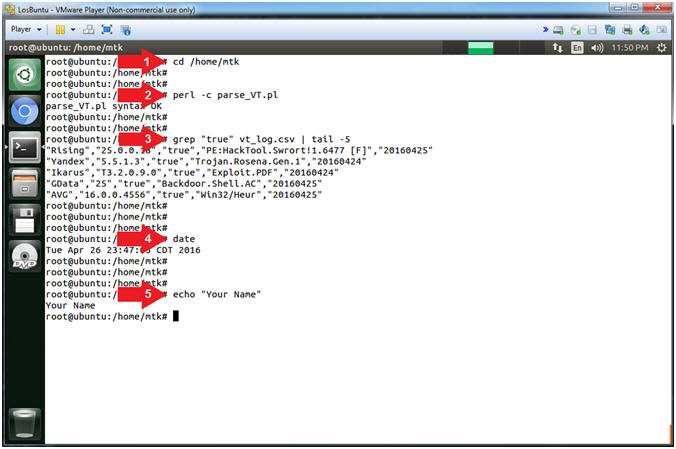
- Proof of Lab
- Instructions:
- cd /home/mtk
- perl -c parse_VT.pl
- grep "true" vt_log.csv | tail -5
- date
- echo "Your Name"
- Replace the string "Your Name" with your actual name.
- e.g., echo "John Gray"
- Note(FYI):
- Command #1, Use (cd) to change directory into /home/mtk.
- Command #2, Use (perl -c) to instruct the perl interpreter to analyze the code (parse_VT.pl) for proper syntax.
- Command #3, Use (grep) to search vt_log.csv for the string(true), then use (tail -5) to display the last 5 lines of the output filtered by (grep).
-
Proof of Lab Instructions:
- Do a PrtScn
- Paste into a word document
- Upload to Moodle
- Instructions: