(LosBuntu: Volatility)
{ Download and Install MimiKatz.py Plugin }
| Section 0: Background Information |
- What is the scenario?
- Forensics Investigators constantly have to update their skillset with tools that change the game. Many of you have played with the stand alone version of MimiKatz and/or the Metasploit MimiKatz plugin. But did you know that there is a MimiKatz plugin for Volatility? This is important because it provides another way to capture a password (of a logged in user) from a memory image without having to extract the HIVE and crack passwords.
- The following lesson will show you how to download and configure the mimikatz.py plugin with volatility.
- What is mimikatz?
- Mimikatz is a tool that pulls plain-text passwords out of WDigest interfaced through LSASS. WDigest is a DLL first added in Windows XP that is used to authenticate users against the HTTP Digest authentication and Simple Authentication Security Layer (SASL) exchanges. Both of these require the user's plain-text password in order to derive the key to authenticate, thus why it is stored in plain-text.
- Special thanks goes out to the mimikatz author, Benjamin DELPY (@gentilkiwi), for his game-changing work.
- Reference: https://github.com/gentilkiwi/mimikatz
- What is LosBuntu?
- I wanted to thank my good friend Carlos Cajigas (@carlos_cajigas) for creating LosBuntu and for his generous guidance and mentorship in Cyber Forensics.
- LosBuntu is a Linux Live DVD distribution (distro) that can be used to assist in data forensic investigations. It is a compilation of Master Cajigas' many years of experience as a former law enforcement agent and IBM forensics investigator.
- Special Thanks
- Thank you (@cruzhams) for providing the blueprints to get mimikatz working with Volatility.
- Pre-Requisite Lab
-
Lab Notes
- In this lab we will do the following:
- Download mimikatz.py
- Add mimikatz.py to Volatility plugins directory
- Create a Construct
- In this lab we will do the following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- You are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2016 No content replication of any kind is allowed without express written permission.
| Section 1: Power On the LosBuntu VM |
- Note(FYI): LosBuntu will be used later to forensically collect a memory snapshot of the BadBlue Metasploit Attack Vector.
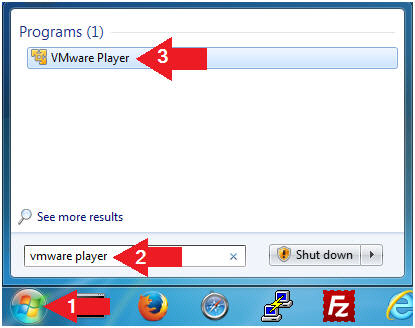
- Open VMware Player on your windows machine.
- Instructions:
- Click the Start Button
- Type "vmware player" in the search box
- Click on VMware Player
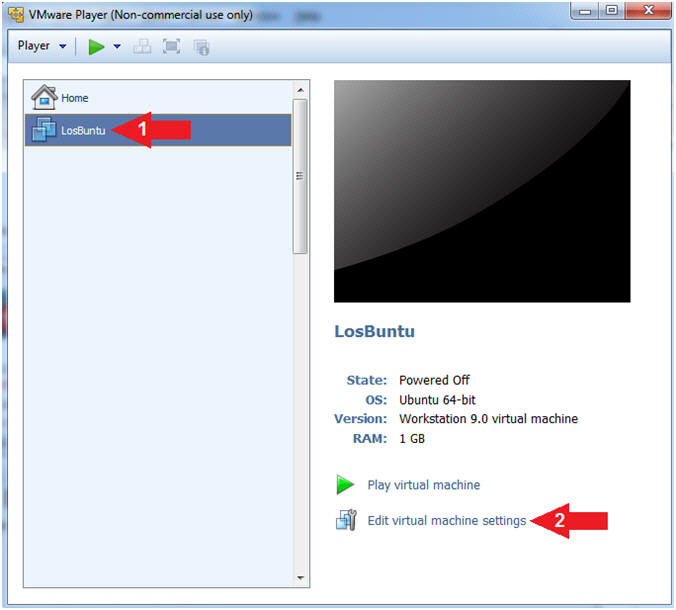
- Instructions:
- Edit Virtual Machine Settings
- Instructions:
- Select LosBuntu
- Click Edit Virtual Machine Settings
- Instructions:
- Configure Memory
- Instructions:
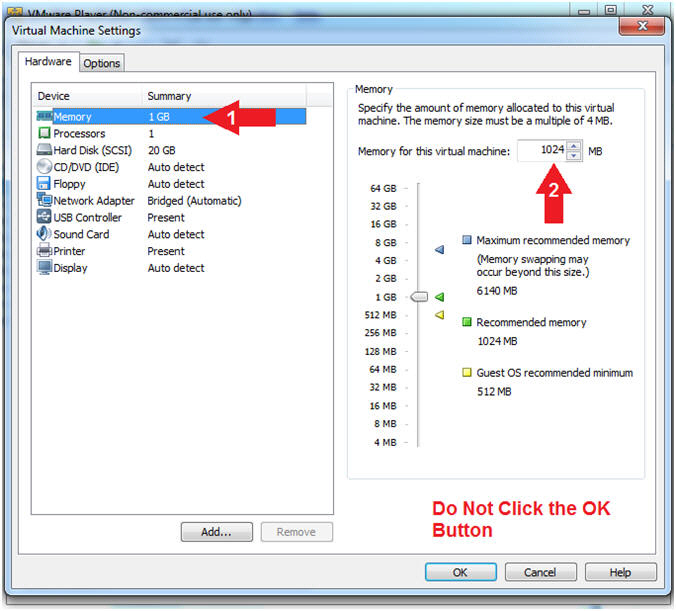
- Click on Memory.
- Up the memory to 1 GB
- Note(FYI):
- LosBuntu really needs 1.5 to 2 GB; however, you are only configuring MimiKatz with Volatility in this lesson.
- Do NOT Click the OK Button, we still have more to configure.
- Instructions:
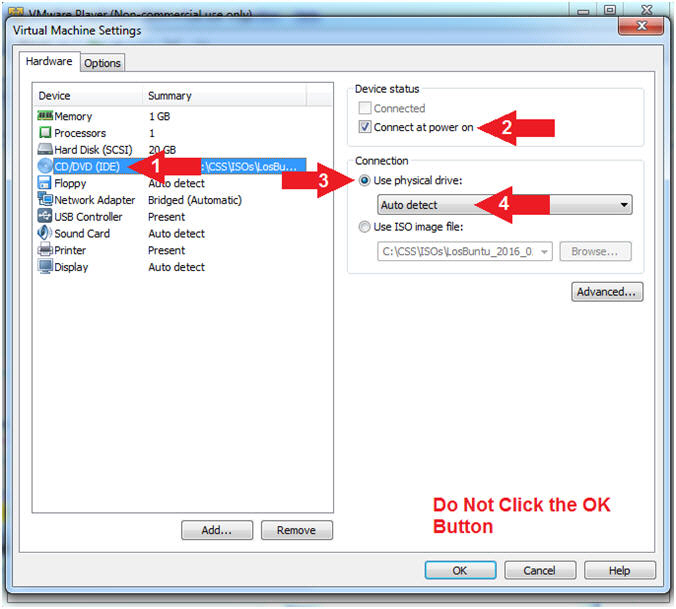
- Configure CD/DVD(IDE)
- Instructions:
- Click on CD/DVD(IDE)
- Device status: Check Connect at power on
- Connection: Click Use physical drive
- Select Auto detect
- Note(FYI):
- Do NOT Click the OK Button, we still have more to configure
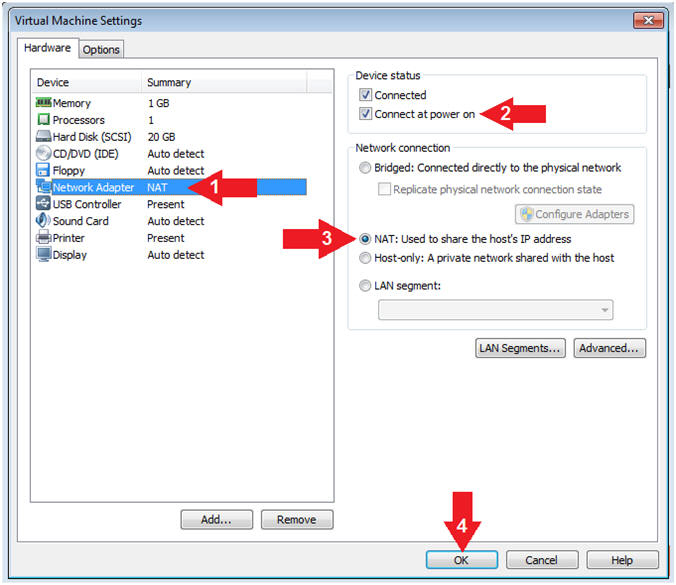
- Instructions:
- Configure Network Adapter
- Instructions:
- Click on Network Adapter
- Device status: Check Connect at power on
- Network Connection: Click NAT: Used to share the ....
- Click the OK Button
- Instructions:
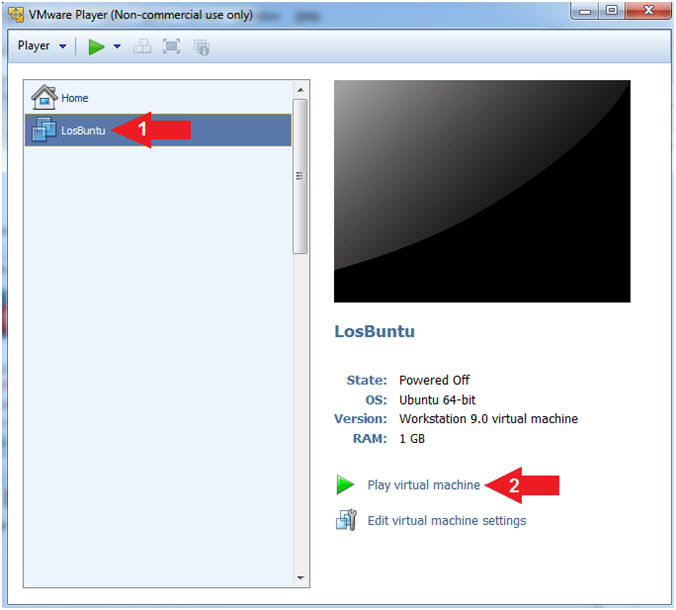
- Play LosBuntu Virtual Machine
- Instructions:
- Select LosBuntu
- Click Play virtual machine
- Instructions:
| Section 2: Login to LosBuntu |
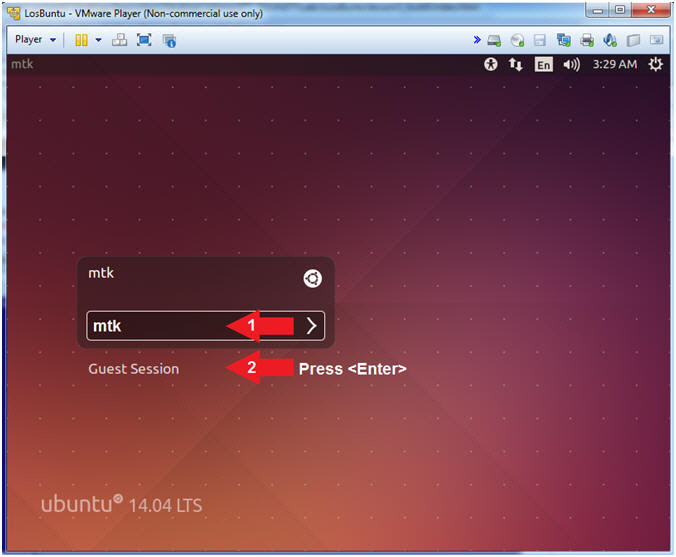
- Login to LosBuntu
- Instructions:
- Password: mtk
- Press <Enter>
- Instructions:
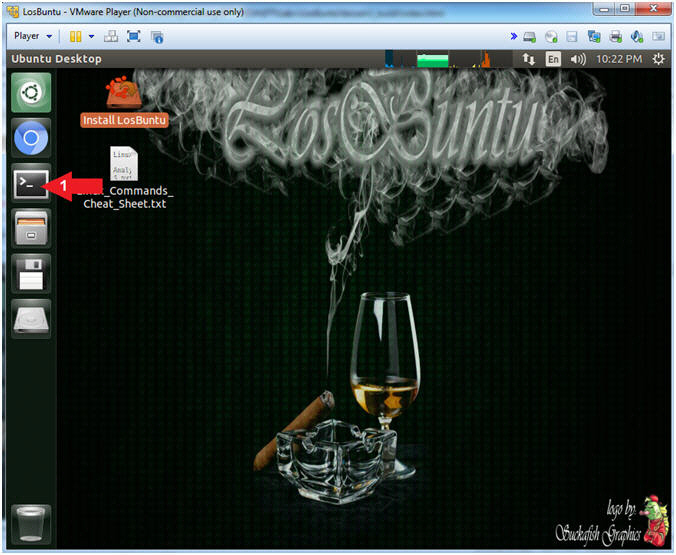
- Open Terminal Windows
- Instructions:
- Click on the Terminal Window

- Click on the Terminal Window
- Instructions:
- Become root
- Instructions:
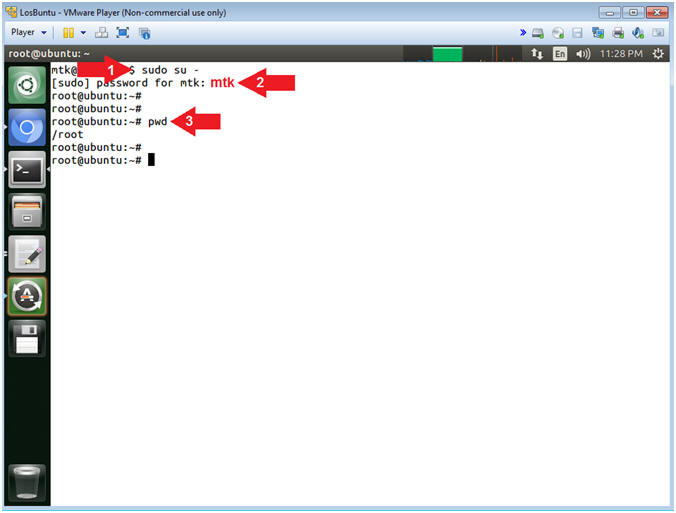
- sudo su -
- password: mtk
- pwd
- Note(FYI):
- Command #1, Use (sudo su -) to simulate an initial root login where the /etc/profile, .profile and .bashrc are executed. Not only will the root user's environment be present, but also the root user will be placed in it's own home directory (/root).
- Command #2, Use (pwd) to display the current working directory of the particular user.
- Instructions:
- Obtain IP Address
- Instructions:
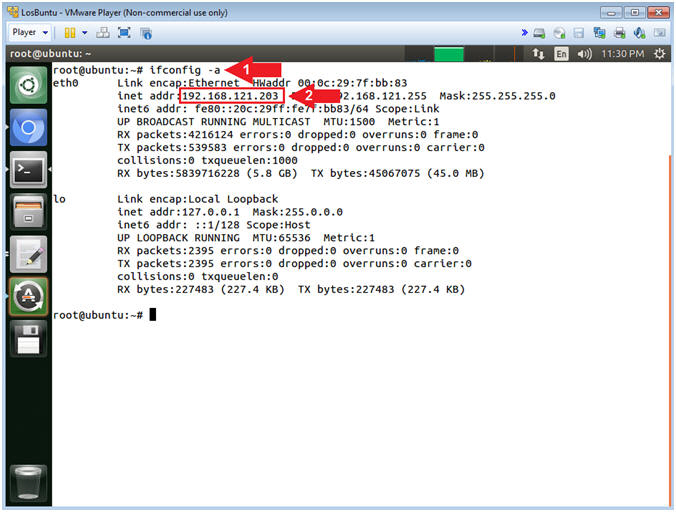
- ifconfig -a
- Record Your IP Address
- Note(FYI):
- Command #1, Use (ifconfig) to view all
(-a) IP Addresses associated with LosBuntu. You should only have
two interfaces: eth0 and lo.
- eth0 - Is the primary interface. In my case, the IP Address is 192.168.121.203.
- lo - Is the local loopback address. The loopback address is used to establish an IP connection to the same machine or computer being used by the end-user. The loopback construct gives a computer or device capable of networking the capability to validate or establish the IP stack on the machine.
- If your host machine has Internet
Connectivity, but LosBuntu does not have an IP Address associated
with eth0, then issue the following command as root.
- dhclient -v
- Command #1, Use (ifconfig) to view all
(-a) IP Addresses associated with LosBuntu. You should only have
two interfaces: eth0 and lo.
- Instructions:
| Section 3: Download MimiKatz Plugin |
- Download MimiKatz (On
LosBuntu)
- Instructions:
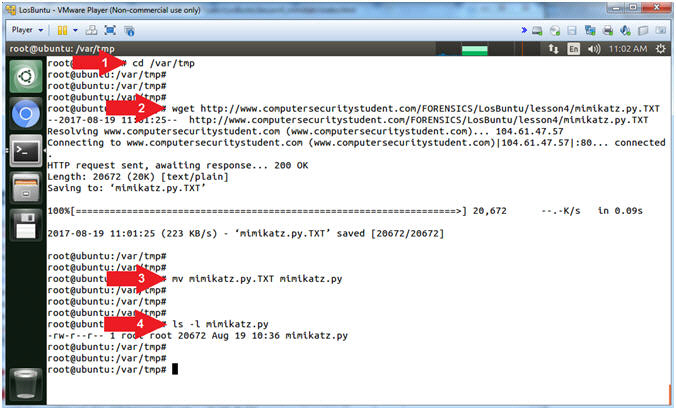
- cd /var/tmp
- wget http://www.computersecuritystudent.com/FORENSICS/LosBuntu/lesson4/mimikatz.py.TXT
- mv mimikatz.py.TXT mimikatz.py
- ls -l mimikatz.py
- Note(FYI):
- Command #1, Use (cd) to navigate into the (/var/tmp) directory.
- Command #2, Use (wget) to download mimikatz.py
- Command #3, Use (mv) to rename (mimikatz.py.TXT) to (mimikatz.py)
- Command #4, Use (ls -l) to list (ie., view) the details of the mimikatz.py file.
- Instructions:
- Determine Volatility Plugins Location
- Instructions:
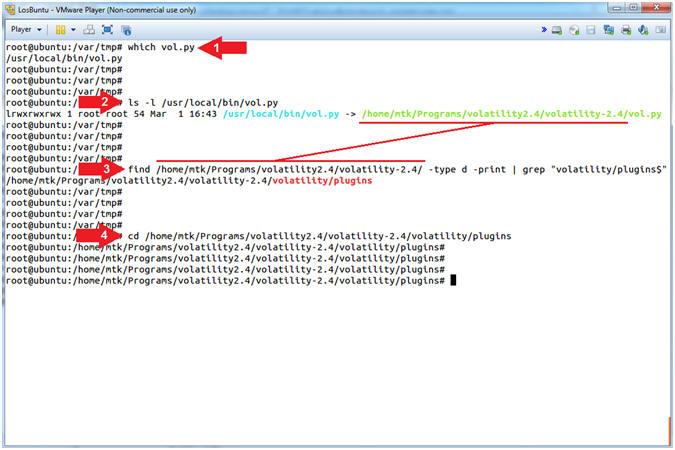
- which vol.py
- ls -l /usr/local/bin/vol.py
- find /home/mtk/Programs/volatility2.4/volatility-2.4/ -type d -print | grep "volatility/plugins$"
- cd /home/mtk/Programs/volatility2.4/volatility-2.4/volatility/plugins
- Note(FYI):
- Command #1, Use (which) to return the path name of vol.py
- Command #2, Use (ls -l) to view the details of the vol.py program. Notice that (/var/local/bin/vol.py) is a soft link that really points to (/home/mtk/Programs/volatility2.4/volatility-2.4/vol.py)
- Command #3, Use (find) to search the (/home/mtk/Programs/volatility2.4/volatility-2.4/) directory and use the (-type) flag to only show directories using (d) and use (grep) to only display output that ends with ($) and contains the string (volatility/plugins). The ($) means ends with.
- Command #4, Use (cd) to navigate to the plugins directory (/home/mtk/Programs/volatility2.4/volatility-2.4/volatility/plugins).
- Instructions:
- Copy MimiKatz Into Plugins Directory
- Instructions:
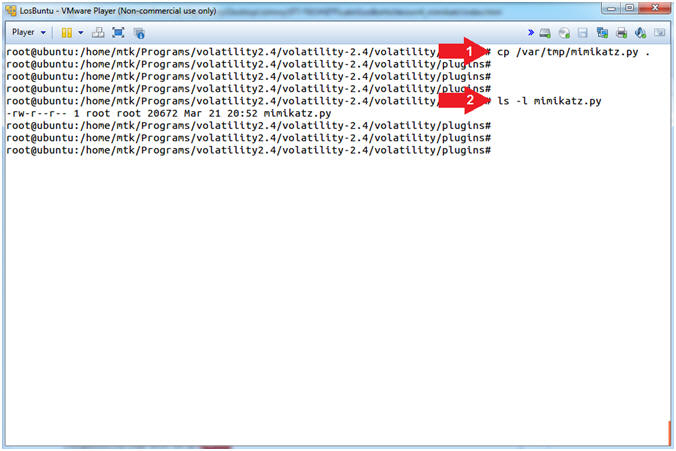
- cp /var/tmp/mimikatz.py .
- ls -l mimikatz.py
- Note(FYI):
- Command #1, Use (cp) to copy mimikatz.py from the (/var/tmp) directory into (.), which is the current working directory.
- Command #2, Use (ls -l) to list the details of the mimikatz.py file.
- Instructions:
| Section 3: Install MimiKatz Construct |
- Install MimiKatz Construct
- Instructions:
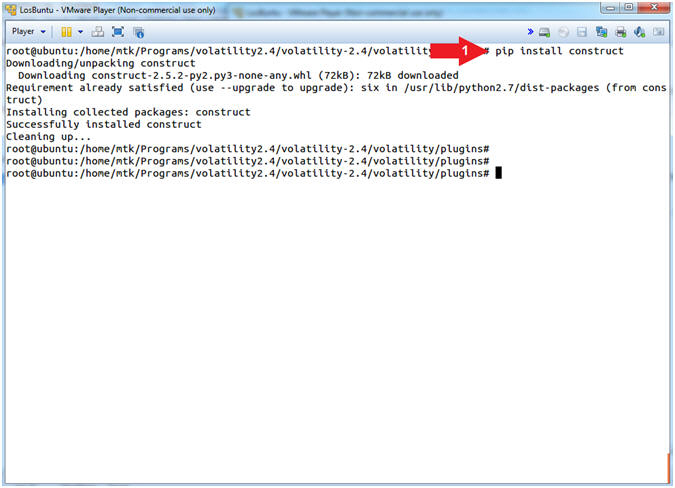
- pip install construct
- Note(FYI):
- Command #1, Use (pip) to install the construct to go with mimikatz.py.
- pip is a Python package installer, recommended for installing Python packages which are not available in the Debian archive.
- Construct is a powerful declarative parser (and builder) for binary data.
- Instructions:
| Section 4: Proof of Lab |
- Copy Forensic Files to Samba Share (On
LosBuntu)
- Instructions:
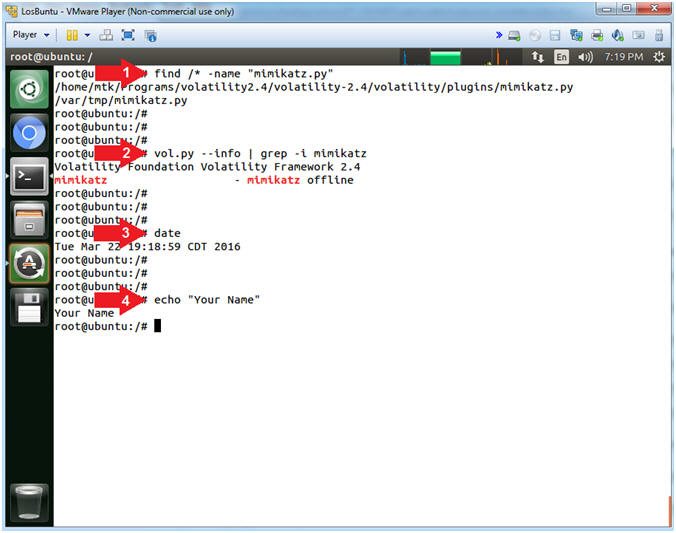
- find /* -name "mimikatz.py"
- vol.py --info | grep -i mimikatz
- date
- echo "Your Name"
- Replace the string "Your Name" with your actual name.
- e.g., echo "John Gray"
- Note(FYI):
- Command #1, Use (find) to search the entire server, starting slash (/) directory, which basically means search the entire computer for the (mimikatz.py) file.
- Command #2, Use (vol.py --info) to list all of volatilities plugins and use (grep) to only display the mimikatz plugin.
-
Proof of Lab Instructions:
- Do a PrtScn
- Paste into a word document
- Upload to Moodle
- Instructions: